A wireless sensor network (WSN) is made up of several autonomous spatially distributed sensor nodes that can be used to sense information about the physical or environmental conditions like pressure and temperature etc. and to cooperatively pass their data to the destination location through the network. Wireless sensor nodes are energyconstrained and efficient techniques have to be employed while collecting data to maximize network lifetime. Energy is expended in two ways; in sensing the data and in sending the data to sink. This paper focuses on data collection and discusses about several ways in which data can be sent to the sink.
Keywords |
| Data collection, mobile elements, power management, discovery, data communication. |
INTRODUCTION |
| Wireless Sensor Networks are used in a large variety of applications including military applications, environmental
applications, health-care applications, home applications and other commercial applications. WSNs contain a large
number of sensor nodes, which are tiny devices that work using a battery. These devices perform three functions:
sampling a physical quantity from the surrounding environment, processing (and possibly storing) the acquired data
and transferring them through wireless communications to a data collection point called sink node or base station. One
of the ways to increase the network lifetime is by introducing mobility into the Wireless Sensor Network (WSN). |
| Advantages of Mobility in Wireless Sensor Networks |
| 1. Sparse WSN – Since the nodes are mobile we can manage with fewer nodes. So sparse WSN becomes a feasible
option. |
| 2. Less Cost – Since fewer nodes can be deployed, the network cost reduces. We can make use of mobile elements
already present like moving vehicles, public transport etc. to transport data, |
| 3. More Reliable – Data loss is reduced as the mobile elements visit the nodes to collect data directly through singlehop
transmission as opposed to multi-hop transmissions. Interferences and collisions are avoided. |
| 4. Funneling effect avoided – In traditional networks, the nodes near the sink are overloaded as they have to relay the
data to the sink node. By making use of mobile collectors we can ensure that energy consumption is more uniform,
since the mobile element collects the information by visiting the node. |
| 5. Improved Coverage – Since the data collector is mobile it has improved coverage and it also has the additional
advantage of connecting disconnected networks. |
Challenges faced in incorporating mobility in WSN |
| 1. Node Detection - As communication occurs only when the nodes are in the transmission range of each other, the
nodes have to be correctly and efficiently detected. |
| 2. Mobility-awareness – The nodes must be aware of the mobility pattern so they can be awake only when they
expect the mobile element to be in their transmission range. |
| 3. Policy– The elements are mobile so a policy must be used to ensure efficiency in movement in order to increase
the lifetime of the network. |
| 4. Efficient Data Transfer – Movement of nodes occur so the data exchange must have knowledge about the mobility
pattern. The data that is transferred to the sink must be correct and optimized. |
COMPONENTS OF WIRELESS SENSOR NETWORKS |
| Nodes – They sense data, they also forward and relay messages to other nodes in the network. |
| Sinks – They are the destinations of information. They can collect data either directly or indirectly using intermediate
nodes. Sinks can use data coming from sensors autonomously or make them available on the Internet to interested
users. |
| Mobile Data Collectors – They are neither sources nor destinations, they merely act as intermediate nodes to collect
data. |
| A network is said to be mobile when at least one of the above components is mobile. |
WIRELESS SENSOR NETWORKS MOBILE ELEMENTS (WSN-ME) |
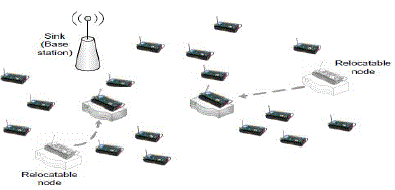
| Re-locatable nodes – These nodes change their location to forward data to the destination. The architecture is
depicted in Figure 1. |
| They do not carry any information in contrast to mobile nodes. They change the topology of the network. Predefined
Intelligent Lightweight tOpology managemenT (PILOT) nodes are used during link failure to re-establish connectivity
in network. They act as bridges when nodes are unstable. Algorithms for placement of re-locatable nodes in order to
improve the network connectivity have been discussed in [5][6]. |
| Mobile Data Collectors (MDCs) – They visit each node and gather data. They can be mobile sinks or mobile
relays. |
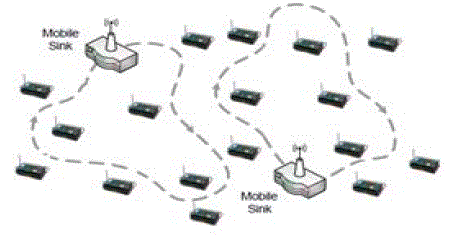
| Mobile Sinks – These mobile nodes are the destination and have high energy. They move around and collect
data. The collected data can be made available to users using wireless internet connection. The path between the sink
and node is not fixed and changes with time. Path between node and sink is multi–hop. The architecture is depicted in
Figure2. |
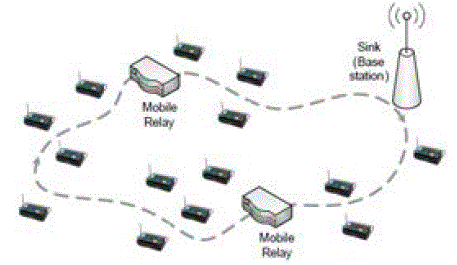
| Mobile Relays – They are not the source or destination of the data, but they are intermediate nodes used for data
passing. The architecture is depicted in Figure3. |
| The data-MULE system was proposed [7][8]. This data-MULE system consists of a three-tier architecture, where the
second tier is represented by relays, called Mobile Ubiquitous LAN Extensions (MULEs). |
| The MULEs pass through the network collect the data from the sensor nodes and when they to near the sink
they pass the collected data to the sink. The MULEs move in straight line and to reduce delay the data can be relayed
by other nodes to reach the sink. If obstacles are present then the MULE will not be able to move along a straight line.
When there are only a few MULEs and when all sensors are not connected, data MULEs may not cover all sensors by
navigating along a straight line. |
| A message ferrying scheme [14][15]provide the relaying of messages in sparse and mobile networks. Message
ferries move through the field and get data from nodes. Message ferries can be thought of as a moving communication
infrastructure which allows data communication in wireless networks that are sparse. |
| Mobile Data Collectors called M-Collectors were proposed in [1]. Here M-Collector will move through the
network and gather information. This is called as M-Collector tour and it is based on the optimal path as found out by a
variant of the spanning tree algorithm called spanning tree covering algorithm. Since delay will be high if we use a
single mobile collector, we can use many M-Collector to collect data in a parallel manner. But these techniques cannot
be used to transfer emergency data. |
| This problem can been addressed by the usage of long range wireless communication between the sink and
MDC to transmit the emergency data as soon as it is sensed, instead of the MDC sending it to sink at the end of the
tour. |
| We can also use a technique where we design the topology as a minimum hop transmission. Certain nodes
with high energy are designated as polling points. The sensors move the data from the sensor node to the polling point
and the polling point sends control signals to base station. The base station will dispatch the mobile collector to get the
data from the polling points. In this scheme the cost of having multiple data collectors is avoided by making use of a
single data collector. |
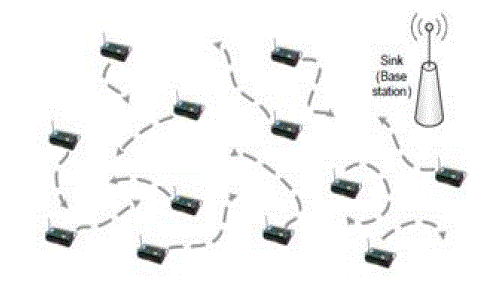
| Mobile peers - Mobile peers are ordinary mobile sensor nodes in WSN-MEs. They can be the source or they can be
used to relay the messages in the network. Mobile peers are depicted in Figure 4. Their interactions are symmetrical
because the sink itself might also be mobile. When a peer node is in communication range, it can transfer its own data
and it can gather data from the other peer nodes while moving in the sensing area. |
| Mobile peers have been successfully employed in the context of wildlife monitoring applications, such as
tracking of zebras in [9][10][11]. Sensor nodes are attached to animals and act as peers, so they generate data and also
carry and forward all data coming from other nodes which they have been in contact with earlier. When mobile peers
get near a base station, they push all the gathered data. Redundant data are discarded by peers in order to save storage.
The problem with using animals to collect the data is that the movement is unpredictable. This can be avoided by using
a predictable robot or vehicle as suggested in the [1].Mobile peers can also be used for data collection in urban sensing
scenarios [2]. Sample applications include personal monitoring (e.g., physical exercise tracking), civil defense (e.g.,
hazards and hotspot reporting to police officers) and collaborative applications (e.g., information sharing for tourism
purposes). Here, sensors are not used primarily for monitoring the environment, but are rather utilized to characterize people in aspects of interactions and context (or state) information. An example is represented by handheld mobiscopes
[12] where handhelds devices –such as cell phones or PDAs – gather data from the surrounding environment and report
them to servers, which give services to users. |
Overview of Data Collection |
Terminology |
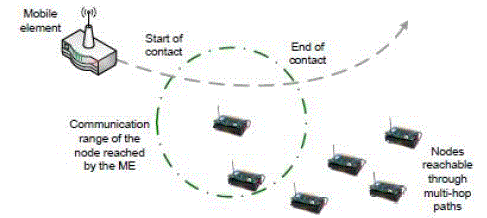
| Contact - ME is in contact with a sensor when they can reach out each other through wireless communications. In
general, a contact happens when two or more nodes are in their mutual communication range. |
| Contact Time - The amount of time the nodes are in contact is called as contact time. |
| Contact Area - The contact area of a node is defined as the region where that node can possibly be in contact with other
nodes. |
| Discovery - Since nodes cannot communicate unless they are in contact, discovery is the process which allows a node
to identify a contact, i.e., an ME in its communication range. |
| Data Transfer -Data transfer is the message exchange between nodes which are in contact. The data transfer covers only
single-hop transmissions, which may involve several nodes, where at least one is mobile. |
| Residual Contact Time -The residual contact time is defined as the amount of time which is actually used for data
transfer during a contact. The residual contact time is generally shorter than the contact time because the node has to
find out the presence of an ME before starting the message exchange. |
| Routing - The process of data forwarding toward an ME, i.e., the selection of the path or the sequence of pair-wise
message transmissions to the intended destination. |
| The data collection is depicted in Figure 5. |
Phases |
| The phases for data collection in WSN-MEs are: discovery, data transfer and routing to MEs. Each phase has its own
issues and requirements which we briefly described below. |
| a. Discovery is the initial step for collecting data in WSN-MEs, since the presence of the ME in the contact area is
generally not known at sensors. The aim of discovery protocols is to find contacts as soon as they happen, and with
less energy expenditure. In other words, discovery must maximize the number of detected contacts and the residual
contact time, while at the same time minimizing the energy consumption. Discovery permits the nodes to detect the presence of the ME while it is in the contact area. Since communication is possible only during contacts, discovery
should not only be able to correctly detect the presence of the ME, but should also be timely, so that the contact time
can be fully exploited. |
| Indeed, contacts need to be detected even when they occur very infrequently. In order to reduce the energy
consumption due to discovery, two complementary approaches can be used. First, it is possible to design (general)
mobility-independent low-power protocols, which can detect MEs no matter what the mobility pattern is. Second, it is
also possible to exploit some knowledge on the mobility of nodes, so that sensors can be active only when the ME is
expected to be in contact. |
| b. Data transfer immediately follows discovery. The goal of the data transfer protocols is to maximize the throughput –
in terms of messages successfully transferred per contact – while minimizing the energy consumption. After the
presence of an ME has been detected, actual data transfer has to be accomplished by using a data collection protocol.
By data transfer, we mean the communication process between an ME and its one-hop neighbors. As a consequence,
data transfer protocols have to be aware of the issues which result from mobility. In fact, the communication process is
influenced, not only by the conditions prevalent in the channel, but also by the distance between the source and the
receiver, which changes based on their speed. |
| c. Routing to MEs is actually possible only when the density of the network is enough to allow (even partial) multi-hop
routes. This is true for dense WSN- MEs, where routing to ME is always possible. This is also possible in case of
sparse WSN-MEs, where nodes can organize as clusters that are disconnected. There are two main classes of routing
techniques for uncontrollable MEs namely, flat routing and proxy-based routing. The routing paths to the ME are
adaptively computed and updated in both the cases, so that it can be reached while navigating through the network.
Flat routing is characterized by the fact that all nodes behave the same way, and, hence, there are no sensors with
special roles. Proxy-based routing, on the contrary, selects a number of proxies or gateways among sensor nodes.
Proxies bridge communications between the static sensors and the ME. |
| In this case, routing is possible only when an ME is in contact with at least one node in the cluster. However,
some nodes can be selected as bridges and act as gateways between the cluster nodes and the ME. In both cases, the
aim of routing is to discover the best multi-hop paths – in terms of both delivery ratio and low energy consumption –
towards either the ME or a node which can be in contact with the ME. |
Impact of mobility |
| Different kinds of mobility can have significant impact on the phases of data collection. The aspect of
mobility which has the most important impact on the data collection process is controllability, depending on whether
the ME’s motion is autonomous or not. |
| Two main patterns for uncontrolled mobility are deterministic and random. |
| The deterministic mobility pattern is characterized by the regularity in the contacts of the ME, which enters the
communication range of sensor nodes at specific and periodic times. This can occur when the ME is placed on a
shuttle for public transportation, as in [3]. On the other hand, the random mobility pattern is characterized by
contacts which take place not regularly, but with a distribution probability. For example, Poisson arrivals of a mobile
element have been discussed in [4], while random direction ME mobility has been investigated in [13]. In general,
anode should perform discovery continuously, so that it can ensure that the chances of detecting contacts is enhanced. |
| However, when some knowledge on the mobility pattern of nodes can be exploited, the node can restrict
discovery to the times where the probability of an ME being in proximity is high. |
| Controlled mobility exploits nodes which can actively change their location, because they can control their trajectory
and speed. |
| As a consequence, motion becomes an additional factor which can be effectively exploited for designing data
collection protocols specific to WSN-MEs. It should be noted that controlled mobility can make some issues related to
data collection less relevant. For example, the discovery problem can be somewhat made simple, since MEs can be
instructed to visit (individual) nodes at specific times. In addition, the duration of contacts has fewer issues, since the
MEs can stop at nodes until they have collected all stored data. Anyway, different problems arise in this context, mainly related to how to
schedule ME arrivals at sensors – which includes defining both the trajectory and the speed of the ME – while satisfying certain quality of service constraints (such as minimizing latency and buffer overflows) and keeping the
energy consumption as low as possible. |
CONCLUSION |
| In this paper we have discussed the techniques used for collecting data. The terminology concepts involved in mobile
data collection were discussed and some of the advantages and disadvantages were also investigated. |
| |
Figures at a glance |
 |
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
Figure 5 |
|
| |
References |
- M. Ma, Y. Yang and M. Zhao, âÃâ¬ÃÅTour Planning for Mobile Data-Gathering Mechanisms in Wireless Sensor NetworksâÃâ¬ÃÂ, IEEE TRANSACTIONSON VEHICULAR TECHNOLOGY, VOL. 62, NO. 4, MAY 2013.
- Campbell, A. T. ,Eisenman, S. B. , Lane, N. D. , Miluzzo, E. , and Peterson, R. A. 2006.âÃâ¬ÃÅPeople-centric urban sensingâÃâ¬Ã In Proceedings of the2ndInternational Workshop on WirelessInternet (WICON 2006). Article no. 18.
- Chakrabarti, A. ,Sabharwal, A. , and Aazhang, B. 2003.âÃâ¬ÃÅUsing predictable observer mobilityfor power efficient design of sensor networksâÃâ¬Ã InProceedings of the 2nd International Workshopon Information Processing in Sensor Networks (IPSN 2003). 129âÃâ¬Ãâ145.
- Somasundara, A. ,Kansal, A. , Jea, D. , Estrin, D. , and Srivastava, M. 2006. âÃâ¬ÃÅControllably mobile infrastructure for low energy embeddednetworksâÃâ¬ÃÂ. IEEE Transactions on Mobile Computing 5, 8, 1536âÃâ¬Ãâ1233.
- Tang, C. and McKinley, P. 2006.âÃâ¬ÃÅEnergy optimization under informed mobilityâÃâ¬Ã IEEE Transactions on Parallel and Distributed Systems 17, 9(Sept.), 947âÃâ¬Ãâ962.
- Dini, G. ,Pelagatti, M. , and Savino, I. M. 2008. âÃâ¬ÃÅAn algorithm for reconnecting wireless sensor network partitionsâÃâ¬ÃÂ.In Proceedings of the5thEuropean conference on Wireless Sensor Networks(EWSN 2008).253âÃâ¬Ãâ267
- Shah, R. C. , Roy, S. , Jain, S. , and Brunette, W. 2003.âÃâ¬ÃÅData mules: Modeling a three-tierarchitecture for sparse sensor networksâÃâ¬Ã InProceedings of the 2ndACM International Workshopon Wireless Sensor Networks and Applications (SNPA 2003). 30âÃâ¬Ãâ41.
- Jain, S. , Shah, R. , Brunette, W. , Borriello, G. , and Roy, S. 2006. âÃâ¬ÃÅExploiting mobility for energy efficient data collection in wireless sensornetworksâÃâ¬Ã ACM/Springer Mobile Networksand Applications 11, 3 (June), 327âÃâ¬Ãâ339.
- Oki, H. , Wang, Y. , Martonosi, M. , Peh, L. , and Rubenstein, D. 2002. âÃâ¬ÃÅEnergy-efficient computing for wildlife tracking: Design tradeoffs andearly experiences with ZebraNet.âÃâ¬ÃÂ.In Proceedings of the 10thInternational Conference on Architectural Support for ProgrammingLanguages andOperating Systems (ASPLOS 2002).96âÃâ¬Ãâ107.
- Haas, Z. J. and Small, T. 2006. âÃâ¬ÃÅA new networking model for biological applications of ad hocsensor networksâÃâ¬ÃÂ. IEEE/ACM Transactions onNetworking (TON) 14, 1 (February), 27âÃâ¬Ãâ40.
- Small, T. and Haas, Z. 2003. âÃâ¬ÃÅThe shared wireless infostation model âÃâ¬Ãâ a new ad hoc networkingparadigm (or where there is a whale, there is away).âÃâ¬Ã In Proceedings of the 4thACM International Symposium on Mobile Ad Hoc Networking and Computing (MobiHoc 2003). 233âÃâ¬Ãâ244.
- Abdelzaher, T. ,Anokwa, Y. , Boda, P. , Burke, J. , Estrin, D. , Guibas, L. , Kansal, A. , Madden, S. , and Reich, J. 2007.âÃâ¬ÃÅMobiscopes for humanspacesâÃâ¬ÃÂ. IEEE Pervasive Computing 6, 2 (April-June), 20âÃâ¬Ãâ29.
- Poduri, S. and Sukhatme, G. S. 2007. âÃâ¬ÃÅAchieving connectivity through coalescence in mobilerobot networksâÃâ¬Ã In Proceedings of the 1stInternational Conference on Robot Communicationand Coordination (RoboComm 2007). 1âÃâ¬Ãâ6.
- Jun, H. , Zhao, W. , Ammar, M. , Zegura, E. , , and Lee, C. 2005. âÃâ¬ÃÅTrading latency for energy inwireless ad hoc networks using messageferrying.âÃâ¬ÃÂIn Proceedings of the 1stIEEE Workshop onPervasive Wireless Networking (PWN 2005).220âÃâ¬Ãâ225.
- Zhao, W. ,Ammar, M. , and Zegura, E. 2004. âÃâ¬ÃÅA message ferrying approach for data delivery insparse mobile ad hoc networksâÃâ¬ÃÂ. In Proceedings of the 5th ACM International Symposium onMobile Ad Hoc Networking and Computing (MobiHoc2004). 187âÃâ¬Ãâ198.
|