ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
V.M.Prabhakaran1, Prof.S.Balamurugan2, S.Charanyaa3
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
This paper proposes various data flow models efficiently guard Electronic Health Records (EHRs). Personal Health Records (PHRs) should remain the long-term property of patients data. MyPHRMachines a patient centric system that takes a radically new architectural solution to health record interoperability. Patients Can View their Medical data and they can access and share through remote Virtual machine. Multi authority based encryption with My PHR system (MA-My PHR) is defined to solve the Key generation issues. Finally we illustrate how a prototype of MyPHRMachines supports the use case of a real world patient.
Keywords |
| Electronic Health Records(EHRs0, Privacy, Microdata, Medical Healthcare System, Database Security. |
INTRODUCTION |
| Scientific communities in areas such as high energy physics, gravitational wave physics, geophysics, astronomy and bioinformatics involve the use of distributed data sources. Hence analysis of their datasets is represented and structured as scientific workflows. Scientific workflows usually need to process large amount of data and computationally intensive activities. Cloud computing is new paradigm for distributed computing which delivers Infrastructure AS A Service (IaaS), Platform as a Service (PaaS), and Software as a Service(SaaS) and are made available as subscriptionbased services in a pay-as-you-go model to consumers computing on to the cloud IoanCristianTrelea [2003]. It aids customers to dynamically provision computing resources around the globe, and also a. Among the various challenges faced in emerging cloud as a successful technology, the major challenge identified is scheduling tasks on to resources. Tasks identified and placed in the cloud may be static or dynamic in nature. In order to efficiently and cost effectively schedule the tasks and data of applications onto these cloud computing environments, application schedulers have different policies that vary according to the objective function: minimize total execution time Osman I .Li [1993] H. EI. Rewini and T.G. Lewrs and H. H. Ali [1994] , minimize total cost to execute, balance the load on resources used while meeting the deadline constraints of the application, and so forth. |
| The remainder of the paper is organized as follows. Section 2 deals about Survey of Literature of Techniques prevailing to protect EHRs. Basic Primitives and Terminologies are discussed in Section 3. Section 4-6 depicts the various levels of data flow models ranging from 0 to 2. A sample code snippet for cloudlet creation is discussed in Section 7. Section 8 concludes the paper and outlines the direction for Future Work. |
II. LITERATURE SURVEY |
| P.-Y. Yin, S.-S. Yu and Y.-T. Wang (2006) presented a hybrid particle swarm optimization algorithm for finding the near optimal task assignment with reasonable time. The experimental result shows that the HPSO outperforms the GA and the cost difference between the two approaches is statistically significant. Also, the convergence and the worstcase analyses of the HPSO have been empirically conducted. A. E. M. Zavala, A. H. Aguirre, E. R. Villa Diharce, and S. B. Rionda (2008) presented a new constrained optimization algorithm based on a particle swarm optimization (PSO) algorithm approach. Hybrid approach based on a modified ring neighborhood with two new perturbation operators designed to keep diversity is proposed. The paper shows that it is possible to improve PSO and keeping the advantages of its social interaction through a simple idea: perturbing the PSO memory. The proposed algorithm shows a competitive performance against the state-of-the-art constrained optimization algorithms. The proposed algorithm can be used to solve single objective problems with linear or non-linear functions and subject to both equality and inequality constraints which can be linear and non-linear |
| The task of scheduling a group of dependent or independent tasks among heterogeneous computing environment is a well-established investigational area. The traditional techniques for solving Task Assignment Problem, such as dynamic programming, branch and bound, and divide and conquer has mainly two disadvantages namely the long time consumption and lack of applicability for real-time scheduling applications. Reuy Maw Chen [2001] derived an optimal task assignment scheduling algorithm, to minimize the execution and communication cost and substantiated the algorithm using simulation results. Many heuristic techniques employ certain graphical representation such as Max Flow / Mincut Algorithm to determine the optimal assignment of tasks to processors so as to minimize the total execution and communication cost. This concludes that traditional methods employed, to obtain optimal task assignment are fast, deterministic and tends to produce accurate results, but greatest disadvantage is that it often gets stuck in local optima. Another disadvantage of employing traditional optimization algorithms in solving task assignment problems is the time complexity involved which may be exponential or polynomial. These compelling disadvantages have led to employ modern heuristic approaches such as simulated Annealing algorithm, Genetic Algorithm and Ant colony algorithms. Edwin S.H. Hou et.al.(1994). Applied the heuristic approach, Genetic Algorithms for Multiprocessor scheduling. Annie S.hu et.al.(2004) . Researched on proposing an Incremental Genetic Algorithm Approach to for multiprocessor Scheduling. Graham Ritchie (2003) focused on developing a static multiprocessor scheduling algorithm with ant colony optimization and local search techniques. Reng-Yang et-al [22] proposed a hybrid particle swarm optimization algorithm with Hillchmbing heuristic as the local search method for optimal task assignment in distributed system. |
| P.Visalakshi et.al. (2009), developed a new hybrid approximation algorithm and also a new parallel version of particle swarm optimization to solve the task assignment problem. The hybrid heuristic model developed, involves Particle Swarm optimization algorithm and Simulated Annealing Algorithm, which performs static allocation of tasks in a heterogeneous distributed computing system in a manner that is designed for cost minimization. The parallel version of Particle Swarm optimization which involves data parallelism is also experimented. The research has led to a conclusion that among the two methods proposed, hybrid approximation algorithm and parallel version of Particle Swarm optimization, the parallel version turned out be more effective and efficient in finding near optimal solutions. |
| P.Visalakshi et.al. (2009) presented a Hybrid Particle Swarm optimization (HPSO) method for solving task assignment problem, which is np-hard in nature. An algorithm was developed based on Particle Swarm optimization PSO, a recently developed population based heuristic optimization technique to dynamically schedule heterogeneous task on to heterogeneous processors in a distributed environment. The major issue in task scheduling is load balancing is taken into consideration and the nature of the tasks that are to be scheduled are assumed to be independent and nonpreemptor simulation results ensure that hybrid PSO yields a better result when compared to normal PSO , when employed to solve a task assignment problem. The result of HPSO is also compared with another popular heuristic optimization technique, Genetic Algorithms, and result of the research indicated that PSO outperforms GA. P.Visalakshi et.al. (2007) proposed a Hybrid Particle Swarm Optimization Algorithm with Dynamically varying inertia and employed it for multiprocessor scheduling problem. The proposed hybrid heuristic model involved. Particle Swarm Optimization Algorithm and simulated Annealing algorithm PSO with dynamically varying inertial parameter was also implemented and proved to be efficient and effective in finding near optimal solutions when compared to fixed inertia. |
III. BASIC PRIMITIVES AND TERMINOLOGIES |
| Cloud environment may describe a company, organization or an individual who uses a Web based application for every mission rather than installing software and storing data on a computer. Cloud environment involves in provide a functionality to outsource and encrypt the data. Cloud storage service is accessed through the cloud computer service, web service application programming interface or by a cloud storage gateway. The cloud based workspace is centralized providing easy functionality to share. The cloud environment can provide improvements in system efficiency & density. Cloud environment solve the problem of complicated configuration management, Decreased productivity, Limited accessibility and Poor collaboration. It has the capability to access all work, databases and other information from any device. Cloud environment involves in providing some basic network model for storage of data in the cloud. The basic network model for the cloud data storage and three different network entities are |
| 1. User |
| 2. Cloud storage server |
| 3. Cloud service provide |
| a. User: An entity which has large data files to be stored in the cloud and relies on the cloud for data maintenance and computation can be either individual consumers or organizations. |
| b. Cloud Storage Server (CSS): An entity which is managed by Cloud service provider. Cloud storage is a subgroup of cloud computing. Cloud computing organizations offer users access to not only storage, but also processing power and computer applications mounted on a remote network. Cloud storage provides users with instant access to a wide ranging of resources and applications hosted in the infrastructure of another organization through a web service interface. Security of stored data and data transfer may be a concern during storing the sensitive data at a cloud storage provider. |
| c. Cloud Service Provider (CSP):A cloud provider is a company that compromises some constituent of cloud computinghas significant storage space and computation resource to maintain the user data. The Data owner encrypted some keywords about his data, and service provider supported the owner to retrieve his data by keywords and not allow others to retrieve. When supposing the role of cloud provider, an organization is accountable for making cloud services available to cloud customers. |
IV. LEVEL 0 DATA FLOW DIAGRAM |
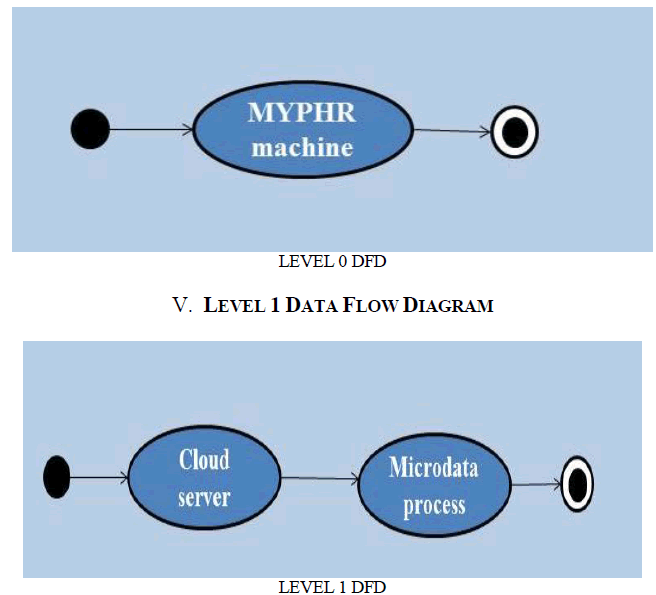 |
VI. LEVEL 2 DATA FLOW DIAGRAM |
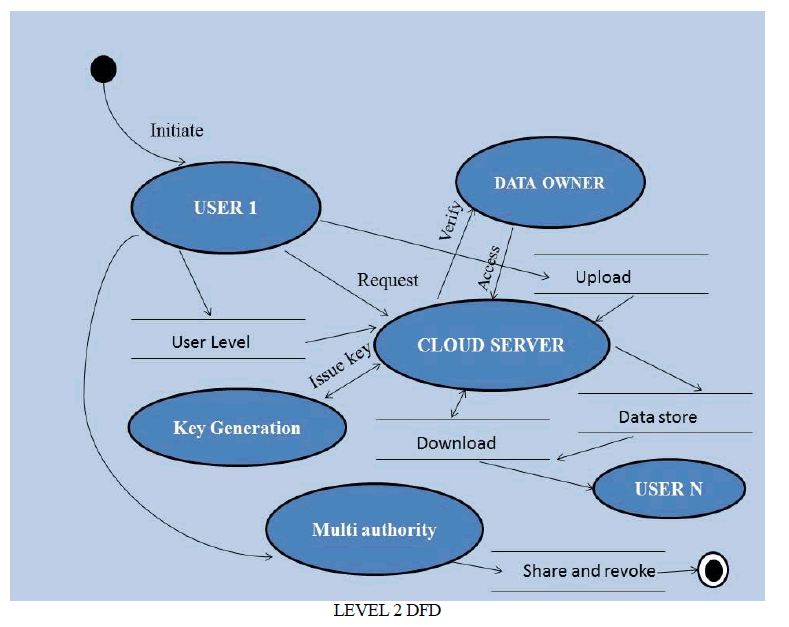 |
VII. SAMPLE CODE SNIPPET FOR CLOUDLET CREATION |
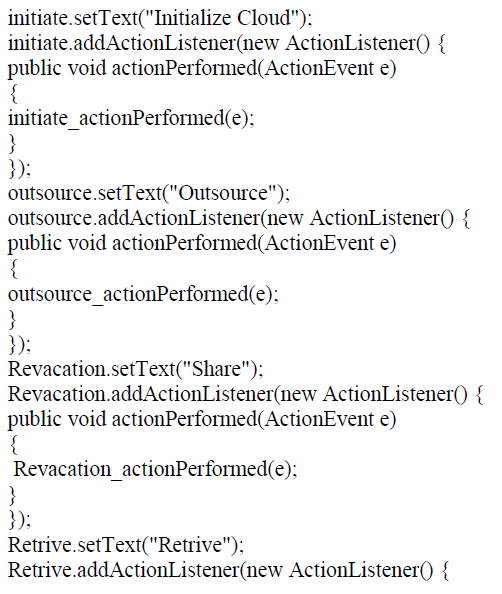 |
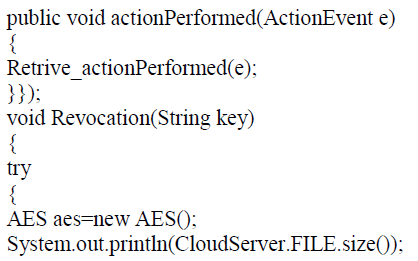 |
VIII. CONCLUSION AND FUTURE WORK |
| Portability of critical clinical data, sharing information securely and accessibility of data from different healthcare centers for treatment process can simplify the whole healthcare service. MyPHRMachines allows also the controlled sharing of application software that is required to view or analyze health records. The multi-authority attribute based encryption which it will have many attribute authority for handling the different set of users from various domainsIn this paper, the issue of outsourcing of data in cloud is addressed by the method of key generation for cloud user. Cloud computing, besides providing a maximized effectiveness of shared resources, also provides an easy way of storing and retrieving data. Personal Health Records (PHRs) are designed to maintain lifelong details of patients. Automated Patient Identifier and Patient Care System is designed to count hospitalized patients based on the concept of Current Procedure Terminology (CPT) manager. Cloud storage service is accessed through the cloud computer service, web service application programming interface or by a cloud storage gateway. The cloud based workspace is centralized providing easy functionality to share. The cloud environment can provide improvements in system efficiency & density. As a part of future work, we have planned design the UML diagrams to look into the problem and to increase the clarity and to implement the uploading of encrypted medical data in cloud and in the process of creating individual cloudlets for preventing unauthorized user. |
References |
|