Keywords
|
| Data hiding, Tracking, Tampering, Blindly extraction, Spread spectrum embedding. |
INTRODUCTION
|
| Data tracking and tampering are rapidly increasing in everywhere like online tracking, mobile tracking etc.So we need a secured communication scheme for transmitting the data. Forthat, we are having many data hiding schemes and extraction schemes. Data hiding schemes are initially used in military communication systams like encrypted message, for finding the sender and receiver or itâÃâ¬ÃŸs very existence. Initially the data hiding schemes are used for the copy writepurpose. In [1] Fragile watermarks are used for the authentication purpose,i.e to find whether the data has been altered or not. Likewise the data extraction schemes also provides a good recovery of hidden data .This is the goal of the secured communication. |
II RELATEDWORK
|
| There are many data hiding and data extraction schemes are comes into existence. The important data hiding technique is steganography.It is differ from cryptography in the way of data hiding. The goal of steganography is to hide the data from a third party whereas the goal of cryptography is to make data unreadable by a third party. In [2] The steganalysis method is used. The goal of steganalysis is to determine if an image or other carrier contains an embedmessage. In my project the concept of „Watermarked Content only attackâÃâ¬ÃŸ in the watermarking security context is taken.i.e the blindly recovery of data is considered. In [3],in steganalysis concept it is said to be Universal Steganalysis means instead of using any priori information ,they take into account all available steganography methods to devise a single steganalysis framework. This approach can detect any steganography if sufficient numbers of cover and stego images have been taken into account during the design process.In [4] spread spectrum embedding algorithm for blind steganography have based on the understanding that the host signal acts as a source of interference to the secret message of interest.Such knowledge can be useful for the blind receiver at the recovery side to minimize the recovery error rate for a given host signal.To increase the security and payload rate the embedder will take multicarrier embedding concept. In [5] the spread spectrum communication is explained. Here a narrow band signal is transmitted over a much larger bandwidth such that the signal energy present in any single frequency is imperceptible. Similarly in SS embedding scheme, the hidden data is spread over many samples of host signal by adding a low energy gaussian noise sequence. The DCT transformation is taken for embedding purpose as a carrier since it is a fast algorithm and for itâÃâ¬ÃŸs efficient implementation. In [6] the Generalized Gaussian Distribution (GGD) has been used to model the statistical behavior of the DCT coefficients. In [7] there are many extraction procedures to seek the hidden data. Butit is having some disadvantages. Iterative Least Square Estimation (ILSE) is prohibitively complex even for moderate values. Pseudo-ILS (ILSP) algorithm is not guaranteed to converge in general and also it provides measurably worse results.So,these two algorithms coupled and so called Decoupled weighted ILSP(DW-ILSP).But here also have an disadvantage like ,it may not be valid for large N.. |
III PROPOSED SYSTEM
|
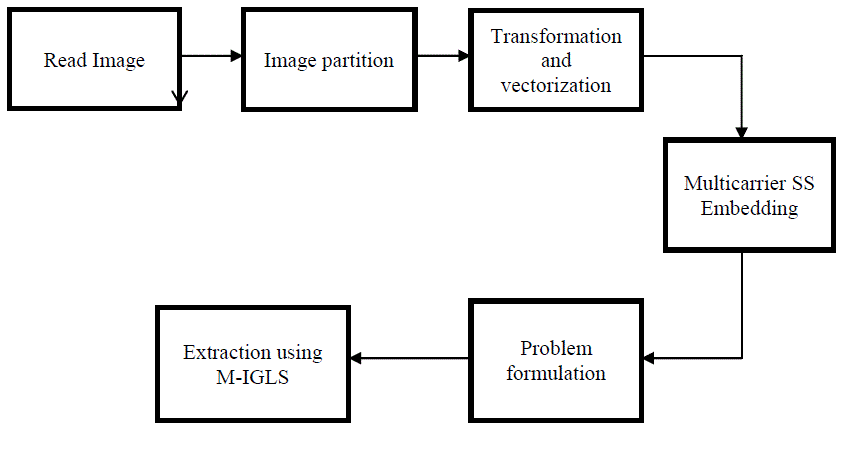
| The proposed system uses blind recovery of data and it uses the DCT transform as a carrier for embedding the data in digital media.Embedding is performed by using multicarrier SS embedding technique.It uses M-IGLS algorithm for the extraction of the hidden data.It is a low complexity algorithm and provides strong recovery performance. It attains equal probability of error recovery to known host and embedding carriers.It is used as a performance analysis tool for the data hiding schemes. |
IV MODULEDESCRIPTION
|
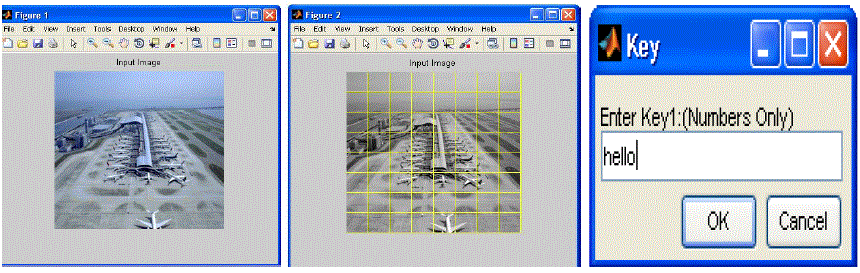
| Preprocessing and image partition:The hidden message has to hide in digital media like audio,video or image. Herefor hiding the data image is taken as host.Image can either as RGB or gray scale image.Image is partitioned into nonoverlapping blocks. Each block should carry hidden information bits. Forthat, block division features are to be known. The image is divided into blocks on the basis of 8*8 matrix. This 8*8 blocks are independently processed for embedding in different domain. Bythis, the embed blocks are synchronised. |
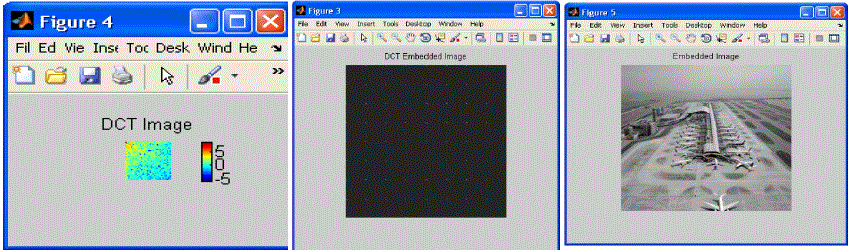
| Transformation and vectorization: For image transformation, we will take the DCT transform. It is well known that DCT transformation provides excellent energy compaction in low spectral coefficients for highly correlated data. Any disturbance directly or indirectly added in the frequency domain may result in a change of statistical properties.DCT is applied in blocks of 8*8 matrix. The gaussian distribution is used to model the statistical properties of the DCT coefficients. Then the vectorization process will undertaken.Vectorization is the process of converting raster graphics to vector graphics. Multicarrier SS embedding: The embedding method is designed to satisfy the perceptual constraints and improve the detectability as well as the embedding rate. Instead of the pixel value, the histogram can be modified to embed the data. If we examine typical histograms of DCT coefficients we will find some samples have high amplitudes that the generalized Gaussian model cannot adequately found. We will consider the DCT coefficients whose amplitude is below a certain threshold value. In this embedding scheme, the hidden data is spread over many samples of host signal or image by adding the DCT coefficient as the carrier. |
| Problem formulation: With high resolution digital images as carrier, detecting hidden nessages is also considerably difficult. The hiddenimage often a binary sequence in embedded by substituting a host signal component with a quantized value. Thequantization error will produce due to data embedding. As per the embedding rule, the quantization error α>0.5 is added back to quantization value in order to compensate for quantization distortion. During the detection, the original image is not available we must treat it as additive noise. The distortion can be occurring due to the original host image and due to the embedding and compression process. Featurevector extraction is used to achieve the detection. |
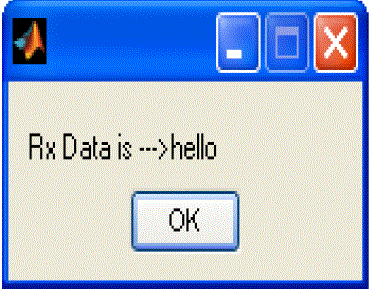
| Data extraction using M-IGLS: After the detection process, if the data is present in the image, then we have to extract it. So we are using an algorithm known as Multicarrier Iterative Generalized Least Squares. This comprises the following steps. Each time compute a least squares. Update for one of the unknown matrices conditioned on a previously obtained estimate for the other matrix. Proceed to update the other matrix and repeat until convergence of the least squares cost function is reached. Convergence is the property that different transformation of the same state have a transformation to the same end state. Convergence of the least square cost is guaranteed since each update may either improved or maintained. The final output is generally dependent on the initialization. |
V RESULT
|
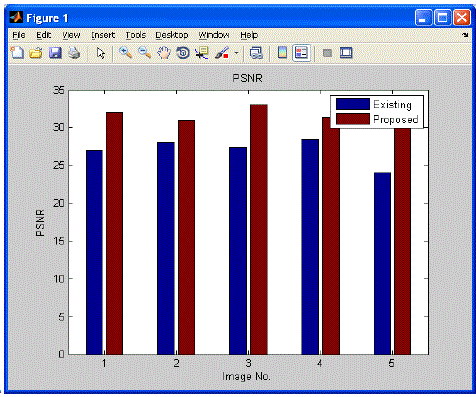
| The proposed method is to extract the hidden data from the digital media. Here blindly recovery of data is considered. That is the original host end embedding carrier is not need to be known. This method uses multicarrier embedding and DCT transformation for the embedding the data into the host image. The M-IGLS algorithm is used for the extraction purpose. This algorithm is a low complexity algorithm and it attains the probability of error recovery equals to known host and embedding carriers. It is used as a tool to analyse the performance of the data hiding schemes. |
| In this performance graph peak signal-to-noise ratio,extract the hidden data from the digital media.PSNR is most commonly used to measure the quality of reconstruction of image compression. PSNR is the ratio between the maximum possible power of a signal and the power of corrupting noise that affects the fidelity of its representation. For color images the image is converted to a different color space and PSNR is reported against each channel of that color space. Typical values for the PSNR in lossy image and video compression are between 30 and 50dB.This was obtained in our proposed system. For higher value the bit rate is to kept better. |
VI CONCLUSION AND FUTURE WORK
|
| Data tracking and tampering is rapidly increasing in communication. So we have to secure the data from the trackers. Hence we need a robust and secured data hiding and extraction schemes. The main aim of the proposed system is to provide a good extraction technique which considered the blindly recovery of data. This method uses the M-IGLS algorithm for the extraction. The data is embedded via DCT transform by multicarrier SS embedding. This extraction technique will provides high peak signal to noise ratio and it will attains the probability of error recovery equals to known host and embedding carriers. This technique is enhanced by using harmony search algorithm where it provides low time consumption and high attack resistance. |
| |
Figures at a glance
|
 |
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
Figure 5 |
|
| |
References
|
- F.A.P.Petitcolas,R.J.Anderson,andM.G.Kuhn.”Informationhiding.A survey,”,Proc. IEEE, Special Issue on Identification and ProtectionofMultimedia Information, vol. 87, no. 7, pp. 1062–1078, Jul. 1999.
- S. Lyu and H. Farid, “Steganalysis using higher-order image statistics,”IEEE Trans. Inf. Forensics Security, vol. 1, no. 1, pp. 111–119, Mar.2006.
- G. Gul and F. Kurugollu, “SVD-based universal spatial domain imagesteganalysis,” IEEE Trans. Inf. Forensics Security, vol. 5, no. 2, pp.349–353, Jun.2010.
- M. Gkizeli, D. A. Pados, and M. J. Medley, “Optimal signature design for spread-spectrum steganography,” IEEE Trans. Image Process., vol.16, no.2, pp. 391–405, Feb. 2007
- C. Fei, D. Kundur, and R. H. Kwong, “Analysis and design of watermarking algorithms for improved resistance to compression,” IEEE Trans. ImageProcess., vol. 13, no. 2, pp. 126–144, Feb. 2004.
- C. Qiang and T. S. Huang, “An additive approach to transform-domaininformation hiding and optimum detection structure,” IEEE Trans. Multimedia,vol. 3, no. 3, pp. 273–284, Sep. 2001.
- T. Li andN.D. Sidiropoulos, “Blind digital signal separation using successive interference cancellation iterative least squares,” IEEE Trans SignalProcess., vol. 48, no. 11, pp. 3146–3152, Nov. 2000
|