Keywords
|
| Electronic voting systems, electoral system, manual voting systems, fingerprint |
INTRODUCTION
|
| One of the most important features of democracy that is very common to all people of various types is the act of election. Democracy thus encourages individual freedom according to the rule of law, so that people may behave and express themselves as they choose. This not only gives people a chance to elect their leaders, but also to freely express their views on issues. In response to the 1948 Universal Declaration of Human Rights which puts import on the necessity of free elections, nations aim at new and improved voting procedures which are of relevance to elections in the 21stcentury[12]. With the passage of time,voting, which was mainly manual, has been influenced by Information Technology, with debates arising about the relevance or not, of computerized/online voting [2]. Nevertheless, it is impossible to completely rule out the need for technology and electronic voting, with the growing number of eligible voters and manual ballot papers involved [4]. Smith and[6] indicate that electronic voting is the nextlogical step in applying online information-gathering andretrieval technologies to e-government |
RELATED WORKS
|
| Types of voting systems: Voting is a method by which groups of people make decisions. These decisions could be political, social or public. Voting can also be used to choose between difficult plans of actions or to decide who is best eligible to be awarded a prize. Voting can thus be defined as a process that allows a group of individuals to choose between a number of options. Most voting systems are based on the concept of majority rule or plurality. For example, in an election, a candidate with a plurality receives more votes than any other candidate, but does not necessarily receive the majority of the total votes cast. [7]. |
| Five different types of voting systems may be identified. These are: |
| ? Paper-Based Voting Systems |
| ? Direct-Recording Electronic (DRE) Voting Systems |
| ? Public Network DRE VotingSystems |
| ? Precinct Count Voting Systems |
| ? Central Count Voting Systems |
| Paper-based Voting Systems (PVS): record, count, and produce a tabulation of the vote count from votes that are cast on paper cards or sheets. Some PVSs may allow voters to make selections by means of electronic input devices. Voter selections are, however, not independently recorded, stored or tabulated by such input devices. |
| Direct-recording Electronic (DRE) voting systems: record votes by means of a ballot display provided with mechanical or electronic optical components which could be activated by the voter. Such systems record voting data and ballot images in computer memory components. Also, data processing is achieved by the use of computer programs. |
| Public network DRE voting systems (PNDRE):Make use of electronic ballots and transmit vote data from the polling stations to other locations over a public network. The votes may be transmitted as individual ballots as they are cast, or periodically as batches of ballots, or as one single batch, at the end of voting. |
| Precinct count voting systems (PCVS):put the ballots in a tabular form at a particular place, say, a polling station. They provide mechanisms that store vote count electronically and transmit the results to a central location over public telecommunication networks. |
| Central count voting systems (CCVS):Tabulate ballots from multiple precincts at a central location. Voted ballots are safely stored temporarily at the polling station. These ballots are then transported or transmitted to a central counting location. CCVSs may, in some cases, produce printed reports on the vote count. |
| Characteristics of a voting system:Voting systems must be transparent and comprehensible enough that voters and candidates can readily accept the results [7]. This means that the veracity of a voting system isnecessary for the acceptance of the results of that election. [13] gives a comprehensive assessment of paper versus electronic voting systems. For a voting system to be considered transparent and comprehensiblesome important criteria must be met, otherwise it may lead to indecisive or inaccurate election results. |
| First of all, the anonymity of a voter’s ballot must be preserved, in order to ensure that the voter is safe when voting against a candidate, and also to guarantee that voters have no evidence that proves which particular candidates received their votes. It is believed that the existence of such evidence could allow votes to be bought [7]. |
| Secondly, the voting system must be tamper-proof in order to prevent a wide range of attacks, including ballot stuffing by voters and incorrect tallying by insiders (poll officials). Thirdly, it should be userfriendly. This means that it should be easily comprehensible and usable by the entire voting population. |
| Current day voting systems: With the development of information technology, nations all over the world are replacing archaic punch cards and mechanical voting systems with electronic voting systems (e-voting) aimed at increasing voter participation and speeding up the release of election results [5]. [2]gives an extensive list on references relating to electronic voting (including internet-based voting). Brazil and India are examples of countries that use evoting for both general and state elections [8]. Statistics show that the use of Electronic Voting Mechanisms (EVMs) - an e-voting system in India – has eliminated the occurrence of invalid votes during elections. Prior to their use, the number of invalid votes that were recorded in India was always more than the winning margin between the candidates. Aside from eliminating invalid votes, EVMs ensured that the total number of votes cast was tallied within two to three hours as against thirty to forty hours when the conventional means were used. |
| In considering voting mechanisms, [6] examines the process of setting technical communication standards for e-voting. [1]] also analyze various attempts at e-voting and discuss their benefits and vulnerabilities. St. Albans, UK, in May 2007, implemented a fully electronic election with no paper-based voting allowed. People were to use a number of channels to vote, the Internet, kiosks, Interactive Voice Recognition (IVR) via telephones or mobile phones, and also by post. Within six minutes, the system had counted all the ballots – recording the fastest ever vote count. Furthermore, no invalid vote was recorded, and all attempts to subvert the system by means of worms, viruses and Denial-of-Service proved futile [5]. |
| Newer and more improved trends in voting are showing that a greater number of developed nations are beginning to choose e-voting systems over manual votingsystems due to their convenience and the ease which they offer voters and election officials [1]. It is important to note that even though e-voting systems appear to be the best alternative to paper-based and other mechanical systems, they must be used with caution because experts believe that some of such systems could have challenges ranging from software engineering, auditing pitfalls, to insider threats, thereby undermining their integrity [11]. |
| In his review on electronic voting security criteria, i.e., confidentiality, integrity, availability, reliability and assurance, [9] concluded that a lot of such criteria are by nature very difficult to satisfy. [4] wrote on the US online voting system and the challenges it faces, [10] clearly pointed out critical security requirements for online voting and [3] discuss e-voting privacy protection. Despite all the success stories recorded on the use of electronic voting systems, it is believed that further studies must be carried out to improve upon them. |
MATERIALS AND METHOD
|
| Methodologies are comprehensive, multiple-step approaches to systems developments that will guide people’s work and influence the quality of the final product. Most methodologies incorporate several development techniques. The systematic procedure by which a complex or scientific task is accomplished is called techniques. Techniques are particular processes that will follow by, to ensure that the work is well thought-out, complete and comprehensible to others. |
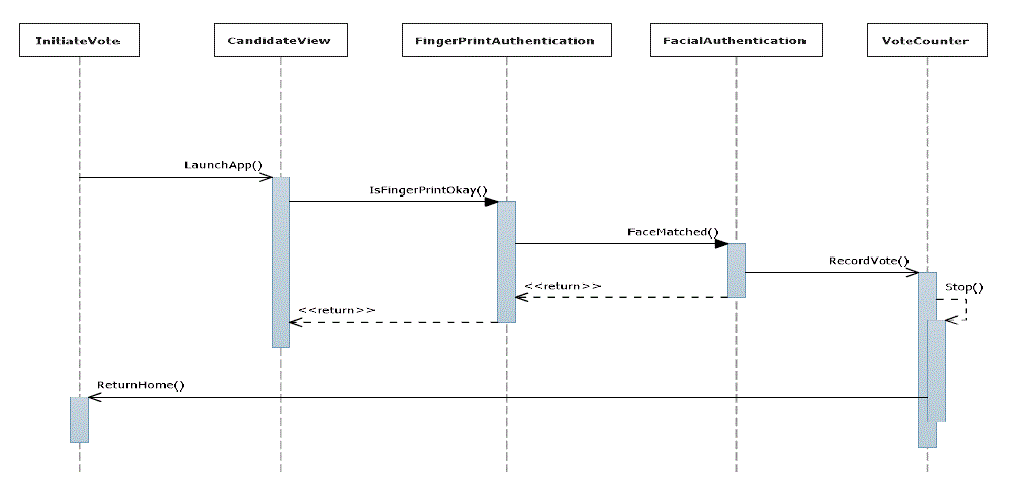
| The diagram in figure 1 is a sequence diagram which describes the flow of the internal operations of the designed system. The first method to invoke is to launch InitiateVote method and the IsFingerPrintOkay method is called to verify the captured fingerprint. |
THE RESULT
|
| The interface in figure 2 indicates the display of the political aspirant across different parties. The interface will be displayed for the voters so that he/she can select the candidate of her desire for the selected political position. The voter can only select one candidate in this category. Also, there are six political parties(Champion Party, Straight Party, Bright Party, Good Party, Finest Party and Confidence party). |
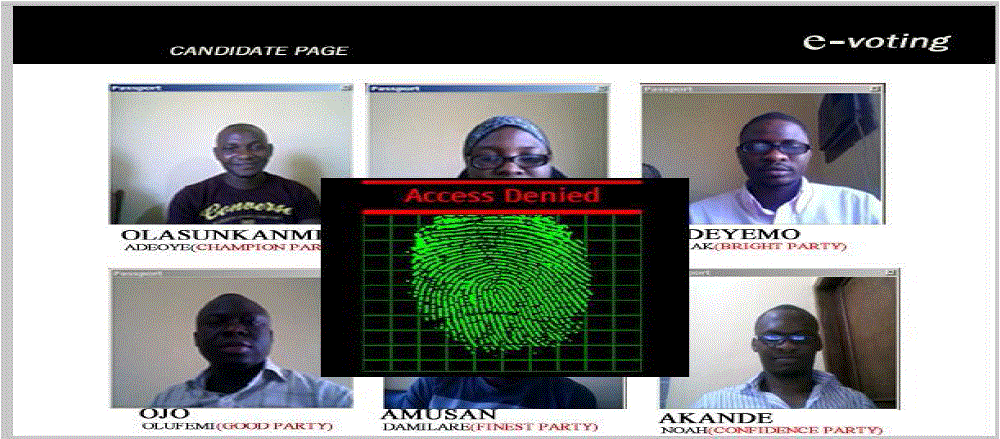
| The interface shown in figure 3 describes what will be seen when the voter selects any candidate, this is the first stage of the multimodal verification of voter’s biometric identity. The interface is used to indicate to the user that authentication process is required as no voter will be allowed to move any step further without first passing this stage. |
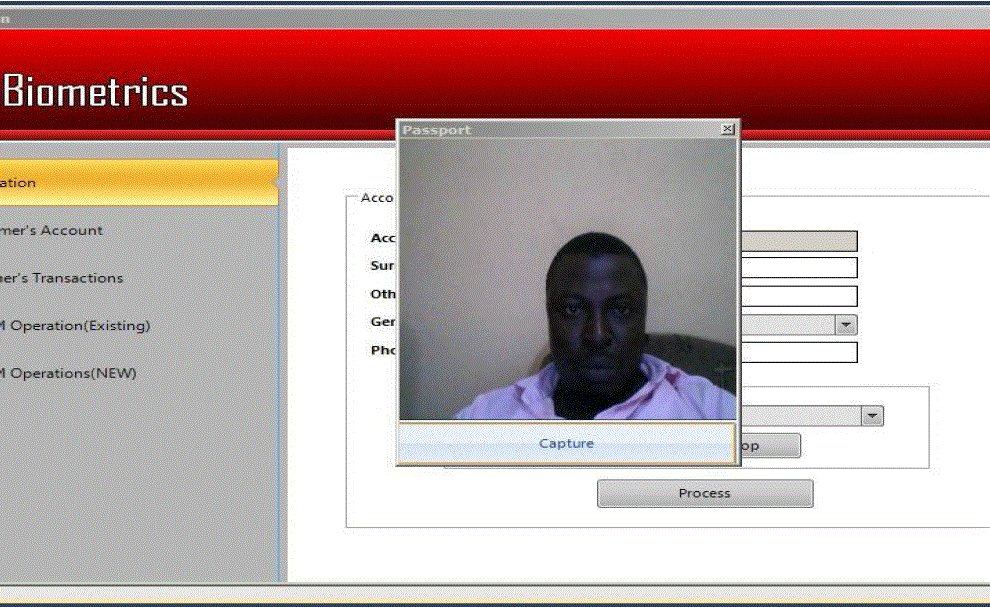
| The next stage after the voter selects the candidate of his/her choice, is the interface in figure 4 which will be prompted so that the fingerprint of authentication of the voters will be taken. |
| The diagram shown in figure is the interface where the voter’s face will be authenticated against the one taken during the enrollment stage. The voter will be allowed to vote for the selected candidate provided the two authentication stages are valid. |
Figures at a glance
|
 |
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
Figure 5 |
|
References
|
- Awad, M.L. and L. Ernst, 2011. Internet voting in the USA: Analysis and commentary. Transforming Government: People, Process Policy,5(1): 45-55
- Cranor, L., 2011. Electronic Voting Hot List. Retrieved from: http://lorrie.cranor.org/voting/hotlist.html (Accessed on: 15 May, 2011).
- Evangelia K., G. Stefanos and C. Kalloniatis, 2007. Protecting privacy in system design: The electronic voting case. Transforming Government: People, Process Policy,1(4): 307-332.
- Evers, J., 2004. Experts Challenge US Online Voting System. Retrieved from: http://www.infoworld.com/article/04/01/21/HNonlinevoting_1.html(Accessed on: 15 May, 2011).
- Kelly, A.D., 2003. Secure Oracle 91AS Gets Their E-Vote. Oracle Magazine, January-February, 45-50.
- Kitcat, J., 2004. Government and ICT standards: An electronic voting case study. J. Inf. Community. Ethics Soc., 2(3): 143-158.
- Kohno, T., A. Stubblefield, A.D. Rubin and D.S. Wallach, 2004. An Analysis of an Electronic Voting System. McGraw Hill, New York
- Mira, L.M., 2004. For Brazil Voters, Machines Rule. Wired News, Jan, 24.
- Neumann, P.G.,1993. Security Criteria for Electronic Voting. 16th National Computer Security Conference, Baltimore, Maryland, September. Retrieved from: http://www.csl.sri.com/users/neumann/ncs93.html,(Accessed on: 15 May, 2011) of the ACM, 45(12): 39-43
- Pescatore, J. and C.H. Baum, 2004. Online Voting can’t be Trusted on Standard PCs.Retrieved from: http://news.zdnet.co.uk/security/0,1000000189, 391 48110,00.htm (Accessed on: 15 May, 2011)
- Rubin, A., 2002. Security considerations for remote electronic voting over the internet, Communications
- Salomonsen, G.. 2005. Voting for Online Democracy. Retrieved from: http://www.physorg.com/news4011.html,(Accessed on: 15 May, 2011).
- Shamos, M.I., 2004. Paper v.Electronic Voting Records An Assessment. Retrieved from: http://euro.ecom.cmu.edu/people/faclty/mshamos/paper.htm, (Accessed on: 15 May, 2011).
|