The development of technology, coupled with availability of sophisticated computing devices facilitating anywhere, anytime access, have made mobile applications a very common feature. Mobile banking, mobile commerce being amongst them. Enforcement of data integrity and consistency, handling of concurrency, failure has become more magnified due to the environment being wireless and data being real time. Further issues of device mobility, bandwidth, latency, disconnections and resource constraints of the device itself cannot be ignored. Therefore transaction management and its related protocols gain significance. In this paper we make a comprehensive review of the effects of mobile environment on transaction management.
Keywords |
| Transaction Management, Mobile devices, MANETs, MDS. |
INTRODUCTION |
| The issues related to mobile databases and protocols used to overcome the problems occurring in transaction
management due to use of mobile devices have gained significance in the presence of advancing technology and
sophisticated devices. Many protocols have been proposed for transaction management based on constraints of ACID
properties, concurrency control, replication of data, commitment of data in multiple phases, locking mechanisms and
timestamp based approaches. |
| In this work we try to review the effects of mobile environment on transaction management. The paper is organized as
follows. In section –A we make a thorough analysis of transaction and all aspects related to its management. In section-
B we discuss about the mobile environment and its impact on transaction management by highlighting the issues of it
in mobile environment. Section-III concludes the paper. |
| A. Transaction |
| A transaction is a logical unit of work that contains one or more structured query language statements. It is
completed explicitly when it is committed or rolled back implicitly when a DDL command (CREATE, DROP, RENAME, or
ALTER) is executed. The advantages of transactions include |
| • Improved quality, integrity, and consistency of data. |
| • Robust applications. |
| 1) Characteristics of Transaction: |
| • Number of transactional steps. |
| • Time dependency. |
| • Is the process Synchronous or Asynchronous. |
| • Process reusability. |
| • Transactional complexities |
| o Synchronization |
| o Unit of work |
| o Concurrency |
| • Transaction scope. |
| • Data exchange complexity. |
| • Size of the data set |
| • Structure - are the logical and physical structures similar or not. |
| • Is the data explicitly clear or is the state and process request inferred from data values. |
| • Augmentation - does the data need to be augmented as part of the process in order to complete the transaction |
| • Entity identity management |
| • Process exception complexity |
| 2) Properties of Transaction: |
| • Atomicity: A transaction must be an atomic unit of work |
| • Consistency: On completion a transaction must leave all data in a consistent state. |
| • Durability: The modification persists even in the event of system failure. |
| • Isolation: The changes made by one operation become visible to other concurrent operations. |
| • Serializability: The concurrency control correctness criterion. |
| • Read-Once/Write-All protocol: The replica control protocol. |
| • Query optimization: The process which selects the "best" execution strategy . |
| • Query processing: The process by which a declarative query is translated into low-level data manipulation operations. |
| • Logging protocol: The protocol which records, in a separate location, the changes that a transaction
makes to the database . |
| B. Environment |
| A mobile environment is different from the traditional distributed environment due to its unique
characteristics like the mobility of users and/or resource, the frequent or unpredictable disconnections of
wireless networks, the resource constraints of mobile computing devices, channel unreliability to
limited bandwidth and power consumption. |
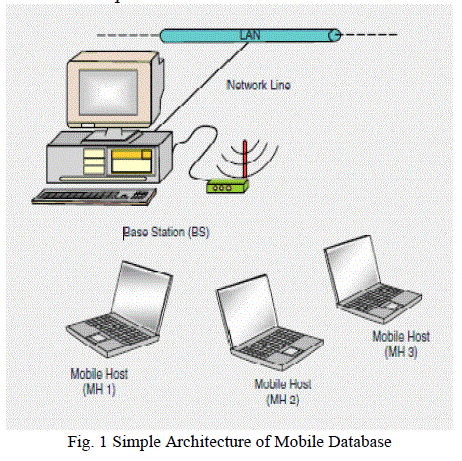 |
| 1) MDS : A mobile database system (MDS) is a distributed system that |
| • Supports mobile connectivity. |
| • Be connected to by a mobile computing device over a mobile network. |
| A mobile database is shown in Fig.1 is a database that can be connected to by a mobile computing
device over a mobile network. The client and server have wireless connections. A cache is maintained
to hold frequent data and transactions so that they are not lost due to connection failure. |
| 2) Examples of Mobile Database Applications: |
| M-Commerce |
| Rescue applications |
| Autonomous Rover Vehicles |
| Homecare Applications |
| 3. MANET: A mobile ad-hoc Network (MANET) is a collection of mobile servers and clients that can
communicate with each other directly via wireless link in the absence of fixed wired infrastructure.
MANET needs to consider specially data replication that is traditionally seen as a way to increase the
availability, reliability and performance of transaction processing. It is an autonomous system of
mobile routers (and associated hosts) connected by wireless links, the union of which form an
arbitrary graph. The routers are free to move randomly and organize themselves arbitrarily, thus the network's wireless topology may change rapidly and unpredictably. Such a network may operate in a
standalone fashion, or may be connected to the larger Internet. Sensor nodes consist of sensing, data
processing, and communication components and typically form ad hoc networks. Due to a lack of
infrastructure support, each node acts as a router, forwarding data packets for other nodes. We
assume that each device of mobile ad-hoc network runs a local database that performs the transaction
and data management functions. Each client may offer its mobile database content to other
participants through a web service. Although a mobile database continues working even when the
wireless connection breaks up, it cannot communicate with other nodes, thus it cannot receive service
requests or send service results. |
| C. Differences between Mobile Ad-Hoc Network and Fixed-Wired Network Transaction Processing |
| If we compare traditional transaction processing in fixed-wired environments with transaction processing in mobile
environments, we can identify the following new challenges that are induced by the mobile character of a network
and its underlying applications |
| 1)Enhanced Failure Model: Compared to fixed-wired networks, mobile environments suffer from a variety of
failures: Message loss occurs in fixed wired networks due to rare problems like buffer over-flows or data
packet collisions. In mobile networks, however, message loss occurs more frequently. For example, if the sender or
receiver moves out of scope, if the channel suffers from interference, if obstacles hamper the transmission, or if the
sender’s or receiver’s battery drains suddenly during message transmission. Network partitioning due to the
movement of participants occurs in mobile environment more frequently than in fixed-wired networks, in
which this event is very seldom. |
| 2) Message Reception Model:In mobile ad-hoc networks, a message that is sent is not only received by the
destined recipient. Each participant that is close to the sender can hear the message. When a routing strategy is
used, participants those are located close to the path that the message takes will get the message. |
| 3) Device Controllability: Distributed databases in fixed-wired networks are usually used for performance and
availability reasons. Thus, there is often a single database owner that controls all of its databases. In mobile
networks, however, each user owns and controls only a single device. In case of wireless network, we cannot
guarantee that all individual users cooperate and do not move away, since there is no central instance that
controls the devices. |
| 4) Compensation Applicability:Transaction processing models that apply the concept of compensation, explicitly
allow databases to run into a possibly inconsistent state that is compensated later. However, the models using
compensation assume that databases are some how connected to a single site that controls the compensation.
Thus, participants having inconsistent states will not participate in proceeding transactions with different
participants as long as their inconsistent states have not been compensated. |
| 5)Capabilities : The mobile devices have limited capabilities like memory, processing, and storage constraints. |
| 6)Input Mechanism(s):The most common input mechanisms for mobile devices are built-in keypads, pens and
touch screen interfaces. Usually, PDAs contain software keyboards, some PDAs may also support external
keyboards. |
| 7)Network Stack is shown in Table I and wireless ISO layers is shown in Table-II. |
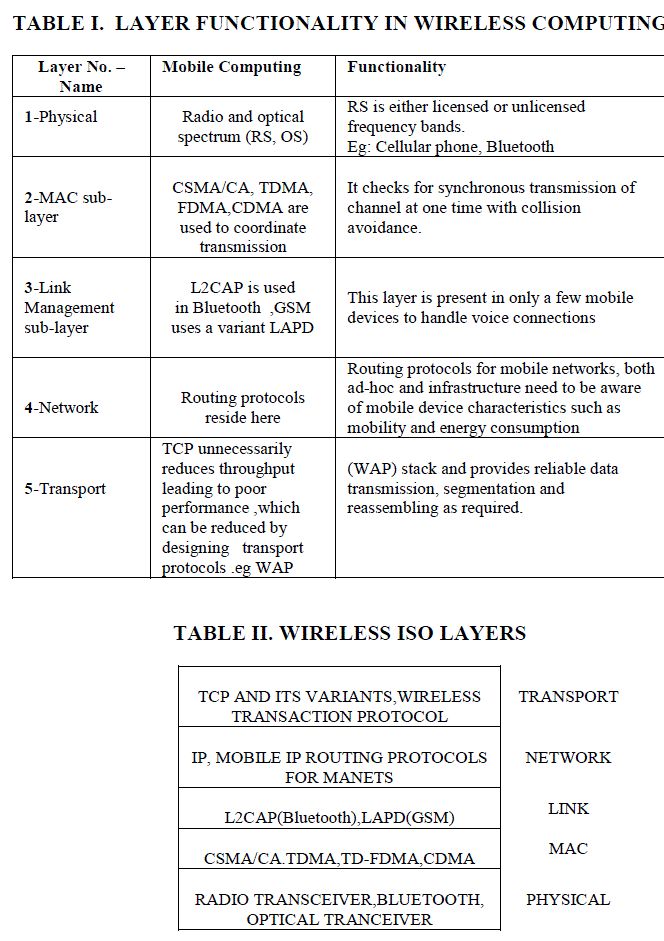 |
| D. Database Management Issues with regards to mobile environment |
| • Mobile users must be able to work with even poor wireless connection. |
| • Applications must provide significant interactivity. |
| • Applications must be able to access local device/vehicle hardware, such as printers, barcode scanners, or GPS
units (for mapping or Automatic Vehicle Location systems). |
| • Bandwidth must be conserved (a common requirement on wireless networks that charge per megabyte or
data transferred). |
| • Users don't require access to truly live data, only recently modified data. |
| • Limited life of power supply (battery). |
| • The changing topology of network. |
| • Replication /Caching. |
| • Hands-off. |
| • Disconnection (Voluntary, Involuntary). |
| • Varying resources. |
| • Communication constraints(wireless communications are slow(e.g., 9.6 kbps in GSM and up to 170 kbps in
GPRS)) |
| • Unreliable(Interference). |
| • Limited capabilities of the mobile devices(storage constraints). |
WORK DONE ON TRANSACTION MANAGEMENT IN MOBILE DEVICES |
| A . ACID Properties: |
| Problem: (complete/partial) Satisfiability. |
| Solution: Consistent operation during disconnection has been also extensively addressed in the context of
network partitioning .the first file systems designed to support disconnections and weak connectivity is
isolation transaction in Coda. |
| B. Commit Protocols |
| Commit Protocols are magnificent sources of committing transactions, maintaining data, integrity and
consistency. Problem: Difficulty in maintaining atomicity, integrity and consistency.
Solution: Atomic commit protocols (ACPs) like 2-Phase-Commit, 3-Phase-Commit and consensus based
protocols are used to guarantee an atomic execution of distributed transaction in fixed network. |
| C. Concurrency Control |
| Concurrency is defined as the ability of multiple processes and threads to access and change the data records
at the same time . There are two approaches pessimistic concurrency, optimistic concurrency.
Problem: Inconsistent Analysis, Lost Update problem and uncommitted dependency.
Solution: The above problems can be solved by using concurrency control technique called locking. |
| D . Caching/ Replication |
| Caching and replication generally attempt to guarantee that most data requests are for data that is being held in
main memory or local storage, negating the need to perform I/O, or a remote data retrieval. |
| Problem: The performance considerations go beyond simple speedups and data retrieval delays. |
| Solution: Data are cached at the mobile device in order to avoid excessive energy consumption and to cope
with intermittent connectivity. Preloading or perfecting called as hoarding is used to sustain
disconnection. |
| E. Data Dissemination |
| Data dissemination models are concerned with read-only transactions where mobile clients can pull information
from
sources, or the sources can push data automatically.
Problem : Generating Invalidation Report.
Solution: Statefull/Stateless Synchronous/Asynchronous approaches are used. |
| F. Location-Based Services |
| These approaches depend on the way the moving objects are modeled ,managed and the types of locationdependent
queries used .
Problem : Location-Dependent Query Processing.
Solution: exploiting the dynamic features of the mobile environment to provide user with context-aware
information. |
| G. Security |
| Security has greater significance in a mobile environment than in a wired environment. |
| Problem: The current Bluetooth security protocol uses procedures that have low computation complexity, so
they are susceptible to attacks |
| Solution: Research in securing routing protocols for networks using peer-to-peer architectures has resulted in interesting protocols such as Ariadne [Yih-Chun Hu and Adrian Perrig and David B. Johnson] .The Wireless
Transport Layer Security protocol is the only known protocol for securing transport layer data in mobile
networks. |
CONCLUSION |
| In this paper we have explained about the environment of mobile devices ,Issues related to it and the protocol related
to wireless environment .The types of problems in different protocol and its solution being an issue to be solved in
future by different researcher in different ways because of the increasing demand and use of wireless devices.
Wireless devices has some constraints but still it is in demand because of the improvement in handheld and wearable
devices, which would lead to a significant increase in the deployment of mobile computing applications in the near future, even though not all of the underlying problems would have completely wrapped up solutions in the short term, it
acts as an area which need to be more explored. |
References |
- C.J.Date, A.Kannan, S.Swamynathan ―An Introduction to Database Systems,PearsonEducation,Sixth Impression,2008.
- Thomas Connolly, Carolyn Begg,DataBaseSystem:A Practical Approach to Design, Implementation and Management, 3rd ed.,Dorling Kindersley(India)Pvt. Ltd. ,New Delhi,2006
- Sebastian Obermeier ―Database Transaction Management in Mobile Ad-Hoc Networks ― , Dissertation Copy 2008
- JochenSchiller , ―Mobile Computing , AddisionWisley, Edition 2,2003
- Albert Held Sven Buchholz, Thomas Ziegert and Alexander Schill ,Transaction Processing in a Mobile Computing Environment with Alternating Client Hosts
- Thomas Connolly and Carolyn Begg ,Database System ―, Addison Wisely, Edition 2,1998
- PreethiVishwanath , ―Mobile Ad Hoc Network Security(PPT).
- Magnus Frodigh, Per Johansson and Peter Larsson,Wireless ad hoc networking—The art of networking without a network ― , First published in Ericsson Review no. 04, 2000
- Mobile Ad hoc Networks (MANET) http://www.ietf.org/html.charters/manetcharter.htm (2000-05-28).
- Vijay Kumar,Magaret H Dunham,NitinPrabhu ,AyseYaseminSeydim,A Timeout Based Mobile Transaction Commitment Protocol ,IEEE,OCT 2002
- SilberschatzKorth and Sudharshan , ―Database Concepts ― ,Pearsons Publication,5 Edition
- VaheAmirbekyan, Krzysztof Zieliñski ,―The Role of Transaction Management in CORBA/ODB Integrated Systems' Performance,2000 ACM Symposium on Applied Computing, March 19-21,2000,Italy.
- Lidong Zhou and Zygmunt J. Haas ,Cornell University ,Secured Adhoc Networks,1999 IEEE.
- CHI-FU HUANG, HUNG-WEI LEE and YU- CHEE TSENG, ―A Two-Tier Heterogeneous Mobile Ad Hoc Network Architecture and Its Load- Balance Routing Problem, Kluwer Academic Publishers, Netherlands 2004.
- A.Climent et al., ―Alternative Strategies for Concurrency Control in Distributed Database Systems ―, Technical Report TR/2000-10, Enginyeria La Salle, 2000.
- D.RoselinSelvarani,T.N.Ravi ,A Survey on Data and Transaction Management in Mobile Databases,IJDMS vol4 ,No. 5,Oct 2012.
- Matthias Wiesmann and Andre Schiper,Comparision of Database Replication Techniques Based on Total Order Broadcast,IEEETransaction on Knowledge and Data Engineeering,Vol17,No. 4 ,April 2005.
- Samba Sesay,Zongkai Yang and Jianhua He, A Survey on Mobile Ad Hoc Wireless Networks,Information Technology Journal 3(2),2004, Asian Network for Scientific Information.
- Sanjay Kumar Madria and Sourav S.Bhowmick,Mobile Data Management,IEEE Journal Nov 2001.
- Vishnu Swaroop ,UdaiShanker,Mobile Distributed Real Time Database Systems:A Research Challenges ―,International Conference on Computer and Communication Technology ,2010.
|