ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
G.M.Keerthi1 and M.Gopinath2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
Network Security is the most vital component in information security because it is responsible for securing the information among the networked computers. This paper analyzes the symmetric key and public key cryptographic techniques. The paper combines the characteristics of the AES and ECC for encryption standard. Implementation of encryption of the information is done in such a way that it will be impossible for the attackers to read the resources. In this method, conversion of text is done using AES algorithm and key will be encrypted using ECC algorithm. Result will be cipher which is decrypted on the receiver‘s side. This combined encryption methods enhance the speed and security.
Keywords |
| Cryptography, Advanced Encryption Standard, Elliptic Curve Cryptography, Encryption, Decryption. |
INTRODUCTION |
| Security processing is computation intensive, which normally includes lookup and fetching/updating of parameters (keys, encryption/authentication algorithms, initial values, and security-related protocol information), encryption and authentication, data transfer, bus contention resolution, etc. Powerful security processing architectures are thus important in high-speed network applications. Encryption algorithm is an important role for information security. Encryption is the process of transforming plaintext data into cipher text in order to secure its meaning and so preventing any unauthorized user from retrieving the original data. The Encryption has long been used by militaries and governments to facilitate secret communication. For technical reasons, an encryption scheme usually uses a pseudorandom encryption key generated by an algorithm. It is in principle possible to decrypt the message without possessing the key, but, for a well-designed encryption scheme, large computational resources and skill are required. |
| The Advanced Encryption Standard (AES) is the one among the symmetric key cryptographic algorithm which has been introduced to overcome the limitations of other algorithms like DES (Data Encryption Standard). The security of AES will be high due to the presence of large number of rounds or blocks and steps. The output of one block acts as the input of the next block in both encryption and decryption. For the wireless networks, this significantly is advantageous to the power needs. The elliptic curve cryptography is a type of symmetric key encryption method that is used for key exchange, digital signatures and also for encrypting the secure data. When compared to the other asymmetric key algorithms the system resource utilization like band width, memory, hard disk of this ECC is very much less. Therefore ECC is treated as the best suitable cryptographic algorithms for the wireless devices. |
RELATED WORK |
| Wireless networks play critical roles in present work, home, and public places, so the needs of protecting of such networks are increased. Encryption algorithms play vital roles in information systems security. These symmetric algorithms consume a significant amount of computing resources such as CPU time, memory, and battery power. CPU and memory usability are increasing with a suitable rates, but battery technology is increasing at slower rate. This analyse the several encryption algorithms with the merits [2]. |
| Advanced Encryption Standard (AES) and Elliptic Curve Cryptosystems (ECC) is the best two algorithms of symmetric encryption technology and asymmetric encryption technology. This analyzes the AES algorithm and S-box structure, then the replace plan based on S-box structure is proposed to improve AES encryption algorithm, secondly the ECC algorithm is been explained [1]. RSA (Rivest, Shamir and Adleman) is being used as a public key exchange and key agreement tool for many years. Due to large numbers involved in RSA, there is need for more efficient methods in implementation for public key cryptosystems. Elliptic Curve Cryptography (ECC) is based on elliptic curves defined over a finite field [7]. Wireless sensor networks (WSN) are constrained in terms of computational and energy resources. There is enormous research going on for converting the stream based cipher to public key based cipher to increase the level of security in the information transfer in WSN. A recent research validates public key cryptography such as Elliptic Curve Cryptography (ECC) is feasible for wireless sensor network. Also symmetric key algorithms are efficiently implemented and used in wireless sensor network[4]. |
| Protecting the information transmitted over the network is a difficult task and the data security issues become increasingly important. At present, various types of cryptographic algorithms provide high security to information on networks, but there are also has some drawbacks. To improve the strength of these algorithms, we propose a new hybrid cryptographic algorithm in this paper. The algorithm is designed using combination of two symmetric cryptographic techniques [3]. Exchange of private information over a public medium must incorporate a method for data protection against unauthorized access. To enhance the data security against the DPA attack in network communication, a dual field ECC processor supporting all finite field operations is proposed. The ECC processor performs hardware designs in terms of functionality, scalability, performance and power consumption. A unified scheme is introduced to accelerate EC arithmetic functions. The hardware is optimized by a very compact Galois field arithmetic unit with fully pipelined technique [8]. |
AES AND ECC |
| Cryptography is the study of techniques for secure communication in the presence of third parties. More generally, it is about constructing and analyzing protocols that overcome the influence of adversaries and that are related to various aspects in information security such as data confidentiality, data integrity, authentication, and non-repudiation. Cryptography prior to the modern age was effectively synonymous with encryption. AES is one among the encryption cryptographic algorithm. Companies usually encrypt their data before transmission to ensure that the data is secure during transmission. The encrypted data is sent over the network and is decrypted by the intended recipient. The encryption algorithms are usually summarized into two popular types: Symmetric key encryption and Asymmetric key encryption. |
| In Symmetric key encryption, only one key is used to encrypt and decrypt data. The keys may be identical or there may be a simple transformation to go between the two keys. The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link. The key should be distributed before transmission between users. Therefore, key plays an important role in security purposes. Strength of Symmetric key encryption depends on the size of key used. Stream ciphers encrypt the digits (typically bytes) of a message one at a time.Block ciphers take a number of bits and encrypt them as a single unit, padding the plaintext so that it is a multiple of the block size. Blocks of 64 bits have been commonly used. The Advanced Encryption Standard (AES) algorithm approved by NIST uses 128-bit blocks. In the symmetric encryption algorithm we make use of Advanced Encryption Standard (AES). This algorithm supersedes the Data Encryption Standard (DES). AES is based on a design principle known as a substitution-permutation network, combination of both substitution and permutation, and is fast in both software and hardware. AES operates on a 4×4 column-major order matrix of bytes, termed the state, although some versions of Rijndael have a larger block size and have additional columns in the state. Most AES calculations are done in a special finite field. |
| Asymmetric key encryption is used to solve the problem of key distribution. In Asymmetric key encryption, private key and public key are used. Public key is used for encryption and private key is used for decryption (E.g. RSA, Digital Signatures and ECC). The term "asymmetric" stems from the use of different keys to perform these opposite functions, each the inverse of the other – as contrasted with conventional cryptography which relies on the same key to perform both. In public key cryptography [4], each user or the device involved in the transmisson have a pair of keys for the communication, a public key and a private key and a set of operations associated with the keys to do the operations. Only the intended user/device knows the private key whereas the public key is distributed to all users/devices taking part in the communication. Since the knowledge of public key does not compromise the security of the Algorithms, it can be easily exchanged online. Public-key cryptography finds application in, amongst others, the IT security discipline information security. Information security (IS) is concerned with all aspects of protecting electronic information assets against security threats. Public-key cryptography is used as a method of assuring the confidentiality, authenticity and non-reputability of electronic communications and data storage. |
SYSTEM ARCHITECTURE |
A.SENDER SIDE: |
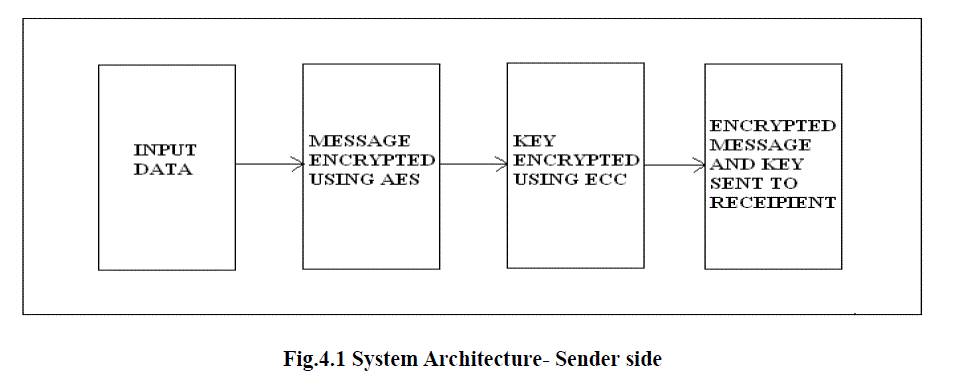 |
| In this paper, we analyse both the symmetric and asymmetric encryption algorithm. Combining both the algorithm results in the overcome of demerits of one over the other algorithm. Symmetric algorithm being the fast in computation leading to the higher speed in the data/information transmission. This algorithm has issues in the security since there is same key used for both the encryption and decryption. The key exchange should be done in the most secured way for the secured communication. The key exchange is the most important thing to be done in the symmetric algorithm. When there occurs error or defects in the key exchange, then it may lead to the spill of information. In the case of asymmetric algorithm, security is one of the most beneficial parameter which is needed for the network security. |
B.RECEIVER SIDE: |
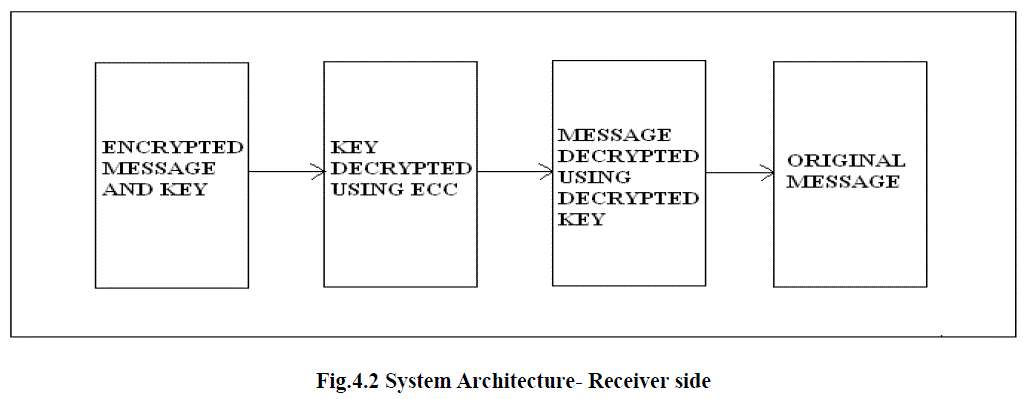 |
| This asymmetric algorithm has two different keys for the encryption and decryption to be done. When there is separate keys then the operation can be done in the most secured way. Public key and private key forms the two different keys for the asymmetric algorithm. This algorithm leads to the time consumption since it needs the separate encryption and decryption to be done in the asymmetric form of algorithm. In order to enhance the security which is predominant role in the network security, we combine the characteristic of both the algorithm. The key used to encrypt the information in the AES is been encrypted using the ECC. The encryption of ECC can be done by means of the public key which is common among the users. This wont be kept secret as the private key. Using the same key the information is being encrypted using the symmetric algorithm AES. As the result of encryption, the text is in the form of Cipher text (unreadable form). The encrypted key which is the public key of the asymmetric algorithm. This key is further decrypted using the private key of asymmetric decryption. Private key is kept in the most secured way to prevent the looting of the information. Private key will be given to the intended user in order to decrypt the message. Then this decrypted key will be given as key to perform the symmetric decryption. |
ALGORITHM |
C. ADVANCED ENCRYPTION STANDARD (AES) |
| The AES algorithm is done by the series of steps, |
| 1.Subbytes |
| 2.Shiftrows |
| 3.Mixcolumns |
| 4.Addround keys |
The SubBytes step: |
 |
 |
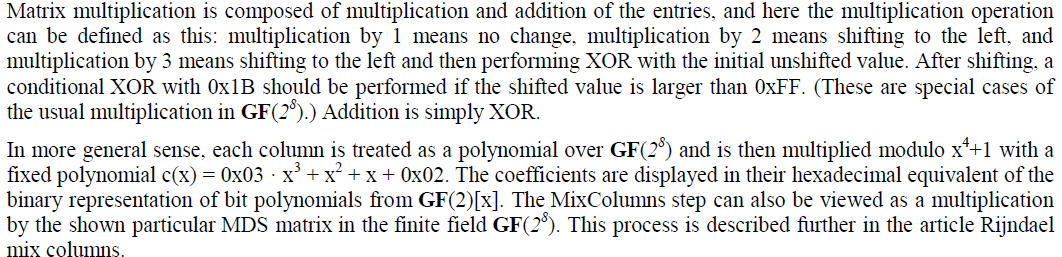 |
The AddRoundKey step: |
| In the AddRoundKey step, each byte of the state is combined with a byte of the round subkey using the XORoperation (⊕). |
| In the AddRoundKey step, the subkey is combined with the state. For each round, a subkey is derived from the main keyusing Rijndael's key schedule; each subkey is the same size as the state. The subkey is added by combining each byte of the state with the corresponding byte of the subkey using bitwise XOR. |
Optimization of the cipher |
| On systems with 32-bit or larger words, it is possible to speed up execution of this cipher by combining the SubBytes andShiftRows steps with the MixColumns step by transforming them into a sequence of table lookups. This requires four 256-entry 32-bit tables, and utilizes a total of four kilobytes (4096 bytes) of memory — one kilobyte for each table. A round can then be done with 16 table lookups and 12 32-bit exclusive-or operations, followed by four 32-bit exclusive-or operations in the AddRoundKey step. |
| If the resulting four-kilobyte table size is too large for a given target platform, the table lookup operation can be performed with a single 256-entry 32-bit (i.e. 1 kilobyte) table by the use of circular rotates. |
| Using a byte-oriented approach, it is possible to combine the SubBytes, ShiftRows, and MixColumns steps into a single round operation. |
ECC ALGORITHM |
| The ECC uses curves whose variables coefficients are finite numbers, there are two families commonly used on the cryptography, the first uses elliptic curves over prime finite field, which is also referred as the odd characteristic or modulo p. It is the field of integers modulo an odd prime number p, where p is large prime number. This one is best suited for software implementations of ECC. The second uses elliptic curves over binary field. This is also referred as the even characteristic or finite field with elements, where m is large integer number. This one is more suitable for hardware implementation of ECC [14]. ()pEF pF 2()mEF2mF2m |
| The mathematical operations of ECC are defined over elliptic curve. For the first type, the elliptic curve is the set of points that satisfies the following equation: , where, such that x, y, a, b. ()pEF (,)xy23ymod(xaxb) mod pp=++324a27b0 +≠p∈F |
| For the second type, elliptic curve is the set of points that satisfies the following equation: 2()mEF (,)xy . 2322, 0, where a,b,x,ymyxyxaxbb+=++≠∈F |
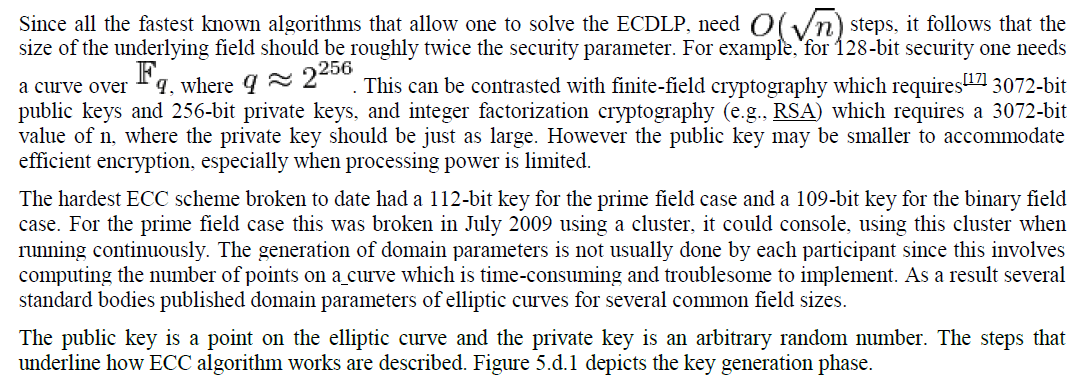 |
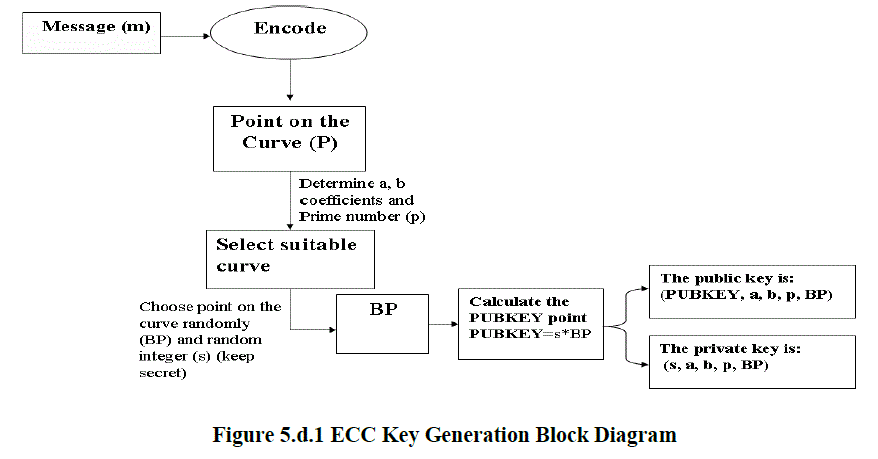 |
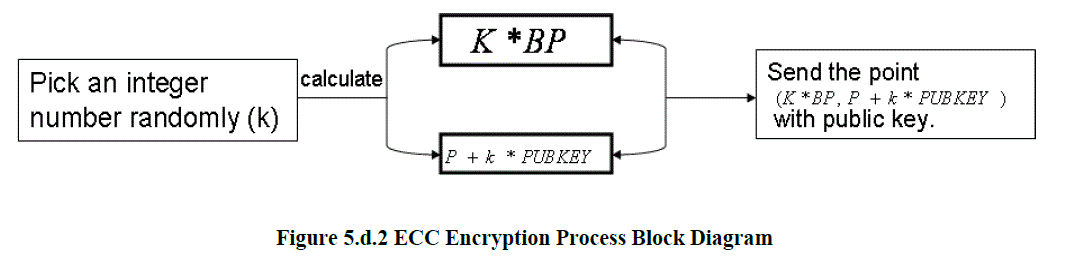
| To encrypt P, a user picks an integer, k, at random and sends the point (k* BP, P + k* PUBKEY). Figure 5.d.2 depicts the encryption operation. |
 |
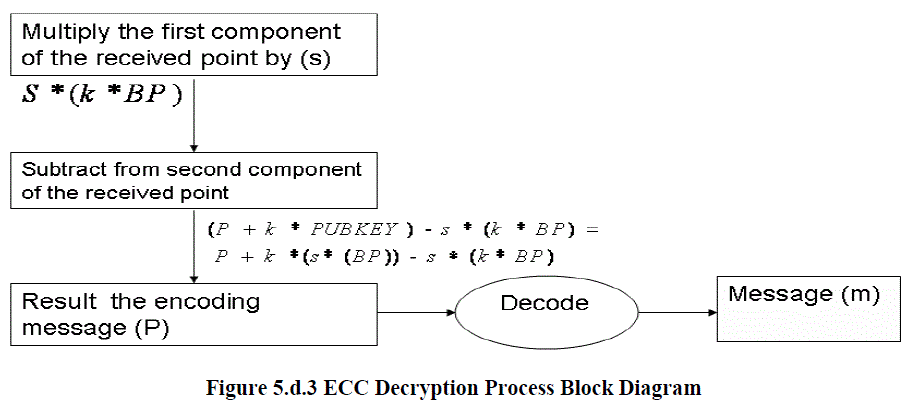
| Decrypting this message is done by multiplying the first component of the received point by the secretkey, s, and subtract it from the second component, i.e., (P + k * PUBKEY) − s * (k * BP) = P + k *(s* (BP)) − s * (k* BP) = P. This operation is shown in Figure 5.d.3. |
 |
CONCLUSION |
| Secured Data Transfer in using Hybrid Cryptography provides the hybrid cryptography method. For better communication advanced algorithms are used which will be very hard to crack. This architecture provides the secured communication in internet where the speed of the transmission would be high as there is combination of both the symmetric and asymmetric encryption standards. Employing both methods will enable the secured and hish speed data communication. The future recommendations of this project can include the selection of the appropriate encryption algorithms in such a way that all the network resources are utilized effectively and all the resource limitations of the sensor network are satisfied. |
References |
|