Keywords
|
| Cloud Computing, SaaS, Web service, framework. |
INTRODUCTION
|
| Cloud computing and storage are terms that are now in popular use in today’s business environment. While almost all large organizations have switched to online storage and computing, there are many small and medium sized users who are still hesitant to do so. Lack of information is a common possible cause for this.Cloud Computing makes computer infrastructure and services available "on-need" basis. The computing infrastructure could include hard disk, development platform, database, computing power or complete software applications. To access these resources from the cloud vendors, organizations do not need to make any large scale capital expenditures. Organization need to use "pay peruse", the billing model of cloud computing, which is similar to the electricity payment that we do on the basis of usage. |
| Cloud computing largely depends upon virtualization technology. Virtualization refers to the technique in which all the capabilities of a piece of hardware are faithfully reproduced in a software program. Depending upon what is being virtualized, there are the three types of Cloud Computing incarnations - IaaS (Infrastructure as a Service), PaaS (Platform as a Service) and SaaS (Software as a Service). |
| For most business organizations, implementation and maintenance of business processes has been a frustrating experience in the presence of ever changing business requirements. A significant amount of productive time is spent in managing and upgrading infrastructure and migration of services from one technology to another and integration of new services with the existing environment. Increasingly, IT teams are turning to cloud computing technology to minimize the time spent on lower-value activities and allow IT to focus on strategic activities with greater impact on the business. Initially security was a major hurdle that prevented migration to public cloud but now most cloud storage providers employ high end encryption techniques to safeguard data thus increasing the confidence of cloud users. The data centers are monitored round-the-clock to take care of security vulnerabilities, ensuring that user data is secured at all times. |
| This paper covers the concepts, terminologies and issues related to cloud computing, followed by a Case study related to Cloud technology. The paper is organized as follows: Next section gives a brief overview to Cloud technology. Section 3 describes its types, section 4 talks about advantages and issues related to Cloud technology over traditional methods. A Case study of a cloud-based application, developed for student project management and evaluation, that uses Google’s AppEngine as PaaS and services provided by Google such as Google data service, Blobstore, and OAUTH authorization , is discussed in Section 5. The possible extensions are discussed in conclusion. |
TYPES OF SERVICES PROVIDED THROUGH CLOUD
|
| Infrastructure as a Service (IaaS): |
| These are various services where the hardware is being virtualized. Virtual machines (i.e. CPU + Memory), virtual disks (e.g. Amazon EBS), virtual file-systems (e.g. Amazon S3), virtual databases (e.g. Google BigTable, Amazon SimpleDB, SQL Azure) are all examples of infrastructure as a Service. Basically, these services can provide the user the same benefits that he would have had by having an hardware infrastructure spread over several server rooms and labs without the responsibility of monitoring and maintaining the same. The users consume processing, storage, networks and other computing resources with the ability to rapidly and elastically scale and control resources to deploy and run software and services. |
| Platform as a Service (PaaS): |
| These are various services where the software development platform (i.e. programming language, runtime environment, etc.) is being virtualized. Google AppEngine (Java/Python), Microsoft Azure (.NET/Visual Studio) are examples of PaaS. A complete development environment, with state of the art tools, is at your service so that new services can be quickly developed, deployed and managed. |
| Software as a Service (SaaS): |
| These are various services that have virtually removed the need of hardware and software engineers altogether and the end-users can get the software solution satisfying their requirements at their door-step. In SaaS without putting in much efforts user gets a ready-made software that he can directly start using. Like SalesForce – software used by sales agents. Here users consume applications such as CRM, ERP and social collaboration tools from multiple client devices through a web browser. |
| 2.4 Business Process as a Service (BPaaS): |
| Here users consume business outcomes (for example, payroll processing, HR) by accessing business services via webcentric interfaces. |
| Today, there are three primary delivery models of cloud: |
| Private cloud: where the assets and the consumers are located within a single enterprise. |
| Public cloud: where the assets are located outside of the enterprise. |
| Hybrid cloud: combines above two models. |
ADVANTAGES OF CLOUD COMPUTING
|
| There are a number of advantages of Cloud Computing over the old way of doing things: |
| Convenience: Cloud Computing is easy. Not having to deal with real machines, and disk failures, and electricity failures etc, is a huge benefit. |
| Cost: There are two different cost advantages to cloud computing. Sometimes it is cheaper than the physical alternative. At other times, the advantage comes from the fact that you have to pay small installments every month instead of a large chunk of money when you’re buying the infrastructure. |
| Cheaper: Usually cloud computing turns out to be cheaper. This is mainly because cloud computing providers are able to share their infrastructure across a large number of customers, giving them economies of scale, and higher utilization. |
| Pay-as-you-go: We need to pay as per our consumptions like our ordinary electricity bills. And at times when we’re not really using the server, we can shut it off, and don’t pay for it. If during a busy month, we need two servers, we can get a second server for just one month, and then delete it at the end of the month. Much better than having to buy an entire second server that will be useless after the first month. |
| Easy scalability: If we’re a growing company, and the demand for computing suddenly increases (for example, you suddenly get 10,000 new customers), IaaS providers provide many scalability options at the click of a button. PaaS and SaaS providers take care of scaling completely, in a manner transparent, and don’t even need to think about it. |
| Location Independence: A cloud computing service can be used from anywhere irrespective of the actual physical location or infrastructure. |
ISSUES RELATED TO CLOUD TECHNOLOGY
|
| Privacy: |
| The cloud model has been criticized by privacy advocates for the greater ease in which the companies hosting the cloud services control (CSP), thus, can monitor at will, lawfully or unlawfully. The point is that because of CSP operations, customer or tenant data may not remain on the same system, or in the same data center or even within the same provider's cloud. This can lead to legal concerns over jurisdiction. Cloud computing poses privacy concerns because the service provider at any point in time, may access the data that is on the cloud. They could accidentally or deliberately alter or even delete some information [2]. |
| Open standards: |
| Most cloud providers expose APIs that are typically well- documented but also unique to their implementation and thus not interoperable. Some vendors have adopted others' APIs and there are a number of open standards under development, with a view to delivering interoperability and portability [3]. |
| Security: |
| As cloud computing is achieving increased popularity, concerns are being voiced about the security issues introduced through adoption of this new model. Physical control of the Private Cloud equipment is more secure than having the equipment off site and under someone else’s control. Physical control and the ability to visually inspect the data links and access ports is required in order to ensure data links are not compromised. Dealing with all sorts of security issues is a major challenge before Cloud technology. |
| Abuse: |
| As with privately purchased hardware, crackers posing as legitimate customers can purchase the services of cloud computing for nefarious purposes. This includes password cracking and launching attacks using the purchased services [4]. In 2009, a banking Trojan illegally used the popular Amazon service as a command and control channel that issued software updates and malicious instructions to PCs that were infected by the malware [5]. |
CASE STUDY
|
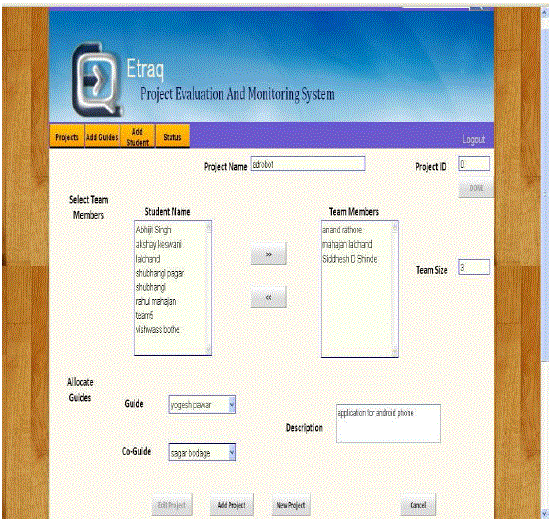
| We developed a cloud based web application called “ETRAQ” (Evaluation Transparency, Remote, Accurate and Quick). It is an application for project evaluation and development monitoring. It was a solution for a problem faced in most of colleges, which is to monitor and evaluate projects undergoing every year by the students. It is used to guide their work, assign a new task, evaluate it and monitor their pace. With a poor teacher student ratio, it is difficult to provide attention that is so very important for continuous assessment of student projects. |
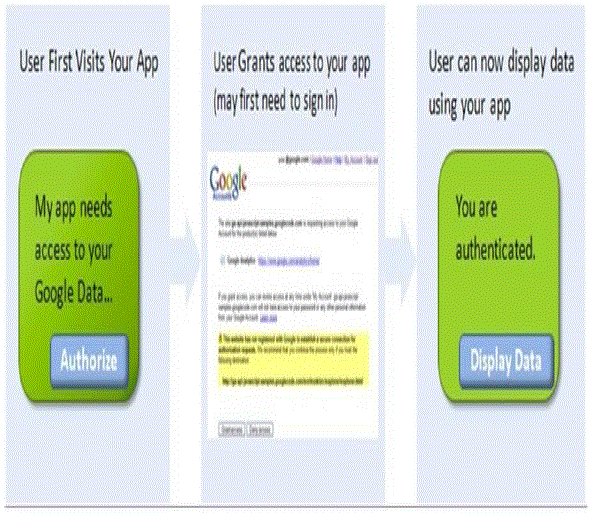
| ETRAQ performs above things easily and efficiently. We used Cloud as a Platform, provided by Google’s AppEngine [6]. Google App Engine lets you run your web applications on Google's infrastructure, they are easy to build, easy to maintain, and easy to scale as your traffic and data storage needs grow. With App Engine, there are no servers to maintain. You can just upload your application, and it's ready to serve your users. The application makes use of Google’s OAUTH authorization (Fig-1). With OAUTH authentication, first-time users of our application must authorize access to their Google data, the users see some text and a link or button directing them to authenticate (sign in) using their Google Account credentials , the user`s credentials are not saved in the application space thus giving security an upper hand. |
| The data related to the application is stored on Google DataStore. The datastore writes data in objects known as entities, and each entity has a key that identifies the entity. Entities can belong to the same entity group, which allows you to perform a single transaction with multiple entities. Entity groups have a parent key that identifies the entire entity group. The default datastore for an application is the High Replication datastore. This datastore uses the Paxos algorithm to replicate data across datacenters. The High Replication datastore is extremely resilient in the face of catastrophic failure. |
| The application is designed using Google Web Toolkit. Google Web Toolkit is a Web Application Framework dealing with Servers and Clients. When a Server is required to do some processing in a web-app, services must be used. A service is used to invoke server-side code from the client. |
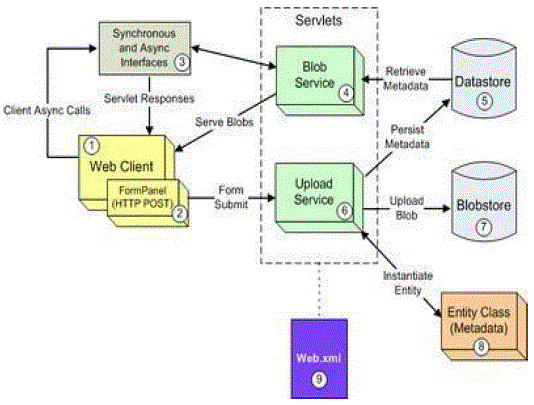
| The application provides direct facility for the students to submit the artifacts or files to their guide by just uploading the files. Guide gets the list of the artifacts submitted and can view/download it .This Facility is provided by Google Blobstore service (Fig-2). The Blobstore API allows our app to serve data objects, called blobs that are much larger than the size allowed for objects in the Datastore service. Blobs are created by uploading a file through an HTTP request. Blobstore creates a blob from the file's contents and returns an opaque reference to the blob, called a blob key, which you can later use to serve the blob. |
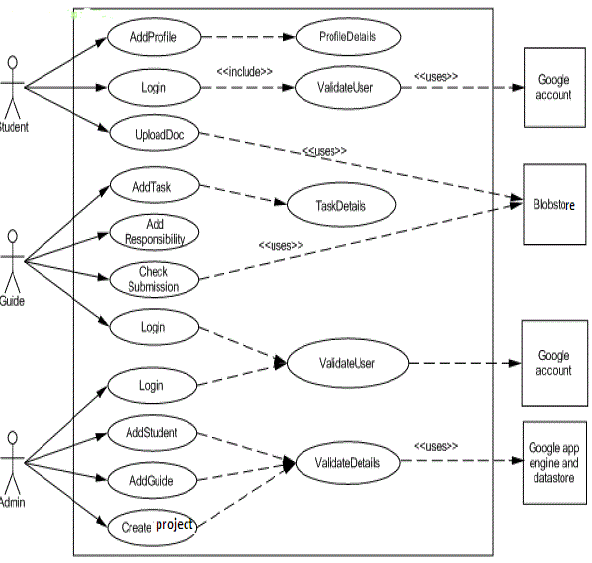
| Student. Admin is responsible to create a project group and assign guides to it. Guide logins and gets information and other details of the group. He can assign new task to the group, check the artifacts or files submitted by respective groups. Students need to login to view the assigned task by the guides and submit the documents using simple form provided. This process reduces the efforts of the guides to evaluate the work also, the data is available anywhere and anytime, increases synchronization between group members. |
| The application brings all the active members under one roof providing an easy to use interface for required interactions.. |
CONCLUSION
|
| With some additions and modifications ETRAQ can be used for monitoring and controlling of Industrial projects. In educational institutes it can be used for other things like evaluating projects during project competitions or during external evaluations. Further ETRAQ can be made Multi- tenant which will enable sharing of the application and resources among large pool of users. |
| The implementation process brought out clearly the effectiveness of cloud platform and the lessons learned can be used in developing a framework for implementing services on the cloud for education sector. |
| For countless enterprises and their IT organizations, adopting a cloud model is one path to cost efficiency and a more effective IT-enabled business. Cloud provides a large set of commonly required set of services and large tool set that can be effectively used in quickly converting a business process requirement into a service on the cloud. |
| Enterprises of varying size and complexity will benefit from a cloud solution. |
Figures at a glance
|
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
|
References
|
- “The NIST Definition of Cloud Computing". National Institute of Science and Technology.
- "Cloud Computing Privacy Concerns on Our Doorstep" (http://cacm.acm.org/magazines/2011/1/103200-cloud- computing-privacy-concerns-onour-doorstep/fulltext).
- Eucalyptus Completes Amazon Web Services Specs with Latest Release"(http://ostatic.com/blog/eucalyptus- completes-amazon-webservices-specs-with-latest-release).
- "Amazon.com Server Said to Have Been Used in Sony Attack" Bloomberg. (Retrieved 2011-08-20).
- PlayStation Network hack launched from Amazon EC2 - The Register
- Google AppEngine’s - http://developers.google.com/appengine
- “Get more out of cloud with a structured workload analysis” - IBM October 2011
|