Keywords
|
| Delay Tolerant Networks (DTN); Epidemic; Bundle Protocol; Prophet; Store-Carry-Forward, contact. |
I.INTRODUCTION
|
| The Delay-Disruption Tolerant Network communication model can also be used in Wireless (Terrestrial) environments, both in Military and Civilian applications. Communication network realize straight forward thing recently, but it is still very difficult to transmit data in some networks in presence of delay and interruption. To avoid the issue many researchers have proposed many solutions over the last few years. However, such approaches are not feasible in some specific cases, which resulted in a concept of DTN. Its routing protocols based on the knowledge of end-to-end paths perform poorly, and numerous opportunistic routing algorithms have been proposed. Nodes must have enough processing power and storage to keep data until another good intermediate carrier node or the destination is found, following a store-carry-and forward (SCF) paradigm[1]. In DTNs, communication opportunities are not entirely random, which means that communication patterns (e.g., such as time of last encounter between two nodes) can be used to attempt inferring future contact opportunities as well as to exploit node mobility in order to achieve a fast delivery of data by flooding the network (e.g., Epidemic [8]). Similar results can be achieved by controlling flooding based on: i) delivery probability optimizations (e.g., Spray and Wait [7]); ii) history of encounters (e.g., PROPHET [4]); priority (e.g., MaxProp[2]); future prediction (e.g., EBR [5]). |
II. EMPIRICAL REVIEW
|
| E. Ayday, H. Lee, and F. Fekri [9] in this paper Delay Tolerant Networks (DTNs) have been identified as one of the key areas in the field of wireless communications. They are characterized by large end-to-end communication latency and the lack of end-to-end path from a source to its destination. Our main objective in this paper is to develop a robust trust mechanism and an efficient and low cost malicious node detection technique for DTNs. Inspired by our recent results on reputation management for online systems and e-commerce, we developed an iterative malicious node detection mechanism for DTNs which is far more effective than existing techniques. Our results indicate the proposed scheme provides high data availability and packet-delivery ratio with low latency in DTNs under adversary attacks. |
| E. Ayday, H. Lee, and F. Fekri [10] in this paper, Delay/Disruption Tolerant Networks (DTNs) have been identified as one of the key areas in the field of wireless communication, wherein sparseness and delay are particularly high. Our main objective in this paper is to develop a robust trust mechanism and an efficient and low cost malicious node detection technique for DTNs. Inspired by our recent results on reputation management for online systems and ecommerce, we develop an iterative malicious node detection mechanism for DTNs referred as ITRM. The proposed scheme is a graph-based iterative algorithm motivated by the prior success of message passing techniques for decoding low-density parity-check codes over bipartite graphs. Applying ITRM to DTNs for various mobility models. |
| J. Burgess, B. Gallagher, D. Jensen this paper presents Disruption-tolerant networks (DTNs) attempt to route network messages via intermittently connected nodes. Routing in such environments is difficult because peers have little information about the state of the partitioned network and transfer opportunities between peers are of limited duration. In this paper, we propose MaxProp, a protocol for effective routing of DTN messages. MaxProp is based on prioritizing both the schedule of packets transmitted to other peers and the schedule of packets to be dropped. These priorities are based on the path likelihoods to peers according to historical data and also on several complementary mechanisms, including acknowledgments, a head-start for new packets, and lists of previous intermediaries. Our evaluations show that MaxProp performs better than protocols that have access to an oracle that knows the schedule of meetings between peers. Our evaluations are based on 60 days of traces from a real DTN network we have deployed on 30 buses. |
| J.H. Cho, A. Swami in paper managing trust in a distributed Mobile Ad Hoc Network (MANET) is challenging when collaboration or cooperation is critical to achieving mission and system goals such as reliability, availability, scalability, and reconfigurability. We seek to combine the notions of "social trust" derived from social networks with "quality-of-service (QoS) trust" derived from information and communication networks to obtain a composite trust metric. We discuss the concepts and properties of trust and derive some unique characteristics of trust in MANETs, drawing upon social notions of trust. We provide a survey of trust management schemes developed for MANETs and discuss generally accepted classifications, potential attacks, performance metrics, and trust metrics in MANETs. Finally, we discuss future research areas on trust management in MANETs based on the concept of social and cognitive networks. |
III.STRUCTURAL DESIGN OF DELAY TOLERANT NETWORK
|
| The structural design of DTN is designed in such a way that it counters most of the assumptions and conditions that traditional TCP/IP based networks are based on[3]. DTN architecture is based on following design principles: |
| - Use variable-length (possibly long) messages (not streams or limited-sized packets) as the communication abstraction to help enhance the ability of the network to make good scheduling/path selection decisions when possible. |
| - Use a naming syntax that supports a wide range of naming and addressing conventions to enhance interoperability. |
| - Use storage within the network to support store-and-forward operation over multiple paths, and over potentially long timescales[6] (i.e., to support operation in environments where many and/or no end-to-end paths may ever exist); do not require end-to-end reliability. |
| - Provide security mechanisms that protect the infrastructure from unauthorized use by discarding traffic as quickly as possible. |
| - Provide coarse-grained classes of service, delivery options, and a way to express the useful lifetime of data to allow the network to better deliver data in serving the needs of applications. |
a. Concept of Bundle Protocol
|
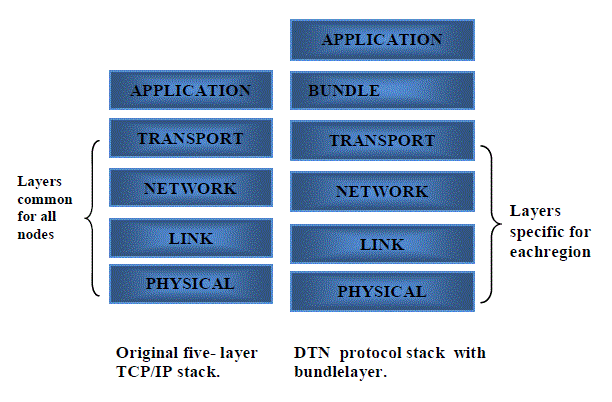
| A Delay Tolerant Network can be considered as an overlay on the existing regional networks. This overlay is called as the bundle layer. This layer is intended to function above the existing protocol layers and provide the function of a gateway when two nodes come in contact with each other[6]. The main advantage of this kind of protocol is flexibility. It can be easily linked with the already existing TCP/IP protocol networks or can be used to link two or more networks together. The position of the bundle layer can be seen in the following fig. 2. |
| Bundles are also called as messages. The main advantage of this kind of protocol is flexibility. It can be easily linked with the already existing TCP/IP protocol networks or can be used to link two or more networks together. The transfer of data from one node to another can be made reliable by storing and forwarding entire bundles between nodes. The bundles comprise of three things, source node’s user-data, control information (e.g., source node ID, destination node ID, TTL etc.), a bundle header. Besides Bundle transfer, custody transfer is also done. The custodian node for a bundle keeps the message until it is successfully transferred to the next node and it takes the custody for that message or until the TTL of the message expires. |
b. Store and Forward Technique
|
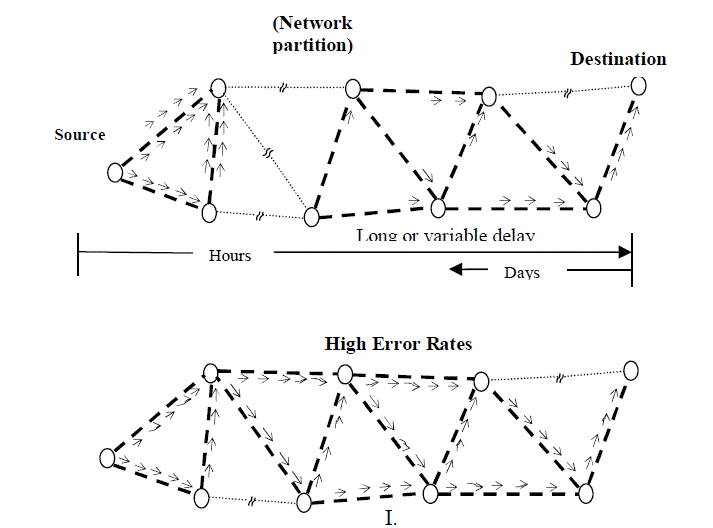
| Delay Tolerant Networks have overcome the problems associated with the conventional protocols in terms of lack of connectivity, irregular delays, asymmetric bidirectional data rates etc. using the concept of store and forward. The method of store and forward is very analogous to the real life postal service. Every letter has to pass through a set of post offices; here it is processed and forwarded, before reaching the destination. Here the complete message or a chunk of it is transferred and stored in nodes successively until it reaches the destination. The following figure (fig. 3), gives a rough graphical representation of how a message is propagated through a network. |
c. APPLICATIONS OF DTN
|
| 1. Terrestrial Mobile Networks: These may include, for example, a limited-power RFtransceiver equipped bus, which travels around the city providing opportunistic communication capability to nodes that happen to be within its transmission radius. Such networks may suffer from frequent disconnection, due to node mobility and RF interference. |
| 2. Exotic Media Networks: These networks include near-Earth satellite communications, free-space optical communication and underwater acoustic links. Link delay may be high in such scenarios because of lossy links, as well as large RTTs. |
| 3. Military Ad-hoc Networks: These frequently consist of several mobile nodes deployed on the battlefield. Seamless communication may not always be possible in such networks because of hostile elements such as intentional jamming or simply, node failures. |
| 4. Sensor Networks: These networks are characterized by a high volume of nodes with only limited power and processing capability. Again, these nodes are susceptible to failure due to power outages, or low-duty cycle functioning. |
IV.METHODOLOGY
|
| The Routing protocols in opportunistic networks, deal with knowledge and phenomena in many fields, which cannot be clearly just by true or false. Using decision based fuzzy knowledge to process can improve the describing ability for fuzzy knowledge, and can grasp the essential meaning of fuzzy knowledge. For using the nature of opportunistic networks parameters such as the Message Transmitted Count of nodes, Message Size and Time To Live to calculate the importance of message. Due to ambiguity and uncertainty of opportunistic network environment a fuzzy based protocol is proposed to find the destination node in shortest time with less buffer usage. |
| Fuzzy-spray can reduce overall latency in DTN by intelligently selecting appropriate messages to send to the relay-node during its next contact time. It uses fuzzy logic to prioritize messages that are stored in the buffer, based only on local parameters from each message, namely forward transmission count and message size. There is no need to know a priori information about network such as node mobility model, or node-distribution across the deployed area. The simulation results show that fuzzy-spray has the best performance in terms of overall speed of delivery, and lowest average message delay compared with other existing algorithms. |
| The protocol is based on two parameters: the Forward Transmission Count (FTC) and the message size. These parameters are input to a fuzzy rule which prioritizes the messages to be transmitted. Selected messages are broadcast to all the neighbors. The forwarding and replication techniques are the same as Epidemic (always and unlimited). The queue management is destination independent and is based on the message priority. |
MESSAGE TRANSMITTED COUNT
|
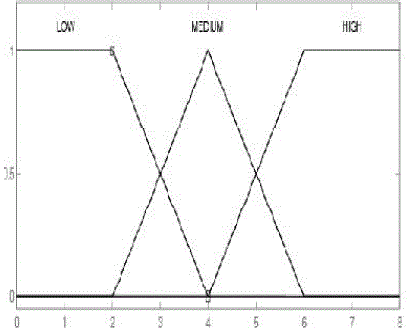
| In Fuzzy-Spray protocol, Forward Transmission Count or FTC was proposed in order to prioritize messages in buffer of nodes. In Decision we used the same concept to calculate the copies of message in the network. This parameter is increased when the nodes exchanges their messages so it is approximately show the number of message transmission in the network. The value of MTC is as same as FTC but the membership function had been defined again and it is depicted in Fig.4 |
MESSAGE SIZE (MS)
|
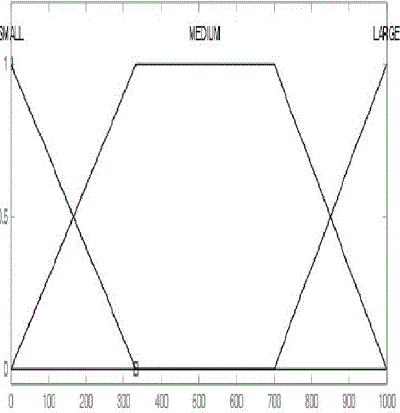
| Since that most nodes of the mobile network nodes or devices have limited buffer size and the size of message is very important so we considered it as input parameters as same as Fuzzy Spray Protocol but there is some deference in the member ship function which is defined as Fig.5. |
MEMBERSHIP FUNCTIONS OF INPUT VARIABLES
|
| The membership function of FTC is low, medium and high, with linear symmetric shape. Figure 5 illustrates the degree of membership function of FTC for 200 nodes DTN. The most important problem of fuzzy logic is to define the appropriate ranges for each input. We run simulation in different environments in order to investigate appropriate ranges, in terms of percentage of network nodes, for any arbitrary size of DTN network. We found that the maximum number of FTC is about 12% of number of nodes, for various network sizes from 40 to 200 nodes. |
V.CONCLUSION
|
| Delay-tolerant networks are a new development in network research, the hope of connecting people and devices that hitherto were either unable to communicate, only at great cost. In this paper we have surveyed existing techniques for routing in such networks.We will investigate ways amount of changes per fits best under the instantaneous conditions with their features such as intermittent connectivity, resource limitation and high delay. The fuzzy membership functions can be adaptively constructed based on known network parameters. The fuzzy decision mechanism is very simple compared to complex prediction mechanisms used in many other DTN protocols. |
| |
Figures at a glance
|
 |
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
Figure 5 |
|
References
|
- Artemios G. Voyiatzis, “A survey of delay – disruption tolerant networking applications”, Journal of Internet engineering, Vol 5 no 1, pp: 331-343, June 2012.
- J. Burgess, B. Gallagher, D. Jensen, B. N. Levine, Maxprop: Routing for vehicle-based disruption-tolerant networks, in: Proceedings ofINFOCOM, Barcelona, Spain, April, 2006.
- V. Cerf, S. Burleigh, A. Hooke, L. Torgerson“Delay-Tolerant Networking Architecture” Network Working Group Google/Jet PropulsionLaboratory, April 2007
- K. Fall, “A Delay-Tolerant Network Architecture for challenged Internets,” proc. Of Annual conf. of the special Internet Group on DataCommunication(ACMSIGCOMM’03),pp.27-34,Aug.2003.
- E.P.C.Jones and P.A.S. Ward,”Routing Strategies for Delay-Tolerant Network,”submitted to computer communication Review(underreview),2008 .
- Lloyd Wood, et. al, “Use of Delay Tolerant Networking Bundle Protocol from Space”, IAC – 08 – B2.3.10, Global Government Solutions Group,Cisco Systems, UK.
- T. Spyropoulos, K. Psounis, C. S. Raghavendra, Spray and wait: an efficient routing scheme for intermittently connected mobile networks, in:Proceedings of ACM SIGCOMM WDTN, Philadelphia, USA, August, 2005.
- A. Vahdat and D. Becker, “Epidemic routing for partially connected ad hoc networks,” Duke University, Tech. Rep. CS-2000-06, 2000.
- E. Ayday, H. Lee, and F. Fekri, “Trust Management and Adversary Detection for Delay Tolerant Networks,” Proc. Military Comm. Conf., pp.1788-1793, 2010.
- E. Ayday, H. Lee, and F. Fekri, “An Iterative Algorithm for Trust Management and Adversary Detection for Delay Tolerant Networks,” IEEETrans. Mobile Computing, vol. 11, no. 9, pp. 1514-1531, Sept. 2012.
- J. Burgess, B. Gallagher, D. Jensen, and B.N. Levine, “Maxprop: Routing for Vehicle-Based Disruption-Tolerant Networking, “Proc.IEEE INFOCOM,Apr.2006.
|
BIOGRAPHY
|
| B.SHUBASHINI is a Research scholar in Department of Computer Science, Nallamuthu Gounder Mahalingam College, Pollachi. She received her Master of computer science M.Sc (Cs) from Sri Ramakrishna college of arts and science for women , coimbatore under Bharathiar University, Coimbatore. She has presented a paper in National level conference and attended Workshop / Seminar. Her research focuses on mobile computing (Delay tolerant network). |
| Dr. Antony Selvadoss Thanamani is presently working as Professor and Head, Dept of Computer Science, NGM College, Coimbatore, India (affiliated to Bharathiar University, Coimbatore). He has published more than 100 papers in international/ national journals and conferences. He has authored many books on recent trends in Information Technology. His areas of interest include E-Learning, Knowledge Management, Data Mining, Networking, Parallel and Distributed Computing. He has to his credit 24 years of teaching and research experience. He is a senior member of International Association of Computer Science and Information Technology, Singapore and Active member of Computer Science Society of India, Computer Science Teachers Association, New York. |