Keywords
|
| Cloud, Cloud Service, Smat Education, SaaS, PaaS. |
INTRODUCTION
|
| Cloud computing is not a new technology but is to construct computing environment like a big cloud by mixing the virtualization technology for existing grid computing, distributed computing, utility computing, web service, server and storage with the existing base technologies such as open source software. These cloud computing technologies are mostly being studied to be utilized in reducing corporate costs. Ian Poster, Ph. D., a professor with University of Chicago defines cloud computing as a "large-scale distributed computing paradigm that is virtualized, dynamically scalable and manageable, and economically feasible, in order to offercomputing power, storage, platform, and service on Internet upon an external client's request".This study was made on cloud that is practical and available in the field of education, contrary to previous corporate efficiency studies. In addition to Green IT emerging as a global issue, issues that were sought for in this study were defined as Clean IT, Open IT, and Global IT, and a new cloud model meeting this, EaaS cloud model, was developed. According to the smart education promotion strategy of the Ministry of Education, Science and Technology in 2011, a huge cost was funded for the program to construct smart education system in all of domestic elementary, middle, and high schools by 2015. However, several problems have been found in the actual research model schools, which was an obstacle to the promotion of smart education. Among those problems, it was frequently pointed out that there was difficulty in smart device uses and that there was difficulty in teaching the classroom itself when a student had system problem during smart education. Also, in the aspect of contents use by students, various kinds of contents shall be provided, and standardized environment shall be offered for onlinebased student rating system in the smart era. As an education system model to solve those problems of smart education, a new cloud service, EaaS service model, is presented in this study. In this study, an idea was conceived that as long as network line speed is fully secured, a remote high performance cloud computer can be used like my computer by mixing the SaaS cloud model and virtualization technology and solving technical problem in applying this to education. For this, in this study, a BCN-based model was designed and tested. The existing SaaS cloud server has a disadvantage that once one user terminal receives the service, the use is limited except the relevant server. Consequently, with increased users, expansion of the server occurs simultaneously. This leads to multi-tenancy of a single instance of the existing SaaS. That is, multi-tenancy shall be supported to utilize cloud service in education. To settle this problem, a certification system server was constructed to control and manage service at the previous step of cloud service, virtually implementing a server level of multi-tenancy in this study. Namely, EaaS(Education as a Service) service was developed as a new cloud certification service to implement Cloud in Cloud(Cloud of Cloud) service. Section 2 Related Studies describe the concepts and definitions of cloud service, virtualization, and Green IT with Clean IT, Open IT, and Global IT newly defined in this study. Section 3 describes EaaS System Design, Section 4 describes EaaS system test results, and Section 5 draws a conclusion. |
RELATED STUDIES
|
| The successful employment of semantic web services is dependent on the availability of highquality ontologies. Building such ontologies is difficult and costly, thus hampering web services deployment. Our ontology learning method [6] automatically generates ontologies from WADLs (Web Application Description Languages)[7] and their underlying semantics. |
| CLOUD COMPUTING SERVICE |
| Cloud computing is divided into three based on offered service: Software as a Service(SaaS) to rent user required software, Platform as a Service(PaaS) to provide professional system environment, and Infrastructure as a Service(IaaS) to provide hardware necessary for computing such as CPU, memory, graphic, data storage, etc. through network.<Table 1> [1-3,6-10]. |
| VIRTUALIZATION |
| Displayed equations or formulas are centered and set on a separate line (with an extra line or halfline space above and below). Displayed expressions should be numbered for reference. The numbers should be consecutive within each section or within the contribution, with numbers enclosed in parentheses and set on the right margin. Virtualization is defined as a technology to efficiently use resources by logically integrating the physically different systems or logically dividing one system[80]. Virtualization has become an essential element for nearly all clouds. Cloud shall perform several user applications, and in user's eyes, it shall be viewed as if all applications are being simultaneously performed and all available resources can be used in the cloud. In virtualization, through abstraction, base fabric is integrated into a pool of resources, and resource overlay(e.g. data storage service or web hosting environment) can be built on it. Also, in virtualization, applications can be composed, arranged, started, moved, paused, resumed, and ended as each application is encapsulated, and better security, manageability, and Isolation are provided. |
| Virtualization method is divided into three: Bare-Metal/Hypervisor or Full Virtualization, Para-virtualization, and Host Para-virtualization.Full Virtualization and Para-Virtualization are intended to make several operating systems of the virtual machine use hardware resources of the host in division through control program called hypervisor, instead of emulating hardware of the virtual machine. Full Virtualization is a technology of providing guest operating system that is not corrected by virtualization software on the Full Virtualization environment, where general-purpose x86 virtualization hardware(CPU, memory, disk, I/O unit, etc.) is constructed on VMM. The basic composition of Para- Virtualization is same as Full Virtualization, Bare-Metal /Hypervisor, but in the aspect of guest operating system, kernel of the guest operating system is partially applied for smooth communication with VMM. This method partially permits directly physical hardware access for some virtualization hardware resources according to the need. In Host Para-Virtualization, VMM is installed on the host operating system to create a virtual machine, where the guest operating system recomposes hardware perceived by the host operating system as virtual hardware. Among hardware level virtualization techniques, it has many limitations in performance and capacity of resource management as it is run on the environment where the host operating system is installed, but it is easy for general people to use. The products of Microsoft's Virtual Server and Virtual PC, VMware Server, VMware Workstation, and VMware Player adopt this technology[5]. |
| NEW IT DEFINITION |
| In this study, Green IT, Clean IT, Open IT, and Global IT are defined as new IT paradigms based on BCN and virtualization technology[4]. |
| 1) Green IT |
| Until now, IT industry has grown with the two major forces of software and hardware, and diversified services using information and communication technology are being provided for users. Innovative development of such information and communication technology has substituted humans and the number of users is increasing in geometric progression. Considering that carbon dioxide emission per personal computer(PC) amounts to 1 ton in a year, the level of emission is really serious. Also, with emergence of high-speed Internet and newest smart IT devices, consumers regard them as old models just 2~3 years after purchase and begin to change them, and the reuse rate of consumers who are to use the used products is very low, resulting in the sharply increased amount of the waste of IT devices. As IT products and related facilities have been pointed out as one of the major causes for environmental pollution such as global warming, an environment-friendly technology, Green IT, which is intended to induce the curtailment of energy and resource consumption to prevent it, for example, destroying metal materials harmful to the human body like lead, or waste recycling, is being handled as a very critical issue in international politics and business areas. |
| 2) Clean IT |
| The largest market in IT is online market, and the age and subjects are various, ranging from preschool children to adults. However, online has raised quality problems such as troubling in teacher-centered continuous management and customized learning by learner level, because it just has focused on the use of learner-centered simple online contents technology. For example, seen from common problems and difficulties in existing online systems centered on computer environment by user, educatees suffer very complex procedure such as installing a program in their computer to receive an education or adjusting the environment, and sometimes, they have to install an undesired program vulnerable to security. In addition, a desired application program may not be installed according to system specification, and they cannot install necessary software for receiving education due to its high price. Besides, exposure to dangerous environment such as virus, spyware, and hacking is a factor to interfere with PC uses during education. Settlement of such existing online problems using EaaS cloud technology is defined as Clean IT. Although cloud technology arouses a great issue and is being applied to various fields, there are few cases in the field of education and the availability is low, yet. |
| 3) Open IT |
| With technological advances, software is being rapidly developed. The specification of a PC being currently used becomes not enough to execute the newest software and it is handled as a scrap metal in an instant. This leads to an unintended polarization. Many people go through a financial difficulty in purchasing expensive PCs, making them fail to follow the latest trend. More troubling is that students cannot receive proper education due to the PC environment. To settle these problems, an environment like a high specification PC is provided in a low specification PC through EaaS system, and newest software is remotely offered, enabling everyone to be given an equal opportunity of education. That is, an IT environment where children are not discriminated against education is defined as Open IT(Social IT). |
| 4)Global IT |
| The world has very unequal structure. Good food is thrown away in some places, while children starve to death in other places. Like this, double-facedness is shown in the world. Education is not that much different from food. While there is difficulty in moving food and it is impossible to reuse due to difficulty in storage, IT service can be provided to every part of the earth. In this study, the extended version of Open IT, Global IT, is suggested, which is aimed at supporting online education for countries having poor education environment such as Southeast Asia or Africa by using the Broadband Convergence Network(BCN) of the National Information Society Agency(NIA), and solving the educational imbalance using IT technology. |
EAAS SYSTEM DESIGN
|
| This section describes the details and base technology of EaaS System. EaaS System is set by installing VM(here, VMware is used) in the existing cloud server and constructing EaaS server at the previous step of the cloud server for certification control. Four manager classes play a key role in the implemented certification system: Agent Manager manages the information of cloud servers, Session Manager manages the information of clients connected to the current cloud server and notifies Time Manager of this, Time Manager manages time required for the client to use that is, plays a role of scheduling, and Software Manager manages programs to run according to client's requirement. Through the said EaaS certification system, the user who is to use cloud service can be provided with the same quality of desired service in his/her PC terminal irrespective of his/her PC terminal system performance just by directly connecting to EaaS cloud system without setting any program or service except OS, Window |
| A. DETAILS AND BASE TECHNOLOGY |
| Displayed equations or formulas are centered and set on a separate line (with an extra line or halfline space above and below). Displayed expressions should be numbered for reference. The numbers should be consecutive within each section or within the contribution, with numbers enclosed in parentheses and set on the right margin. |
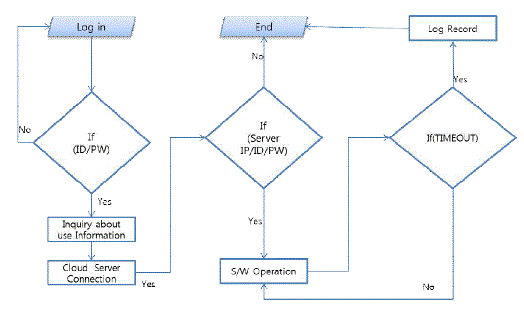
| 1) Algorithm diagram |
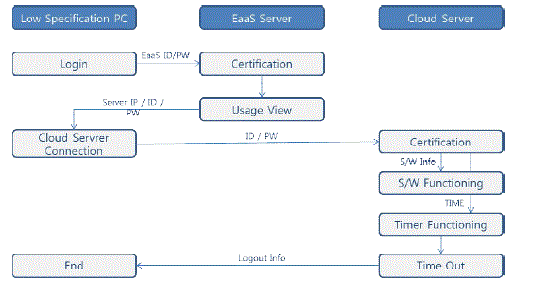
| As shown in 'FIg. 1', the client PC requests certification to the Eaas server through ID and password. The Eaas server approves user information requested by the client and provides IP, system ID and password of the Cloud Server to be used by the client. The client connects to the information of Cloud Server that is to be offered from the EaaS server, this is checked in the Cloud Server, and the set software is operated. As long as the client finishes the work within the given time, it is ordinarily terminated, but if the client exceeds the time given by the user, it is forcedly terminated by Session Manager and then recorded in the server.Displayed equations or formulas are centered and set on a separate line (with an extra line or half line space above and below). Displayed expressions should be numbered for reference. The numbers should be consecutive within each section or within the contribution, with numbers enclosed in parentheses and set on the right margin. |
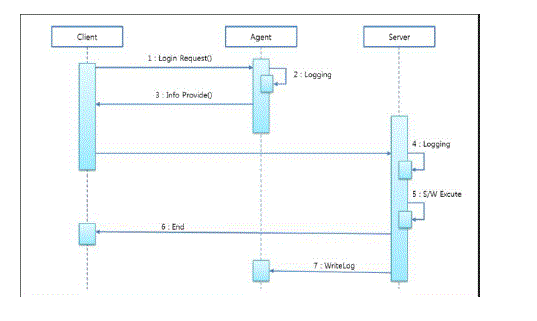
| 2) Sequence diagram - design UML |
| The aforesaid algorithm is successively displayed in a sequence diagram. The whole flow is same, it is divided into client, agent, and server according to each role, and the client connects to the server based on information given by the agent |
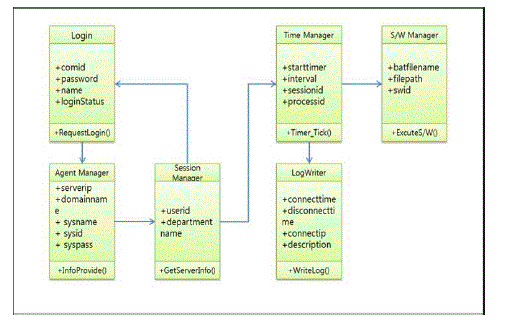
| 3) Major class module diagram |
| 'FIg. 3' shows a major class in system implementation. In the implemented system, 4 manager classes play key roles: Agent Manager manages the information of cloud servers and notifies the client of the information, Session Manager manages the information of clients being currently connected to the cloud server and notifies Time Manager of the information, Time Manager manages time required for the client to use that is, plays a role of scheduling, and Software Manager manages programs to run according to client's requirement. |
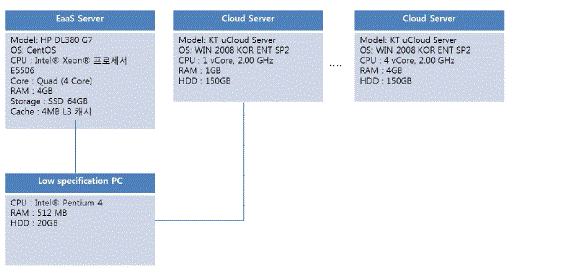
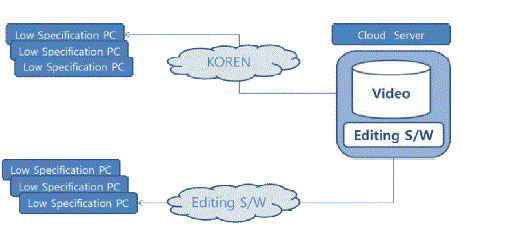
| 'FIg. 4' shows hardware diagram being utilized in the study. Each of EaaS server, Cloud server, hardware specification for low specification PC, and connection diagram is displayed. |
| FIg. 5' shows a flow of certification and software operation for each function of software modules. |
EAAS SYSTEM TEST
|
| To implement EaaS service and perform real test, in this study, EaaS system was constructed in the KT cloud server, 40 low specification PCs in Sunchon National University were connected to the EaaS system server using existing Internet, and video play and editing program operation was tested in the cloud server. At this test, although low specification PCs were used, the system could be used at rapid rate without difficulty in use due to any system load or problem in high specification program use. To construct and test the EaaS cloud system, the Sunchon National University network was interlocked with KOREN, the EaaS server was constructed for EaaS user, serial number, software and user schedule, the EaaS cloud server was set in the KT ucloud server to which EaaS users were to connect, and the network for KOREN connection to a low specification PC for EaaS users was set.In this study, an EaaS service model was tested using the KOREN network of NIA(National Information Society Agency) for implementation of BCN-based test. |
| A. KOREN INTERLOCK |
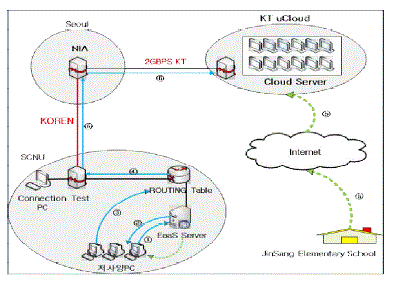
| Network construction was conducted at from Information & Computing Center to 404-ho Computer Room, No.3 Building of College of Engineering, Sunchon National University, using optical network equipment leased from the National Information Society Agency(NIA) NOC. The left figure below shows network composition with KOREN, Sunchon National University, and KT uCloud interlocked, while the right figure shows optical network equipment leased from NIA. Log in on http://cactic2.koren.kr, click KOREN → 4.Member → 4.Gwangju in the left menu, and then the KOREN use network traffic of Sunchon National University is divided into input and output, where average value and maximum value can be viewed in a graphic. Also, data can be saved in form of a CSV file and exactly analyzed. |
| B. SETTING FOR EAAS SYSTEM ESTABLISHING |
| 1) PC setting for EaaS user |
| For EaaS users to connect to the cloud server, network environment was set in a low specification PC. Specification and network setting of a low specification PC are as follows: IP address capable of KOREN connection that was assigned to Sunchon National University ranges from 203.255.253.162 to 190, and of these, 162 was allotted to optical equipment. There were 40 PCs to be used for test but only 27 IP addresses were available, so a router was used to connect the computer where an official KOREN IP address was not allotted to KOREN. The cloud for test was tested using KT U-Cloud service. As shown in 'FIg. 6', each EaaS cloud service was tested using a test scenario in existing Internet common network and KOREN network, and its performance and network traffic were compared, analyzed, and monitored.? Cloud-based large capacity multimedia contents play and traffic analysis in KOREN network. ? Cloud-based large capacity multimedia contents editing software operation traffic analysis in KOREAN network.IP newly given by NOC is assigned to a PC at the Computer Room that is connected to KOREN network, and 2 IPs are basically set in the PC including existing Internet common network IP. Accordingly, same conditions are provided in test environment, enabling accurate comparative analysis. |
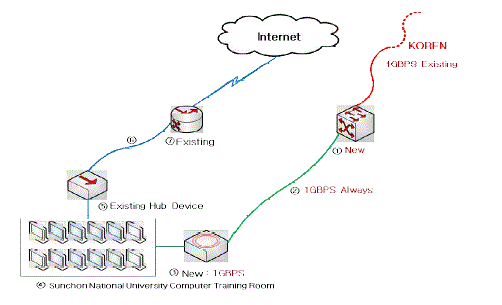
| 'FIg. 7' shows real KOREN network speed and diagram of lining which was requested by Sunchon National University to NIA. |
| 'FIg. 8' shows a diagram of test environment where each traffic of KOREN network and Internet common network is monitored in testing cloud-based EaaS system performance |
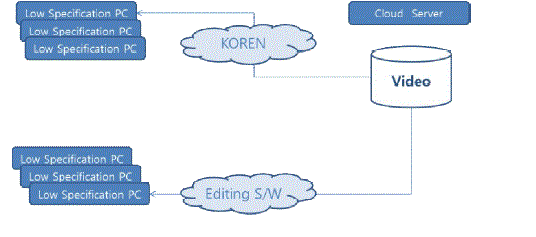
| 'FIg. 9' shows a diagram of test environment which is intended to monitor and analyze traffic when cloud-based EaaS system is utilized by each user using video editing tools. |
| C. TEST RESULTS |
| 1) Results of first test |
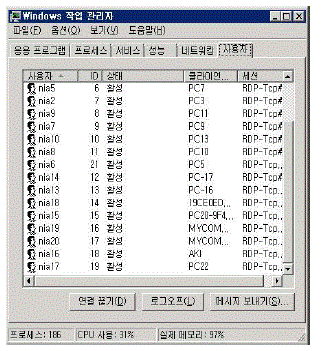
| 40 low specification PCs were connected to cloud server A at 404-ho, No.3 Building of College of Engineering, Sunchon National University at 19:00 ~ 21:00 on December 27, 2011, and MS Office test, video play and editing were tested. The figure below shows the information of users whose low specification PC is remotely connected to the cloud server by means of RDP(Remote Desktop Protocol). The users whose prefix of their name is NIA are EaaS users connected in a low specification PC. Those whose session is active are connected for use, while those whose prefix of their session is RDP- are connected to a remote desktop. |
| When 40 low specification PCs were connected to cloud server A and MS's Office program was used, the average CPU use rate of cloud server A was 20%, and 970MB out of a total of 1GB of actual memory was used on an average. Also, network use bandwidth measured in cloud server A was 7.6MB corresponding to 0.38% of a total of 2Gbps. |
| 2) Results of second test |
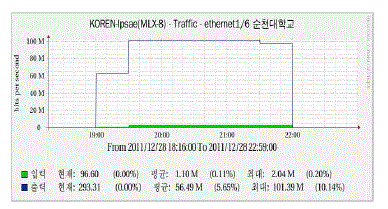
| 40 low specification PCs were connected to cloud server B at 404-ho, No.3 Building of College of Engineering, Sunchon National University at 19:00 ~ 22:00 on December 28, 2011, and video play and editing test was conducted. When 40 low specification PCs were connected to cloud server B and video play and editing test was conducted, the average CPU use rate of cloud server B was 51%, and 1.6GB was used on an average out of a total of 16GB actual memory. Also, network use bandwidth measured in cloud server B was 99.94Mbps corresponding to 4.88% of 2Gbps in total.The figure below shows that the amount used of Sunchon National University on the CACTIC2 site, and 99Mbps traffic occurred at 19:30 ~ 22:00 when a video play and editing program was used, and maximum 101.39Mbps traffic occurred. |
| D. KOREN TEST AND ANALYSIS |
| In this study, KOREN-based EaaS cloud system was tested into 3 steps: In step 1, to see if the EaaS cloud system developed in this study normally runs, 40 low specification PCs were connected to VM self-constructed in Sunchon National University, and no abnormal condition was found in video play and editing program operation on VM. In step 2, EaaS cloud was constructed in the KT cloud server, 40 low specification PCs within Sunchon National University were connected to the EaaS cloud server using the existing Internet network, and the MS' Office Program was operated well on the cloud server without trouble. Also, no abnormal condition was found when the video play and editing program was executed. In step 3, in the same manner as step 2, the EaaS cloud was constructed in the KT cloud server, 40 low specification PCs within Sunchon National University were connected to the EaaS cloud server using the newly constructed KOREN, and the MS' Office Program was operated well on the cloud server without trouble. On an average, 100Mbps traffic was continuously generated by operating the video play and editing program but the EaaS cloud system was executed without trouble. However, in 100Mbps bandwidth, 45 or more PCs were simultaneously connected, so it was impossible to operate the video play and editing program. |
| As a result of test by steps, once only 100 Mbps bandwidth was offered in network without limitations, there was no trouble in connecting 40 low specification PCs to the cloud server and operating the video play and editing program. Like this, the use of clean KOREN network can solve problems incurred in common network by steps in a short time, and therefore, it can play a role of excellent Testbed. |
CONCLUSIONS AND FUTURE WORK
|
| The EaaS service system developed in this study has great significance in that it actually implemented scalability, flexibility, and security that are sought for by cloud, and consequently satisfies Green IT, Clean IT, Open IT, and Global IT. In this study, a new cloud service model, which has not been studied previously, was developed, and utilization of this service is expected to contribute to settlement of global environmental problems by decreasing waste and implementing Green IT through lower computer system specification. Also, the most frequent problems incurred whenever general users use PC are malignant code and virus, and this system can radically block these problems and implement Clean IT. In addition, once resources acquired from software donation or system donation apply to this system, they are available with maximum efficiency, and ultimately, Social IT enabling social contribution that is, Open IT can be implemented. If this service is provided through KOREN high speed future Internet network, it will be expanded into global service, and Global IT will be pursued, where equal educational benefits can be received in the whole world. The EaaS cloud service model started from an idea of settling problems of government-initiated smart education and optimizing for smart education. Existing SaaS-based cloud service caused problems in educational uses, however, this study is very meaningful in that it was an attempt to solve such problems and at the same time, provide service from the viewpoint of general users, contrary to existing cloud services limited to a corporate level of business service. This study is also meaningful in that a service model to implement scalability, flexibility, and security that were pursued by cloud service was developed, and four values intended in this study, Green IT, Clean IT, Open IT, and Global IT, were actually implemented. |
ACKNOWLEDGMENT
|
| This paper was supported by(inpart) Sunchon National University Research Fund in 2013. |
Tables at a glance
|
 |
| Table 1 |
|
Figures at a glance
|
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
|
 |
 |
 |
 |
| Figure 5 |
Figure 6 |
Figure 7 |
Figure 8 |
|
 |
 |
 |
| Figure 9 |
Figure 10 |
Figure 11 |
|
References
|
- Hyoungyong O., Byoung-Won M., Yong-Sun O: User Customized Web Interface Design Optimized for SaaS-based Digital Library Systemfocusing on the LinkSaaS Website-., The Journal of the Korea Contents Association, Vol.11, No.5, pp.148-156,2011.
- Dong-ho K., Jung-hoon L., Yang-pyo P.: A Study of Factors Affection the Adoption of Cloud Computing, The Journal of Society for e-Business Stidies, Vol.17, No.1, pp.111-136,2012.
- Gartner: Gartner Identifies the Top 10 Strategic Technologies for 2009,2008.
- NiraiJuneja., “A Walk in the Clouds, webscale solution", Retrieved from http://www.slideshare.net/njuneja.
- Sung-Jae J., Yu-mi B., Woo-Young S., A Study on the Secure Enhanced Efficient Web System based on Linux Virtualization, Journal of Security Engineering, Vol. 7, No. 4, pp.335-350,2010.
- Gillett, F., Future View: The New Tech Ecosystems of Cloud, Cloud Services, and Cloud Computing, Future,2008.
- Gartner Group., Assessing the Security Risks of Cloud Computing, http://www.infoworld.com/article/08/07/02/gartner_seven_cloudcomput in g_security_ risks _1 .html,2008.
- Hyun-Soo A., IT environmental changes and challenges caused by Apperance of SaaS, National Information Society Agency,2007.
- Foster, I., et al., Cloud Computing and Grid Computing Environments Workshop, pp. 1-10,2009.
- Mell, P., Grance, T., TheNIST Definition of Cloud Computing, National Institute of Standards and Technology, 2009.
- Sheth A., Gomadam K., and Lathem J.,“SA-REST: Semantically interoperable and easier-to-use services and mashups”, IEEE Internet Computing,Vol.11, No.6, pp.91-94,2007.
- Battle R. and Benson E.,“Bridging the semantic web and Web 2.0 with representational state transfer (REST)”, Journal of Web Semantics,No.6,pp.61-69, 2008.
- Morbidoni C., Phuoc D., Polleres A., Samwald M., and TummarelloG.,“Previewing semantic web pipes”, Proceedings of the 5th European Semantic Web Conference on the Semantic web, Research and Applications, pp.843-848,2008.
- Riemer J., Martin-Recuerda F., Ding Y., et al.,“Triple space computing: Adding semantics to space-based computing”, The Semantic Web – ASWC 2006, Lecture Notes in Computer Science, 4185, pp.300-306,2006.
- Hess A. and KushmerickN.,“Learning to attach metadata to web services”,Proceedings of the 2nd International Semantic Web Conference pp.258-273,2003.
- Dong X., Halevy A., Madhavan J., Nemes E., and Zhang J.,“Similarity search for web services”, Proceedings of the 30th VLDB conference, pp.372-383,2004.
- Sabou M., Wroe C., Goble C., and StuckenschmidtH.,“Learning domain ontologies for semantic web service descriptions”, Journal of Web Semantics,Vol.3,No.4, pp.340-465,2005.
- Guo H., Ivan A., Akkiraju R., and Goodwin R.,“Learning ontologies to improve the quality of automatic web service matching”,Proceedings of IEEE International Conference on Web Services, pp.118-125,2007.
|