Keywords
|
| Ad Hoc Networks, Energy Aware Routing, Battery Aware Routing, Energy Efficiency. |
INTRODUCTION
|
| Wireless technologies have become increasingly popular in our everyday business and personal lives. Personal digital assistants (PDA) allow individuals to access calendars, e-mail, and address and phone number lists, and the Internet. Some technologies even offer Global Positioning System (GPS) capabilities that can pinpoint the location of the device anywhere in the world. In the wireless technologies promises to offer even more features and functions in the next few years. WSN is a very large array of diverse sensor nodes that are interconnected by a communication network. The elementary components of sensor nodes are sensing unit, a processing unit, transceiver unit. |
| The sensor nodes senses the physical quantity is being measured and coverts it into an electrical signal. After that the signal is fed to an A/D converter and is ready to be used by the processor [1]. The processor will convert the signal into data depending on how it is programmed and it sends the information to the network by using a transceiver. The sensing data is shared between the sensor nodes and are used as input for a distributed estimation system [2]. The fundamental objectives of the WSN are most reliability, accuracy, flexibility, cost effectiveness, and ease of deployment. The WSN is made up of individual multifunctional sensor nodes [3]. |
| As we know that wireless sensor network mainly consists of tiny sensor node which is equipped with a limited power source. The life span of an energy network is constrained sensor network is determined by fastly the sensor consumes energy. A node in the network is no longer useful when its battery dies. Researchers are now developing new routing mechanisms for sensor networks to save energy and pro-long the sensor lifespan. The dynamic clustering protocol allows us to space out the lifespan of the nodes, allowing its do the minimum works it needs to transmit the data [4]. The WSN can be applied to a wide range of applications, such as environment management monitoring, industrial sensing and infrastructure protection, temperature sensing. So, it is essentially to improve the energy efficient to enhance the quality of application service. In this paper, to address his problem of energy efficiency reliable routing in wireless networks in the presence of unreliable communication links or devices or loss wireless link layers by integrating the power control techniques into the energy efficient routing. The link layer implements a perfect reliability and the case when the reliability is implemented through the transport layer [5]. |
| Nodes in an ad hoc network have limited power resources as well as limited the processing power. When a routing, a sharp degradation in the network service may result if the routing algorithm does not account for the limited resources, eventually decreasing the lifetime network [6]. To maximize network lifetime, the paths for message flows are chosen in such a way that the total energy consumed along the path is minimized while avoiding the energy in the depleted nodes. To finding the path network which consume minimum energy and finding paths which do not use energy depleted nodes lead to conflicting objectives [7]. In contrast to conventional power aware algorithms, The MRPC identifies the capacity of a node just by its residual battery energy, but also been the expected energy spent in reliably packet over forwarding the specific link. Such the formulation method captures the scenarios of where link transmission costs also has depend on physical distances between nodes and the link error rates [8]. |
| A realistic power consumption model of the wireless communication subsystems can be typically used in many sensor network node devices is presented. The simple power consumption models for major components are individually identified; the effective transmission range of the sensor node is modelled by the output power of the transmitting a power amplifier, to sensitivity of the receiving low noise amplifier, and RF environment [9]. Traditionally, the PSR method is estimated to fraction of successful transmissions over a window of a test packet. Inorder to demonstrate that counting based methods do not react to changes in the wireless channel fast enough and that the only way to address this problem is to estimate the PSR based on the receiver's characteristics and on the signal to noise ratio (SNR) at the receiver [10]. |
| Instead, in QUEST, the per-rate/-neighbour management of link quality is achieved by profile lookup. We perform test bed experiments to achieve the profile and also unravel two major bugs in Midwife driver, widely employed by many researchers to build an 802.11 based system. To utilizing the large database of transmitter and receiver traces with an indigenously developed tools, in order to study the impact of an altering the averaging time period on the profile for different transmission rates [11]. |
LITERATURE REVIEW
|
[1] Max-Min Battery Capacity Routing (MMBCR)
|
| MMBCR is a power-aware routing algorithm that addressed the problem of increasing the operational life time. MMBCR used Min-Max route selection scheme. Like Min-Max route selection scheme, MMBCR selects the route whose critical node has the highest residual battery energy. In MMBCR, a cost metric Cp associates with a specific path P is given by |
| Cp = min {Bi} |
| where Bi is the residual battery capacity of node i lies on route P. The path selected by PMMBCR is given by |
| PMMBCR= max {Cp} |
| This scheme can prevent nodes from being overused. This extends the time until the first node powers down and increases the operation time before the network is partitioned |
2] Maximum Residual Packet Capacity (MRPC
|
| MRPC identifies the capacity of a node by take into account both residual battery energy and expected energy spent in reliably forwarding a packet over a specific wireless link. Like MMBCR, MRPC also used Min-Max route selection scheme. MRPC selects the route whose critical node (the one with the smallest residual packet transmission capacity) has the largest packet capacity. Let Ci, j be a node-link metric for the link (i, j) and is defined as |
| Ci, j = Bi/Ei, |
| where Bi is the residual battery capacity of node and Ei.j is the transmission energy required by node i to transmit a packet over the link (i, j). Mathematically speaking, MRPC associates with a specific path P, the maximal lifetime (the maximum number of packets that may be potentially forwarded between source and destination over the path P) Lifep given by |
| Lifep= min {Ci, j} |
[3] Max-Min Battery Capacity Routing(MMBCR)
|
| MMBCR is a power-aware routing algorithm that addressed the problem of increasing the operational life time. MMBCR used Min-Max route selection scheme (it is an algorithm which selects the path that has the highest value for its most critical node). Like Min-Max route selection scheme, MMBCR selects the route whose critical node has the highest residual battery energy. In MMBCR, a cost metric Cp associates with a specific path P is given by |
| Cp = min {Bi} |
| where Bi is the residual battery capacity of node i lies on route P. The path selected by PMMBCR is given by PMMBCR= max {Cp} |
LEACH PROTOCOL
|
| Low Energy Adaptive Clustering Hierarchy (LEACH) is the first hierarchical cluster based routing protocol for wireless sensor networks which its partitions the nodes into clusters, every each clusters dedicated to the node with extra privileges called Cluster Head (CH) is responsible for creating and manipulating a TDMA (Time division multiple access) schedule and sending aggregated data from nodes to the BS where these data is needed using CDMA (Code Division Multiple Access) remaining nodes are cluster members. |
Routing
|
| Low Energy Adaptive Clustering Hierarchy protocol is the first hierarchical cluster based routing protocol for wireless sensor network which partitions the nodes into cluster, in each clusters dedicated to the node with extra privileges called Cluster Head (CH) is responsible for creating and manipulating a TDMA (Time Division Multiple Access) schedule and sending aggregated data from nodes to the BS where these data is needed using CDMA. |
Ad-hoc networks
|
| The sensor nodes can be communication each other without via base station and the sensor networks application may be one of method or combine two kinds of methods. For example, LEACH in categorization of the sensor nodes into many clusters, and according to the algorithm select one of clusters head of them. The clusters head will be a management and then the process of the nodes been cluster, then communication between the node and sink. The cluster head is like a base station. |
Energy saving for packet sending wireless links
|
| Let x - bit represent the size of a packet transmitted over the physical link and let εu,v(x) represent the energy saving by a transmitted node u to transmit a packet of length x to a receiving node v through the physical link (u.v). ωu, v(x) denote the energy saved by the receiving node v to receive and process the packet of length x transmitted by u. Represents the energy saved by the transmission could be abstracted into two distinct parts, the circuit excluding the power amplifier of them transmitter. Power amplifier is to generate the required output power for data transmission over the air. The energy saving method is to receiving the circuit including the Low Noise Amplifier (LNA) of the receiver. |
COMPARISON OF ENERGY EFFICIENT ROUTING PROTOCOLS
|
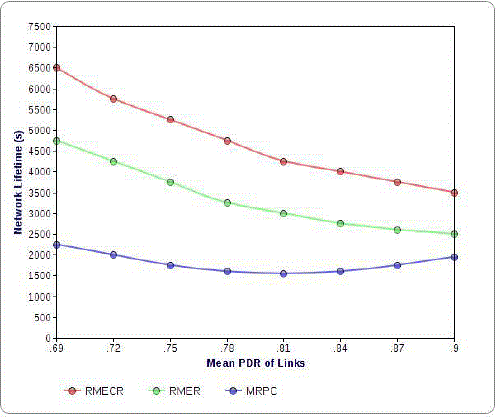
| In wireless ad hoc network, there are huge number of routing protocol using for to the better energy consumption, reliability and operational life time. The Fig I represents several routing protocols which enable to produce energy efficiency,reliability together. |
| We perform test bed experiments to achieve the profile and also unravel two major bugs in Midwife driver, widely employed by many researchers to build an 802.11 based system. To utilizing the large database of transmitter and receiver traces with an indigenously developed tools, in order to study the impact of an altering the averaging time period on the profile for different transmission rates [11]. |
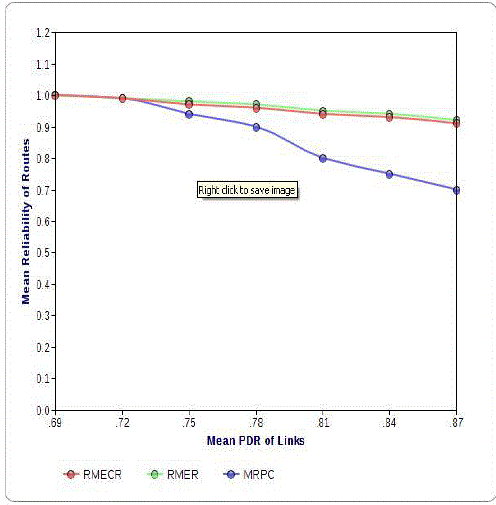
| Fig. 2 shows reliability feature of the algorithms. Similar to the RMER algorithm, RMECR is another algorithm used for able to find more reliable routes and also have better results comparing to MRPC. |
NETWORK SIMULATOR
|
| Network simulation is a technique where a program models the behaviour of a network either by calculating the interaction between the different network entities using a mathematical formulas or actually capturing and playing back observations from a production network. Network simulation plays a vital role in communication and computer network in which program models the behaviour of a network by calculating the interaction between the different network entities using mathematical formulas. The behaviour of the network can be observed in a test lab. |
| Network simulator software predicts the behaviour of a computer network. In simulators the computer network modelled and then performance is analysed. Typically the users can they customize the simulator for their specific needs. Usually simulator come with support for the protocols and network in use such as WLAN, Wi-Max, TCP, WSN, cognitive radio. Network simulator can also provide other tools to facilitate visual analysis. |
EXPERIMENTAL RESULTS
|
Existing Model:
|
| To evaluate the performance of RMECR and RMER algorithms, to consider the network in which nodes are uniformly distributed in a square area. Nodes are assumed to be static. If there is no error in the header and preamble the payload method is detected. Nevertheless, the payload is detected erroneously, the packet will be dropped. Increasing the transmission range reduces the number of times a packet needs to be forwarded en route to its final destination. |
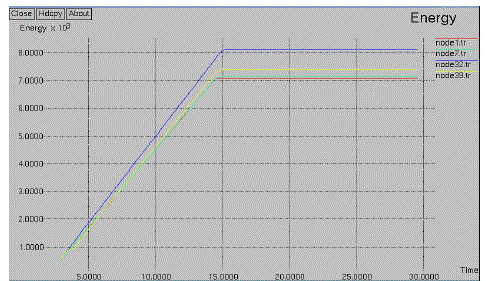
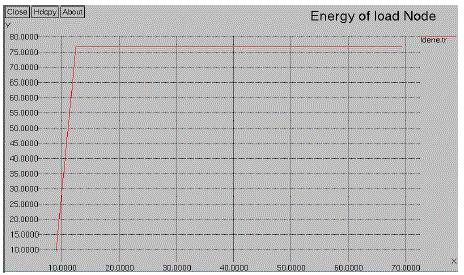
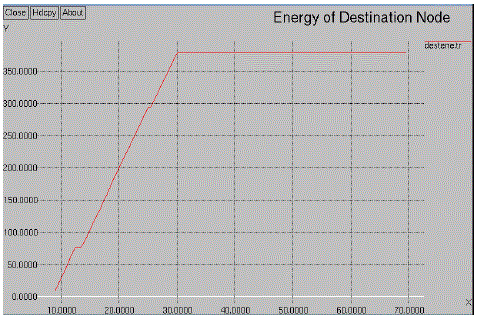
| The fig.6.1 denotes the energy diagram of existing system. In this system the threshold value only fixed to the node operation. The source node and destination nodes are automatically considered. For the node threshold value decreases the packet losses will be created. |
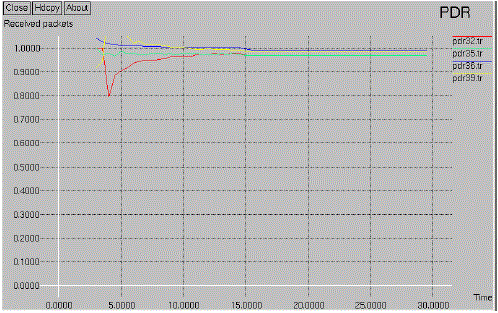
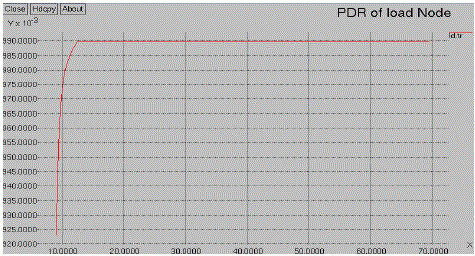
| The fig 6.2 denotes the packet delivery ratio of existing method. The ratio of the number is delivered the data packet to the destination. This illustrates the level of delivered data to the destination. In this method the packet delivery ratio is simulated. When a packet loss increases the ratio value will be increased. |
Proposed Method:
|
| The proposed method the energy efficient based life time network has used for and to create nodes, it forms to a group of clusters. The packet data has delivered to cluster. The PDR (Packet to Delivery Ratio) represents for a ratio of delivered the packets. |
| For the simulation process the threshold value, Source node, Destination node and load node has been created. For the simulation process the source node has been delivered the data between the sources to the destination via load node. In order to the process the load node has varied by means of threshold value. The data has delivered by clusters by means of load node. |
| The packet data has delivered to cluster. The PDR (Packet to Delivery Ratio) represents for a ratio of delivered the packets. For the simulation process the source node has been delivered the data between the sources to the destination via load node. |
| The data has delivered by clusters by means of load node. |
CONCLUSION
|
| In the wireless sensor networks these nodes can operates to limited the battery energy, the efficient energy utilization is very important. One of the main characteristics of the networks is that the transmission power consumption is closely coupled with the route section. The energy efficient method has been considered in the wireless ad hoc network routing, inorder to the conventional routing objective is to minimize the total consumed energy in reaching the destination. In this paper, it’s have been formulated the routing problem as maximizing the network lifetime. Some proposed schemes related to energy aware routing are summarized and some common drawbacks are detected. The idea of energy-aware routing should be further enriched with the energy overheads associated with signaling and mobility management in ad hoc wireless environments. |
Figures at a glance
|
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
 |
 |
 |
| Figure 5 |
Figure 6 |
Figure 7 |
|
References
|
- X. Li, H. Chen, Y. Shu, X. Chu, and Y.-W. Wu, “Energy Efficient Routing with Unreliable Links in Wireless Networks,” Proc. IEEE Int’l Conf.MobileAdhoc and Sensor Systems (MASS ’06), pp. 160-169, 2006.
- Nagy, A. El-Kadi, and M. Mikhail, “Swarm Congestion and Power Aware Routing Protocol for Manets,” Proc. Sixth Ann. Comm. Networksand Services Research Conf., May 2008.
- A.B. Mohanoor, S. Radhakrishnan, and V. Sarangan, “Online Energy Aware Routing in Wireless Networks,” Ad Hoc Networks, vol. 7, no. 5, pp.918-931, July 2009.
- Misra and S. Banerjee, “MRPC: Maximizing Network Lifetime for Reliable Routing in Wireless Environments,” Proc. IEEE Wireless Comm.and Networking Conf. (WCNC ’02), pp. 800-806, 2002.
- Q. Wang, M. Hempstead, and W. Yang, “A Realistic Power Consumption Model for Wireless Sensor Network Devices,” Proc. Third Ann. IEEEComm. Soc. Sensor and Ad Hoc Comm. and Networks (SECON ’06), pp. 286-295, Sept. 2006.
- M. Senel, K. Chintalapudi, D. Lal, A. Keshavarzian, and E. Coyle, “A Kalman Filter Based Link Quality Estimation Scheme for Wireless SensorNetworks,” Proc. IEEE Global Telecomm. Conf. (GlobeCom ’07), pp. 875-880, Nov. 2007.
- L. Verma, S. Kim, S. Choi, and S.-J. Lee, “Reliable, Low Overhead Link Quality Estimation for 802.11 Wireless Mesh Networks,” Proc. IEEEFifth Ann. Comm. Soc. Conf. Sensor, Mesh and Ad Hoc Comm. and Networks (SECON ’08), June 2008.
- C.-K. Toh,” Maximum Battery Life Routing to Support Ubiquitous Mobile Computing in Wireless Ad Hoc Networks” IEEE CommunicationJune 2001.
- Dongkyun Kim, J.J. Garcia-Luna-Aceves, Katia Obraczka, Juan-Carlos Cano, and Pietro Manzoni, “Routing Mechanisms for Mobile Ad HocNetworks Based on the Energy Drain Rate” IEEE Transactions on Mobile Computing, Vol. 2, No. 2, April-June 2003.
- Jae-Hwan Chang and LeandrosTassiulas,” Maximum Lifetime Routing in Wireless Sensor Networks” IEEE/ACM Transactions OnNetworking, Vol. 12, No. 4, August 2004.
- Hongwei Zhang, AnishArora, and PrasunSinha, “Link Estimation and Routing in Data driven Sensor Network” IEEE Transactions OnMobileComputing, Vol. 8, No. 5, May 2009.
|