ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
K.Anusudha1 and N.Venkateswaren2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
Modern healthcare systems are based on managing diagnostic information of patients in a digital way. To guarantee the security, authenticity and management of medical images and information through storage and distribution, the watermarking techniques are used. This paper aims at developing a watermarking technique in wavelet domain which uses the Electronic Health Record (EHR) as watermark and hospital logo as the reference image. Embedding of the EHR data is based on energy band selection and in reference to the bit location in the reference image. Performance of the proposed method was tested for four modalities of medical images; MRA, MRI, Radiological, and CT. Simulation results show no visible difference between the watermarked and the original image. Moreover, the proposed watermarking method is robust against a wide range of attacks such as JPEG compression, Gaussian noise addition, histogram equalization, contrast adjustment, sharpening and rotation.
Keywords |
| Medical image watermarking (MIW), Electronic Health Record (EHR), Discrete Wavelet Transform (DWT). |
INTRODUCTION |
| Telemedicine combines Medical Information System with information technology that includes use of computers to receive, store and distribute medical information over long distances. Currently, telemedicine applications in teleconsulting, telediagnosis, telesurgery and remote medical education play a vital role in the evolution of the healthcare domain [1]. The transmission, storage and sharing of electronic medical data via the networks have many purposes such as diagnosis, finding new drugs and for scientific research. Exchange of medical image between hospitals located in different geographical locations is a common practice .Hence, healthcare industry demands secure, robust and more information hiding techniques promising strict secured authentication and communication through internet or mobile phones. |
| In general information hiding includes digital watermarking and steganography [3]. A watermarking scheme imperceptibly alters a cover object to embed a message about the cover object (e.g owner’s identifier) [4]. Watermarking is used for copyright protection, broadcast monitoring and transaction tracking and thus robustness of digital watermarking schemes becomes critical.Incontrast, steganography is used for secret communications. A Steganograhic method undetectably alters a cover object to conceal a secret message. Thus, steganographic methods can also hide the very presence of covert communications. |
| In general, digital watermarking algorithms can be divided into two classes depending on the domain of watermark embedding. The first group belongs to the algorithms which uses spatial domain for data hiding [13,14] ,while algorithms of the second group take advantage of transform domain like Discrete cosine Transform (DCT) [7], Discrete Fourier Transform(DFT) [15] and Discrete Wavelet Transform (DWT) [16] for watermarking purpose. Previous works reveals that transform domain schemes are typically more robust to noise, common image processing tasks and compression when compared with spatial transform schemes [17]. Digital watermarking can also be categorized into visible and invisible, fragile and robust, blind and non-blind with emphasis on authentication, rightful ownership, availability of the host image etc. |
| Researchers proposed watermarking techniques and reported findings in the literature survey both integrity and confidentiality requirements (Wang et al.,2000; Zhou et al,2001;Chao et al,2002;Giakoumaki et al,2003;Shieh et al,2004; Piva et al,2005;Xuan et al,2006; |
| Wang et al[6] proposed to embed secret messages in the moderately significant bit of the cover image. A genetic algorithm is developed to find an optimal substitution matrix for the embedding of the secret messages. They also proposed to use a local pixel adjustment process (LPAP) to improve the image quality of the stego image. As the local pixel adjustment process modifies the LSBs, the technique cannot be applied to data hiding schemes based on simple LSB substitution. Zhou et al [7] presented a method that attaches digital signature and EPR into the medical image. Their method uses LSB replacing technique to embed the signature. Chao et al [8] proposed a secure data hiding technique based on the bipolar multiple base conversion to allow a variety of EPR data to be hidden within the same mark image.Giakoumaki et al [9] presented a wavelet based multiple watermarking approach.Their method addresses confidentiality protection and data authentication problems by using three separate watermarks. |
| Shieh et al [10] a genetic algorithm (GA) based watermarking scheme is presented.GA is used to locate the optimal frequency bands for watermark embedding. Piva et al [11] a simple and secure self recovery authentication technique is presented which hides an image digest in subbands of Discrete Wavelet Transform. Xuan et al [12 ] have presented histogram shifting based reversible watermarking techniques .In this work, a part of the histogram of high frequency wavelet co-efficients shifted towards right by one point and then watermark is embedded by using the histogram zero point. |
| Based on good time frequency features and discrimination that match well with the Human Visual System (HVS) motivates the use of DWT in image watermarking among several techniques [18].In medical applications, it is very important to maintain the quality of images because of their diagnostic value. The performance of watermarking schemes can be improved by several methods. Dual watermarking technique is one of the methods to increase the level of security on the watermarked data. |
| In this work a new method for protecting the patient information is introduced in which the information is embedded as a watermark in the discrete wavelet transform (DWT) of the medical image using the hospital logo as a reference image. The scheme is blind so that the EHR can be extracted from the medical image without the need of the original image. Therefore, this proposed technique is useful in telemedicine applications. |
| The paper is organised as follows: Section 2 explains the EHR generation and the proposed algorithm is introduced in section 3. Simulation results for the proposed technique on different types of images are presented in section 4, Performance metrics and analysis is discussed in section 5 and conclusion is given in section 6. |
ELECTRONIC HEALTH RECORD |
| In many areas of health care, particularly in emergency care, health professionals rely on the information provided by the patients about their medical history. However, reliability of the information may be difficult that has acquired from patients who are unwell, confused or having communication difficulties. It is thereby suggested that a personal electronic health record device might empower patients to be aware and have more control of their health status. A number of different versions of patient record systems exist and it referred by a number of varying terms and acronyms, a common one being Electronic Health Record (EHR). |
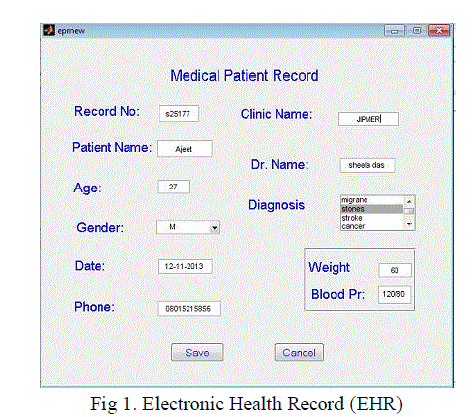 |
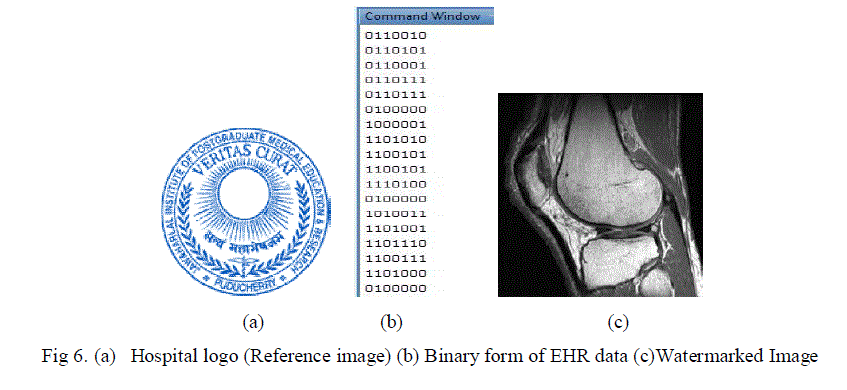
| As shown in Fig.1, the patient’s information can be inserted in the Electronic Health Record (EHR) which includes personal information (name, gender, age,... etc.), clinical information (doctor’s name, diagnosis, blood group.. etc.) and some management information (record number, date.. etc.) |
PROPOSED METHOD |
| The proposed system consists of: embedding mode and extraction mode. |
A. Embedding Phase |
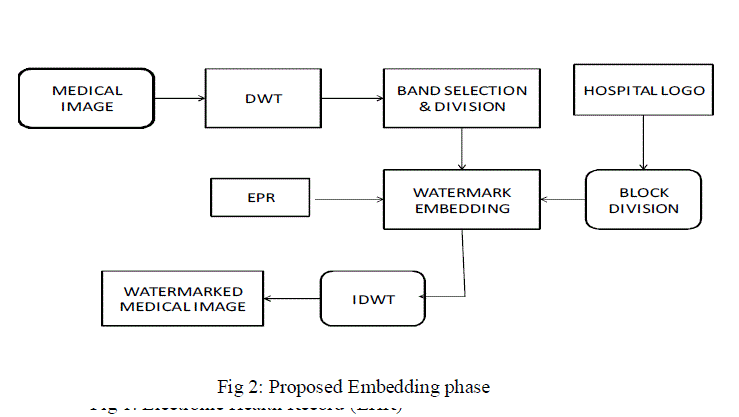
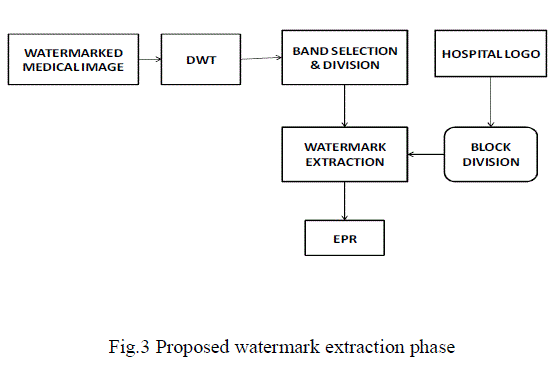
| Band selection in Discrete Wavelet Transform is used for the embedding the Electronic Health record onto the cover medical image with the hospital logo as the reference image. Fig 3 shows the proposed embedding block. The algorithm for the proposed phase is as follows. |
| Step1 |
| For a given NxN host medical image ‘I’, m-level DWT is applied which produces 4m sub-bands of wavelet coefficients. Each sub-band is a matrix of coefficients at a specific resolution with size nxn where n = N/4m/2. |
| Step 2 |
| Compute the energy of each sub-band using the following equation: |
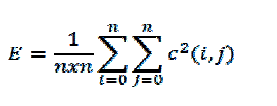 (1) (1) |
| Where E denotes the energy, nxn is the size of sub-band, and 'C' is the DWT coefficient. To ensure trade-off between robustness and imperceptibility out of four bands two sub-bands with middle energy are selected for watermark embedding brk where b is sub-band number 1or2 and k = 1, . . . . . . . , n/4 is the block number. |
 |
| Step 3 |
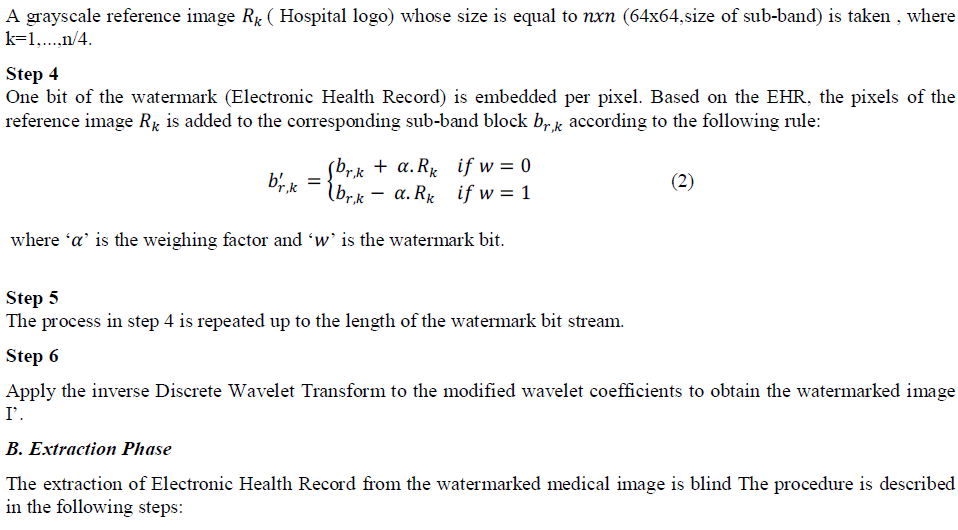 |
 |
 |
SIMULATION RESULTS |
| The performance of the proposed algorithm is tested on 8 grayscale medical images [2] as shown in Fig.4. Four types of medical images CT, MRI, and MRA and radiological of size 256x256 pixels have been considered as sample medical images. |
 |
| Among the samples shown in Fig 5, MRI2 image is shown for the illustration of the proposed work. As per the watermarking procedures, the sample medical image is watermarked with the Electronic health record with hospital logo as reference image.The step by step output of the images are as shown in Fig 5-6. |
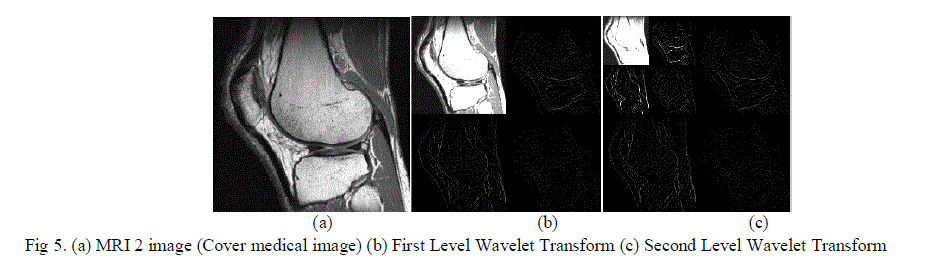 |
| The sub bands with mid energy levels are selected for the watermarking process. |
 |
PERFORMANCE METRICS |
| The performance evolution of the watermarking approach is analysed against various attacks [19]. The Peak-Signal- To-Noise is defined as: |
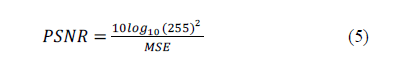 |
| Where ‘MSE’ is the mean squared error between the original and distorted image and is defined as follows: |
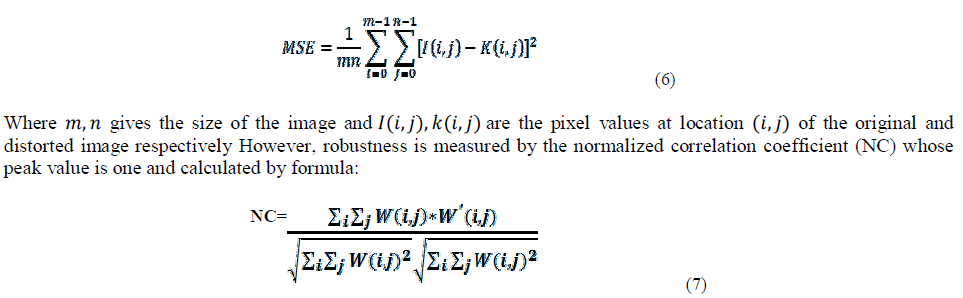 |
| Where w (i, j) is the reference image and W’(i, j) is the watermarked image. Results are shown below. |
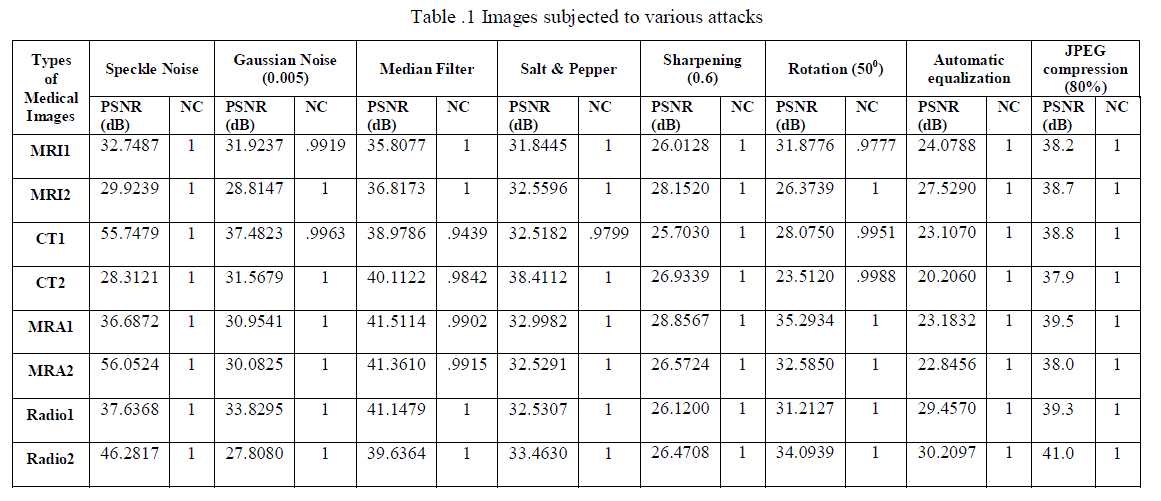
| Table 1 shows the PSNR, Mean NC for all tested images in no attack case and with various attacks. The result shows that the watermark is retrieved successfully. The NC is 1.00 for all images. |
| The four types of medical images are subject to different attacks to measure the robustness of the watermarking algorithm. The MSE, PSNR and NC for the case of attacked images. Analysis of the results shows that our proposed scheme has high degree of robustness to sharpen and automatic equalization attacks. |
| The similarity between recovered and original information is equal to 1 for the four types of images as shown in Table 1For Gaussian noise attack, the patient information is recovered with NC=1when the variance is .001.However, with variance of 0.005 the MRI1 and CT1images are recovered by NC .9919 and .9963. For median filter attack as indicated, the radiological image type resulted in the best robustness NC=1while the other three types have NC less than 1. |
| The results of image attack at different values of the Gamma correction parameter (Par). Satisfactory results are found in the case of contrast attack by factor 10. But, when this factor is increased to 30 the patient information failed to be extracted from the image except for the case of the MRI1 and Radio2 images .The medical image is rotated by 5o. Before extracting the watermark, the image is re-rotated to its original position. The results indicate that the patient information can be extracted with NC=1 except for the MRI1, CT1 and CT2 images where NC=0.9977, 0.9957, and 0.9988 consequently. |
 |
CONCLUSION |
| In this paper, a new dual watermarking scheme has been introduced for security and privacy of patient information. The robustness of the proposed technique is checked by applying some common attacks on the images and examining the visual quality of medical images by the PSNR and NC (normalized correlation coefficient) parameters. Simulation results shows that the proposed scheme is robust against common attacks such as Speckle noise, Gaussian noise, Median filter, salt &pepper noise, Gamma correction, Rotation, Automatic Equalisation and JPEG compression. From the simulation results, it is observed that the proposed technique is more suitable for radiological images as the robustness of this image to various attacks is better than the other input images. |
References |
|