Keywords
|
| Steganography, X-Box, LSB Technique, Information Hiding. |
INTRODUCTION
|
| Image steganography is a method of hiding the information in the cover image Steganography, the word steganography is coming from the Greek words. stegos, means covered and the graphia means writing, it is the art and science of hiding the message in such way that only recipient can know the their is a exists of the message . Using this method, you can embed a secret message inside a piece of unsuspicious information and send it without anyone knowing of the existence of the secret message. Steganography and cryptography are very closely related. Cryptography hides the content of the messages so they cannot understand. Steganography on the other hand, will hide the both content of the message and also the existence of the message. In some situations, sending an encrypted message will arouse suspicion while an “invisible” message will not do so. Both sciences can combine to produce good protection of the message. when the steganography fails and the message can be detected, it is still of no use and it will be similar to encrypted using cryptography techniques. The principle defined by Kerckhoffs for cryptography, also holds good for steganography.The quality of a cryptographic technique should only depend on a small part of information, that is secret key. The same is valid for steganographic technique: knowledge of the system that is used in these technique, should not give any information about the existence of secret messages. Finding a message should only be possible with knowledge of knowing the secret key or stego key. |
| As the development of Internet technologies increases, the transmission of digital media is now-a-days convenient over the networks. But secret message transmissions over the Internet system suffer from serious security overhead. So, protecting of secret messages during transmission becomes an important issue In this generation, steganography is mostly used on computers with digital data being the carriers and networks being the high speed delivery channels. Figure.1 shows the block diagram of a simple image steganographic system. |
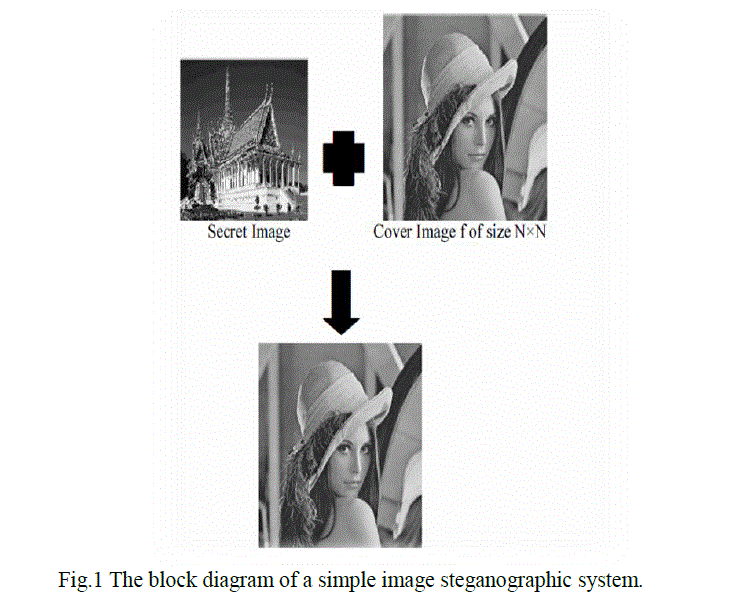 |
RELATED WORKS
|
| Least significant bit (LSB) insertion is a common, simple approach in the image steganography technique. In this method embedding information in a cover image in such a way that The least significant bit (the 8th bit) of some or all of the bytes inside cover image is changed to a bit of the secret message. For example a grid for 3 pixels of a 24-bit image can be as follows: |
| (00101101 00011100 11011100) |
| (10100110 11000100 00001100) |
| (11010010 10101101 01100011) |
| When the number 200, which binary representation is 11001000,and it is embedded into the least significant bits of this part of the cover image, the resulting grid is as follows: |
| (00101101 0001110111011100) |
| (10100110 1100010100001100) |
| (11010010 1010110001100011) |
| Although the number was embedded into the first 8 bytes of the grid, only the three underlined bits needed to be changed according to the secret message. On average, only half of the bits in an image will need to be modified to hide a secret message and it requires maximum cove size. Since there are 256 possible intensities of each primary color, changing the least significant bit of a pixel results in small changes in the intensity of the colors. These changes cannot be perceived by the human eye ,thus the secret message is successfully hidden. With a well chosen image, even we can hide the message in the least as well as second to least significant bit and still not see the difference. In the example discussed above, consecutive bytes of the image data – from the first byte to the end of the message – areused to embed the information. This approach is very easy to detect the secret message. A slightly more secure system is for the sender and receiver to share a secret key that specifies only certain pixels to be changed. It should an adversary suspect that LSB steganography has been used, no one has way of knowing which pixels to target without the secret key. LSB matching (LSBM),LSBM revised (LSBMR) [2] and Edge Adaptive based LSBMR [3] steganography techniques are popular LSB like steganography methods. |
PROPOSED IMAGE STEGANOGRAPHY
|
| Image Encoding: This technique is based on mapping of different values from x-boxes. |
 |
| Generation of four different X(X-OR)-boxes: X-Boxes are a 2x2 matrix, where 16 (0 to 15) values are stored as given fig[5]. |
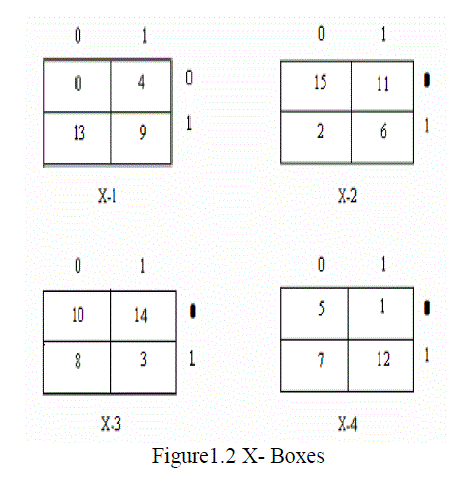 |
| To put values in X-boxes, we use X-OR property: o XOR 0 = 0 , 1 XOR 1 =0 and 0 XOR 1 = 1 , 1 XOR 0= 1. |
| For example 13 is inserted in any one of the four X-Boxes as follow: 13=1101=11 XOR 01=10 Thus the position of 13 is 2nd row and 1st column. |
| Bit Division:Then, we need to take the cipher encrypted image; say with dimension 64x64. Now, we convert the values from decimal to binary. For example, Thefust pixel value of the encrypted image=149 Then, binary of |
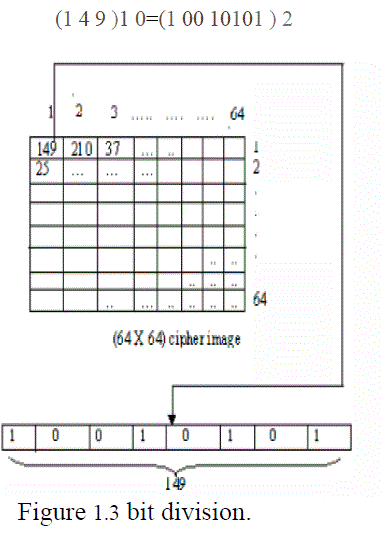 |
| Now, we need to divide this 8bit values into 4parts taking 2bits in each. |
| (1 4 9 )1 0=(1 00 10101 ) 2 |
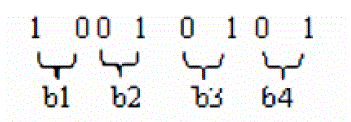 |
| X-box Mapping:Now we just map the values of b1 ,b2 , b3 ,b4 from the X-mapping box. First we take b1 =10; Then we search the value of 1st row and O th column of the X-I box; After mapping we get the value (13) 10=(1101 ) 2 Similarly we get mapping values for the b2,b3, b4;We get in the same way 11,14,1 sequentially. |
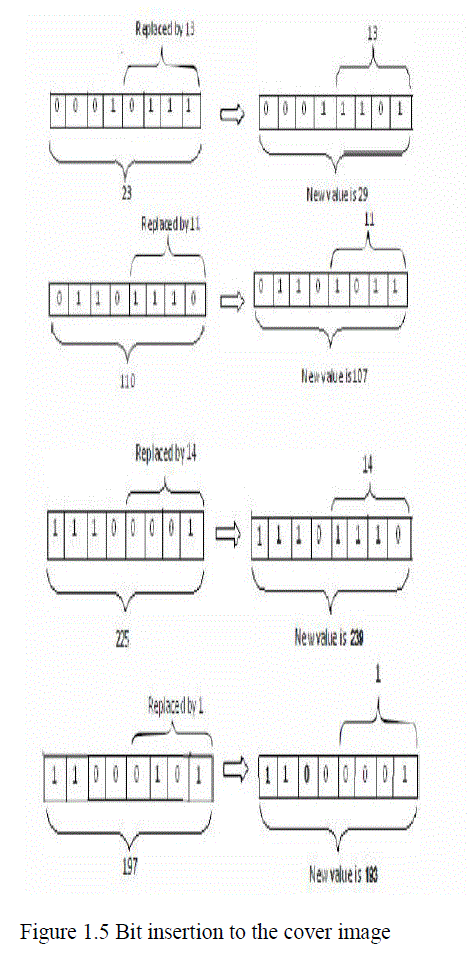
| Bit insertion into the cover image:After getting the new mapping values we insert these values into the cover image. We placed these values into the 4 bit LSB of cover image sequentially. First we take the pixels one by one from the cover image. The 4 LSB bits are replaced by 13,11,14,1 respectively. |
 |
| Here we take the pixels sequentially. |
| (23)10 = (00010111)2 |
| (110)10 = (01101110) 2 |
| (225)10 = (11100001) 2 |
| (197)10 = (11000101) 2 |
| Formation of Stego image:After getting the new pixel values we form the stego image. The pixel values 29, 107, 239, 193 are placed into the position of the previous values. Similarly we take the pixels one by one and insert the cipher image into them and replaced them. Thus we get the Stego-image |
 |
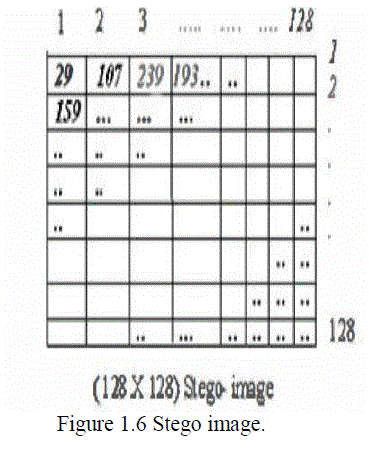 |
| These Stego image content the cipher image but we cannot recognize the cipher image. The changes of the pixel values will be varied from 0 to 15 which is a negligible amount of pixel value. So the pixel values or colors will not be change in large amount. |
EXPERIMENTAL RESULTS AND SECURITY ANALYSIS
|
| In this we will discuss the experimental results along with the security analysis.This embedding technique is no doubt a strongest Steganography technique than normal LSB encoding technique.Because, we embed each 2 bits of Cipher Image into the 4 bit of Cover Image. Again before insertion we coded these two bits by some mapping box into another form. So if one can understand that something is embedded in it, but the mapping will be totally unknown to him. So to extract the image is really a tough job. |
  |
 |
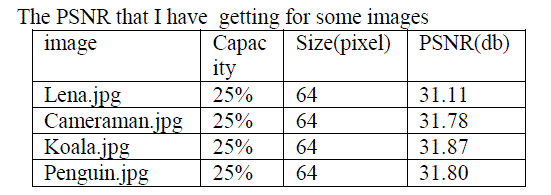 |
CONCLUSION
|
| In this paper, I have implemented a mapping based steganography process by using FPGA to improve security and image quality compared to the existing algorithms. Our approach is better because without stego key, no one can extract the original information from the stego-image, For purposes of secret communication which is more important. |
References
|
- J.R.Krenn.“Steganography and Steganalysis”
- S-FChiou “An efficient reversible data hiding scheme based on SMVQ”.
- Sivaranjani “Edge adaptive image stegnography based on LSB matching revisited”.
- Yan -ping Zhang, Juan Jiang, Chao Xu, Bo Hua “A new scheme for image hiding based on digital images” .
- Amitava Nag, SaswatiGhosh, SushantaBiswas, DebasreeSarkar, ParthaPratimSarkar“An Image Steganography Technique using X-Box Mapping”
|