ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
K.Mythilipriya1, B.Arunkumar 2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
The Wireless sensor network is used to monitor the temperature, humidity, Sound, pressure, etc. Work within wireless sensor networks (WSNs) Quality of service (QoS) has been isolated and specific either on certain functional layers or application scenarios. However the area of sensor network quality of service (QoS) remains largely open. In this paper we define WSNs QoS requirements within a WSNs application, and then analyzing Issues for QoS Monitoring. In this we define IEQGOR, that integrates awake/asleep schedules, MAC, routing, traffic load balancing. A promising routing scheme in wireless sensor networks (WSNs), is shifting toward duty-cycled WSNs in which sensors are sleep scheduled to reduce energy consumption.
Keywords |
| WSN , QOS, IEQGOR , ExOR |
INTRODUCTION |
| A wireless sensor network (WSN) consists of spatially distributed sensors to monitor physical or environmental conditions, such as temperature, sound, pressure, etc. and to cooperatively pass their data through the network to a main location. The more modern networks are bi-directional, also enabling control of sensor activity. The development of wireless sensor networks was motivated by military applications such as battlefield surveillance; today such networks are used in many industrial and consumer applications, such as industrial process monitoring and control, machine health monitoring, and so on. |
| The development of wireless sensor networks was motivated by military applications such as battlefield surveillance; today such networks are used in many industrial and consumer applications, such as industrial process monitoring and control, machine health monitoring. The WSN is built of "nodes" – from a few to several hundreds or even thousands, where each node is connected to one (or sometimes several) sensors. Each such sensor network node has typically several parts: a radio transceiver with an internal antenna or connection to an external antenna, a microcontroller, an electronic circuit for interfacing with the sensors and an energy source, usually a battery or an embedded form of energy harvesting. A sensor node might vary in size from that of a shoebox down to the size of a grain of dust, although functioning "motes" of genuine microscopic dimensions have yet to be created. The cost of sensor nodes is similarly variable, ranging from a few to hundreds of dollars, depending on the complexity of the individual sensor nodes. Size and cost constraints on sensor nodes result in corresponding constraints on resources such as energy, memory, computational speed and communications bandwidth. The topology of the WSNs can vary from a simple star network to an advanced multi-hop wireless mesh network. The propagation technique between the hops of the network can be routing or flooding. |
| The WSN is built of "nodes" – from a few to several hundreds or even thousands, where each node is connected to one (or sometimes several) sensors. Each such sensor network node has typically several parts: a radio transceiver with an internal antenna or connection to an external antenna, a microcontroller, an electronic circuit for interfacing with the sensors and an energy source, usually a battery or an embedded form of energy harvesting. A sensor node might vary in size from that of a shoebox down to the size of a grain of dust, although functioning "motes" of genuine microscopic dimensions have yet to be created. The cost of sensor nodes is similarly variable, ranging from a few to hundreds of dollars, depending on the complexity of the individual sensor nodes. Size and cost constraints on sensor nodes result in corresponding constraints on resources such as energy, memory, computational speed and communications bandwidth. The topology of the WSNs can vary from a simple star network to an advanced multi-hop wireless mesh network. The propagation technique between the hops of the network can be routing or flooding |
II. RELATED WORK |
| In [1] author say that the relative complexity of problems under the restriction to unit disk graphs and to grid graphs. From these complexity results, it would seem that unit disk graphs are more closely related to planar graphs in terms of complexity than to grid graphs. In [2] author have presented a new contention-based algorithm for geographic routing that works reactively (i.e. without prior neighborhood knowledge) and guarantees delivery in unit disk graphs. Its distinct property is that no other nodes than the ones on the message path are actively involved in the communication. The Sweep Circle traversal traverses the α-shape of a network, which is a boundary of the same length or even shorter than the boundary of the Gabriel subgraph. This makes Gabriel graph planarization obsolete, regardless of whether neighbors are known (by beaconing) or not. [3] Compass Routing Suppose that we want to ravel from an initial vertex s to a destination vertex , and that all the information available to us at any point in time is the coordinates of our destination, our current position, and the directions of the edges incident with the vertex we are located at. Starting at s, we will in a recursive way choose and traverse the edge of our geometric graph incident to our current position and with the closest slope to that of the line segment connecting the vertex we are standing at to t. Ties are broken randomly. |
| In [5] author show that holes are important topological features that need to be studied. In routing, holes are communication voids that cause greedy forwarding to fail. Holes can also be defined to denote regions of interest, such as the “hot spots” created by traffic congestion or sensor power shortage. Author define holes to be the regions enclosed by a polygonal cycle which contains all the nodes where local minima can appear. Author also propose simple and distributed algorithms, the Tent rule and BoundHole, to identify and build routes around holes. In [6] author utilize position information to provide more reliable as well as efficient routing for certain applications. Thus extensions to existing position based routing algorithm have been described to work more efficiently even in cases where they are not working at present. An algorithm is proposed, which removes some of the drawbacks of the existing GPSR (Greedy perimeter stateless routing) position based routing algorithm. In proposed algorithm different algorithm has been used to planarize the graph so that it will not disconnect the route in case of location inaccuracy in perimeter mode whereas in GPSR in certain cases of location inaccuracy it will disconnect the graph and hence the packets will not be routed thereby decreasing packet delivery ratio. |
| In [7] Several routing protocols based on the positions of the mobile hosts have been proposed. The author describe a robust routing protocol that tolerates up to roughly 40% of variation in the transmission ranges of the mobile hosts. More precisely, this protocol guarantees message delivery in a connected ad hoc network whenever the ratio of the maximum transmission range to the minimum transmission range is at most √2. In [9] author presented FAR, a new face aware mobicast routing protocol, which, in theory, reliably delivers messages spatially and has good mobicast temporal characteristics. This protocol relies on the notion of spatial neighbor- hoods and features a novel timed face aware forwarding method. Since mobicast belongs to a new spatiotemporal multicast paradigm and there exists no close protocol for interesting and fair quantitative comparison. |
III. PROPOSED ALGORITHM |
| A. Description of the Proposed Algorithm: |
| The formal description of the Improved Efficient QOS aware GOR |
| S : Source Node |
| C1 : Candidate with in its communication range |
| Ci : Candidate set |
| Nei : Neighbor node |
| Two adjustable parameters introduced, which represents the minimum and maximum number of candidates to be prioritized, respectively. EQGOR will only prioritize the first k available next-hop nodes based on the observation of the similar pareto principle in GOR. For sending node i, candidates in Ci are descendingly sorted according to the ‘‘SPP PRR’’ metric. Initially, we include the first node of Ci into Fi and remove it from Ci. Then, we check nodes in Ci in sequence, where c1 always denotes the first node in Ci. When intending to add c1 into Fi, it should be within the transmission range of any node in Fi. Otherwise, it will be eliminated from Ci. If there is no packet duplication (i.e., c1 can overhear any node in Fi), we search the best place to insert c1 into Fi. The searching procedure is to try every possible inserting position in Fi, and calculate the expected single-hop packet speed values. For the remaining nodes in C, candidates will be selected to meet the hop QoS requirements at a minimum cost, i.e., simply appending to Fi. When the number of available next-hop nodes increases in dense networks, the time complexity of EQGOR. In Algorithm 1, although the first node in Ci is included into Fi directly, it is not necessary the first candidate of Fi finally. |
IV. PSEUDO CODE |
 |
V. SIMULATION RESULTS |
| The simulation is conducted using the Network Simulator NS2. To implement the proposed mechanism IEQGOR is run in NS-2. It combines geographic routing, awake-sleep scheduling, and back-to-back data packet transmission for achieving an energy-efficient data gathering mechanism. It selects the relay node, based on low traffic and link quality. It achieves remarkable delivery ratio, latency and can greatly limit energy consumption. Awake/sleep schedules, routing, traffic load balancing, and back-to-back packet transmissions has been integrated. Nodes alternate between awake/sleep modes according to independent wake-up schedules with fixed duty cycle d. |
| The simulation is done for Packet delivery ratio , Energy consumption and Delay using IEQGOR whose results are shown in Figure 1 , 2 & 3 respectively. |
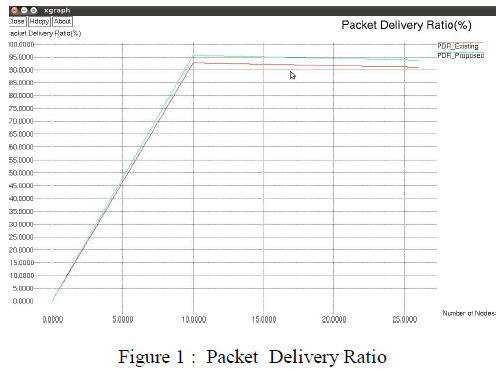 |
| The above figure shows that the Packet delivery ratio of the proposed system is better than the existing system |
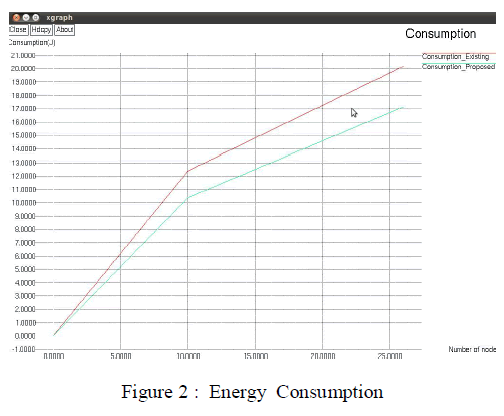 |
| Figure 2 shows that the energy consumption of the proposed system is less when compared with the existing system |
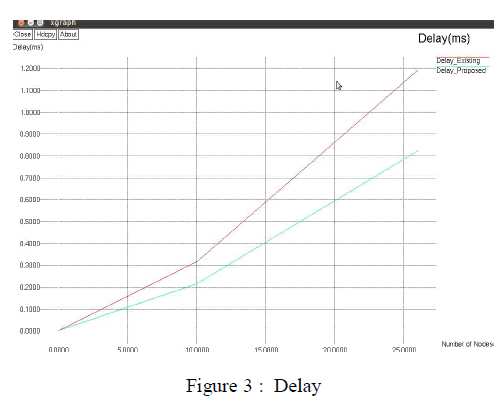 |
| The above figure shows that the delay calculated for the proposed system is less than the existing system. |
VI. CONCLUSION AND FUTURE WORK |
| The geographic opportunistic routing (GOR) exploits for multi constrained QoS provisioning in WSNs, which is more suitable than the multipath routing approach. Author founds that existing GOR protocol cannot be directly applied to the QoS provisioning in WSNs. Because the computations delay of a GOR protocol should be also considered in WSNs. The problem of efficient GOR has been studied for multi constrained QoS provisioning (EGQP) in WSNs. The EGQP problem formulated as a multi objective multi constraint optimization problem and analyzed the properties of EGQP’s multiple objectives. Based on the analysis and observations, an Efficient QoS-aware GOR (EQGOR) algorithm proposed for QoS provisioning in WSNs. EQGOR achieves a good balance between these multiple objectives, and has a very low time complexity, which is specifically tailored for WSNs considering the resource limitation of sensor devices. This can be enhanced so as to reduce the overhead. |
References |
|