Keywords
|
| Intrusion detection is the act of detecting unwanted traffic on a network or a device. An IDS can be a piece of installed software or a physical appliance that monitors network traffic in order to detect unwanted activity and events such as illegal and malicious traffic, traffic that violates security policy, and traffic that violates acceptable use policies. The intrusion detection has to be performed in decentralized system. Decentralized systems like Mobile Ad hoc Networks (MANET), Vehicular Ad Hoc Networks (VANET) and Wireless Sensor Networks (WSN). |
INTRODUCTION
|
| There are many existing techniques are available in order to provide a secure communication in the mobile ad hoc networks. Some of the existing mechanisms are listed below. |
| NICE (Network Intrusion Detection and Counter Measure Selection In Virtual Network System) |
| Network Intrusion detection and Countermeasure selection in virtual network systems is used to establish a defence-in-depth intrusion detection framework. For better attack detection, NICE incorporates attack graph analytical procedures into the intrusion detection processes. The design of NICE does not intend to improve any of the existing intrusion detection algorithms; indeed, NICE employs a reconfigurable virtual networking approach to detect and counter the attempts to compromise VMs, thus preventing zombie VMs. |
| There are two phases in NICE |
| ? Deploy a lightweight mirroring-based network intrusion detection agent (NICE-A) on each cloud server to capture and analyze cloud traffic. |
| ? Once a VM enters inspection state, Deep Packet Inspection (DPI) is applied, and/or virtual network reconfigurations can be deployed to the inspecting VM to make the potential attack behaviours prominent. Phase 1:NICE A |
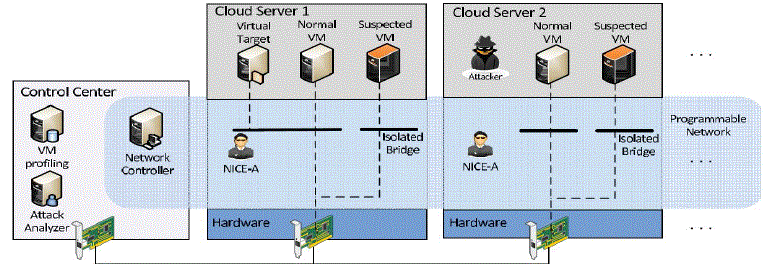
| The NICE-A is a Network-based Intrusion Detection System (NIDS) agent installed in either Dom 0 or Dom U in each cloud server. It scans the traffic going through Linux bridges that control all the traffic among VMs and in/out from the physical cloud servers. In our experiment, Snort is used to implement NICE-A in Dom0. It will sniff a mirroring port on each virtual bridge in the Open Virtual Switch (OVS). Each bridge forms an isolated subnet in the virtual network and connects to all related VMs. |
| Phase 2: Deep Packet Inspection |
| Deep packet inspection (DPI) is normally referred to as a technology that allows packet-inspecting devices, such as firewalls and IPS, to deeply analyze packet contents, including information from all seven layers of the OSI model. This analysis is also broader than common technologies because it combines techniques such as protocol anomaly detection and signature scanning, traditionally available in IDS and anti-virus solutions. |
| The NICE framework is illustrated in Fig. 3.1. It shows the NICE framework within one cloud server cluster. Major components in this framework are distributed and light-weighted NICE-A on each physical cloud server, a network controller, a VM profiling server, and an attack analyzer. The latter three components are located in a centralized control centre connected to software switches on each cloud server (i.e., virtual switches built on one or multiple Linux software bridges). NICE-A |
| The NICE-A is a Network-based Intrusion Detection System (NIDS) agent installed in each cloud server. It scans the traffic going through Linux bridges that control all the traffic among VMs and in/out from the physical cloud servers. |
| VM Profiling |
| Virtual machines in the cloud can be profiled to get precise information about their state, services running, open ports, and so on. One major factor that counts toward a VM profile is its connectivity with other VMs. |
| Attack Analyzer |
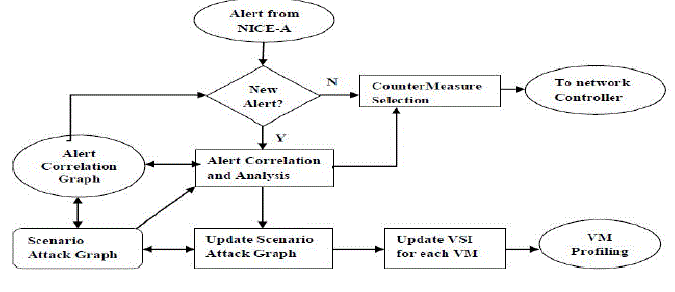
| The major functions of NICE system are performed by attack analyzer, which includes procedures such as attack graph construction and update, alert correlation, and countermeasure selection. The attack analyser shown as Fig 3.2.The process of constructing and utilizing the SAG consists of three phases: Information gathering, attack graph construction, and potential exploit path analysis. With this information, attack paths can be modelled using SAG. Each node in the attack graph represents an exploit by the attacker. Each path from an initial node to a goal node represents a successful attack. |
PROPOSED SYSTEM
|
| Wireless networks face different security threat such that there is either a data loss or data inconsistency. Grouping or clustering in wireless networks refers to the process of forming connected nodes together communication. The nodes within the cluster are connected to a controlling factor which operates communication inside and outside the group. This particular controlling factor is called the group head. |
| The group head is responsible for establishing communication outside the cluster. The head communicates with the head of the other group via intermediate nodes. The group formation is done by P2P technique. P2P is a pointto- point communication by which the group members are formed by the head provided the member is reachable in one hop. That means the head and group member must communicate in single hop; direct link must be available. |
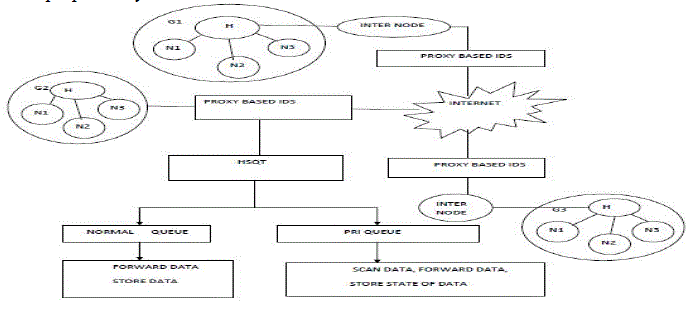
| A HSQT queue is a type of priority queue where a closed circuit covers the entire queue as much time as the data is present in the queue. The advantage of tunnelling is that no attacker can breach the tunnelling effect. In case of a one side attack, the IDS scans and neglects packet (contaminated) and updates the packet information and status for further use. When the same kind of packet reverses for the second time, it simply checks the previous entries and denies the packet. |
| When there is a more than one way attack, i.e., the attackers handling more than one link to the IDS node causing traffic and initiating a DOS attack. In such a case the HSQT queue shreds up and drops the incoming packets and thus the normal queue becomes active. In this case the attackers are handled by other IDS which eliminate the threat for a particular time period within which the HSQT rebuilds to an IDS state. |
| Architecture of the proposed System |
| The IDS node’s architecture is specially designed such that it can act as an intermediate and a NIDS node. Therefore it consists of two types of queue: normal queue and a HSQT queue. A normal queue is set active when the nodes communicate with each other and there is no misbehaviour observed. This resembles the normal data transfer between source and destination where the intermediate node buffers data transfer. |
| The IDS node’s architecture is specially designed such that it can act as an intermediate and a NIDS node. Therefore it consists of two types of queue: normal queue and a HSQT queue. A normal queue is set active when the nodes communicate with each other and there is no misbehaviour observed. This resembles the normal data transfer between source and destination where the intermediate node buffers data transfer. |
| Advantages of Proposed System |
| ? Periodic node information updates: A peer-to-peer communication protocol in which nodes periodically exchange state information about themselves and about other nodes they know about. |
| ? Least of flooding probability: By using proxy based IDS reduce the attacker flooding probability in mobile ad hoc network because it is acting as a intermediate node and monitoring node |
SYSTEM DESIGN
|
| The main module of the proposed system are |
| ? Group Formation using P2P |
| ? Assigning a Group Header |
| ? Implementing a Hybrid Sequenced Queue Tunnelling |
| Group Formation Using P2P |
| The group formation is done by P2P technique. P2P is a point-to-point communication by which the group members are formed by the head provided the member is reachable in one hop. That means the head and group member must communicate in single hop; direct link must be available. 4.2 Assigning a Group Header |
| The Header picks the first node from the queue, sets a timer to interrupt after one quantum, and enables the active communication. If the head is still active at the end of the quantum, the active communication is pre-empted and the node is added to the tail of the queue. If the active communication finishes before the end of the quantum, the current head is released. In either case, the header assigns the nodes to the next active communication in the ready queue. The group header is subjected to change periodically. The group head is chosen by election algorithms. A best example for election algorithm in round ring algorithm. |
| Round Ring algorithm |
| 1. Choose an header for the first time |
| 2. Use a time slice till which the node remains the head |
| 3. When the time slice period of the node exceeds, choose the next neighbouring node as head and enable active links through it. |
| 4. Repeat through step 2 until there is an active head always. |
| Implementing a Hybrid Sequenced Queue Tunnelling |
| An IDS refers to a network framework that monitors all the nodes that are in its coverage region to avoid node misbehaviour and to update information about the misbehaviour to the nearby nodes. In a network, a common node that covers maximum nodes in a region acts as a NIDS architecture. The IDS node’s architecture is specially designed such that it can act as an intermediate and a NIDS node. Therefore it consists of two types of queue: normal queue and a HSQT queue. |
| A normal queue is set active when the nodes communicate with each other and there is no misbehaviour observed. This resembles the normal data transfer between source and destination where the intermediate node buffers data transfer. A HSQT queue is a type of priority queue where a closed circuit covers the entire queue as much time as the data is present in the queue. The advantage of tunnelling is that no attacker can breach the tunnelling effect. In case of a one side attack, the IDS scans and neglects packet (contaminated) and updates the packet information and status for further use. When the same kind of packet reverses for the second time, it simply checks the previous entries and denies the packet. |
CONCLUSION
|
| Wireless networks face different security threat such that there is either a data loss or data inconsistency. Many IDS models have been designed to overcome the security threats. We propose an enhanced scheme by which the IDS can act as both an intermediate node as well as a monitoring node preventing DOS at its initial stage. The HSQT technique used minimizes the DOS attack and prevents an attacker node from transferring malicious packet throughout the network. It alerts the source and continues monitoring the misbehaviour of the node in its coverage region. For maximum coverage we place more than one IDS node such that almost all the nodes in the scenario are covered by one IDS at least. |
Figures at a glance
|
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
|
References
|
- Cloud Sercurity Alliance, “Top Threats to Cloud Computingv1.0,”https://cloudsecurityalliance.org/topthreats/csathreats.v1.0pdf,Mar 2010.
- M. Armbrust, A. Fox, R. Griffith,A.D.Joseph, R. Katz, A.Konwinski, G. Lee, D. Patterson, A. Rabkin, I. Stoica, and M.Zaharia, “A Viewof Cloud Computing,”ACM Comm.,vol. 53,no. 4, pp. 50-58, Apr. 2010.
- B. Joshi, A. Vijayan, and B. Joshi, “Securing Cloud Computing Environment Against DDoS Attacks,” Proc. IEEE Int’l Conf.ComputerComm. and Informatics (ICCCI ’12), Jan. 2012.
- H. Takabi, J.B. Joshi, and G. Ahn, “Security and Privacy Challenges in CloudComputing Environments,” IEEE Securityand Privacy, vol. 8, no. 6, pp. 24-31, Dec. 2010.
- “Open vSwitch Project,” http://openvswitch.org, May 2012.
- Z. Duan, P. Chen, F. Sanchez, Y. Dong, M. Stephenson, and J.Barker, “Detecting Spam Zombies by Monitoring OutgoingMessages,” IEEE Trans. Dependable and Secure Computing,vol. 9,no. 2, pp. 198-210, Apr. 2012
|