An effective Position-based Opportunistic Course-plotting (POR) technique which uses the stateless property of regional redirecting and the passed on features of wi-fi technique. When a information package is sent out, some of the next door next door neighbor nodes that have overheard the transferring will provide as delivering candidates, and take turn to ahead the package if it is not relayed by the particular best forwarder within a certain time frame. By using such in-the-air back-up, connections is handled without being disrupted. The additional latency experienced by local direction recovery is reduced and the duplicate delivering due to package redouble is also reduced. In the case of connections gap, a Unique Destination-based Gap Managing (VDVH) strategy is further recommended to work together with POR. Both theoretical research and simulation outcomes show that POR achieves excellent efficiency even under excellent node versatility with appropriate cost and the new gap handling strategy also works well.A new scalable key control strategy for WSNs which provides a excellent secured relationship protection. For this purpose, we make use of the unital design. We show that the primary implementing from unitals to key pre-distribution allows us to achieve excellent program scalability. However, this simple implementing does not guarantee a higher key talking about probability. Therefore, we suggest an enhanced unital-based key pre-distribution strategy providing excellent network scalability and excellent key talking about probability roughly lower enclosed. We perform approximated research and designs and evaluate our solution to those of present methods for different requirements such as storage area space cost, program scalability, program relationship, and average secured direction length and program resiliency. Our outcomes show that the recommended strategy improves the program scalability while providing high secured relationship coverage and overall enhanced efficiency. Moreover, for an equivalent program size, our solution decreases significantly the storage area space cost compared to those of present alternatives.
Keywords |
| Geographical routing, VDVH, PRO, unital-based key, Cloud computing, data sharing, privacypreserving,
access control, dynamic groups. |
INTRODUCTION |
| A novel Position-based Opportunistic Redirecting (POR) method is suggested, in which several sending applicants
storage cache the bundle that has been obtained using MAC interception. If the best forwarder does not ahead the
bundle in certain time spots, suboptimal applicants will take convert to a head the bundle according to a regionally
established purchase. In this way, provided that one of the applicants is successful in getting and sending the bundle,
the information transmitting will not be disturbed. Prospective multipath are utilized on the fly on a per packet
foundation, major POR’s outstanding sturdiness. The primary efforts of this document can be described as follows: We
recommend a position-based opportunistic redirecting procedure which can be implemented without complicated
adjustment to MAC method and accomplish several wedding celebration without dropping the benefit of accident
prevention offered by 802.11.The idea of in-the-air back-up considerably increases the sturdiness of the redirecting
method and decreases the latency and copy sending due to local path repair. In the case of interaction gap, we |
| recommend a Exclusive Destination-based Gap Managing (VDVH) plan in which the advantages of selfish sending
(e.g., huge enhancement per hop) and opportunistic redirecting can still be obtained while handling interaction voids.
We assess the effect of node flexibility on bundle distribution and describe the enhancement introduced about by the
contribution of sending applicants. The expense of POR with focus on shield utilization and data transfer useage intake
due to sending candidates’ copy sending is also mentioned. Through research, we determine that due to the selection of
sending area and the properly designed replication restriction plan, POR’s efficiency gain can be carried out at little
expense cost. Lastly, we assess the efficiency of POR through comprehensive models and confirm that POR
accomplishes excellent efficiency in the face of great node flexibility while the expense is appropriate. In this perform,
our aim is to deal with the scalability issue without degrading the other system efficiency analytics. For this objective,
we focus on the style of a plan which guarantees a excellent protected protection of comprehensive systems with a low
key storage expense and a excellent system resiliency. To this end, we make use, of the unital style idea for efficient
WSN key pre-distribution. Indeed, we recommend a innocent applying from unital style to key pre-distribution and we
show through systematic research that it allows to accomplish great scalability. Nonetheless, this innocent applying
does not assurance a higher key discussing possibility. Therefore, we recommend an improved unital based key predistribution
plan that preserves a excellent key discussing possibility while improving the system scalability. An initial
perform and few conversations were offered in the efforts of our perform are given next: evaluation the primary state of
the art of symmetrical key management techniques for WSNs that we categorize into two categories: probabilistic
techniques and deterministic ones. We further define the classification into sub-categories in accordance with the real
concepts and methods used in key come back and agreement. We present the use of unital style concept in key pre
distribution for WSNs. We display that the primary applying from unitals to key pre-distribution gives beginning to
extremely scalable plan while offering low possibility of discussing typical important factors. We recommend an
improved unital-based key pre-distribution plan to be able to improve the system scalability while keeping a good key
discussing possibility. We confirm that sufficient option of our remedy parameter should assurance high key discussing
possibility roughly reduced surrounded by 1-e-1hile ensuring high system scalability. We analyze and compare
our new approach against main existing schemes, with respect to different criteria: storage space expense, power intake,
system scalability, protected connectivity coverage, average protected path length and system resiliency. The obtained
results display that our remedy enhances the system scalability while providing good overall system activities.
Moreover, we display that at equal system size, our remedy reduces significantly the storage space expense and thereby
the power intake. |
II. POSITION-BASED OPPORTUNISTIC ROUTING |
2.1 Overview |
| The design of POR is depending on geographical redirecting and opportunistic sending. The nodes are believed to be
aware of their own place and the roles of their immediate others who live nearby. Community place details can be
interchanged using one-hop shining example or piggyback in the details packet’s headlines. While for the place of the
place, we believe that a place signing up and search assistance which charts node details to places is available just as in
. It could be noticed using many types of place assistance. In our situation, some effective and effective way is also
available. For example, the place of the place could be passed on by low bit rate but long variety receivers, which can
be applied as regular shining example, as well as by responses when asked for by the resource. When a resource node
wants to deliver a bundle, it gets the place of the place first and then connects it to the bundle headlines. Due to the
place node’s activity, the multiple hop direction may diverge from the true place of the ultimate place and a bundle
would be decreased even if it has already been provided into the area of the place. To deal with such issue, additional
examine for the place node is presented. At each hop, the node that sends the bundle will examine its next door
neighbor list to see whether the place is within its transmitting variety. If yes, the bundle will be straight sent to the
place, just like the place location forecast plan described in. By executing such recognition examine before selfish
sending depending on place details, the impact of the direction divergence can be very much reduced. In traditional
opportunistic sending, to have a bundle obtained by several applicants, either IP passed on or an incorporation of
redirecting and MAC method is implemented. The former is vulnerable to MAC accident because of the deficiency of
accident prevention assistance for passed on bundle in current 802.11, while the latter needs complicated
synchronization and is not easy to be applied. In POR, we use identical plan as the MAC multicast method described
in. The bundle is passed on as unicast (the best forwarder which makes the biggest positive improvement toward the place is set as the next hop) in IP part and several wedding celebration is obtained using MAC interception. The use of
RTS/CTS/DATA/ACK considerably decreases the accident and all the nodes within the transmitting variety of the
emailer can eavesdrop on the bundle efficiently with higher possibility due to method booking. |
2.2 Selection and Prioritization of Forwarding Candidates |
| One of the key issues in POR is the choice and prioritization of sending applicants. Only the nodes in the sending place
would get the opportunity to be back-up nodes. The sending place is identified by the emailer and the next hop node. A
node in the sending place meets the following two conditions: 1) it creates beneficial improvement toward the
destination; and 2) its variety to the next hop node should not surpass 50 percent of the transmitting variety of a wi-fi
node (i.e., R=2) so that preferably all the sending applicants can listen to from one another. In Fig. 1, the place
surrounded by the strong bend is identified as the sending place. The nodes in this place, besides node A (i.e., nodes B,
C), are prospective applicants. According to the needed variety of back-up nodes, some (maybe all) of them will be
chosen as sending applicants. The concern of a sending applicant is made the decision by its variety to the location. The
closer it is to the location, the greater concern it will get. When a node delivers or delivers a bundle, it chooses the next
hop forwarder as well as the sending applicants among its others who live nearby. The next hop and the applicant
record consist of the forwarder record. Criteria 1 reveal the process to choose and focus on the forwarder record. The
applicant record will be connected to the bundle headlines and modified hop by hop. Only the nodes specified in the
applicant record will act as sending applicants. The reduced the catalog of the node in the applicant record, the greater |
 |
| concern it has. |
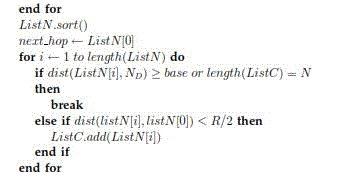 |
| Every node preserves a sending desk for the packages of each circulation (identified as source-destination pair) that it
has sent or submitted. Before determining a new forwarder record, it looks up the sending table; an example is shown
in Table 1, to examine if a real product for that location is still available. The sending desk is designed during details
bundle signals and its servicing is much simpler than a redirecting desk. It can be seen as a trade-off between
performance and scalability. As the organization of the sending desk only relies on regional details, it requires much
less a chance to be designed. |
2.3 Restriction on Possible Copy Relaying |
| Due to accident and nodes’ activity, some sending applicants may don't succeed to get the bundle submitted by the next
hop node or greater concern applicant, so that a certain quantity of duplicate sending would happen. If the sending
applicant assumes the same sending situation as the next hop node, which indicates it also determines an applicant
record, then in the most severe, the reproduction place of a bundle will protect the whole group including the location
as the middle and the range can be as huge as the range between the resource and the location. |
III. SCHEME DESCRIPTION |
| This section describes the details of Mona including system initialization, customer registration, customer revocation,
computer file generation, computer file deletion |
3.1 System Initialization |
| The group manager takes charge of system initialization as follows: |
Generating a bilinear map group system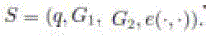 |
 |
3.3 User Revocation |
| User revocation is performed by the group manager via a public available revocation list (RL), based on which group
members can encrypt their data files and ensure the confidentiality against the revoked users. As illustrated in Table 1, |
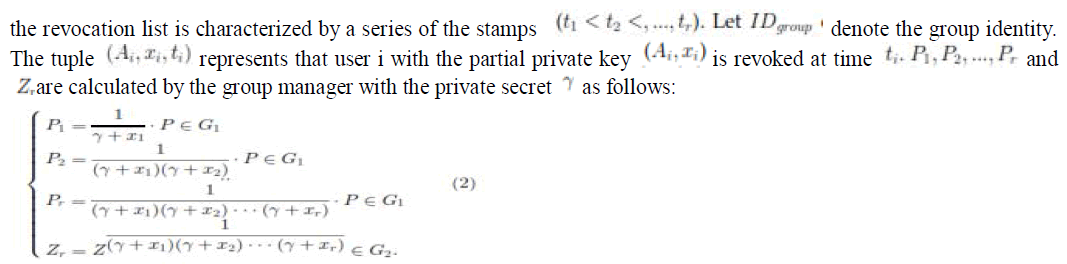 |
| Inspired by the proven response procedure in [19], to assurance that customers acquire the newest edition of the
cancellation record, we let the team manger upgrade the cancellation record each day even no customer has being
suspended in the day. In other terms, the others can confirm the quality of the cancellation record from the included
current date .In addition; the cancellation record is surrounded by a trademark sig(R, L) to announce its credibility. The
trademark is produced by the team administrator with the BLS trademark criteria [20],
.Finally, the group manager migrates the revocation list into the cloud for public usage. |
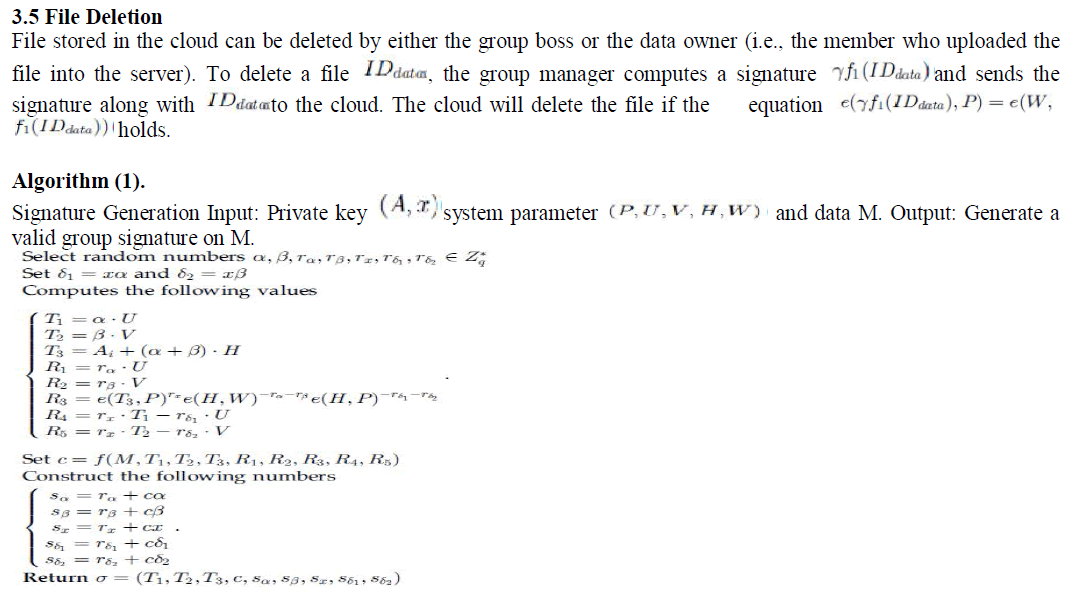
3.4 File Generation |
| To store and share a data file in the cloud, a group member performs the following operations: |
| 1. Getting the revocation list from the cloud. In this step, the member sends the group identity as a request to
the cloud. Then, the cloud responds the revocation list RL to the member. |
2. Verifying the validity of the received revocation list. First, checking whether the marked date is fresh. Second,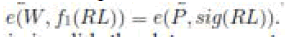 verifying the contained signature sig(RL) by the equation If the revocation list is
invalid, the data owner stops this scheme.
3. Encrypting the data file M. This encryption process can be divided into two cases according to the revocation list. verifying the contained signature sig(RL) by the equation If the revocation list is
invalid, the data owner stops this scheme.
3. Encrypting the data file M. This encryption process can be divided into two cases according to the revocation list. |
 |
 |
IV. PROPOSED CP-ABE SCHEME WITH VERIFIABLE OUTSOURCED DECRYPTION |
| In this section, we first propose a new CP-ABE scheme utilizing Waters’ CP-ABE scheme [4], which is proven to be
selectively CPA-secure. Then, based on the scheme, we propose a CP-ABE scheme with outsourced decryption and
prove that it is selectively CPA-secure and verifiable in the standard model. |
A. New CP-ABE Scheme |
| Before presenting our new CP-ABE scheme, we give some intuitions of our construction. Based on Waters’ CP-ABE
scheme [4], we add to the ciphertext the encryption of an extra random message and a checksum value, which is
computed with this random message and the actual plaintext. We regard this checksum value as a commitment of the
actual plaintext, which can be used to check if the transformation is done correctly in our CP-ABE Scheme with
verifiable outsourced decryption. In fact, using our techniques, we can modify unbounded ABE schemes [7], [33] to
unbounded ABE scheme with verifiable outsourced decryption. |
 |
| The first and second areas are encryptions of concept and a unique concept respectively, using the security criteria of
Waters’ CP-ABE plan [4]. Actually, the second and third areas are repetitive. However, the repetitive areas are the
factor that we can build a CP-ABE with verifiable contracted decryption from the above CP-ABE plan. |
| Theorem 1: Suppose that the construction of Waters [4] is a selectively CPA-secure CP-ABE scheme, then the above
construction of CP-ABE scheme is also selectively CPA-secure. |
| Proof: To prove the selective CPA security of our CP-ABE scheme, we consider the following two games. |
| • The original selectively CPA-secure game of CP-ABE. |
| • Same as except for the way that the challenger generates the challenge ciphertext where the challenger picks randomly and the rest parts of the challenge ciphertext are generated properly as in . |
B. Our CP-ABE Scheme with Verifiable Outsourced Decryption |
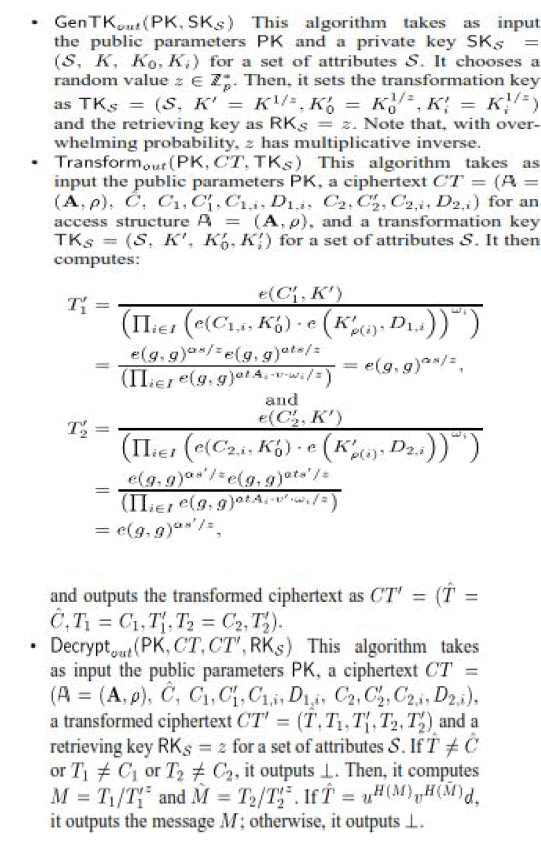 |
| Obviously, the above CP-ABE scheme with outsourced decryption satisfies correctness. In the above construction, a
user runs the algorithm to recover the plaintext from the transformed ciphertext and computation cost incurred by the
user is about three exponentiations, which is far less than the cost of running the algorithm to recover the plaintext from
the original ciphertext directly. The input of algorithm includes the original ciphertext and the transformed ciphertext.
In fact, the user only needs to know to verify the correctness of the transformation done by the cloud. |
| Theorem 2: Assume that
is selectively CPA- secure. Then the above construction of CP-ABE scheme with outsourced decryption is selectively
CPA-secure. |
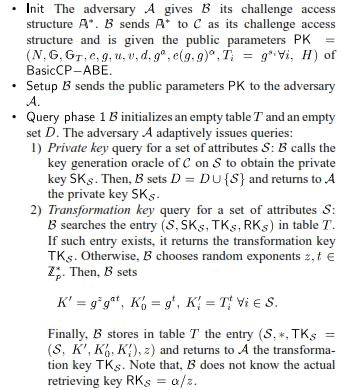
| Proof: Suppose there exists an adversary that can attack the above CP-ABE scheme with outsourced decryption in the
selectively CPA-secure model with nonnegligible advantage. We build an algorithm that can attack the CP-ABE |
| scheme in the selectively CPA-secure model with non negligible advantage. Let be the challenger
corresponding to in the selectively CPA-secure game of the CPABE
scheme runs to execute the following steps. |
 |
| •The adversary A submits two (equal length)
messages and an access structure. A, B sends and A to B to obtain the challenge ciphertext
Then, B sends to the adversary A as its challenge ciphertext. |
| • continues to adaptively issue private key queries as in Query phase 1, and responds the queries as in Query phase 1. |
| • The attacker results a bit also results. So, we develop a criteria that can strike in the precisely CPA-secure design with
non minimal benefits, if can strike the above CP-ABE plan with contracted decryption in the precisely CPA-secure
design with non minimal benefits. |
V. PERFORMANCE EVALUTION |
| In order to evaluate the performance of our CP-ABE scheme with verifiable outsourced decryption presented, we
implement our scheme in software based on the libfenc library [18] and using a 224-bit MNT elliptic curve from the
Stanford Pairing-Based Crypto library [34]. Although our implementation based the MNT curve implies the use of
asymmetric pairing; only a small change need to be made on our scheme of symmetric setting in the implementation. Specifically, suppose that an asymmetric pairing takes elements from and as inputs. Then, according to the description of our scheme in Section, we generate two’s, one from and another from , and compute two corresponding. We further
set as group elements in .As a consequence, among the ciphertext and private key components,
are group elements in while are group elements. The reason why we
apply our suggested plan using asymmetric coupling is that: compared to symmetrical combinations, asymmetric
combinations are much quicker and more lightweight to apply [35]–[37]. We gather our rule on two devoted
components platforms: |
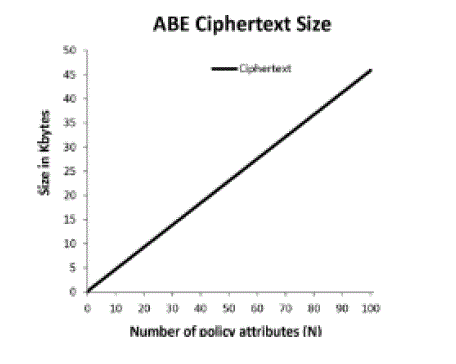
| Discussion: The ABE ciphertext size and decryption/transformation time increase linearly as the ciphertext policy’s
complexity grows. An encryption under a ciphertext policy with 100 attributes results in an ABE ciphertext of nearly
46 KB and it takes about 5 seconds for the Intel platform to decrypt this ciphertext. On the other hand, decryptio The
ABE ciphertext size and decryption/transformation time increase linearly as the ciphertext policy’s complexity grows.
An encryption under a ciphertext policy with 100 attributes results in an ABE ciphertext of nearly 46 KB and it takes
about 5 seconds for the Intel platform to decrypt this ciphertext. On the other hand, decryption time degrades
considerably on the ARM platform: it requires more than 1 second to decrypt a ciphertext under a policy with one
attribute, 5 seconds under a policy with ten attributes and almost 50 seconds under a policy with one hundred attributes.
As expected, outsourcing substantially reduces the computation time required for devices with limited computing
resource to recover the plaintext. The bulk of the decryption operation is now handled by the proxy. The transformed
ciphertext is not only much efficient to decrypt but also much smaller in size. In our implementation, each partiallydecrypted
ciphertext has a constant size of 392 bytes, regardless the complexity of its corresponding ciphertext policy.
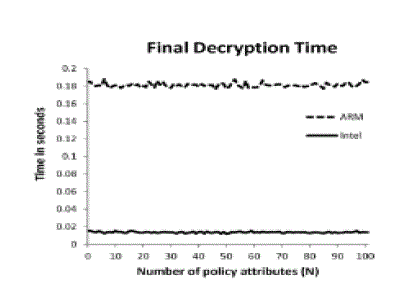
The final decryption and verification of the transformed ciphertext requires only 13 milliseconds on the Intel platform
and approximately 180 milliseconds on the ARM platform n time degrades considerably on the ARM platform: it
requires more than 1 second to decrypt a ciphertext under a policy with one attribute, 5 seconds under a policy with ten
attributes and almost 50 seconds under a policy with one hundred attributes. As expected, outsourcing substantially
reduces the computation time required for devices with limited computing resource to recover the plaintext. The bulk of the decryption operation is now handled by the proxy. The transformed ciphertext is not only much efficient to decrypt
but also much smaller in size. In our implementation, each partially-decrypted ciphertext has a constant size of 392
bytes, regardless the complexity of its corresponding ciphertext policy. The final decryption and verification of the
transformed ciphertext requires only 13 milliseconds on the Intel platform and approximately 180 milliseconds on the
ARM platform. |
CONCLUSION |
| In this paper, we design a secure information discussing plan, Mona, for powerful groups in an untrusted reasoning. In
Mona, a customer is able to work together with others in the group without exposing identification comfort to the
reasoning. Additionally, Mona facilitates effective customer cancellation and new customer becoming a member of.
More specially, effective customer cancellation can be carried out through a public cancellation list without upgrading
the private important factors of the staying customers, and new customers can directly decrypt data files saved in the
reasoning before their contribution. Moreover, the storage expense and the security calculations cost are continuous.
Comprehensive studies show that our suggested plan meets the preferred security requirements and assures
performance as well. |
Figures at a glance |
 |
 |
| Figure 1 |
Figure 2 |
|
|
References |
- A. Sahai and B. Waters, âÃâ¬ÃÅFuzzy identity-based encryption,âÃâ¬Ã in Proc. EUROCRYPT, 2005, pp. 457âÃâ¬Ãâ473.
- V. Goyal, O. Pandey, A. Sahai, and B. Waters, âÃâ¬ÃÅAttribute-based encryption for fine-grained access control of encrypted data,âÃâ¬Ã in Proc. ACM Conf. Computer and Communications Security, 2006, pp. 89âÃâ¬Ãâ98.
- R.Ostrovsky,A.Sahai,andB.Waters,âÃâ¬ÃÅAttribute-basedencryption with non-monotonic access structures,âÃâ¬Ã in Proc. ACM Conf. Computerand Communications Security, 2007, pp. 195âÃâ¬Ãâ203.
- B. Waters, âÃâ¬ÃÅCiphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization,âÃâ¬Ã in Proc. Public Key Cryptography, 2011, pp. 53âÃâ¬Ãâ70.
- A. B. Lewko, T. Okamoto, A. Sahai, K. Takashima, and B. Waters, âÃâ¬ÃÅFully secure functional encryption: Attribute-based encryption and (hierarchical) inner product encryption,âÃâ¬Ã in Proc. EUROCRYPT, 2010, pp. 62âÃâ¬Ãâ91.
- T. Okamoto and K. Takashima, âÃâ¬ÃÅFully secure functional encryption with general relations from the decisional linear assumption,âÃâ¬Ã in Proc. CRYPTO, 2010, pp. 191âÃâ¬Ãâ208.
- A. B. Lewko and B. Waters, âÃâ¬ÃÅUnbounded HIBE and attribute-based encryption,âÃâ¬Ã in Proc. EUROCRYPT, 2011, pp. 547âÃâ¬Ãâ567.
- J. Bethencourt, A. Sahai, and B. Waters, âÃâ¬ÃÅCiphertext-policy attribute- based encryption,âÃâ¬Ã in Proc. IEEE Symp. Security and Privacy, 2007, pp. 321âÃâ¬Ãâ334.
- L. Cheung and C. C. Newport, âÃâ¬ÃÅProvably secure ciphertext policy ABE,âÃâ¬Ã in Proc. ACM Conf. Computer and Communications Security, 2007, pp. 456âÃâ¬Ãâ465.
- N. Attrapadung, J. Herranz, F. Laguillaumie, B. Libert, E. de Panafieu, and C. RÃÆàfols, âÃâ¬ÃÅAttribute-based encryption schemes with constant-size ciphertexts,âÃâ¬Ã Theor. Comput. Sci., vol. 422, pp. 15âÃâ¬Ãâ38, 2012.
- S. Hohenberger and B. Waters, âÃâ¬ÃÅAttribute-based encryption with fast decryption,âÃâ¬Ã in Proc. Public Key Cryptography, 2013, pp. 162âÃâ¬Ãâ179.
- M. Green, S. Hohenberger, and B. Waters, âÃâ¬ÃÅOutsourcing the decryption of ABE ciphertexts,âÃâ¬Ã in Proc. USENIX Security Symp., San Francisco,CA,USA, 2011.
- M. Bellare and P. Rogaway, âÃâ¬ÃÅRandom oracles are practical: A paradigm for designing efficient protocols,âÃâ¬Ã in Proc. ACM Conf. Computer and Communications Security, 1993, pp. 62âÃâ¬Ãâ73.
- R. Canetti, O. Goldreich, and S. Halevi, âÃâ¬ÃÅThe random oracle methodology, revisited (preliminary version),âÃâ¬Ã in Proc. STOC, 1998, pp. 209âÃâ¬Ãâ218.
- J. B. Nielsen, âÃâ¬ÃÅSeparating random oracle proofs from complexity theoretic proofs: The non-committing encryption case,âÃâ¬Ã in Proc. CRYPTO, 2002, pp. 111âÃâ¬Ãâ126.
- S. Goldwasser and Y. T. Kalai, âÃâ¬ÃÅOn the (in)security of the fiat-shamir paradigm,âÃâ¬Ã in Proc. FOCS, 2003, pp. 102âÃâ¬Ãâ113.
- M. Bellare, A. Boldyreva, and A. Palacio, âÃâ¬ÃÅAn uninstantiable randomoracle-model scheme for a hybrid-encryption problem,âÃâ¬Ã in Proc. EUROCRYPT, 2004, pp. 171âÃâ¬Ãâ188.
- Green, A. Akinyele, and M. Rushanan, Libfenc: The Functional Encryption Library.
- R. Gennaro, C. Gentry, and B. Parno, âÃâ¬ÃÅNon-interactive verIfiable computing: Outsourcing computation to untrusted workers,âÃâ¬Ã in Proc. CRYPTO, 2010, pp. 465âÃâ¬Ãâ482.
- K.-M. Chung, Y. T. Kalai, and S. P. Vadhan, âÃâ¬ÃÅImproved delegation of computation using fully homomorphic encryption,âÃâ¬Ã in Proc. CRYPTO, 2010, pp. 483âÃâ¬Ãâ501.
- C. Gentry, âÃâ¬ÃÅFully homomorphic encryption using ideal lattices,âÃâ¬Ã in Proc. STOC, 2009, pp. 169âÃâ¬Ãâ178.
- C. Gentry and S. Halevi, âÃâ¬ÃÅImplementing gentryâÃâ¬Ãâ¢s fully-homomorphic encryption scheme,âÃâ¬Ã in Proc. EUROCRYPT, 2011, pp. 129âÃâ¬Ãâ148.
- B. Parno, M. Raykova, and V. Vaikuntanathan, âÃâ¬ÃÅHow to delegate and verify in public: Verifiable computation from attribute-based encryption,âÃâ¬Ã in Proc. TCC, 2012, pp. 422âÃâ¬Ãâ439.
- S. Goldwasser, Y. T. Kalai, R. A. Popa, V. Vaikuntanathan, and N. Zeldovich, âÃâ¬ÃÅSuccinct functional encryption and applications: Reusable garbled circuits and beyond,âÃâ¬Ã IACR Cryptology ePrint Archive, vol. 2012, p. 733, 2012.
- B. Chevallier-Mames, J.-S. Coron, N. McCullagh, D. Naccache, and M. Scott, âÃâ¬ÃÅSecure delegation of e lliptic-curve pairing,âÃâ¬Ã in Proc. CARDIS, 2010, pp. 24âÃâ¬Ãâ35.
- B. G. Kang, M. S. Lee, and J. H. Park, âÃâ¬ÃÅEfficient delegation of pairing computation,âÃâ¬Ã IACR Cryptology ePrint Archive,vol.2005,p.259, 2005.
- P. P. Tsang, S. S. M. Chow, and S. W. Smith, âÃâ¬ÃÅBatch pairing delegation,âÃâ¬Ã in Proc. IWSEC, 2007, pp. 74âÃâ¬Ãâ90.
- M. Blaze, G. Bleumer, and M. Strauss, âÃâ¬ÃÅDivertible protocols and atomic proxy cryptography,âÃâ¬Ã in Proc. EUROCRYPT, 1998, pp. 127âÃâ¬Ãâ144.
- G. Ateniese, K. Fu, M. Green, and S. Hohenberger, âÃâ¬ÃÅImproved proxy re-encryption schemes with applications to secure distributed storage,âÃâ¬Ã in Proc. NDSS,SanDieg o, CA, USA, 2005.
- A. Beimel, âÃâ¬ÃÅSecure Schemes for Secret Sharing and Key Distribution,âÃâ¬Ã Ph.D. dissertation, Israel Inst. of Technology, Technion City, Haifa, Israel, 1996.
- A. B. Lewko and B. Waters, âÃâ¬ÃÅDecentralizing attribute-based encryption,âÃâ¬Ã in Proc. EUROCRYPT, 2011, pp. 568âÃâ¬Ãâ588. [32]
- R. Canetti, H. Kra wczyk, and J. B. Nielsen, âÃâ¬ÃÅRelaxing chosen-ciphertext security,âÃâ¬Ã in Proc. CRYPTO, 2003, pp. 565âÃâ¬Ãâ582.
- T. Okamoto and K. Takashima, âÃâ¬ÃÅFully secure unbounded inner-product and attributebased encryption,âÃâ¬Ã in Proc. ASIACRYPT, 2012, pp. 349âÃâ¬Ãâ366.
- B. Lynn, The Stanford Pairing Based Crypto Library.
- S. Chatterjee and A. Menezes, âÃâ¬ÃÅOn cryptographic protocols employing asymmetric pairingsâÃâ¬ÃâThe role of revisited,âÃâ¬Ã Discrete Appl. Math., vol. 159, no. 13, pp. 1311âÃâ¬Ãâ1322, 2011.
- SD.Galbrith,K.G.Paterson,andN.P.Smart,âÃâ¬ÃÅPairingsforcryptographers,âÃâ¬Ã Discrete Appl. Math., vol. 156, no. 16, pp. 3113âÃâ¬Ãâ3121, 2008.
- N. P. Smart and F. Vercauteren, âÃâ¬ÃÅOn computable isomorphisms in efficient asymmetric pairing-based systems,âÃâ¬Ã Discrete Appl. Math., vol. 155, no. 4, pp. 538âÃâ¬Ãâ547, 2007.
|