Keywords
|
| Face Recognition, GSM Module, MMS Module, Radio Frequency Identification technology, Thumb Registration. |
INTRODUCTION
|
| In today’s world owing a car is not a big deal but safeguarding the owned car has become a great deal. Even though the modern automobiles are heterogeneously combined by the combination of latest digital components it had also created the opportunity for new attacks [1]. A recent statistical report by United States of America (USA) has stated that around 2800 vehicles are being stolen in an average for a day. While the automotive industry has always considered safety a critical engineering concern, it is not logical whether the vehicle manufacturers have anticipated in their designs and the possibility of an adversary. Compounding this issue, in order to resolve the attack over the automotives many security systems such as car alarm, radar communication system and immobilizer perceptions are in existence. The current prevailing security system has certain disadvantages by itself [2] .Hence it has become evident to develop a security system to make an identity and monitor the security of an automotive. |
OVERVIEW OF THE PROJECT
|
| The ultimate aim of this project is to provide a hi-tech security to the automotive and preventing the unauthorized persons from accessing it .The proposed system possess three modes of operations namely training mode, automatic mode and the manual mode. In the training mode certain parameters of the driver such as name, license number, employment ID, and blood groups are initially collected in the database for each individuals. The corresponding person’s thumb impressions in different textures will be trained using Pattern Matching Algorithm (PMA). Parallely the facial image of the individual will also be put together and accumulated as a total database. In the automatic mode, system will be verified with the RFID module based testing. Based on the result obtained, if matched with the above criterion will be placed in the thumb registration system. The verification of this module leads to the face recognition in which the faces of the current person will be compared with the training faces and the selection of the original image will be done using the Principle Component Analysis (PCA) algorithm. Soon after the assessment the user will be permitted to drive the vehicle. |
| In case of emergency the key will be inserted in the key insertion slot after which the camera in the car takes the snap of the person who drives the car .The snap shot will be messaged to the owner with the help of Multimedia Messaging Service (MMS).The owner after providing the password makes the driver to drive the car.The path of the car will be traced with the help of the Global Positioning System (GPS) module with the help of which the location of the car is monitored and the car will also be stopped by providing the password to the system by the owner if required. All the above mentioned technologies will be tested using the LabView software. Based on the results obtained from the software, the design of hardware is done with the suitable components. The steps are taken to reduce the time delay required to complete these modules successfully by the authenticated user. |
LITERATURE REVIEW
|
| Security systems nowadays have become a need for vehicles available with many modern features. This car security system with extra access and intelligent alarming. This system will be accessed and configured by owner using Bluetooth module communication via mobile phone to turn in on or off [3]. This system suggests that GSM based security system are more stout then an ordinary security system .The ordinary systems are simply based on the concept of sensors .They sound an alarm on detecting movement [4,5]. This system of technology has now lost its appeal as it became a common sighting in meteors where these alarms go of unnecessarily. Due to the insecure environment the ratio of the vehicle theft increases rapidly [6]. Because of this the manufactures of the automotive are taking some serious steps for the protection of their valuable vehicles which includes activating alarms, steering wheel lock systems. They ensure authorization for the owners and also inbuilt these anti-theft system to prevent car from theft [7]. |
| Drawbacks |
| The automotive theft and the hijackings had been taken place by common ways of stealing cars .This is done by deactivating the alarm or steering wheel lock by cutting wires, but the methods proposed in above surveys would also sound ineffective [8]. The drawback of this system is, the results obtained from RADAR are not accurate. The drawback of immobilizer concept was the software present in the system could be hacked easily. |
BLOCK DIAGRAM OF THE SYSTEM
|
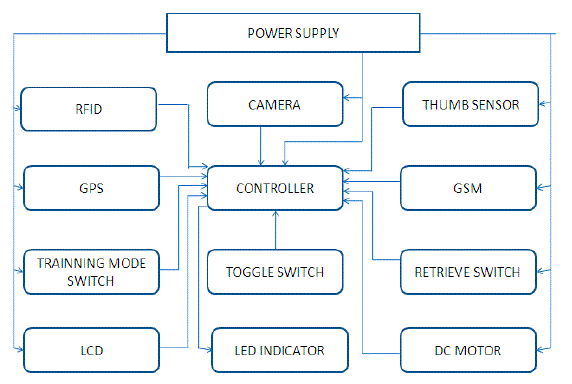
| The block diagram of the overall system is shown in the fig 1. It comprises of many modules such as RFID system, Thumb Registration system, face recognition system as its main segments .It also includes different modules such as GPS, Toggle switch for toggling purpose, and Retrieving switch along with the LED and LCD indication .All these modules are supplied with power with the help of Power supply unit. |
STRUCTURE OF RFID SYSTEMS
|
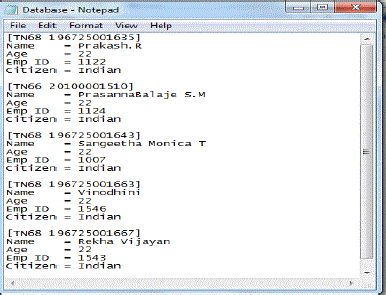
| The modules that are required to design this system are as follows Voltage Maintainer circuit, Oscillator block, Transistor-Transistor Logic (TTL), Encoder.Voltage Maintainer converts 5v to 3.3vusing IC-LM358 for maintaining at the appropriate voltages [9]. These kinds of maintainers are preferred for baud rate at 2400 rates per second. The Oscillator will be employed in order to avoid the ripple factor. They also use the filters to achieve resonant frequency generated at the rate of 125 KHz at the baud rate of 2400.Helical type of antenna is employed in this paper. The Transistor-Transistor Logic (TTL) uses up to convert 3.3v to 5v of power supply.Zener diode is used to regulate the voltage. Common emitter configuration is carried out in TTL logic. The database of RFID system is shown in fig 2. |
THUMB REGISTRATION SYSTEM
|
| Fingerprint Identification and Digital Certification and it is used in a wide range of embedded applications. It features with the SEA/RSA accelerator engines, the embedded non-volatile memory (Flash/OTP), the fingerprint processing accelerator and its algorithm firmware. Cordis 5+ is the 32-bit RISC core which is featured with 16-/32-bit ISA and Harvard bus architecture. The Enhanced DSP instruction extensions and accelerators are supported by this core system. In addition, a 5-stage pipeline is used to increase the amount of operational parallelism, giving the most performance out of each clock cycle. It is competent for System on Chip (SOC) products targeted at consumer, networking, automotive and other cost-sensitive markets. The image of synochipis shown in the fig 3. |
| The thumb impressions of different users are taken initially and stored.The database is chosen as such, the RFID of a particular user has to get matched with the thumb impression. They are matched using the PMA.This algorithm was used inbuilt in the embedded programming .The image of thumb impression for different users is shown in the fig 4. |
IMPLEMENTATION OF MODULES
|
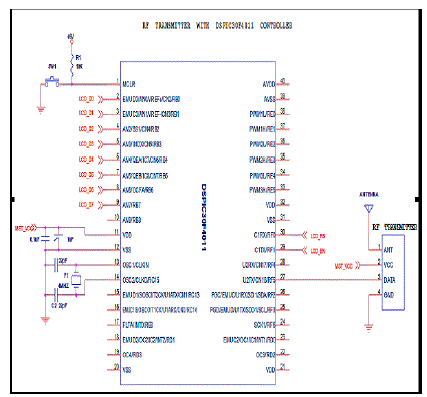
| A. INTERFACE OF RF MODULE WITH DSPIC |
| The RF transmitter employs a SAW-stabilized oscillator, for ensuring accurate frequency control for best range performance. It receives serial data and transmits it wirelessly through RF through its antenna. The bandwidth of RF transmitter works on typical frequency of 12 Megahertz. The LCD is seized with the circuit to display the required information. The interface of DSPIC with RF module is specified in the fig 5. |
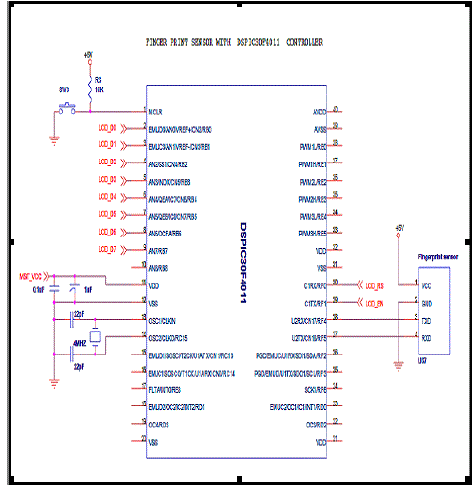
| B.INTERFACE OF FINGER PRINT SENSOR WITH DSPIC |
| Fingerprints are the traces of an impression from the friction ridges of any part of a human or other primate hand. The finger print sensor consists of a synochip which incorporates the various images of finger prints. It features with the SEA/RSA accelerator engines, the embedded non-volatile memory (Flash/OTP), the fingerprint processing accelerator and its algorithm firmware. Synochip works on typical frequency of 120 MHz .The DSPIC is interfaced with the finger print sensor as shown in the fig6. |
RESULTS AND DISCUSSIONS
|
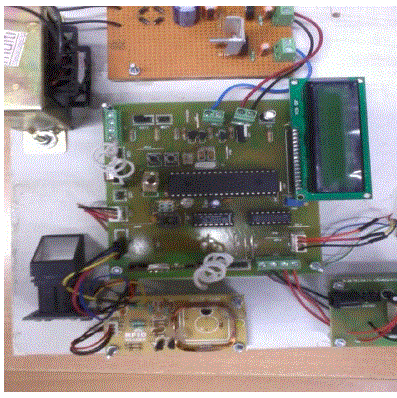
| On following the above procedures and methodology hardware implementation as well as the software implementation has been done. The software implementation is done withthe help of LabVIEW software. The fig 7.1shows the result of the overall hardware implementation of RFID systems and thumb registration. |
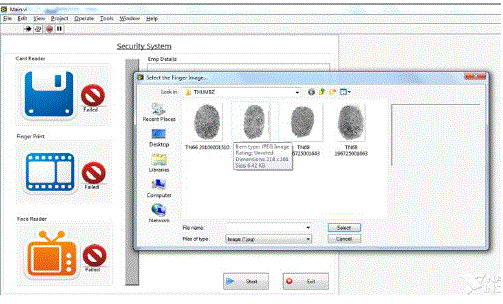
| The biometrics recognition has been implemented. This module testing has been executed with the help of LabVIEW software. The analysis of the system is done with the help of Pattern Matching Algorithm (PMA).The fig 7.2 displays the output of thumb authentication system. |
CONCLUSION
|
| Hence these modules are fully designed and implemented. In future this thumb registration will be followed by the face recognition .After developing the face recognition system .The modules such as MMS and GPS will be implemented in the forth coming days. It is totally dealt with the external security to the automotive .In future this project may extend its security for the human beings to safe guard their valuable life from accidents. Even if occurred, the monitoring necessities such as the status of the person, the heartbeat, the pulse of the human and the condition of the patient will be reported to their relatives and the nearby hospitals .These ideas will be implemented in future. |
ACKNOWLEDGMENT
|
| The authors would like to thanks the Management, Principal and the HOD Electronics and Communication Engineering, Dr.N.G.P.Institute of Technology, Tamil Nadu, India for their support and technical advices. |
Figures at a glance
|
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
 |
 |
 |
 |
| Figure 5 |
Figure 6 |
Figure 7 |
Figure 8 |
|
| |
References
|
- Dong-Sun Kim. Member, IEEE, seung- yerlLee,Member,IEEE,Byung-SooKim.Member,IEEE,Sung-Chul Lee and Duck-JinChung,Member,IEEE “on the design of an Embedded Biometric Smart Card Reader”, IEEE Transactions on RIFD systems ,Vol 3, PP.573-577,June 2010
- Jifeng Dai and JieZhou, Senior Member, IEEE,” Multifeature-Based High-Resolution PalmprintRecognition”,IEEE Transactions on PatternAnalysis and Machine inteligence.Vol.33 No.5., pp.945-957, May 2011.
- Zhijian Hu and Yunping Chen,” New Method Of Live Line Measuring the Inductance Parameters Of Transmission Lines Based On GPSTechnology”,IEEE transactions on power delivery.vol.23 pp.1288-1295, july2008
- Simon Sarkka,Member,IEEE,VilleV.Senoir Member, IEEE , MilikaHuusko , and KaarleJaakkola,” Phase-Based UHF RFID Tracking WithNonlinearKalman Filtering and Smoothing” ,IEEE Sensors journal.vol.12.no.5,pp.904-910, May 2012.
- P.K.Chan student Member ,IEEE,C.S.Choy,SeniorMember,IEEE,C.F.Chan,Member,IEEE,K.P.Pun,Member,IEEE,” Preparing Smartcard forthe F uture:From Passive To Active”,IEEE transactions on smart card ,vol 3,pp.245-250,april 2010.
- MauricioPamplonaSegundo, Luciano Silva, member;IEEE, Olga Regina Pereira Bellon, Member, IEEE, and ChauaC.Queirolo,” AutomaticFace Segmentation and Facial Landmark Detection in Range Images”, IEEE Transactions on systems man and cybernetics-part b:cybernetics.Vol.40.no.5,pp.1319-1330, october 2010
- Sarnin, S.S. Member, IEEE, Tahir, M.H.B.M. Member, IEEE, “Immobilizer Engine Control Unit (ECU) Using Radio FrequencyModule”,IEEE Trans. Ind. Electron.,pages 323-328, april 2007.
- Samarabandu, J.Member, IEEE ; Sidhu, T.Member, IEEE ; Beresh, R.Member, IEEE ; Jian-Cheng Tan Member, IEEE“Security Analysis andAuditing of IEC61850-Based Automated Substations,PowerDelivery”,IEEE Transactions on Volume:25 , Issue: 4 Page(s):2346 – 2355, Oct.2010,
- Brooks, R.R. Member, IEEE ; MD Sander, S.Member, IEEE ; Juan Deng ; Taiber, J.Member, IEEE “Automobile security concerns”VehicularTechnology Magazine, IEEE, Volume:4 , Issue: 2 Page(s):52 – 64, June 2009
|