Keywords
|
| Delay tolerant network, Vehicular DTN and ONE |
INTRODUCTION
|
| Delay tolerant networks (DTNs) permit for routing in networks where end-to-end paths are unstable or unlikely. Unstable paths can be the result of several challenges at the link layer, for example: high node mobility, low node density, and short radio range; intermittent power from energy management schemes; environmental interference and obstruction. Such environments can exist in undeveloped areas or when a stable infrastructure is destroyed by natural disaster or military efforts. DTNs are useful when the information being routed keeps its value longer than the disrupted connectivity delays delivery [1,17,18]. |
| DTNs can be based on moving nodes such as vehicles or pedestrians. The disadvantage of a vehicle based network is that the nodes move more rapidly, reducing the amount of time they are in transmission range of one another. |
| Accordingly, one limited resource in a vehicle-based DTN is the duration of time that nodes are able to transfer data between them as they pass. Storage can be a limited resource as well. |
| Vehicular networks have got an increasing research interest, due to their wide range of possible application scenarios including, but not limited to, networks to disseminate safety related information (e.g., emergency notification, traffic condition, and collision avoidance) or information advertisements (e.g., marketing data), networks to distribute multimedia content, and monitoring networks to collect data (e.g., pollution data and road pavement defects). Vehicular networks can also be employed to provide connectivity to remote rural communities and regions, enabling non-real time services, such as file-transfer, electronic mail, cached Web access, and telemedicine. Disaster hit areas lacking a conventional communication infrastructure can benefit from the deployment of a vehicular network to provide support for communication between rescue teams and assist communication between the rescue teams and other emergency services. To make such applications possible, it is necessary to design networking protocols that can overcome relevant problems that arise from vehicular environments. The high mobility and speed of vehicles is responsible for a highly dynamic network topology and short contact durations [7]. Limited transmission ranges (due to radio coverage), physical obstacles (e.g., buildings in urban environments), and interferences, make these networks prone to disruption and intermittent connectivity issues [7,9]. As a result, these networks may be partitioned, because of the large distances usually involved and to variable node densities, resulting in discontinuities along the path from source to destination. |
| Conventional routing and forwarding protocols designed for fully connected vehicular networks, called vehicular ad hoc networks (VANETs) [9] aim to establish end-to-end connectivity among network nodes and support end-to-end semantics of existing transports and applications. Thus, they fail data delivery in sparse, intermittent, partially connected, and opportunistic vehicular networks. To surpass these problems, vehicular networks may deliver data using the store-carry-and-forward paradigm of delay-tolerant networks (DTNs). This paradigm does not assume that an end to-end network path is currently available, but rather that such path would exist over time. It maximizes the probability of data delivery, particularly in sparsely populated environments, allowing delay-tolerant data traffic from a variety of vehicular applications to be routed over time [9]. Vehicular delay-tolerant networking (VDTN) is an example of a new architecture that employs a store-carry-and-forward operation principle. Datagrams (IP packets) are assembled in variable length data packets, called bundles, and transmitted asynchronously through the network. |
| Various store-carry-and-forward routing protocols have been presented in the DTN related literature [2-6, 12-14]. The main differences among these protocols come from the type of information they consider to make routing decisions (e.g., absence of knowledge, history of node encounters, location information), and their forwarding or replication strategy (i.e., the number of copies created per bundle). |
PROTOCOL DESIGN
|
| These routing protocols employ the concept of „„spray phaseâÃâ¬ÃŸÃ¢Ãâ¬ÃŸ from binary Spray-and-Wait [3], where a small/fixed number of bundle copies are distributed to distinct nodes in the network. |
| The FirstTwoContact protocol operation describes the sequence of steps executed at a node X when a new contact opportunity is detected with node Y. The protocol depends on type of node type. Hence, Y executes the sequence of steps depending on node type [5]. In the first step, X and Y exchange summery of messages. The second step executed on Y consists of checking if Y is in the hop path for any of the bundles stored in XâÃâ¬ÃŸs buffer. If Y is in the hop path, then it does not accept that bundle. Otherwise X sends a bundle to Y. In forth step, if node X is a mobile node then it deletes that copy of bundle after forwarding it to Y. If X is terminal or relay node, then it forwards it to two other nodes and then it deletes that copy of bundle. |
| The FirstTwoMobileContact protocol operation describes the sequence of steps executed at a node X when a new contact opportunity is detected with node Y. The protocol depends on movement model of node. Hence, Y executes the sequence of steps depending on node type. In the first step, X and Y exchange summery of messages. The second step executed on Y consists in checking if Y is in the hop path for any of the bundles stored in XâÃâ¬ÃŸs buffer. If Y is in the hop path, then it does not accept that bundle. Otherwise X sends a bundle to Y. In forth step, if node X is terminal or relay node then it deletes that copy of bundle after forwarding it to Y. If X is mobile node, then it forwards it to two other nodes and then it deletes that copy of bundle. |
PERFORMANCE EVALUATION
|
| This section analyses the performance assessment of the proposed routing protocols in comparison with routing schemes: Spray-and-Wait and FirstContact. The simulation experiments use the Opportunistic Network Environment (ONE) simulator [11]. |
SIMULATION SETUP
|
| The simulation scenario is based on the map-based model of a part of the city of Pune (India) presented in Figure 1. It assumes a fully cooperative opportunistic environment without knowledge of the traffic matrix and contact opportunities. We have considered map-based movement model to deploy mobile nodes, stationery movement model to deploy terminal nodes, static movement model to deploy relay nodes at the intersections of the roads [15, 16]. |
| Two Terminal nodes are placed in the map which are stationary – one as a source and other one as a destination. During the 12 hrs of simulation, 45 mobile nodes (e.g., Cars) move on the map roads with an average speed of 50 km/h, at random locations, and with random pause times between 10 and 30 min. Each mobile node has a 25 megabytes buffer. To increase the number of contact opportunities, two, five and ten stationary relay nodes were placed at the road intersections shown in Figure 1. Each stationary relay node has a 75 megabytes buffer and terminal nodes have 50 megabytes buffer. |
 |
| Data bundles are originated at source terminal node and are destined to destination terminal nodes. To generate data bundles with different sizes a event generator is considered which generates bundles with sizes in the ranges of (500 KB, 1 MB). This event generator assumes [25, 35] seconds of bundle creation interval. Data bundles time-to-live (TTL) is set to 300 minutes. |
| Spray-and-Wait and FirstContact are considered as underlying routing schemes and their performance is evaluated for the same simulation scenario. Number of copies parameter of normal spray-and-wait as well as in binary spray- and- wait is taken as 6 which is 27% of number of mobile nodes in given scenario. |
PERFORMANCE ANALYSIS
|
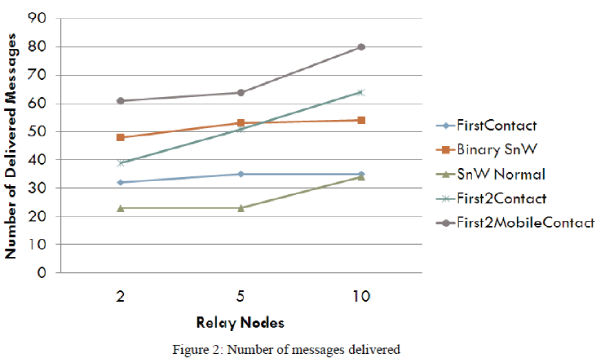
| The performance analysis starts considering random queue. Figure 2 show that all routing protocols increase message delivery ratio when relay nodes are deployed. When analyzing the simulation results with the introduction of five and ten relay nodes, it is observed that FirstTwoMobileContact and FirstTwoContact protocols increase their delivered messages as compared to Spray-and-Wait routing algorithm. |
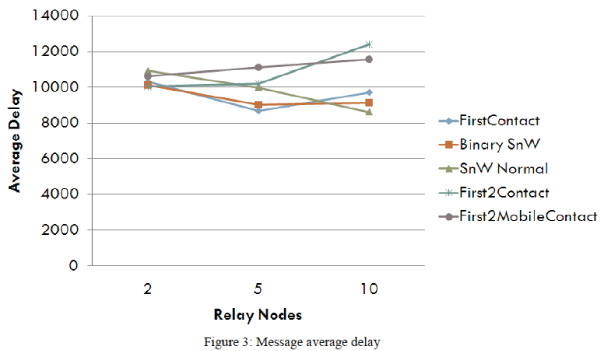
| The message average delay is an interesting metric, since minimizing it reduces the time that messages spend in the network and reduces the contention for resources in the network (e.g. buffer). Figure 3 shows that all routing protocols register similar values for the message average delay, and that relay nodes do not significantly affect this metric for FirstTwoMobileContact. |
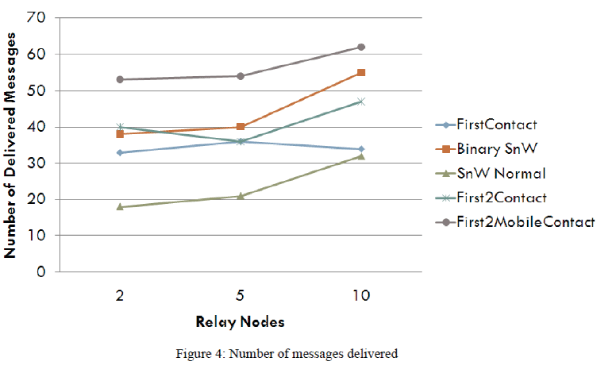
| Figure 4 shows that all routing protocols increase message delivery ratio when relay nodes are deployed. When analyzing the simulation results with the introduction of five and ten relay nodes, it is observed that FirstTwoMobileContact and FirstTwoContact protocols increase their delivered messages as compared to Spray-andwait routing algorithm. |
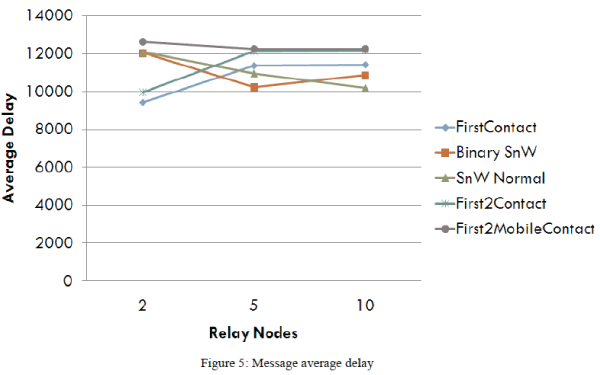
| Figure 5 shows that all routing protocols register similar values for the message average delay, and that relay nodes do not significantly affect this metric. |
 |
 |
 |
 |
CONCLUSION
|
| Delay tolerant networking (DTN) is a timely topic that addresses communication in challenged network environments. Here, a survey of the most promising protocols was presented. These protocols are classified in to two broad categories: Flooding and Forwarding. |
| It also includes DTN-based networks like vehicular delay-tolerant networks (VDTNs) rely on sporadically connected nodes. Here, a static movement model to deploy relay nodes in VDTN is proposed and two routing algorithms to maximize delivery ratio in VDTN are proposed as well. |
| From result analysis, FirstTwoMobileContact and FirstTwoContact routing algorithms increase delivery ratio by almost 16% and 48% as compared to Binary Spray-and-wait routing algorithm considering random queue in given scenario respectively. It is also shown that FirstTwoMobileContact routing algorithms increase delivery ratio by almost 12% compared to Binary Spray-and-wait routing algorithm considering fifo queue in given scenario. |
References
|
- K. Fall, "A Delay -Tolerant Network Architecture for challenged internets," in Proceeding of annual conference of the special Internet Group on Data Communication (ACM SIGGOMM '03), pp.27-34, 2003.
- T. Spyropoulos, K. Psounis and C. S. Raghvendra, "Spray and Focus Efficient Mobility -Assisted Tolerant Networks," in Proceeding of workshop on PerComapos, pp. 79-85., 2007.
- T. Spyropoulos, K. Psounis, and C. Raghavendra, “Spray-and-wait: an efficient routing scheme for intermittently connected mobile networks,” in Proceedings of the 2005 ACM SIGCOMM workshop on Delay-tolerant networking (WDTN), (New York, NY, USA), pp. 252–259, 2005.
- Vahdat and D. Becker, “Epidemic routing for partially-connected ad hoc networks.” Dept. of Computer Science, Duke University, Technical Report, CS-2000-06, Apr. 2000.
- J. D'souza, Johny Jose, "Routing approaches in Delay Tolerant Networks: A Survey," in Proceeding of International Journal of Computer Applications, Vol. 17, pp. 9-15, 2010.
- ChoonghoLee ,Dukhyun Chang , “Regional token based routing for DTNs “, in Proceeding of International Journal of Information Networking, 2009.ICOIN 2009.
- Paulo Rogerio Pereira, Augusto Casaca, Joel J. P. C. Rodrigues, “ From Delay-Tolerant Network to Vehicular Delay-Tolerant Network”, in IEEE Communication Survey and Tutorials, 1553-877X/11, 2011
- Hao Wu, R. Fujimoto and G. Riley. “Analytical Models for Information Propagation in Vehicle-to-Vehicle Networks”. Vehicular Technology Conference,2004. VTC2004-Fall. 2004.
- Farahmand, F., Patel, A.N., Jue, J.P., Soares, V.G. and Rodrigues, J.J.P.C. „Vehicular wireless burst switching network: enhancing rural connectivity?, Paper presented at The 3rd IEEE Workshop on Automotive Networking and Applications (Autonet 2008), Co-located with IEEE GLOBECOM 2008, New Orleans, LA, USA, 4 December.
- F.Warthman, “Delay-Tolerant Networks (DTNs), A Tutorial ,” in , March, 2003.
- http://www.netlab.tkk.fi/tutkimus/dtn/theone/
- Harras, K., Almeroth, K., Belding-Royer, E., “Delay Tolerant Mobile Networks (DTMNs): Controlled Flooding Schemes in Sparse Mobile Networks”, IFIP Networking, Waterloo, Canada, May 2005.
- LeBrun, J., Chuah, C.-N., Ghosal, D., “Knowledge-Based Opportunistic Forwarding in Vehicular Wire-less Ad Hoc Networks”, IEEE VTC Spring, 2005.
- Zhao, N., Ammar, M., Zegura, E., “A Message Ferrying Approach for Data Delivery in Sparse Mobile Ad Hoc Networks”, In ACM MobiHoc, 2004.
- T. Camp, J. Boleng, and V. Davies, “A survey of mobility models for ad hoc network research,” in Wireless Communication and Mobile Computing (WCMC): Special issue on Mobile Ad Hoc Networking: Research, Trends and Applications, vol. 2, no. 5, pp. 483–502 , 2002
- J. Harri, F. Filali, and C. Bonnet, “Mobility Models for Vehicular Ad Hoc Networks: A Survey and Taxonomy,” in Eurecom Sophia- Antipolis, RR-06- 168 , March 2007
- S. Jain, K. Fall, and R. Patra, “Routing in a Delay Tolerant Network,” in ACM SIGCOM?04, Portland, Oregon, USA , August, 2004
- L. Pelusi, A. Passarella, and M. Conti, “Opportunistic Networking: Data Forwarding in disconnected Mobile Ad Hoc Networks,” in IEEE Comm. Magazine, Vol. 44, No. 11, , Nov. 2006.
|