“Watermarking” is the process of computer-aided information hiding in a carrier signal. Digital watermarks may be used to verify the authenticity or integrity of the carrier signal. In video watermarking, the watermark can be added either to uncompressed data or compressed video streams. Practical video storage and distribution systems store and transmit the video sequences in compressed format, such as using a video on demand (VoD) service to avoid the process of fully decoding and encoding. Most video watermarking applications require the watermark to be embedded and detected in real time. Video watermarking scheme should be robust to geometric distortions, including rotation with cropping, scaling, aspect ratio change, frame dropping, and swapping. Both the Real-time performance and resistance to geometric distortions are important requirements. Discrete Wavelet Transform is invariant to rotation, scaling, and other geometric distortions and Discrete Cosine Transform coefficients Which are subsequently used to construct one-level DWT. This reduces the computational cost and meet the real-time requirement. An additional encryption and decryption keys were used to enhance the security without affecting the quality of video is proposed.
Keywords |
| Watermarking , Discrete Cosine Transform, Discrete Wavelet Transform, Geometric distortions,
encryption, decryption. |
INTRODUCTION |
| Watermarking is a protecting technique which protects (claims) the author‟s property right for
images by some hidden watermarks. According to the domain where watermarks or confidential data are
embedded, both categories can be further classified as the time domain methods and the frequency domain
methods. |
| For spatial domain watermarking methods , the processing is applied on the image pixel values
directly. The watermark is embedded in image by modifying the pixel values. The advantage of this type of
watermarking is easy and computationally fast. The disadvantage is its low ability to bear some signal
processing or noises. |
| For frequency domain methods , the first step is to transform the image data into frequency domain
coefficients by some mathematical tools (e.g. FFT, DCT, or DWT). Then, according to the different data
characteristics generated by these transforms, embed the watermark into the coefficients in frequency domain.
After the watermarked coefficients are transformed back to spatial domain, the entire embedding procedure is
completed. The advantage of this type of watermarking is the high ability to face some signal processing or
noises. |
RELATED WORKS |
| In video watermarking, the watermark can be added either to uncompressed data or compressed
video streams. Practical video storage and distribution systems store and transmit the video sequences in
compressed format, such as using a video on demand (VoD) service system. In these cases, the watermark
should be embedded into the compressed video data to avoid the process of fully decoding and encoding[1]. |
| It is not necessary to fully decode a compressed video stream both in the embedding and extracting
processes. . The method also presents an inexpensive spatiotemporal analysis that selects the appropriate sub
macro blocks for embedding, increasing watermark robustness while reducing its impact on visual quality.
[2]. |
| A real time video watermarking algorithm based on the singular value decomposition (SVD) was
presented. The embedding procedure combines the DCT and SVD. The SVD is applied on the low frequency
AC coefficients of block DCT of the frame then the relation of neighbor coefficients of those middle
frequency bands in the singular values is modified[3]. |
| The robust watermark into video streaming according to the differential energy theory was proposed.
The region should embed watermarks according to the relationship between the energy adjustable threshold
and their differential energy[4]. |
| Unlike still image, video watermarking technology must meet the real-time requirements.
Differential Number Watermarking (DNW) was used. The label bits are embedded in a pattern of number
differences between two sub regions by selectively removing high frequency components[5]. |
| The real-time requirement of video watermarking and proposes a new improved DEW based
algorithm was addressed. Two measures to improve the DEW algorithm's performance are using the ratio of
energy difference to total energy RD to replace energy difference D as pattern to embed label bits and the
selection of embedding other is that cut-off index. The improved algorithm performs better on watermark's
visual quality impact, capacity and robustness than the original DEW algorithm[6]. |
| Digital video data distribution through the internet is becoming more common. These materials need
to be protected to avoid copyright infringement issues. Differential Energy Watermarking (DEW) algorithm is
used for the low bit-rate operation[7]. |
| The differential energy watermarking (DEW) algorithm for JPEG/MPEG streams was proposed. The
DEW algorithm embeds label bits by selectively discarding high frequency discrete cosine transform (DCT)
coefficients in certain image regions[8]. |
EXISTING METHOD |
| A. Discrete Wavelet Transform |
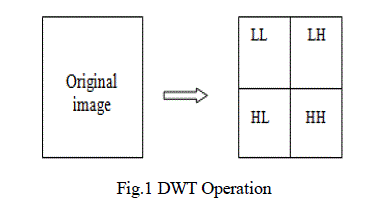
| DWT , is any wavelet transform for which the wavelets are discretely sampled. Wavelets can be used
to extract informations from many different kinds of data including audio and images.The transform generates
subband LL,LH,HL,HH each with one forth. Here most of the energy are concentrated in LL, which
represents the Low-resolution version of the original image.Among the various types of wavelet transform
Haar transform is used. |
 |
| 1) Haar Wavelet: |
| Haar-DWT, the simplest DWT . A 2-dimensional Haar-DWT consists of two operations: One is the
horizontal operation and the other is the vertical one.
Step 1: At first, scan the pixels from left to right in horizontal direction. Then, perform the addition and
subtraction operations on neighboring pixels. Store the sum on the left and the difference on the right. The
process is repeated until the rows are processed. The pixel sums represent the low frequency part while the
pixel differences represent the high frequency part of the original image.
Step 2: Secondly, scan the pixels from top to bottom in vertical direction. |
| Perform the addition and subtraction operations on neighboring pixels and then store the sum on the top and
the difference on the bottom. The process is repeated until the columns are processed.
Finally we will obtain4 sub-bands denoted as LL, HL, LH, and HH respectively. The LL sub-band is the low
frequency portion and hence looks very similar to the original image. |
| B. Discrete Cosine Transform |
| DCT has been widely deployed by modern video coding standards, for example, MPEG, JVT etc.
Like other transforms, the Discrete Cosine Transform (DCT) attempts to de correlate the image data. After de
correlation each transform coefficient can be encoded independently without losing compression efficiency. |
| 1) The One-Dimensional DCT: |
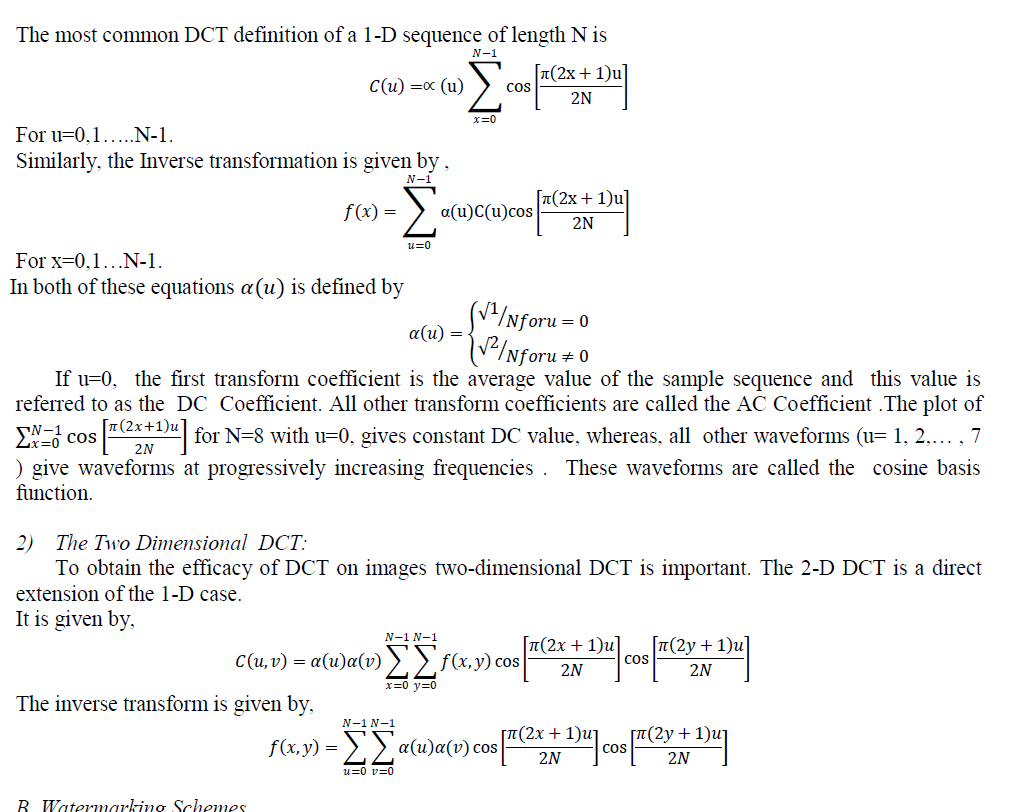 |
| B. Watermarking Schemes |
| 1) Watermarking Embedding: |
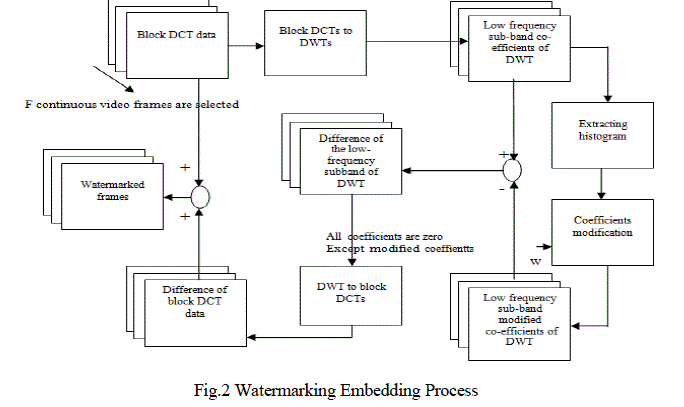
| Fig.2 shows the watermark-embedding process. In one video sequence, continuous frames are chosen to
form a basic carrier unit for watermark embedding, which we call the watermark minimal sequence (WMS).
For each frame in oneWMS, we compute the DWT coefficients directly from the block DCTs. |
| Then, we embed the watermark into the histogram bits calculated from the low-frequency sub band of the
DWT domain. The watermark W is divided into F equal-sized segments, each of which is embedded into the
histogram shape of one frame in each WMS, in order. The steps of the embedding process are as follows. |
| Step 1. For each WMS, we calculate the one -level DWT coefficient matrix of every frame from the block
DCTs. |
| Step 2. We compute the histogram shape in the DWT domain and acquire the number of coefficients in
each bit. |
| Step 3. We embed each watermark bit into two neighboring bits by reassigning the number of coefficients
in the two bits. These bits include gq(j) and gq(j + 1) coefficients, respectively. |
| We control the relative relation of the two bits in order to embed one bit of information: |
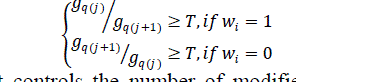 |
| where T is a threshold that controls the number of modified coefficients. We select the threshold by
considering the watermark robustness performance and the distortion.
Afterward, we embed one bit in two consecutive bins. First, we consider the case when wi is 1. If gq(j)/gq(j
+ 1) ≥T, no operation is needed. |
| Otherwise, if gq(j)/gq(j + 1) < T, some randomly selected coefficients will be moved to E1 from E2,
satisfying gq(j)/gq(j + 1) ≥ T. We repeat this procedure until watermark bits are embedded in the corresponding
frame in one WMS. |
| Step 4. The modified differences of all DWT coefficients are inversely transformed to the modified
differences of block DCT coefficients , followed by adding them to the original block DCT coefficients to
generate the new watermarked frame. This process can reduce computational cost and lower complexity
because most of the modified differences of all DWT coefficients are zero. |
| Step 5.Low bits watermark can be embedded into one WMS by repeating steps 2 through 4. |
 |
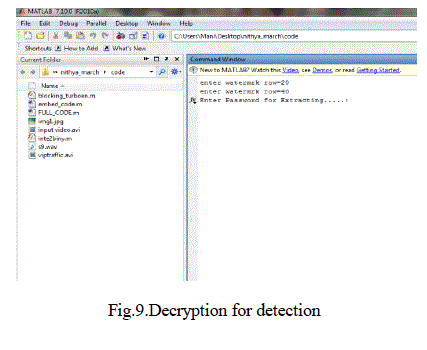
| 2) Watermark Detection: |
| The watermark detection does not need to re-encode the frames into compressed data. Compressed video
data can also be easily and quickly decoded by employing some codec or decoding chips. Therefore, we could
perform the watermark detection after decoding the video data. |
| Fig.3 shows the watermark-detection process. The detection process involves four steps. |
| Step 1 : We choose contiguous frames as one WMS with a sliding window. In each WMS, we calculate
the one-level DWT coefficient matrix RW of every frame by the Haar wavelet transform in the spatial
domain. |
| Step 2 : As in the watermark-embedding process, we compute the low frequency sub band coefficients of
the DWT domain of each frame in one WMS and generate the histogram with equal-sized bins. |
| Step 3 : The number of coefficients in two consecutive bins are gq(j ) and gq(j+1).We can extract the
hidden bit by comparing their values: |
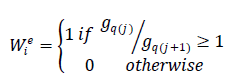 |
| We can extract watermark bits from the corresponding frame in the WMS by repeating this process. |
| Step 4 : By repeating steps 2 through 3, we can extract the Lw-bits watermark from all frames in the
WMS. The extracted watermark sequence is denoted as We= {Wei | i=1,2,.....Lw}. We can then decide the
robustness by comparing it with the original watermark sequence W. |
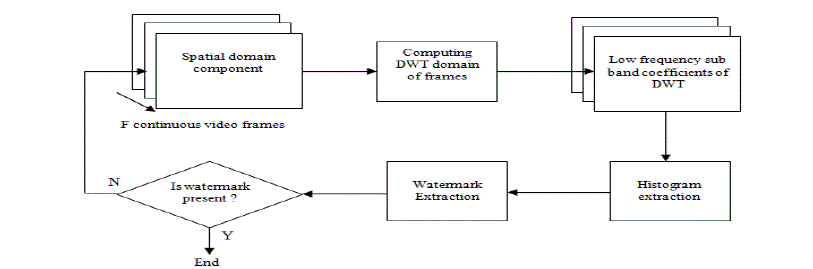 |
| Fig.3 Watermarking detection process |
PROPOSED METHODOLOGY |
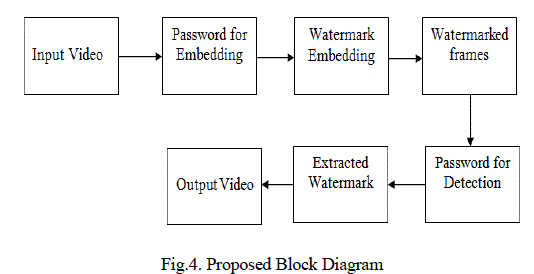
| We present a scheme which involve the secured video watermarking scheme. The secured video
watermarking process involves the additional encryption and decryption scheme additional to the
watermarking embedding and detecting process. This scheme provides the highly secured watermarking
technique. |
 |
RESULTS AND DISCUSSIONS |
| The whole watermark embedding process includes partial decoding, which consists of variable length
decoding and de quantization, the inter transformation between the DWT coefficients and block DCTs,
coefficient modification, and partial encoding. |
| we achieved robustness using the invariance of the histogram shape of the low-frequency sub band
coefficients of the one level DWT domain. The watermark embedding is designed by modulating the relative
relations of each two successive bins in the number of low-frequency DWT coefficients. |
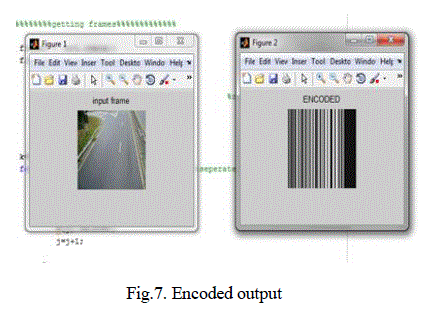
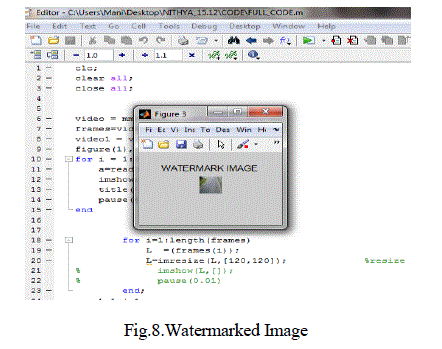
| The simulation results were obtained using MATLAB 7.10.The simulation results were obtained upto the
embedding and detecting process. The continuous video sequence were converted into frames and then the
embedding and detecting processes were simulated and is shown in the fig. |
 |
 |
 |
 |
 |
 |
CONCLUSION AND FUTURE WORKS |
| In this paper the real time video watermarking with high security and high robustness is proposed. The
future work includes the watermarking with further time reduction. |
ACKNOWLEDGEMENTS |
| The authors would like to thank Dr.S.Nirmala, Head of the Department, Department of Electronics
and Communication , Muthayammal Engineering College for her continuous support. Special thanks are due
to the referees that have made several suggestions to significantly improve the paper and the reviewers for
their valuable comments. |
References |
- Liyun Wang, Hefei Ling, FuhaoZuo and Zhengding Lu, “ Real –Time Compressed – Domain Video Watermarking Resistance to Geometric Distortions” IEEE Computer Society , 2012, pp. 70-79.
- A. Mansouri et al., „„A Low Complexity Video Watermarking in H.264 Compressed Domain,‟‟ IEEE Trans. Information Forensics and Security, vol. 5, no. 4, 2010, pp. 649-657.
- D. Wu et al., „„A Fast SVD Based Video Watermarking Algorithm Compatible with MPEG2 Standard,‟‟ Soft Computing, vol. 13, no. 4, 2009, pp. 375-382.
- T. Sun, „„A Novel Self-adaptation Differential Energy Video Watermarking Scheme in Copyright Protection,‟‟ J. Multimedia, 2009, vol. 4, no. 3, pp. 153-160.
- Po-Yueh Chen and Hung-JuLin , “A DWT Based Approach for Image Steganography” International Journal of Applied Science and Engineering 2006, pp. 275-290
- H.F. Ling, Z.D. Lu, and F. Zou, „„New Real-Time Watermarking Algorithm for Compressed Video in VLC Domain,‟‟ Proc. IEEE Int‟l Conf. Image Processing, IEEE Press, 2004, pp. 2171-2174.
- H.F. Ling, Z.D. Lu, and F. H. Zou, „„Improved Differential Energy Watermarking (IDEW) Algorithm for DCT Encoded Image and Video,‟‟ Proc. 7th Int‟l Conf. Signal Processing (ICSP), IEEE Press, 2004, pp. 2328-2331.
- I. Setyawan and R.L. Lagendijk, „„Low Bit-Rate Video Watermarking Using Temporally Extended Differential Energy Watermarking (DEW) Algorithm,‟‟ Security and Watermarking of Multimedia Contents III, SPIE Press, 2001, pp. 73-84.
- G.C. Langelaar and R.L. Lagendijk, „„Optimal Differential Energy Watermarking of DCT Encoded Images and Video,‟‟ IEEE Trans. Image Processing, vol. 10, no. 1, 2001, pp. 148-158.
- C.-S. Lu and H.-Y.M. Liao, „„Video Object-based Watermarking: A Rotation and Flipping Resilient Scheme,‟‟ Proc. IEEE Int‟l Conf. Image Processing, vol. 2, IEEE Press, 2001, pp. 483-486.
|