ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
R.S.Varshini dhevi1 and D.Vijendra Babu2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
A wireless sensor network (WSN) is a collection of nodes organized into a cooperative network. Security and energy consumption have been considered as long-lasting technical challenges in WSNs, as sensors usually suffer from complexity and energy constraints. In particular, it has played an important role in such applications that require proactive actions responding to rapid changes of outside environments. In order to provide data confidentiality in a distributed detection scenario, a simple and efficient physical-layer security is studied. Specifically, to prevent passive eavesdropping on transmitting data from sensors to an ally fusion center (AFC), we propose a novel encryption scheme and decision fusion rules for a parallel access channel model. The proposed scheme takes advantage of a free natural resource, i.e., randomness of wireless channels, to encrypt the binary local decision of each sensor in such a way that the binary local decision is flipped according to instantaneous channel gain between the sensor and AFC. The location-specific and reciprocal properties of wireless channels enable the sensor and AFC to share the inherent randomness of wireless channels which are not available to an eavesdropper. Furthermore, it is shown that the scheme is well-suited to a low complexity and energy efficient modulation technique, non-coherent binary frequency shift keying. To evaluate performances of the proposed Scheme, log-likelihood-ratio-based decision fusion strategies at the AFC are analyzed, and comparisons of decision performances are carried out. In addition, we prove that the proposed scheme achieves perfect secrecy with a simple structure that is suited for sensors of limited complexity.
Index Terms |
| Decision fusion, distributed detection, eavesdropping, encryption, perfect secrecy, wireless sensor networks. |
INTRODUCTION |
| In recent years, wireless sensor networks (WSNs) have gained worldwide attention for use in different applications. Sensor nodes are spatially distributed across a large area of interest to sense, measure, and gather information and transmit the data to the user. The nodes are typically equipped with radio transceivers, micro-controllers, and batteries. They are small in size, inexpensive, and could be deployed in large numbers. They can be used in applications such as military target tracking and surveillance, natural disaster relief, biomedical health monitoring, and industrial automation |
| The uses of WSN for industrial applications are expected to open large opportunities for collecting data, enabling remote control, and automation to improve the safety and productivity of facilities. Unlike wire-based systems, WSNs can be deployed in bearings of motors, oil pumps, whirring engines, or other inaccessible or hazardous environments. In general, wireless solutions are considered to be cheaper compared to wire-based systems. This is due to the cost associated in shielding wires to prevent severe conditions which are usually present in these harsh environments (high humidity, high temperature, strong vibration, etc.). Shortrange wireless technologies such as IEEE 802.15.4 in mesh network configuration are widely considered to be cost effective solution for use in industrial settings. |
| In harsh industrial environments, noise is significant due to the wide operating temperatures, strong vibrations, excessive electromagnetic noise caused by large motors, etc.. Interferences from other wireless systems operating on the same frequency band might also be present. In addition, the signal might be subject to heavy multipath propagation effects caused by multiple reflections from mainly metallic structures in the surrounding environment. The random/periodic movement of people, robots, trucks, and other objects may also cause time varying channel conditions. Effects of the aforementioned propagation impairments to mission-critical signals in industrial settings can result in costly disasters in terms of money, manpower, time, and even human lives. Thus, knowledge of the propagation channel is needed to successfully design and evaluate robust WSNs for industrial applications. II. SYSTEM MODEL AND WORKING PROCESS From military to civilian applications, binary distributed detection problems in wireless sensor networks (WSNs) have been introduced in a wide range of areas such as military surveillance, disaster recovery, environmental monitoring, inventory management, and many others. In particular, it has played an important role in such applications that require proactive actions responding to rapid changes of outside environments. Early warning system such as intrusion detection and disaster alert, network control in the self-organized network, and spectrum sensing in the cognitive radio are the notable ones that the the binary distributed detection can be applied to prevent a potential conflict or crisis. Moreover, in practice, sensors for the distributed detection in WSNs are often incapable of employing traditional cryptographic techniques due to practical constraints of sensors such as limited energy resources, computing power, etc |
| To resolve the technical challenge of secure communications in WSNs, there have been several notable approaches, where the ability of the physical layer is explored as a solution to the data confidentiality for the distributed detection in WSNs. Assuming the presence of a passive eavesdropper called an enemy fusion center (EFC), sensors in a WSN individually or collaboratively transmit their local decisions on a target state to an ally fusion center (AFC), where final decision is made. In this case, the central issue is how to design a physical layer scheme at the sensors to achieve reliable transmission with the AFC while preventing information leakage to the EFC. |
| In, it is found that simultaneous transmission of local decisions using the type-based multiple access (TBMA) protocol over a multiple access channel (MAC) can be utilized for the data confidentiality in costly disasters in terms of money, manpower, time, and even human lives. Thus, knowledge of the propagation channel is needed to successfully design and evaluate robust WSNs for industrial applications. |
SYSTEM MODEL AND WORKING PROCESS |
| From military to civilian applications, binary distributed detection problems in wireless sensor networks (WSNs) have been introduced in a wide range of areas such as military surveillance, disaster recovery, such a way that some sensors are deliberately selected to transmit interfering signals to make the EFC confused. Since all the transmitting data from sensors are naturally fused during transmission over MAC, the EFC is unable to remove the interfering signals, which thus hinders it from making a correct decision. In particular, the rule selecting the sensors generating interference is designed 1) to minimize the degradation of detection performance at the AFC and 2) to be autonomous and nondeterministic, which prevents the EFC from identifying the sensors generating interference. It is shown that, by taking advantage of the inherent randomness of wireless channels, the design goals can be achieved. The results in further show that the proposed scheme provides both reliability and information-theoretic perfect secrecy for distributed detection. Although the scheme reduces the complexity and power consumption required for the security goal at each individual sensor level, the power consumption across the entire sensor network may get even higher due to the wasted energy for generating the interference. In addition, the scheme assumes coherent communications from the sensors to the FCs, which requires full channel state information in the sensors, namely, amplitudes and phases of their channel gains, and thus may be too complicated to be implemented in some applications. On the other hand, the work is addressed the data confidentiality issue over a parallel access channel (PAC) where sensors individually access to the AFC through orthogonal channels. |
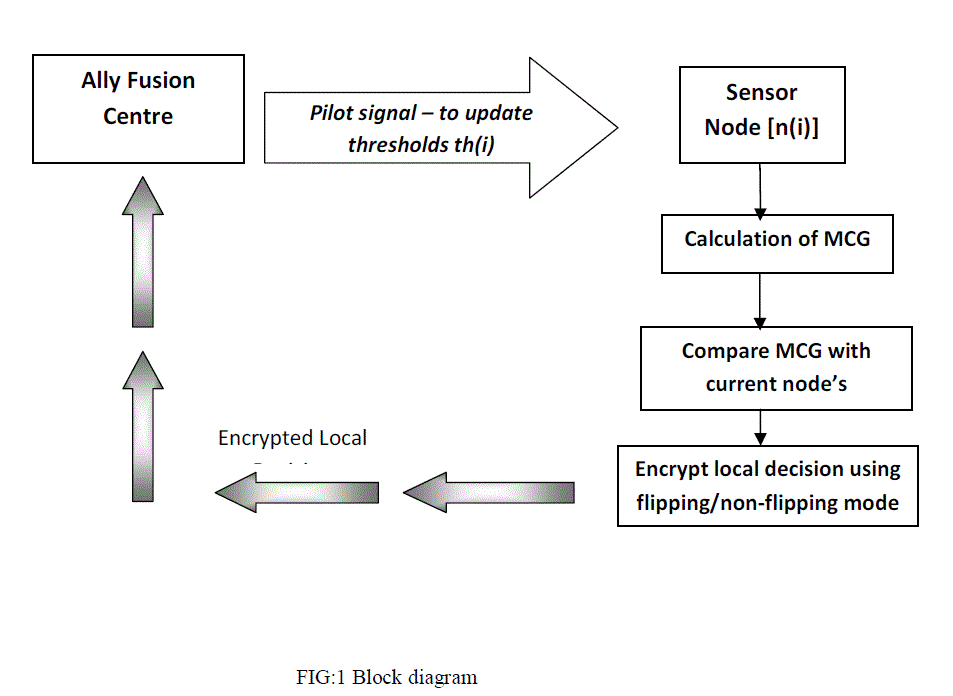 |
| In this scheme, each sensor intentionally induces decision errors by randomly flipping its binary local decision before transmitting it. The rates of intentionally induced errors are assumed to be known at the AFC and sensors a priori except for the EFC. In it is shown that the scheme enables the AFC to detect the target state reliably while resulting in sufficiently high detection error rate at the EFC. This approach seems simple and efficient but basically does not eliminate the key distribution problem since the a priori shared error rates between the AFC and sensors can be understood as a pre shared key. In addition, the detection error rate is a relaxed measure of security that does not guarantee the information-theoretic perfect secrecy. |
| In this paper, we study a transmission scheme at the physical layer to secure the transmission from sensors to the AFC over a PAC without resorting to secret key sharing. |
| In addition, the proposed scheme aim at achieving the information-theoretic perfect secrecy, which is not possible with traditional cryptographic techniques. For this work to be more practical, we consider a simple and energy efficient modulation technique, but not limited to, non coherent binary frequency shift keying (NC-BFSK). NC-BFSK known as green modulation is widely employed in WSNs as a realistic option (e.g., MICA2 Motes ) thanks to its low cost and complexity in implementation. |
A. System Model |
| In the proposed scheme, it is assumed that the AFC broadcasts a pilot signal to initiate distributed detection, and each sensor measures the strength of the received pilot signal, which is equivalent to measuring the magnitude of the channel gain (MCG) from the AFC to the sensor. Since a simple energy detector is enough to measure the pilot signal strength, the required additional complexity may be acceptable in many cases. Then, each sensor autonomously joins one of three groups, dormant, flipping, and non flipping groups, according to their MCG measurements whenever the AFC broadcasts the pilot signal. The sensors in the flipping and non ffipping groups are called activated sensors, and they report their local decisions over a PAC in the time-division duplexing (TDD) manner. |
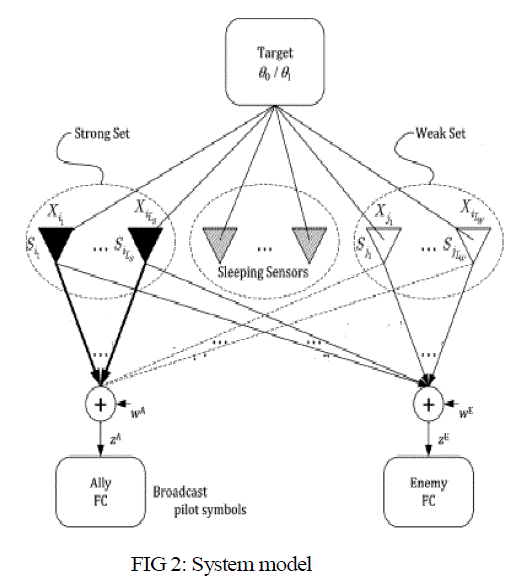 |
| That is, the transmission from the sensors are carried out in the same coherence time over the same wireless channel where the pilot signal is broadcasted. The main idea behind the proposed scheme is that the sensors in the flipping and nonflipping groups send their local decisions to the AFC in the completely opposite ways from each other to make the EFC confused. For example, when two activated sensors involved in the two different groups, i.e., flipping and nonffipping groups, make the same local decision on the target state, the transmitted data from the sensor in one group becomes a bit-flipping version of the other's. Note that the MCGs determining the group assignment of sensors can be seen as an encryption seed obtained from the nature on demand, and thus we need not the assumption i.e., the a priori shared error rates. |
| Meanwhile, at the AFC and EFC, the transmitting data from activated sensors in different groups should be fused in an appropriate way to make a final decision on the target state. Since the activated sensors report their local decisions in the TDD manner in the same coherence time, the received signal strengths at the AFC provide estimates of the MCGs measured at the sensors, and thus the AFC can incorporate such estimates into the fusion. On the other hand, the EFC eavesdrops the signals from the sensors over a statistically independent PAC, and is totally ignorant of the MCGs when it is more than one half wavelength away from the AFC. It should be noted that when compared with the schemes where the signals from the interfering group are used only for confusing the EFC, in the proposed scheme, the signals of the activated sensors from both the flipping and nonffipping groups are combined at the AFC, and thus the energy consumed by sensors to transmit signals is not wasted, which leads to better energy efficiency. |
| Besides the general results of physicallayer security for wireless communications, the proposed scheme is closely related to existing works in three specific areas: 1) secret key extraction from wireless channel, 2) cooperative secrecy, and 3) secret communication using artificial noise. In references there in, wireless channel gains are considered as common randomness exclusively shared by transmitter and legitimate receiver using the TDD protocol. Various schemes to extract secret keys from different types of wireless channels have been extensively studied, e.g., wireless MIMO channels, Ultra-Wide Band channels and multi path fading channel. In WSNs, however, such schemes may be too expensive to be realized in sensor nodes in terms of complexity and/or power consumption. Nevertheless, motivated by the precursory works, we can find a simple but efficient scheme tailored to wireless sensor nodes with constraints of complexity and resources. Novelties of the proposed scheme also lie in judiciously designed cooperations among sensors each of which autonomously conducts different roles, i.e., reporting of their observations and generating interference to confuse possible EFCs. The collective behavior of self-organized sensors achieves the perfect secrecy against passive eavesdropping without requiring high intelligence in the sensors. |
| The works of cooperative secrecy and artificial interference techniques provide a great deal of insight into the techniques we utilize while they are considered in different communication scenarios such as relay networks and point-to-point and multiuser communications. |
| Our contributions in the work are summarized as follows: 1) we derive conditions for the EFC to be totally ignorant of target state, i.e., achieving perfect secrecy, and 2) two decision fusion rules for the AFC are proposed; i) a log-likelihood ratio (LLR) based decision fusion rule with channel statistics and ii) a suboptimal decision fusion obtained from a high signalto- noise ratio (SNR) approximation, and their performances are evaluated. With both reliability and security ensured at the physical layer, our scheme is unique in that it includes an energy-efficient modulation and activation rule of sensors for longer lifetime of WSNs. The claim for security will be thoroughly proved and confirmed by carrying out numerical evaluations of the proposed scheme. In addition, comparisons will be performed, which shows that the proposed scheme outperforms over a broad range of SNR values without compromising the security goals, perfect secrecy. |
SECURITY ANALYSIS |
| In the security analysis of our scheme, the main concern is how much information the EFC can obtain from eavesdropping on the sensors' transmission to the AFC |
A. Perfect Secrecy |
 |
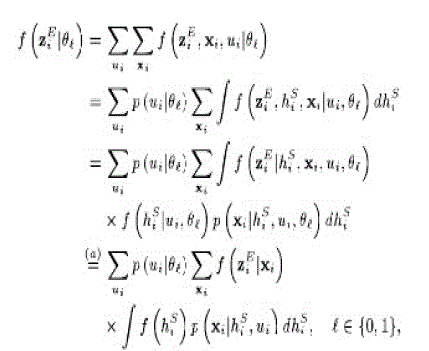 |
 |
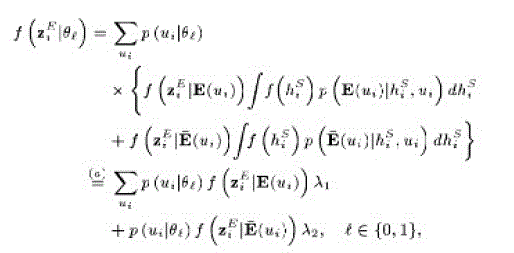 |
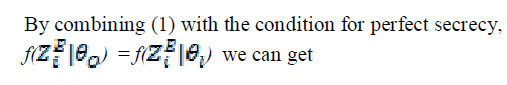 |
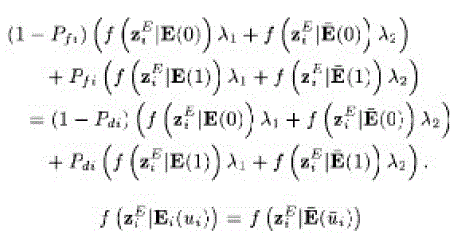 |
| This means that we have to make the sizes of flipping and non flipping groups statistically equal, which is intuitive since equally likely contradicting reports must make the EFC totally confused, which provides perfect secrecy. |
B. Security against Cryptographic Attacks |
| In addition to perfect secrecy against eavesdropping, we further analyze the strength of our proposed scheme against two well known attacks in cryptanalysis where the EFC can attempt to decrypt the captured signals without prior access to an encryption seed. |
| 1) Known Plaintext Attack: In cryptanalysis, it is assumed that an attacker can take some pairs of the plaintext and its encrypted data, i.e., cipher text. In this case, the attacker can obtain secret information such as an encryption seed by analyzing correlation between them. This problem can happen in our scenario if the EFC has prior knowledge about the target state. Comparing the captured signals (cipher text) from the activated sensors with the known target state (plaintext), the EFC can immediately know the group assignment of sensors and their individual encryption seeds. However, such an attempt to attack becomes in vain in our scheme, because each sensor update its encryption seed in every reporting session based on its instantaneous MCG, which is purely random and independent in each session. Even if the EFC obtains all the encryption seeds for activated sensors in a certain time period, they are disposable ones that are useless in the next reporting session. Thus, it is impossible for the EFC to predict which sensors will be activated and how the sensors will encrypt their measurements in the next reporting session. |
| 2) Brute Force Attack: Assuming that K sensors are activated in a certain reporting session, there are no more than 2K group assignments in our scheme. In this case, the EFC can try a brute force attack that checks all possible group assignments and figures out which one is highly likely. Then the Eve can deduce the target state. However, it can be easily showed that the two probabilities for the i -th sensor to be involved in flipping and nonffipping groups are the same under the condition, and 2K group assignments are equally likely (see Appendix A). This is attributed by the following facts: a) the captured signals at the EFC are delivered through the eavesdropping channel that is independent of the main channel, and b) the activation probabilities are decided to be equal. Therefore, even though the EFC can consider all the possible group assignments for a small K, the Eve is unable to recognize which sensors are in the flipping or non flipping groups. |
SIMULATION RESULTS |
| Using the above equation the packets, no. of nodes and SNR ratio are calculated and result are produced using ns-2 comparison with previous research gives void of good and efficient result |
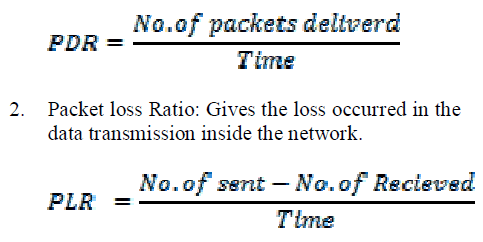
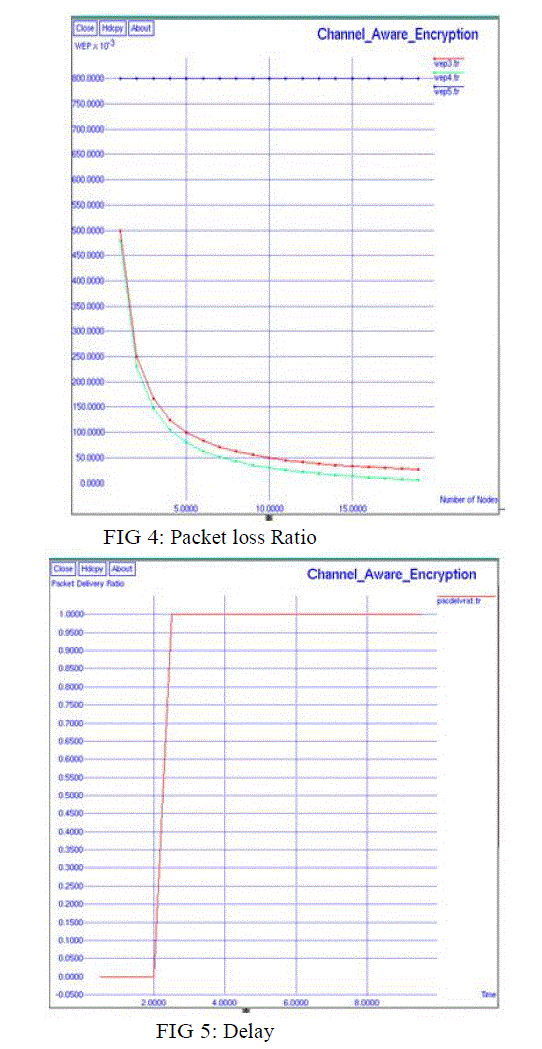
| 1. Packet Delivery Ratio: Gives the ratio of successfully delivered packets |
 |
| 3. Delay: It is the delay occurred during a packet transmission |
| delay = packet sent time - recieved time |
 |
 |
CONCLUSION |
| In this paper, we studied a physical layer security for data confidentiality which is tailored to wireless sensors suffering from limited resources in a distributed detection scenario. In particular, for a WSN where sensors report their binary local decisions over a PAC, we showed that by carefully utilizing a free natural resource, i.e., randomness of wireless channels, it is possible to make the EFC totally ignorant of the target state, i.e., perfect secrecy. |
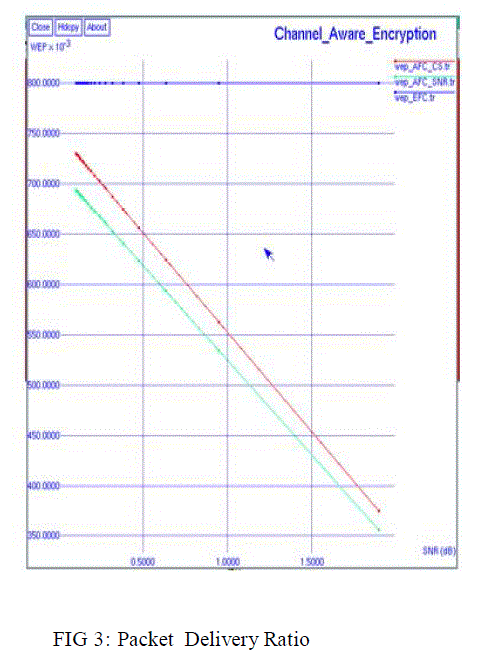
| The claim was thoroughly proved by information-theoretic point of view and also confirmed by performing numerical evaluations. For the performance evaluations, we designed the proposed scheme with an energy efficient modulation technique, NC-BFSK and the fusion rules with channel statistics and the high SNR approximation at the AFC for which performances are evaluated in terms of WEP at various SNR values and sizes of WSN. The evaluation verified that the proposed scheme results in a WEP of 0.5 at the EFC for perfect secrecy. |
| In addition to the confidentiality, the reliability, i.e., WEPs at the AFC of the proposed scheme were evaluated and compared with those of a conventional scheme in which the data confidentiality is implemented by introducing intentional errors in the physical layer. The comparisons showed that the proposed scheme can achieve perfect secrecy while maintaining superior WEP performances across wide ranges of SNR values and sizes of WSN. We believe that this work paves a new dimension to develop an energy efficient security system by utilizing natural resources in WSNs. |
References |
|