Mobile Ad-hoc Network (MANET) is a group of mobile nodes that forms a network. Power constraint is a one of the major design constraints in mobile ad-hoc network. The mobile nodes are battery driven, hence it is important to extend the energy of the each node to improve the operational lifetime. The proposed energy aware routing algorithms for MANETs, called LAR (Location Aided Routing) is based on a fully distributed and a threshold based certified lake address allocation model. Energy Efficient Location Aided Routing (EELAR) Protocol was developed on the concept of the Location Aided Routing (LAR). EELAR makes considerable reduction in the energy consumption of the node batteries by limiting the area of discovering a new route to a smaller zone. Thus, the control packet overhead is reduced. In EELAR, a reference wireless base station is used and the network’s circular area centered at the base station is divided into six equal sub-areas. While LAR is deployed, the increasing in communication transparency and latency is fairly reasonable then it’s also used to dynamic based allocation protocol. The availability and the security are so guaranteed for the MANET auto configuration service while unmoving ensuring efficiently both network and security parameters for a newly arrived node.
Keywords |
| Mobile Ad-hoc network, Location Aided Routing, EELAR, routing, energy efficiency. |
INTRODUCTION |
| A Ad-hoc Network is an infrastructure less network of mobile nodes that are connected by wireless medium. Each
node transmits and receives data, but it does not route anything between the network. In this network, each mobile node
functions not only as a host but also as a router, forwarding packets to other mobile nodes that may not be within direct
wireless transmission range of each other node on the network. Thus non-infrastructure wireless network does not have
fixed router; all nodes are capable of movement and can be connected using dynamic network topologies. If the mobile
nodes are lies in the same communication range then they can communicate directly, otherwise nodes will depend on
some intermediate nodes. Current research challenges in ad-hoc networks are save energy, Limited transmission range,
Broadcast nature of the wireless network, Packet losses due to transmission errors, Limited Power Supply. |
| The paper that covers the following: Section II gives classification of MANET routing protocols. Section III contains
review of some research work in ad hoc routing protocols. Section IV describes the existing and details of the proposed
Location Aided Routing (LAR) algorithm. Section V Contains about the simulation environment. Section V Contains
conclusion. |
MANET ROUTING PROTOCOL |
| MANET routing protocols can be classified into two main categories: periodic protocols and on-demand protocols. In a
periodic (proactive) routing protocol, nodes periodically exchange routing information with other nodes in an attempt
to have each node always know a current route to all destinations. In an on-demand (reactive) protocol, nodes exchange
routing information only when needed, with a node attempting to discover a route to some destination only when it has
a packet for send to that destination In addition, some ad-hoc networking routing protocols are hybrids of proactive and
reactive mechanisms. |
A. On demand routing protocol (reactive) |
| It must be initiated a route discovery procedure to find a route. The source creates a route request (RREQ) packets to
start the route discovery. The RREQ contains the destination IP address, source IP address, sequence number for that
destination. This also contains a hop count, initialized to zero, and a RREQ ID. The RREQ ID is a per-node, the
counter incremented for every node for each process. The RREQ ID used to detect the duplicates. |
B. Table driven routing protocol (proactive) |
| The Destination-Sequenced Distance-Vector Routing protocol (DSDV) is also known as table-driven algorithm. Each
node in the network maintains one or more path to reach to its destination. The improvements made to the Bellman-
Ford algorithm include freedom from loops in routing tables. Each node in the network maintains the routing table that
has the all possible information about the destination. After the each transmission updating the routing table
information. Routing table updates the information periodically. The routing table will contains the information such as
source IP, destination IP address, etc. |
RELATED WORK |
| Major consideration in mobile ad-hoc Network as maximizing the operational life time of network. The previous work
on routing in wireless ad-hoc networks deals with the problem of finding and maintaining correct routes to the
destination during mobility. |
| In this paper two new proposed algorithms are used namely Reliable Minimum Energy Routing (RMER) and Reliable
Minimum Energy Cost Routing (RMECR). [1] The RMECR algorithm is used to find the energy-efficient and reliable
routing to improve the operational life time of the network. It considers the energy consumption and reliable energy of
the each node and also considers the quality of the links to find the reliable route and energy efficient to improve the
lifetime of the network. The RMER and RMECR algorithm proposed for network which uses either Hop-By-Hop or
End-to-End retransmission. The RMECR algorithm produces the result that is similar to the RMER algorithm. The
RMER algorithm does not consider the residual energy of the network [1].RMECR energy consumption, reliable link
and operational life time of the network. In[2] contrast to conventional power-aware algorithms, MRPC that identifies
the capacity of a each node not just by its residual energy, but also by the expected energy spent over an reliable link
for forwarding the packet. MRPC selects the path that has the largest path capacity for an critical node using max-min
formulation (the one with the smallest residual packet transmission capacity). And also present CMRPC, a conditional
variant of MRPC that switches from minimum energy routing to MRPC only when the packet forwarding capacity of
nodes falls below a threshold. In [3] Energy efficient routing and power control techniques in wireless ad hoc networks
have drawn considerable research interests recently. In this address the problem of energy efficient reliable routing for
wireless ad hoc networks in the presence of unreliable communication links or devices or loss wireless link layers by
integrating the power control techniques into the energy efficient routing. To consider both the case when the link layer
implements a perfect reliability and the case when the reliability is implemented through the transport layer, e.g., TCP.
Subsequently study how to perform power control (thus, controlling the reliability of each communication link. When
the communication links are unreliable it uses the more energy for unicast routing such as the power used by the
multicast is optimum. Energy aware routing protocol is an efficient way to extend the operational life time of the
network. Fig. 1 explains the energy consumption in multihop network. |
| In this paper [4] proposed RMECR algorithm which finds the reliable link for the packet transmission. Which consider
the energy consumed for the retransmission of the packet .The RMECR can effectively reduce the energy consumed
per each node and balance the traffic among the each node. Two important requirements of wireless ad-hoc networks: one is energy efficient and another one is reliable routing. In ad-hoc network nodes have limited battery power and
prone to transmission errors. Operational lifetime of the network is also important requirement. All of these
requirements can be achieved with the help of energy-efficient and reliable routing. An online energy aware routing in
wireless networks is the problem of finding energy efficient routes that maximize the network lifetime without the
knowledge of future message flows. Total energy consumed along the path is minimized and this path is chosen for
messages for maximizing the operational life time of the network. And also avoiding the depleted nodes. In this a twophased
energy-aware routing strategy that balances these two conflicting objectives by transforming the routing
problem into a multi-metric widest path problem. And also demonstrate a simple but insightful relationship between the
total energy required along a path and the minimum remaining energy of a node along the path. |
METHODOLOGY |
A. RMER AND RMECR ALGORITHM |
| The reliable routes that maximize the node life time if packets are transmitted through the less reliable link which leads
to the packet loss or retransmission. To avoiding this problem the packets are sent through the energy efficient and
reliable link. The energy cost of a route will be related to its reliability. Packet retransmission increases due to the less
reliable link. Due to the retransmission a larger amount of energy will be consumed per packet. Two types of energyaware
reliable routing algorithms for HBH and E2E systems are used. They are called reliable minimum energy cost
routing (RMECR) and reliable minimum energy routing (RMER). In RMER, energy cost of a path for E2E packet
traversal is the expected amount of energy consumed by all nodes to transfer the packet to the destination node [1]. |
a. Procedure for Energy-Aware Reliable Routing Algorithms for the both HBH and E2E System |
| A new routing algorithm for finding MECP between every two nodes of the network. |
| The following steps to be handle for analysis of Energy Cost of a Path. They are four steps energy cost of a path : |
| 1. Analyzing the expected transmission of data and ACK packets, |
| 2. Analyzing the expected energy cost of a link |
| 3. Analyzing the E2E reliability of a path for data transmission, |
| 4. Formulating the energy cost of a path taking into account the energy cost of links and E2E reliability of the path. |
| In E2E system, the energy cost of a path depends on the number of times that the packet and ACK are transmitted.
Formulating the reliability of data packet and ACK to determine the energy cost of a node. For RMECR, the battery
cost of a link as “the fraction of the residual battery energy of the two nodes of the link which is consumed to forward
the packet.” |
b. Total Energy consumption across a link |
| Let auv(Ld) be the total energy consumed by the transmitting node u, and buv(Ld) be the total energy consumed by the
receiving node v to exchange a packet of length (Ld) [bit][1].The Expressions are, |
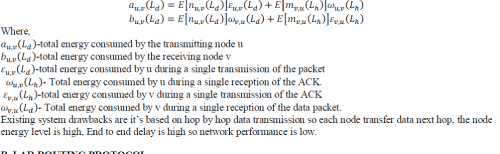 |
B. LAR ROUTING PROTOCOL |
| The new proposed energy aware routing protocol for MANETs, called Energy Efficient Location Aided Routing
(EELAR). This solution relies on a distributed and a threshold based certified cooperative address allocation model.
The new proposed security mechanisms thwart all possible imaginable attacks on auto-configuration in Ad hoc network. The cost of the security improvement brought by Location Aided routing protocol is a low increasing in
latency and communication overhead, which remains acceptable. |
| While EELAR is deployed, the increasing in communication overhead and latency is quite reasonable. The Energy
Efficient Location Aided Routing Protocol is a limited to a small area, fully dispersed energy-aware routing algorithm
but it assumes that a source swelling has the position information of its neighbors and the purpose. EELAR is
equivalent to eloquent the link costs from the starting place node to its neighbors, all the technique to the destination.
Based on this in sequence, the source cannot find the best possible path but select the next hop through which the in
general transmission authority to the end is minimized. The node based availability and the security are so guaranteed
for the Ad hoc network auto-configuration service while still ensuring efficiently both network and security parameters
for a newly arrived node. In this method to implementing the location based authentication of the process and the
system secured on the system models. Location is based to mostly implementing the resources from required logic
function on the process. Nodes which contain accomplished the meet find place in the buddy list. A node which does
not complete is shift to the query mark list, which is a list, containing information concerning the malicious nodes. The
advantages of proposed algorithm’s are Location Aided Routing protocol used so all node energy will be saved, To
identify the location so easily nodes are communicated, Network performance is high. |
RESULTS AND DISCUSSION |
| To implement the Project concept, first should have to construct a network which consists of ‘n’ number of Nodes. This
module is developed to node creation and more than 10 nodes placed in a particular distance. Wireless node placed
intermediate area. Relative to sink each node knows its location. The access point has to receive transmitted packets
then send acknowledge to transmitter. Mobile nodes are deployed in 1300m×1300m area. The simulation parameters
are as follows: |
| Number of nodes : 31 |
| Simulation time : 10 [ms] |
| Bandwidth : 10 [kbps] |
| Transmission range : 70 [m] |
| Data packet size : 512 [bytes] |
| Network area : 1300×1300 [m2] |
| Data rate : 100 [Kbps] |
| ACK packet size : 38 [byte] |
A. Data Transmission |
| Fig. 2 Source will be selected based on their node energy level. The higher energy node is selected as a source node to
transmit the data packets to the destination. |
| Fig. 3 Initially the source 1 has the higher energy after the communication the energy will be low. So that the network
searches the higher energy node and select source 2 as a sender |
| Fig. 4 Residual energy is nothing but the remaining energy in the node after the data transmission they will also be
considered for data transmission to consume energy. Fig represents the usage of residual energy. Next the source 3 has
the higher energy so it will transmit the data packet. |
| Fig. 5 Finally source 4 has the higher energy so the source4 selected as a sender for data transmission the Fig. 5 shows
that data transmission between the source4 and destination. If transmit the data packet through the lower energy node
means packets will be dropped or lost. So to avoid this problem higher energy node will be selected as a source node to
transmit the data packets to the destination. |
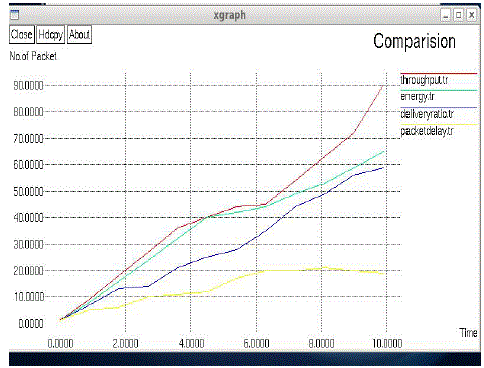
| Fig. 6 shows the comparison of network parameters such as throughput, energy, delay and packet delivery. |
CONCLUSION |
| A transmission error on a specific link implies the need for retransmissions on that link alone. This is a better model for
multi-hop wireless networking environments, which typically always employ link-layer retransmissions. In this case,
the link layer retransmissions on a specific link essentially ensure that the transmission energy spent on the other links
in the path is independent of the error rate of that link. For this analysis, do not bound the maximum number of
permitted retransmissions. A transmitter continues to retransmit a packet until the receiving node acknowledges errorfree
reception. |
| The problem of minimum energy routing for reliable one-to-one communication in the presence of loss links. Banerjee
and Misra solved the problem in the hop-by-hop retransmission model, where each link is assumed to support link layer
hop-by-hop retransmission and guarantee reliable delivery. However, link layer retransmission actually cannot
guarantee reliable delivery, due to various reasons. The algorithms are designed for computing minimum energy paths
in both models. |
Figures at a glance |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
 |
 |
 |
| Figure 4 |
Figure 5 |
Figure 6 |
|
References |
- JavadVazifehdan, R. Venkatesha Prasad, and IgnasNiemegeersEnergy-Efficient Reliable Routing Considering Residual Energy in Wireless Ad Hoc Networks, IEEE Transactions On Mobile Computing, Vol. 13, No. 2, February 2014
- Misra.A and Banerjee.S (2002) ‘MRPC: Maximizing Network Lifetime for Reliable Routing in Wireless Environments,’ Proc. IEEE WirelessComm. and Networking Conf. (WCNC’02).Vol 7,No.6, pp. 800-806.
- Li.X.-Y Wang.YChen.HChu.XWu.Y and Qi.Y( 2009) ‘Reliable and Energy-Efficient Routing for Static Wireless Ad Hoc Networks withUnreliable Links,’ IEEE Trans. Parallel and Distributed Systems. Vol. 20, No. 10, pp. 1408-1421, Oct. Routing in Wireless Networks 2004.
- Nishant Gupta Samir R. Das, (1998 )’Energy-Aware On-Demand Routing For Mobile Ad Hoc Networks’,IEEETrans.Wireless comm.., vol.6 ,no.11,pp.1300-1313.
- Mohanoor.A.BRadhakrishnan.S and Sarangan.V (2009) ‘Online Energy Aware Routing in Wireless Networks,’Ad Hoc Networks. Vol. 7, No.5, pp. 918-931.
- Canming Jiang Yi Shi and Thomas Hou.Y (2005) ‘Cherish every Joule: Maximizing throughput with an eye on network-wide energyconsumption’ Proc.IEEEWirelesscomm. Vol 3, No.5, pp.850-857.
- Chang.J.H and L. Tassiulas.L( 2004) ‘Maximum Lifetime Routing in Wireless Sensor Networks,’ IEEE/ACM Trans. Networking.Vol. 12, No.4, pp. 609-619.
- Dong.QBanerjee.SAdler.M and Misra.A (2005) ‘Minimum Energy Reliable Paths Using Unreliable Wireless Links,’ Proc. ACM MobiHoc. pp.449-459.
- Zhu.JQiao.C and Wang.X (2006) ‘On Accurate Energy Consumption Models for Wireless Ad Hoc Networks,’ IEEE Trans. Wireless Comm.Vol. 5, No. 11, pp. 3077-3086.
|