Keywords
|
| portable ad hoc networks; Group interaction system; consistent communication. |
INTRODUCTION
|
| A mobile ad hoc network is an autonomous collection of mobile nodes that communicate over the wireless link. Due to node mobility, the network topology may change rapidly and unpredictably over time. It does not contain any fixed infrastructure and there is no centralized administration [1]. Each node can act as a router and host. Ad hoc networks are used in wide range of applications like military operations, rescue operations, remote site construction, communication among a group of islands or ships, conferencing without the support of a wired infrastructure, and interactive information sharing [2]. The use of wireless network is exploding as the limiting factors such as adequate bandwidth; machine mass and load, and capability concerns are eliminated or diminished. As a solution, we are initiating to see the plea for small, highly movable devices that exploit wireless communications to organize ad hoc networks that vigorously form, converse and permit data to other wireless users and to wire-based networks, then dissolve. |
| The following are the issues in Ad Hoc Wireless Networks. |
| Medium Access Scheme: The fundamental responsibility of a medium entry control procedure in Ad Hoc Wireless Networks is the distributed arbitration for the shared channel for transmission of packets. |
| Routing: The responsibilities of a Routing Procedure include exchanging the route information; finding a feasible path to a destination based on criteria such as hop length, minimum[7] power required, and lifetime of the wireless link; gathering information about the path breaks; mending the broken paths expending minimum processing power and bandwidth; and utilizing minimum bandwidth. |
| Multicasting: Multicasting plays an important role in the typical applications [4] of Ad Hoc Wireless Networks, namely, alternative pursuit-and-rescue operations and military communication. The indiscriminate measures of nodes change the topology dynamically in an unpredictable manner. |
| Transport Layer Protocols: The main objectives of the transport layer protocols include setting up and maintaining end-toend connections, reliable end-to-end delivery of data packets, flow control, and congestion control. |
| Quality of Service Provisioning: Quality of Service is the performance level of services offered by a service provider or a network to the user. It requires negotiation between the host and the network, resource reservation schemes, precedence scheduling agenda, and call entry control. |
| Self Organization: One very important property that an Ad Hoc Wireless Network should exhibit is organizing and maintaining the network by itself. The major activities that an Ad Hoc Wireless Network is required to perform for selforganization are neighbor discovery, topology organization, and topology reorganization. |
| Security: The security of communication in Ad Hoc Wireless Networks is important, especially in military applications [5]. The lack of any central coordination and shared wireless medium makes them more vulnerable to attacks than wired networks. |
| Addressing and Service Discovery: Addressing and service discovery assume significance in Ad Hoc Wireless Networks due to the absence of any centralized coordinator. Nodes in the network should be able to locate services that other nodes provide. |
| Energy Management: It is defined as the process of managing the sources and consumers of energy in a node or in the network as a whole for enhancing the lifetime of the network. |
| Scalability: Even though the number of nodes in an Ad Hoc Wireless network does not grow in the same magnitude as today’s Internet, we provide a model that reflects the salient properties of the network and propose protocols that support this environment [8]. |
| A.COMMUNICATION ON THE DYNAMIC BATTLEFIELD |
| The modern battlefield is highly dynamic. Units enter and leave and leave the battlefield continuously. The dynamic battlefield demands several characteristics of communications [6]. Some of them are: |
| (1) Fast: While some limited setup may be tolerated before action starts, the ability to communicate during combat should be immediate in its accessibility to the transmitter and its delivery to the recipient. |
| (2) Easy/transparent: The transmitter must be able to communicate with minimal effort apart from their normal battlefield activities. |
| (3) Available: Parties must be able to communicate whenever they need to. |
| (4) Authenticated: The communication initiator must be able to absolutely identify all intended recipients. |
| (5) Private: The communications passed during combat should not be divulged to anyone not intended for receipt. |
| (6) Integrity Protected: Messages must be protected from modification during transmission. |
| (7) Acknowledged: All parties to the communication must know what the other parties did and did not receive. |
| We do not contend that this list is all-inclusive. Further, we recognize the impact of interactions of these requirements and posit that these interactions create the bulk of the complexity involved in secure battlefield communication. |
| B. INTERACTIVE COMMUNICATION ON THE BATTLEFIELD. |
| Modern battlefield doctrine is based on mobility, elasticity and fast response to changing situations, yet also requires close coordination and mutually understood objectives among all members of the [command] group. This demands a group communication paradigm. |
| Group communication [12][6] is sometimes thought of as broadcast technology. Broadcast and group communications are closely related, though not identical. Broadcast technology can provide efficient group communication, though group communication may or may not involve broadcasting messages. The group communications paradigm is preferable over point-to-point connections in such an environment simply from the standpoint of reduced overhead. If the broadcast domains of the group members, the number of transmissions required to fully delivering a group message is minimized. If the broadcast domains are totally overlapping, group messages can be fully delivered with a single transmission. |
| C. CHALLENGES TO MANAGE SECURE GROUPS |
| These criteria are categorized into group membership management, network resource consumption, receiver resource requirements, sender resource requirements and dependency upon particular standards. |
| • Group membership management criteria addresses the concerns of who is and is not part of the group, how the group looks like, and what happens if the group changes. |
| • Network resource consumption criteria are concerned with the load on the network for various stages of the multicast communication process. When analyzing the bandwidth consumption of a solution, it is important to note how many messages must be transmitted each time a member joins or leaves and how large the control messages (those for managing the group) are in relation to the data messages. |
| •Receiver and sender resource requirements consider the following: How many keys must each member or sender store and how large are these keys? What is the processing time involved for the member or sender to, respectively, read or sends messages? Does the solution allow non-members to send data? How many senders are allowed? Must these senders be known in advance of group creation? |
| • Dependence upon standards concern with whether the solution depends upon a particular network protocol or network characteristics such as stability, in order packet delivery, or reliable transmission. |
RELATED WORK
|
| Multicasting [2] is often the most efficient way of achieving point to multipoint communication. Several approaches have been proposed in literature to implement multicasting over MANETs. A classic one (borrowed from the wired Internet) is building a tree that connects all nodes in the multicast group. A different tree can be built for each sender in the group, or a single shared tree can be used to carry messages possibly generated by any node in the group. Tree-based multicasting is very popular in the legacy Internet, but it is questionable whether it is the best approach also for MANETs. Specifically, the intrinsic instability of wireless links makes the tree quite unstable as well, possibly resulting in low delivery rates and high management traffic. To overcome these drawbacks, mesh-based multicasting has been proposed .Group members are not joined by a tree, but by a mesh. This structure is more resilient to link failures and node movements thank to its redundancy, and thus mesh-based multicasting usually achieves higher delivery rates. Both these approaches require nodes to keep some state about the multicast structure. A first argument against this requirement is that both meshes and trees may encompass also node that are not interested in the group, but that have to be member of the structure (and hence keep the state) nevertheless. To overcome this drawback, middleware level solutions have been proposed, in which the mesh or the tree is built on top of an overlay network that just encompasses the intended multicast group members. Even though non group members have possibly to forward traffic for the group, they are not forced to keep the state of the structure anymore. Another advantage of middleware-level solutions is the option of implementing multicast protocols on top of a P2P Distributed Hash Table (DHT). |
| The main idea of this approach is that senders of a multicast group select a random subset of nodes in the group to send data to. The same process is repeated at receiving nodes for a given number of turns, this number and the size of the random subsets being protocol parameters. It has been shown that such protocols are actually able to deliver messages with high probability to all intended receivers .A side effect of gossiping is that the message replication rate is quite difficult to control. Valuating such an approach in comparison with p2p multicasting is an interesting topic which is however out of the scope of this work. |
| Group Communication and Membership: |
| The Group Communication paradigm has already proven to be a useful tool for building reliable distributed systems [6][7]. Decentralized peer-to-peer cooperative environment is the basis for group cooperation in Mobile Adhoc networks [9]. Group of member nodes therein interact and communicate in order to achieve a common goal. A group communication system usually integrates a group membership service with a reliable multicast service. The task of the group membership service is to keep members consistently informed about the current membership of a group by installing views [9]. The formal specification of Members in a group i.e. “nodes” share information, and need a consistent view of that information. Formal specification of group communication is used to define the properties and terminologies [9]. Guaranteed message delivery in group communication needs consistent view of the participating hosts to avoid inconsistencies and mobility induced link failures [11]. To achieve this, nodes need a consistent view of all the other nodes involved in the communication. In this case, geographical location of nodes determines if they can become members of a group. The membership service provides a dynamic view of the current membership to all nodes in the group. |
| The radio ranges of nodes in a group cover a certain geographical area, that is called coverage area or communication range [44]. Nodes have to explicitly issue a request to join a group if it is close enough and within the communication range of each other. When nodes leave the group i.e. when they go out of range and are removed from the group’s membership. The nodes involved in the group communication service are mobile devices, requiring correct handling of frequent topology changes and of a dynamic set of interacting processors. A group membership in an ad hoc mobile network maintains a list of the currently active and connected nodes in the group. When this list changes (with new members joining and old ones departing), the group membership reports the changes to the group members. |
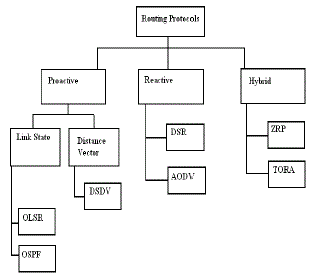
CLASSIFICATION OF ROUTING PROTOCOLS IN MANET
|
| A routing protocol is a protocol that specifies how routers communicate with each other, propagating information and facts that permits them to select routes between any two nodes on a computer network. All routers have a previous realization only of networks attached to it promptly. A routing protocol bonds this information first among immediate neighbors, and then through the linkage. This way, routers acquire knowledge about the topology of the network. |
| Multicast routing protocols [13] for Ad Hoc Wireless Networks can be broadly classified into two types: Application-independent / generic multicast protocols and purpose related multicast protocols. While Applicationindependent multicast protocols are used for conventional multicasting, purpose related multicast protocols are meant only for specific applications for which they are designed. |
| Unicast Routing Protocols |
| • Proactive routing protocols |
| • Reactive routing protocols. |
| A proactive routing protocol is a protocol that is constantly attempting to keep an up-to date routing table by constantly requesting update information from neighboring nodes and sharing routing tables. This means that when a node wishes to send a packet to a destination the route to that destination is already known. The reactive routing protocol only sends requests for a route from the source to the destination when a node wishes to send a packet and there is not a valid route available in the routing table. Hierarchical routing protocols often use clustering techniques to build hierarchical structures on the flat network, where each cluster has a lead node which looks after the cluster and communications with other clusters. |
| Multicast Routing Protocols |
| • Tree based routing protocols |
| • Mesh based routing protocols. |
| A Tree based routing protocol uses a single path from source to destination node. Since there exists a single path, this protocol works efficiently compared to Mesh based multicast routing protocols. |
| A Mesh based routing protocol is formed by having a mesh of nodes in which it uses multiple paths for a source node to reach a destination. Since there are multiple paths available this protocol tends to be a robust one compared to tree based protocols. |
| The following describes some of the Multicast Routing Protocols. |
| A. DIFFERENTIAL DESTINATION MULTICAST ROUTING PROTOCOL |
| L. Ji et al. described [32] the working principle of DDM in which the sources control multicast group membership to ease certain aspects of security administration. A departure from other proposed MANET multicast protocols, DDM encodes the destinations (i.e. the multicast group members to whom the data needs to be delivered). There is no control overhead problem when the group is idle; a characteristic distributed with DSR. Since many multicast applications do not have any efficient traffic flows, it can be expensive in terms of network control overhead to monitor multicast transmitting state in routers during idle periods. In-band control avoids this complexity because if there is no data traffic, there is no necessity for any control information either. It is not necessary for the nodes along the data forwarding routes to maintain multicast transmitting state if it chooses to run under stateless mode. When one intermediate node receives a DDM data packet, it only requires looking at the DDM header to take a decision on how to transmit the packet another similarity to DSR. |
| Secondly, the cost of medium access is high in wireless broadcast networks due to the MAC mechanism and broadcast transmission’s blocking effect to nearby nodes. Although packing information about path route together with data traffic will enlarge data packet size, it minimizes the total number of channel accesses because it diminishes the number of pure control packets developed by the protocol. |
| B. AMRIS: AD HOC MULTICAST ROUTING PROTOCOL UTILIZING INCREASING ID-NUMBERS |
| C. Wu et al. explained the working nature of AMRIS [18] which is an on-demand protocol which constructs a shared delivery tree to support multiple senders and receivers within a multicast session. The key idea that differentiates AMRIS from other multicast routing protocols is that each participant in the multicast session has a session-specific multicast session member id (denoted as msm-id). The msm-id provides each node with the information of its "logical height" in the multicast distribution tree. Each node excluding the root should have one parent that has a logical height (msm-id) that is smaller than it. Each participant calculates its initial msm-id dynamically during the Initialization phase, which is initiated by a special node called Sid, who has the smallest msm-id. Sid is normally elected from among the set of senders if there is more than one. The relationship between the msm-id (and the node that owns it) and Sid (which is also the root of the tree) is that the msm-ids increase in numerical value as they radiate away from Sid. The msm-ids allow nodes that have broken off from the delivery tree (e.g. due to mobility, terrain) to rejoin the delivery tree in a localized fashion without causing permanent routing loops. Another key feature of AMRIS is that it does not depend on the unicast routing protocol to provide routing information to other nodes. AMRIS maintains a Neighbors-Status table which stores the list of existing neighbors’ and their msm-ids. Each node sends a periodic beacon to signal their presence to neighboring nodes. The beacon contains the msm-ids that each node presently has. |
| C. MZRP: MULTICAST ZONE ROUTING PROTOCOL |
| In Multicast Zone Routing Protocol (MZRP) X.Zhang et al. [19] demonstrated the flooding of control packets by each node which searches for members of the multicast group is controlled by using the zone routing mechanism. In zone routing, each node is associated with a routing zone. Table driven or Proactive routing is used within a zone and it is otherwise called as Intra zone routing, whereas a reactive method or on demand routing method is used cross wise in the zones or outside the zone which is otherwise called as Inter zone routing protocol. This protocol combines the best of both ondemand and table-driven routing approaches. Hence it is called as Hybrid routing protocol. |
| In Tree Initialization Phase, it is required to create a multicast delivery tree over the network; the source initiates a two-stage process. In the first stage, the source tries to form the tree inside the zone, and then in the second stage it extends the tree to the entire network. In Tree Maintenance Phase, once the multicast tree is created, the source node periodically transmits TREE-REFRESH packets down the tree to refresh the multicast tree. If any tree node does not receive TREEREFRESH packet within a specific time period, it removes the corresponding stale multicast route entry. MZRP has reduced control overhead as it runs over ZRP. The fact here is unicast and multicast routing protocols can exchange information with each other. MZRP is important as it shows the efficiency of the zone-based approach to multicast routing. The size of the zone is very important in MZRP. The size should be neither too large nor too small. The main disadvantage of this protocol is that a receiver node which is located far off from the source needs to wait for a long time before it can join the multicast session. |
| D. FGMP: FORWARDING GROUP MULTICAST PROTOCOL |
| In a wireless broadcast channel, there is no notion of explicit link interface like in a wired point to point channel Multicast forwarding [20] described by C.Chiang et al. which is based on nodes (routers) which are going to accept multicast packets rather than on links on which multicast packets are forwarded. Traditional multicast protocols based on upstream and downstream links (like CBT, PIM and DVMRP) are not suitable here because creating and maintaining upstream and downstream link status in a wireless network is not efficient. The proposed multicast protocol keeps track not of links but of groups of nodes which participate in multicast packets processing. In a Multicast Group, three broadcasting nodes take the responsibly to forward multicast packets. This scheme can be viewed as “limited scope” flooding. That is, flooding is contained within a properly selected forwarding set. It is interesting to note that with proper selection of the broadcasting group, the Forwarding Group FG scheme can imitate any of the currently available schemes. For example, to produce comprehensive excess flooding, it must include all nodes in the network. For CBT, the FG is constrained to the joints on the shared tree except the leaf nodes. In DVMRP, FG comprises all the non-leaf interconnections on the basis foundation trees. Only single flag and a timer is required for each sending node. When the forwarding (sending) flag is set, each node in FG sends data packets belonging to G until the timer expires. Regardless of member group size, one forwarding flag is sufficient to assure efficient delivery of multicast packets. Storage overhead, a major difficult in conventional multicast protocols, is short, thus expanding the scalability. The soft state approach of using a timer works well in dynamic changing environments. The major problem of FGMP is how to elect and maintain the set FG of forwarding nodes. The size of FG should be as small as possible to reduce wireless channel overhead, and the forwarding path from senders to receivers should be as short as possible to get high throughput. |
| E. CAMP: CORE ASSISTED MESH PROTOCOL |
| J.J.Garcia-Luva-Aceyes et al. described CAMP [21] which was designed to support multicast routing in very dynamic ad hoc networks with broadcast links. It adopts the same basic architecture used in IP multicast. A mapping service is assumed to exist that provides routers with the addresses of groups identified by their names. In the Internet, this facility would be granted by the domain name system (DNS), for instance. Hosts that like to combine a multicast group must first query the mapping service to obtain a group address and then interact with their local routers through Internet Group Multicast Protocol (IGMP) or an equivalent host-to-router protocol to request membership in a multicast group. In addictive to the naming facility consumed by hosts to obtain multicast group addresses, CAMP presumes the accessibility of routing information from a unicast routing protocol. The only need enforced on the routing protocol used is that it must provide correct distances to known destinations within a finite time. CAMP differs from most prior multicast routing protocols in that it builds and maintains a multicast mesh for information distribution within each multicast group. |
| A multicast mesh is a subset of the network topology that provides at least one path from each source to each receiver in the multicast group. CAMP ensures that the shortest paths from receivers to sources are part of a group’s mesh. Packets are directed across the mesh laterally the paths that first reach the routers from the foundation, i.e., the direct paths from sources to receivers that can be defined inside the mesh. CAMP will not indicate such paths along the mesh. A router maintains a cache of the identifiers of those packets it has forwarded recently and forwards a multicast packet received from a neighbor if the packet identifier is not in its cache. Router is the final receiver to combine in the multicast group and does so in the multicast mesh through either router or; consequently, router does not become a member of the mesh. |
| CAMP extends the basic receiver-initiated approach introduced in the Core-Based Tree (CBT) [42] protocol by A.Ballardie et al. for the creation of multicast trees to enable the creation of multicast meshes. Cores are used to limit the control traffic needed for receivers to join multicast groups. In contrast to CBT, one or multiple cores can be defined for each mesh, cores will not be part of the mesh of their group, and routers can combine in a group even if all respected cores become unreachable. A router sends a join request toward a core if none of its neighbors are members of the group; else, it just indicates its membership using either reliable or persistent updates. |
| F. ADMR: ADAPTIVE DEMAND-DRIVEN MULTICAST ROUTING |
| In ADMR , source-based forwarding trees are created whenever there is at least one source and one receiver in the network. ADMR monitors the traffic pattern of the multicast source relevance, and based on that it can identify the link breaks in the tree, as well as sources that became inactive and dead will not be sending any more data. In the former case, the protocol starts local repair procedures and then global repair incase of failure of local repair. In the latter case, multicast processing state is expired smoothly without the requirement to send an explicit shutdown message. To enable maintenance for link breaks in the multicast processing tree when the source refused to send data temporarily, ADMR sends a restricted number of keep-alive at increasing or growing inter-packet times. When the source refused to send any data for a period of time that represents a significant deviation from its sending pattern, the keep-alive stops and the entire tree silently expires. A significant deviation from a source’s sending pattern is an indication that the source is likely to be inactive for a while, in which case it would be wasteful to monitor the routing state in the network. |
| ADMR also prunes individual branches of the tree automatically, when they are not necessary for forwarding. These pruning decisions are based on lack of passive acknowledgements from downstream, instead of relying on the receipt of an explicit prune message. Each multicast data packet is forwarded from the sender to the multicast receivers using MAClayer multicast transmissions along the shortest-delay path between nodes with forwarding state for the group. To deal with partitions, ADMR occasionally sends an existing multicast data packet instead as a network flood, taking the place of the multicast distribution of this existing packet. This data packet flood is used only at infrequent intervals (e.g., once per several tens of seconds) and only when new data is being sent to the given multicast group; in addition, this flood is not a required protocol mechanism and does not represent core functionality. |
| G. SOGR: SELF-ADAPTIVE ON DEMAND GEOGRAPHIC ROUTING |
| X. Xiang et al. demonstrated [33] that there are two Self-adaptive On demands Geographic Routing (SOGR) protocols, in which the route optimization schemes for both the protocols have been introduced. It is assumed that every mobile node is aware of its own position, a source can obtain the destination’s position through some kind of location service, and promiscuous mode is enabled on mobile nodes’ network interfaces. SOGR with Hybrid Reactive Mechanism (SOGR-HR), the next-hop of a forwarding node is determined reactively with the combination of geographic-based and topology-based mechanisms. SOGR with Geographic Reactive Mechanism (SOGR-GR), depends on one-hop neighbors’ positions to make greedy and perimeter forwarding in which it adopts a reactive beaconing mechanism. The periodic beaconing is triggered only when a node overhears data traffic from its neighbors the first time. The beaconing is stopped if no traffic is heard for a pre-defined period. |
| H. GPSR: GREEDY PERIMETER STATELESS ROUTING |
| B. Karp et al. discussed about Greedy Perimeter Stateless Routing (GPSR) [41] which is used for scalability under increasing numbers of nodes in the network, and increasing mobility rate. As these factors increase, the following are the measures of scalability: |
| Routing protocol message cost: It describes the cost for disseminating data packets throughout the network. |
| Application packet delivery success rate: It is described by distributing the application packets in an efficient manner. |
| Per-node state: It demonstrates how much stowage does a routing algorithm require at each node? |
| Networks that push on mobility and number of nodes, or both include: |
| Ad-hoc networks: Perhaps the most examined category is that these mobile networks do not have any fixed infrastructure, and helps for applications like military users, post-disaster rescuers, and temporary collaborations among temporary associates, as at a business conference or lecture. |
| I. GOAFR+: GOPHER-PLUS OUR GEOMETRIC ROUTING ALGORITHM |
| GOAFR+ (pronounced as Gopher-plus") combines similarly to earlier proposals two concepts called greedy routing and face routing. In greedy routing mode the algorithm forwards the routed message at each network node to the neighbor closest to the destination. Already in simple durations, the message can however reach a dead end, a node without any better neighbor. Such cases are overcome by the employment of face routing, which explores the boundaries of faces of the planarized network graph. GOAFR+ uses an early fallback technique to return to greedy routing as soon as possible. It has been shown that additionally restricting its search to an adaptively resized area the algorithm is even more efficient than similar algorithms analyzed earlier on average (random) graphs. Theoretical analysis of these routing algorithms often has to make irritating or far-fetched assumptions, which would hardly ever hold in practice. In this paper, the author is able to drop one such assumption, which assumes that the distance between network nodes cannot fall beneath a constant minimum bound. Graphs with this restriction have also been called civilized or precision graphs in the literature. There is a general notion of a cost metric, defined as a non decreasing function of the length of the edge over which a message is sent. It is shown that the behavior of cost functions for edge length approaching zero proves crucial for the cost of routing. |
| J. LGK: LOCATION GUIDED K-ARY |
| K.Chen et al. described in detail the location-guided LGK [38] and LGS tree construction algorithms, and the location/ membership update mechanism to disseminate location information among a group of nodes. LGK tree formation algorithm provides a k-ary tree rooted at the sender with the group nodes as tree nodes in which packets are transmitted node-by-node along the k-ary tree from the source to the rest of the multicast group via unicast routing. This packet transmitting process is guaranteed loop-less because a destination address will be taken out of the list whenever the packet has reached the final destination. A location-guided k-ary (LGK) tree is constructed by either the sender node selects the nearest k destinations as children nodes, or by grouping the rest of the nodes to the k children according to close geometric proximity, and then it transfers a copy of the packet to each of the k children with its corresponding sub tree as destinations. The location-guided heuristic is greedy in the sense that a packet is always forwarded to the nearest k nodes. This strategy guarantees that in the next step, the k destinations will forward the packet to a set of nodes that are geometrically close to them, and thereby minimizes the overall cost of the packet distribution tree. The fan-out degree k of the LGK tree algorithm plays an important role in deciding the shape of the tree: a small k leads to a long-thin tree; a large k leads to a short-fat tree. The process starts from a sender node in a multicast group. It is assumed that the sender is aware of the members of the group by their network addresses such as IP addresses. It then includes a list of the members as the destinations in every packet it sends out. |
| K. POSTER: POSITION-BASED MULTICAST ROUTING |
| For multicast demonstrated by M.Mauve et al. [39], it is necessary to establish a distribution tree among the nodes, along which packets are forwarded toward the destinations. At the branching points of the tree, copies of the packet are sent along all the branches. The length of the paths to the individual destinations should be minimal and the total number of hops needed to forward the packet to all destinations should be as small as possible. However, with position-based routing, routing decisions are based solely on local knowledge, thus neither the shortest paths to all destinations nor (heuristics for) Steiner trees can be used directly. Instead PBM uses locally available information to approximate the optima for both properties. Given this information the main task of a forwarding node in PBM is to find a set of neighbors that should forward the packet next. These neighbors are called as the next hop nodes. The current node will assign each destination of the packet to exactly one next hop node. Each next hop node then becomes forwarding node for this packet toward the assigned destinations. If the current node selects more than one next hope node, then the multicast packet is split. The most important property of PBM is that each forwarding node autonomously decides how to forward the packet. This decision requires no global distribution structure such as a tree or a mesh. |
| L. SLURP: SCALABLE LOCATION UPDATE-BASED ROUTING PROTOCOL |
| J.Li et al. described [36] an approach for building a scalable routing protocol is to persistently maintain finite location information about nodes in the network and to only find accurate routes to specific nodes when there are packets to be delivered to them, this method is identical to the one adopted in DREAM. Specifically, when a node requires to transmit a packet to some destination, it primarily determines the destination's approximate location and then uses a simple geographic routing protocol to send the packet to the destination. This two phase approach allows us to reduce the cost of maintaining routing information while, simultaneously, providing us the ability to find relatively good routes inexpensively when needed. Thus, SLURP, is based on a combination of approximate geographical routing and a simple static mapping procedure to maintain approximate location information for nodes. |
| M. CBT: CORE BASED TREES |
| A.Ballardie et al. demonstrated CBT [42] which is a shared tree design that was geared towards several design objectives. Many of the source-based tree algorithms are clearly robust; a sender will only transmit the data, and intervening routers combine to get the data where it needs to, creating state through the way. This is the so-called "data driven" method. There is no alternative duplicate protocol involved. It is not as easy to obtain the same level of robustness in shared tree algorithms; a shared tree's core router monitors connectivity among all group members, and is thus a single point of failure. The CBT protocol is relatively simple compared to most other multicast routing protocols. This simplicity can lead to enhanced performance compared to other protocols. The CBT protocol is created to build, design and monitor a shared multicast distribution tree that elaborates only those networks and links which leads to interested receivers. To obtain this, a host initially proposes its interest in combining a group by transmitting an IGMP host membership report throughout its attached link. CBT routers combined with a multi-access link will take part in an explicit election mechanism that elects a single router, the designated router, as the link's upstream router for all groups. Since the designated router may not be the link's suitable next-hop for a particular core router, this may leads to join a message which is being re-directed back through a multi-access link. If this happens, the re-directed message is unicast throughout the link by the designated router to the suitable next-hop, thereby avoiding a looping scenario. When a CBT control message is transmitted over a non-multicast supporting link, it is explicitly taken to the suitable next hop. |
| N. GMP: GEOGRAPHIC MULTICAST ROUTING PROTOCOL: |
| F.Kuhn et al. explained GMP [35] which consists of transmitting nodes that do not require any global knowledge to create a tree which will be used for partitioning the destination nodes into groups and they use only local information during actual route selection. Note that the general Euclidean Steiner tree problem is NP-hard. However, a special case where there are only three nodes, the Steiner point can be calculated efficiently. The progressive nature of the routing scheme enables continuous refinement of the resulting trees, thereby providing better multicast trees than other schemes. In GMP, an efficient Euclidean Steiner tree based geographic multicast routing protocol was proposed. The underlying idea of GMP is that each transmitting node constructs a heuristic Euclidean Steiner tree, including the source and all destinations. The tree is virtual in the sense that it may include interior vertices that do not correspond to any actual wireless sensor nodes. The destinations are divided into groups based on this tree. As in LGS a copy of the packet is then forwarded to a suitable next hop and the process is repeated by the receiving nodes until all destinations are reached. |
| O. EGMP: ENHANCED GEOGRAPHIC MULTICAST PROTOCOL |
| X.Xiang et al. stated in EGMP [31], instead of combining each group member immediately to the tree, the tree is developed in the granularity of zone with the support of location information, which predominantly reduces the tree management problem with a final destination location, a control message can be forwarded directly without expensing a high overhead and delay to identify the path initially, which provides rapid group joining and leaving. However, there are many difficulties in implementing an efficient and well defined robust geographic multicast scheme in MANET. An easiest way to extend the geography based transmission from unicast to multicast is to put the addresses and positions of all the members into the packet header, however, the header overhead delay processing will increase tremendously as the group size increase, which constrains the application of geographic multicasting only to a fixed group. |
| The mobile nodes are handled in square zones for simple destination finding. This partition will help the source node to find the destination node with the help of the coordinate positions ((x1,y1);(x2,y2)). Author has used some of the notations to construct a zone and to elect the leader. The zone leader is elected by its zone members randomly by identifying out the persistent t nodes within a zone. The leader should have the information regarding the zone members. In MANET’s mobile nodes are often dynamically changing its location, the main drawback of the mobile node is, it contains a low capacity to hold the power. That means the mobile nodes or wireless nodes are run with the assistance of the power, if the power get lost then the mobile nodes are not live, these nodes are tentatively crashed or not worked. |
CONCLUSION
|
| In this paper, we have analyzed the different communication protocols which are used to achieve efficient Communication in mobile Adhoc network. However, each protocol has its own advantages as well as its disadvantages making it suitable for some applications and not for others. It is observed that EGMP routing protocol performs with satisfactory results. Our future extension is to achieve reliable communication in VANET. Table 1 summarizes the Interaction protocols, Topology, Initialization and Maintenance Approach of different protocols discussed in this paper. |
Tables at a glance
|
 |
| Table 1 |
|
| |
Figures at a glance
|
 |
| Figure 1 |
|
| |
References
|
- Neha rani, preetisharma and pankaj Sharma” Performance comparison of various routing protocols in different mobility models”. International journal of adhoc, sensor & ubiquitous computing (ijasuc) vol.3, no.4, august 2012.
- Guokai Zeng, , Bo Wang, ,Yong Ding, , Li Xiao, and Matt W. Mutka,, “Efficient Multicast Algorithms for Multichannel Wireless Mesh Networks”, IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS, VOL. 21, NO. 1, JANUARY 2010.
- X. Xiang, Member, IEEE, X. Wang, Member, IEEE, and Y. Yang, Fellow, IEEE “Supporting Efficient and Scalable Multicasting over Mobile Ad Hoc Networks “IEEE TRANSACTIONS ON MOBILE COMPUTING, VOL. 10, NO. 5, APRIL 2011.
- J. J. Garcia-Luna-Acevesand Rolando Menchaca-Mendez , “PRIME: An Interest-Driven Approach to Integrated Unicast and Multicast Routing in MANETs”, IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 19, NO. 6, DECEMBER 2011.
- Shushan Zhao, AkshaiAggarwal, Richard Frost, Xiaole Bai, “A Survey of Applications of Identity-Based Cryptography in Mobile Ad-Hoc Networks”, IEEE COMMUNICATIONS SURVEYS & TUTORIALS, VOL. 14, NO. 2, SECOND QUARTER 2012.
- Quansheng Guan, F. Richard Yu, Shengming Jiang, and Victor C. M. Leung,” Joint Topology Control and Authentication Design in Mobile Ad Hoc Networks with Cooperative Communications”, IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 61, NO. 6, JULY 2012.
- Luo Junhai, Ye Danxia, Xue Liu, and Fan Mingyu, “A Survey of Multicast Routing Protocols for Mobile Ad-Hoc Networks”, IEEE COMMUNICATIONS SURVEYS & TUTORIALS, VOL. 11, NO.1, FIRST QUARTER 2009.
- Xueyuan Su, Sammy Chan, Jonathan H. Manton, “Bandwidth Allocation in Wireless Ad Hoc Networks: Challenges and Prospects”, IEEE Communications Magazine • January 2010 .
- LoayAbusalah, AshfaqKhokhar, and Mohsen Guizani, “A Survey of Secure Mobile Ad Hoc Routing Protocols”, IEEE COMMUNICATIONS SURVEYS & TUTORIALS, VOL. 10, NO. 4, FOURTH QUARTER 2008.
- S.M. Das, H. Pucha, and Y.C. Hu, “Distributed Hashing for Scalable Multicast in Wireless Ad Hoc Network,” IEEE Trans. Parallel and Distributed Systems, vol. 19, no. 3, pp. 347-362, Mar.2008.
- AbdelouahidDerhab and NadjibBadache,” Data Replication Protocols for Mobile Ad-Hoc Networks: A Survey and Taxonomy”, IEEE COMMUNICATIONS SURVEYS & TUTORIALS, VOL. 11, NO. 2, SECOND QUARTER 2009.
- Maurice J. Khabbaz, Chadi M. Assi, and Wissam F. Fawaz,” Disruption-Tolerant Networking: A Comprehensive Survey on Recent Developments and Persisting Challenges”, IEEE COMMUNICATIONS SURVEYS & TUTORIALS, VOL. 14, NO. 2, SECOND QUARTER 2012.
- Aparna k, ” Performance comparison of manet (mobile ad hoc network) protocols (odmrp with amris and maodv)” 2010 international journal of computer applications (0975 – 8887) volume 1 – no. 10.
- C. Wu, Y.Tay, and C.-K. Toh, Ad Hoc Multicast Routing Protocol Utilizing Increasing Id-Numbers (AMRIS) Functional Specification,” Internet draft, Nov. 1998.
- X. Zhang and L. Jacob, “Multicast Zone Routing Protocol in Mobile Ad Hoc Wireless Networks,” Proc. Local Computer Networks (LCN ’03), Oct. 2003.
- C.-C. Chiang, M. Gerla, and L. Zhang, “Forwarding Group Multicast Protocol (FGMP) for Multihop Mobile Wireless Networks,” ACM J. Cluster Computing, special issue on mobile computing, vol. 1, no. 2, pp. 187-196, 1998.
- J.J. Garcia-Luna-Aceves and E. Madruga, “The Core-Assisted Mesh Protocol,” IEEE J. Selected Areas in Comm., vol. 17, no. 8, pp. 1380-1394, Aug. 1999.
- L. Ji and M.S. Corson, “Differential Destination Multicast: A MANET Multicast Routing Protocol for Small Groups,” Proc. IEEE INFOCOM, Apr. 2001.
- X. Xiang, Z. Zhou, and X. Wang, “Self-Adaptive On Demand Geographic Routing Protocols for Mobile Ad Hoc Networks,” Proc. IEEE INFOCOM, May 2007.
- F. Kuhn, R. Wattenhofer, Y. Zhang, and A. Zollinger, “Geometric Ad-Hoc Routing: Of Theory and Practice,” Proc. Int’l Symp.Principles of Distributed Computing (PODC), 2003.
- J. Li et al., “A Scalable Location Service for Geographic Ad Hoc Routing,” Proc. ACM/IEEE MobiCom, pp. 120-130, 2000.
- K. Chen and K. Nahrstedt, “Effective Location-Guided Tree Construction Algorithms for Small Group Multicast in MANET,” Proc. IEEE INFOCOM, pp. 1180-1189, 2002.
- M. Mauve, H. Fubler, J. Widmer, and T. Lang, “Position-Based Multicast Routing for Mobile Ad-Hoc Networks,” Proc. ACM MobiHoc, poster section, June 2003.
- B. Karp, “Greedy Perimeter Stateless Routing (GPSR),” http://www.icir.org/bkarp/gpsr/gpsr.html, 2010.
- A. Ballardie, “Core Based Trees (CBT) Multicast Routing Architecture,” RFC 2201, Sept. 1997.
- Y.B. Ko and N. Vaidya, “Geocasting in Mobile Ad Hoc Networks: Location Based Multicast Algorithms,” Proc. Second IEEE Workshop MobileComputing Systems and Applications (WMCSA), 1999.
|