Mobile cloud computing usually consists of front-end users who possess mobile devices and back-end cloud server. This paradigm empowers users to pervasively access a large volume of storage resources with portable devices in a distributed and cooperative way. During the period between uploading and downloading files (data), the privacy and integrity of files need to be guaranteed. To this end, families of schemes are proposed for different situation. All scheme are lightweight in terms of computational overhead resilient to storage compromise on mobile devices, and do not assume that trust cloud servers are present. We firstly propose an encryption based scheme for the situation of single accessible CS. Next, we propose a coding based scheme for the situation that multiple CSs are available without relying on encryption. We finally propose a sharing based scheme to further decrease the computation overhead by only relying on exclusive-or operation. Also we extend our work to energy consumptions. We provide an analysis of the critical factors affecting the energy consumption of mobile clients in cloud computing.
Keywords |
| Mobile Computing, Cloud Computing, Cloud Gaming, and Multimedia Applications. |
INTRODUCTION |
| Mobile devices (e.g., smart phone, tablet pcs, etc) are increasingly becoming an essential part of human life as the
most effective and convenient communication tools from mobile applications (e.g., iPhone apps, Google apps, etc),
which run on the devices and/or on remote servers via wireless networks. The rapid progress of mobile computing
(MC) becomes a powerful trend in the development of IT technology as well as commerce and industry fields the
mobile devices are facing many challenges in their resources (e.g., battery life, storage, and bandwidth) and
communications (e.g., mobility and security).Cloud computing (CC) has been widely recognized as the next
generation’s computing infrastructure. |
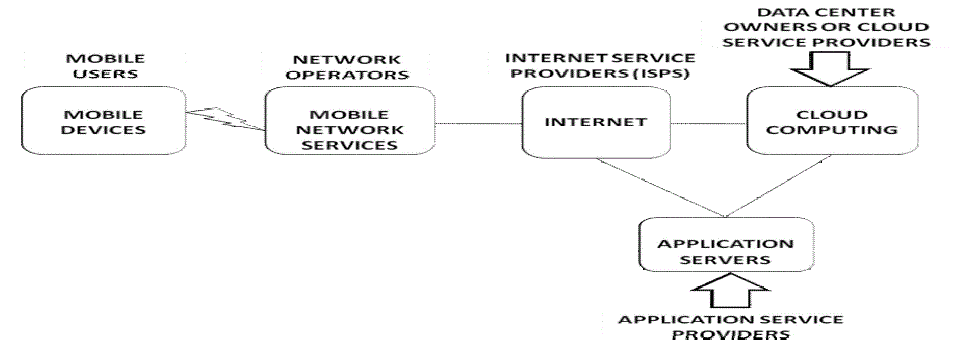
| CC offer some advantages by allowing users to use infrastructure (e.g., servers, networks, and storages), and
software’s provided by cloud providers (e.g., Google, Amazon, and Sales force) at low cost. With the explosion of
mobile applications and the support of CC for a variety of services for mobile users, mobile cloud computing (MCC) is
introduced as an integration of cloud computing into the mobile environment. Mobile cloud computing brings new
types of services and facilities for mobile users to take full advantages of cloud computing. This paper presents a
comprehensive survey on mobile cloud computing. Then provide a brief overview of MCC including definition,
architecture, and its advantages. |
RELATED WORK |
| In [14] authors may be promising to investigate an alternative approach Cloud Mobile Gaming (CMG), where cloud
servers are responsible for executing the appropriate gaming engines, and streaming the resulting game video to the
client devices. Two challenges which are vital for the success of CMG approach: 1) communication constraint in terms
of limited and fluctuating mobile network bandwidth 2) computation constraint reflected by the available server
computing resource for each client. Streaming game video over the bandwidth constrained wireless network may cause
unexpected delay and packet loss, leading to an increase in response time besides adverse impact on the video quality,
thereby unacceptable gaming experience. In [6] authors enabling mobile Internet gaming will significantly change the
experience of mobile users from thin, single player gaming possible today to rich, multi-player Internet gaming
experience, of their familiar games from anywhere. A cloud server based mobile gaming approach, termed Cloud Mobile Gaming (CMG), where the burden of executing the gaming engine is put on cloud servers and the mobile
devices just communicate the user’s gaming commands to the servers. In [15] mobile video games and the gaming
experience remain constrained in two ways: 1) unlike the richness and interactivity of Internet/PC games, current
mobile video games are very light-weight, both in terms of graphics/features supported, as well as the content in the
case of mobile versions of Internet games; and 2) unlike the multiplayer capability, and the associated social
networking, that made Internet/PC video gaming so popular, current mobile video games are primarily single player
games. Enhance the Mobile Gaming User Experience (MGUE) model to address cloud server latency and scalability
issues that may be faced in real deployment scenarios with significant number of mobile game players. In [7] Authors
Consider resource allocation and job scheduling problem of the data analytics cluster in the cloud. A resource
allocation strategy that (1) divides machines into two pools core nodes and accelerator nodes and (2) dynamically
adjusts the size of each pool to reduce cost or improve utilization. In [4] authors propose a joint scheduling adaptation
algorithm that can systematically leverage adaptation techniques introduced in to adapt the communication needs of in
service users if the available wireless network bandwidth is not sufficient for a new CMG user. Our simulation
outcome express that the use of WCS and the joint scheduling adaptation algorithm, can extensively improve the
performance of the CMG approach, increase the number of simultaneous CMG sessions that can be supported, while
maximize aggregate MGUE and minimize the average cloud service cost. |
PROBLEM STATEMENT |
| We envision media rich cloud based mobile applications to emerge, besides many current mobile media services
migrating to the cloud. These developments can lead to new and efficient mobile media experiences, and thereby
revenue growth opportunities. However, as pointed in this section, several technical and eco-system challenges will
need to be addressed, including ensuring high availability, data integrity and user privacy, lowering energy
consumption and cooling costs, ensuring response time and user experience over wireless networks, and reducing cloud
service cost associated with high computing and bandwidth needed by CMM applications, and thereby ensuring service
scalability. |
| A. Online JREA Algorithm |
| It addresses the challenge of fluctuating and band-width constrained wireless network by judiciously utilizing the
power of changing the video source through rendering adaptation, with large impact on network bandwidth needed,
together with adapting the video encoding bit rate address relatively small but frequent network bandwidth fluctuations.
The motivation for developing an online Joint Rendering and Encoding bit rate Adaptation (JREA) algorithm. We next
describe the steps of the JREA algorithm, which decides when and how to switch the Communication Complexity
(CommC) rendering level Computation Complexity (CompC) rendering level and the encoding bit rate during a
gaming session in response to the current network conditions and server utilization. Adapting both rendering and video encoding jointly will necessitate understanding the optimal values (leading to a joint adaptation model) of encoding bit
rate or rendering level that can be used when encoding or rendering is adapted respectively. |
| The first step is to decide the encoding bit rate used to encode the rendered video. During a short time interval, if the
network Round trip Delay (RDelay) keeps increasing and its average value is greater than minimum Acceptable
RDelay JREA algorithm will reduce encoding bit rate. On the other hand, if for a significant time, RDelay remains
below and there is no packet loss, it will increase the encoding bit rate. |
| The second step is to check and update CommC rendering level. After the first step, the new encoding bit rate may
be below the Minimum Encoding Bit Rate (MEBR) for the current CommC rendering level, which will lead to an
unexpected user experience as we discussed before. But this happen, JREA algorithm has to reduce CommC rendering
level to reduce the Minimum Encoding Bit Rate. On the other hand, if the CommC rendering level has not been
changed for over a certain significant period, it will be updated and changed to the Maximum CommC Rendering Level
(MCRL) depending on the current encoding bit rate. |
| The third and last step is to decide on CompC rendering level, depending on server utilization (ServUtil). If ServUtil
is over, the lower CompC rendering level is selected. Otherwise, if CompC rendering level has not been changed for
more than time, and ServUtil is below, it increases CompC rendering level by 1.Next, based on the new selected
CommC and CompC rendering levels JREA algorithm will use the optimal rendering settings from to update the game
graphic engine, as it use the new selected video bit rate to update the video encoder. |
PROPOSED SYSTEM |
| We focus on the storage outsourcing in distrusted CSs (computation outsourcing is usually conducted in trusted
CSs). After a MD creates a file and processes it, it may upload the file into a CS or multiple CSs. Host user or other cooperators
may access it in the future distributed. Obviously, the privacy and integrity of the file must be maintained in
the storage of CSs during the period between uploading and accessing. We extend our work to provide an analysis of
the critical factors affecting the energy consumption of mobile clients in cloud computing. Further, we present our
measurements about the central characteristics of contemporary mobile handheld devices that define the basic balance
between local and remote computing. We also describe a concrete example, which demonstrates energy savings. |
| A. Encryption based Scheme (EnS) |
| In this scheme, file encryption and integrity checking are conducted by MD (Mobile Device) itself, as called. |
| Level-1 Uploading Process: |
| (1) Before uploading files F into CS, MD prompts for asking U to input a password, denoted as PWD. |
| (2) MD generates encryption key (EK= H(PWD) ||FN || FS) and integrity key (IK=H(FN) || PWD||FS) , where FN is
the name of the file F (character string will be changed to bit string), and FS is the size of the file F. |
| (3) MD encrypts F with EK as F′ = ENC (F, EK).MD generates file integrity authentication code, denoted as
MAC = {H (F, IK)}. |
| (4) MD sends {F′ || H (FN) ||MAC} to portal CS. MD stores T = ⟨FN⟩ locally and deletes EK and IK. |
| Level-2 Downloading Process: |
| (1) Suppose MD wants to fetch F with the name FN, MD then sends H(FN) to CS. CS searches in ⟨F′,H(FN),MAC⟩
sends back {F′ ||MAC} that matches H(FN) to MD. |
| (2) MD prompts for asking U to input corresponding PWD for the FN. |
| (3) MD generates encryption key EK= H(PWD || FN || FS) and integrity key IK = H(FN || PWD || FS), where FS is
the size of F′, |F′ |= |F |= FS . |
| (4) MD decrypts out F = DEC (F′, EK), and checks whether MAC = H (F, IK) is held. |
| B. Coding based Scheme (CnS) |
| We observe that under some situations multiple s CS may be presented. To further decrease the computation
overhead of encryption function in power consumption, we propose a Coding based Scheme called CoS without
encryption function but maintaining the secrecy of F as follows. |
| C. Shared based Scheme (CnS) |
| To further decrease the computation overhead, we propose a Sharing based Scheme. The scheme applies a simple
(n,n) xor-based secret sharing method. That is, for sharing a secret s in n holders such that s can be recovered only
when n holders are present, randomly generates n −1 shares and computes the last share. |
| D. Energy trade-off analysis |
| In the context of cloud computing, the critical feature for mobile clients is the trade-off between energy consumed
by computation and the energy consumed by communication. We need to consider the energy cost of performing the
computation locally (Elocal) versus the cost of transferring the computation input and output data (Ecloud).The
proposed system also extend to analyzed the energy consumption of mobile clients in cloud computing. There are many
factors that make cloud computing an attractive technology, but energy consumption is a fundamental criterion for
battery powered devices and needs to be carefully considered for all mobile cloud computing scenarios. In this module
we analysis and compare the performance of the proposed system in the term of security, privacy, energy and
computation overhead. |
FUTURE DIRECTIONS TO ADDRESS CMM CHALLENGES |
| We have presented an adaptive mobile cloud computing approach to address the challenges associated with Cloud
Mobile Gaming, one of the most computing and communication intensive Cloud Mobile Media applications. We will
conclude this paper by discussing two additional new approaches which we believe can significantly help address the
user experience, cost and scalability challenges associated with CMM applications. A critical challenge for CMM applications is the latency and jitter associated with the uplink and downlink transmissions between the mobile device
and the Internet cloud servers. |
| Moreover, the transmission of large amount of content between cloud servers and mobile devices, inherent in CMM
applications, poses a major concern for the capacity of the networks to enable CMM applications. A promising
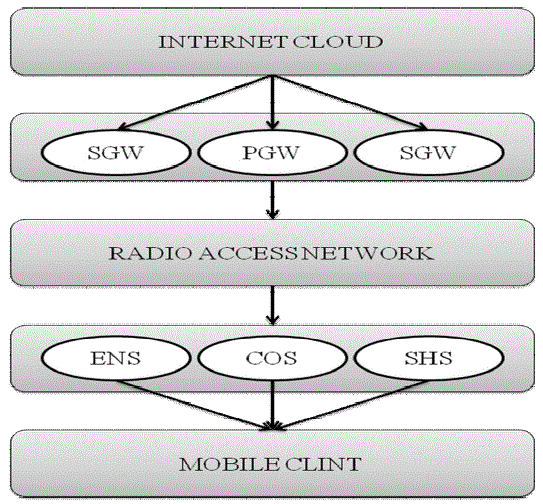
direction will be to bring cloud computing to the edge of the mobile network, supplementing gateway nodes in the
mobile Core Network (CN), and edge nodes like base stations in Radio Access Networks (RAN), and Femto and WiFi
access points, with computing and storage resources, to form a true Mobile Cloud. |
| With a Mobile Cloud architecture, content processing (like graphic rendering or video encoding) and retrieval can be
performed at the edge of the mobile networks, as opposed to in Internet clouds, thereby reducing round trip network
latency, as well as reducing congestion in the mobile CN and RAN. While the direction of Mobile Cloud looks
appealing, there are multiple challenges that need to be addressed. Since there are thousands of base stations and access
points, the proposed Mobile Cloud will be a massively distributed network of smaller computing and storage resources,
as opposed to the more centralized architecture of Internet clouds consisting of a few data centres with much larger
computing and storage footprints. The above difference has interesting implications and challenges. |
| These techniques do not consider the mobile network constraints, which is an important scalability challenge for
CMM applications. Our initial work developing mobile cloud scheduling techniques for Cloud Mobile Gaming has
shown promising results: the ability to significantly increase the number of simultaneous CMG users using available
network resources, while reducing cloud cost. In the future, mobile cloud scheduling techniques will need to be
developed for other CMM applications, as well as consider capacity limited computing and storage resources in the
Mobile Cloud. |
CONCLUSION |
| We proposed schemes for protecting the confidentiality and integrity of uploading files or data in mobile storage
cloud. The scheme EnS tackles the situation where only one cloud server exists. We proofed that it guarantees the
security goal and the necessary condition for this situation. The scheme CoS can avoid the computation of encryption
algorithm in the situation that multiple cloud servers exist by applying linear coding. The scheme ShS can further
decrease the computation overhead by relying only on exclusive-or operations. All proposed schemes are resilient to
the storage compromise on mobile devices, and all assume that the cloud servers are distrusted. We have also analyzed
the energy consumption of mobile clients in cloud computing. There are many factors that make cloud computing an
attractive technology, but energy consumption is a fundamental criterion for battery powered devices and needs to be
carefully considered for all mobile cloud computing scenarios. While energy can be a challenge for mobile cloud
computing, it is also as an opportunity. |
Figures at a glance |
 |
 |
| Figure 1 |
Figure 2 |
|
| |
References |
- S. Wang and S. Dey, “Adaptive Mobile Cloud Computing to Enable Rich Mobile Multimedia Applications”, IEEE Transactions on Multimedia, Vol No. 15,Issue No. 4, pp870 – 883, June 2013.
- Yi xu, shiwenmao, “A Survey of Mobile Cloud Computing for Rich Media Applications”, IEEE Transaction on WirelessCommunications ,Vol No: 20, Issue: 3 pp46 – 53, June 2013.
- H. Ahlehagh and S. Dey, “Video caching in radio access network”, IEEE Transaction on Wireless Communications and NetworkingConference (WCNC), pp1525-3511, Apr. 2012.
- S. Wang, Y. Liu, and S. Dey, “Wireless network aware cloud scheduler for scalable cloud mobile gaming,” IEEE InternationalConference on Communications (ICC), pp2081 – 2086, June. 2012.
- H. Ahlehagh and S. Dey, “Hierarchical video caching in wireless cloud: Approaches and algorithms,” IEEE International Conference onCommunications (ICC) Workshop on Realizing Advanced Video Optimized Wireless Networks, pp 7082 - 7087, June. 2012.
- S. Wang and S. Dey, “Cloud mobile gaming: Modeling and measuring user experience in mobile wireless networks,” in Proc. ACMSIGMO-BILE MC2R, 2012, Vol No. 16, Issue No. 1, pp. 10–21, Jan 2012
- G. Lee, B. Chun, and R. Katz, “Heterogeneity-aware resource allocation and scheduling in the cloud,” in Proc. 3rd USENIX WorkshopHot Topics in Cloud Comput., Jun.2011.
- H. T. Dinh, C. Lee, D. Niyato, and P. Wang, “A survey of mobile cloud computing: Architecture, Applications, and Approaches,”Wirel.Commun.Mob. Comput, 13: 1587–1611. doi: 10.1002/wcm.1203, Oct 2011.
- Y.-T. Lee et al., “World of warcraft avatar history dataset,” in Proc. ACM Multimedia Syst., 2011.
- GirishSolurVirupakshaiah, “Study of Energy Efficiency in Portable Devices Using Cloud Computing; case of multimedia applications”in Proc Multimedia Applications., 2010.
- S. Wang and S. Dey, “Addressing response time and video quality in remote server based internet mobile gaming”, IEEE WirelessCommunications and Networking Conference (WCNC), pp 1-6, Mar. 2010.
- R. Bossche, K. Vanmechelen, and J. Broeckhove, “Cost-optimal scheduling in hybrid IaaS clouds for deadline constrained workload”, IEEE 3rd International Conference on Cloud Computing (CLOUD), pp 228 – 235, Jul. 2010.
- Neil Robinson, “The Cloud: Understanding the Security, Privacy and Trust Challenges” in Proc. Directorate-General Information Society and Media, European Commission, November 2010.
- S. Wang and S. Dey, “Rendering adaptation to address communication and computation constraints in cloud mobile gaming”, IEEEGlobal Telecommunications Conference (GLOBECOM 2010),pp 1–6, Dec. 2010.
- S. Wang and S. Dey, “Modeling and characterizing user experience in a cloud server based mobile gaming approach”, IEEE GlobalTelecommunications Conference (GLOBECOM), pp 1 - 7, Dec. 2009.
|