Recent advances in portable computing and wireless technologies are opening up exciting possibilities for the future of wireless mobile networking. A Mobile Ad-hoc NETwork (MANET) consists of mobile platforms which are free to move arbitrarily. This is in contrast with the topology of the existing Internet, where the router topology is essentially static. In MANET, the nodes are mobile and inter-node connectivity may change frequently during normal operation. In this work, we present an analysis of Ad-Hoc On-Demand Distance vector Routing (AODV) protocol and evaluate the performance of the protocol. AODV is a reactive protocol as it reacts to change and maintain the active routes in the caches or tables for a pre-specified expiration time. Distance vector means a set of distant nodes, which defines the path to destination. AODV can be considered as a descendent of DSR and DSDV algorithms. It uses the same route discovery mechanism used by DSR. AODV attempts to improve on DSR by maintaining routing tables at the nodes, so that data packets do not have to contain routes. Numerous simulations of routing protocols have been made using different simulators. Simulators though cannot take into account of all the factors that can come up in real life and performance and connectivity of mobile Ad-hoc network depend and are limited also by such factors. In our project work, we have analyzed the behavior of AODV protocol with various parameters like pdf, end-to-end delay, throughput, normalized routing load (NRL).
INTRODUCTION |
| In Ad-hoc networks all nodes are mobile and can be connected dynamically in an arbitrary manner. As the range of each
host’s wireless transmission is limited, so to communicate with hosts outside its transmission range, a host needs to enlist
the aid of its nearby hosts in forwarding packets to the destination. So all nodes of these networks behave as routers and
take part in discovery and maintenance of routes to other nodes in the network. Ad hoc Networks are very useful in
emergency search-and-rescue operations, meetings or conventions in which persons wish to quickly share information, and
data acquisition operations in inhospitable terrain. |
| Numerous simulations of routing protocols have been made using different simulators, such as ns2. Simulators though
cannot take into account of all the factors that can come up in real life and performance and connectivity of mobile Ad-hoc
network depend and are limited also by such factors. Routing algorithms are being developed for commercial purposes and
thus will be used outside of laboratories and simulators. As routing protocol AODV has been chosen, since in our opinion
the ideas behind it are very promising. |
RELATED WORK |
| In [1] the ratio of the data packets delivered to the destinations to those generated by the CBR sources is known as packet
delivery fraction. Here five routing nodes are taken into consideration and different values of qlength are taken. With the
increase of the Qlength it is seen that the CBR ratio is also increasing. And therefore this will consequently have an effect
on the packet delivery fraction. In [2] End-to-end delay refers to the time taken for a packet to be transmitted across a
network from source to destination. Taking into consideration of five routing nodes the qlength is changed and the different
value of the end-to-end delivery is obtained. With the change in the qlength the delay also varies. In [3] the relative
throughput is the ratio of the number of packets (or bits) delivered to the different destinations to the number of packets (or
bits) that are attempted to be sent. With the change in the qlength the average throughput is also affected. In [4] the number
of routing packets transmitted per data packet delivered at the destination. Each hop -wise transmission of a routing packet
is counted as one transmission. The above graph shows the variation in normalized routing load with respect to different
values of qlength. |
MANET |
| Mobile Ad-hoc Network (MANET) is a recent developed part of wireless communication. The difference to traditional
wireless networks is that there is no need for established infrastructure. Since there is no such infrastructure and therefore
no preinstalled routers which can, for example, forward packets from one host to another, this task has to be taken over by
participants, also called mobile nodes, of the network. Each of those nodes take equal roles, what means that all of them can
operate as a host and as a router. Next to the problems of traditional wireless networks such as security, power control,
transmission quality and bandwidth optimization, new problems come up in Ad-hoc networks. We have in mind problems
like maintenance and discovery of routes and topological changes of the network. To solve such problems is the challenge
of Ad-hoc Networking. |
Characteristics |
| • Nodes – All the nodes in a mobile Ad-hoc network, regardless of their position, can communicate with other
nodes with the same priority. Since there is no infrastructure there is a need, in order to let distant nodes
communicate with each other, of nodes in the network who take over the position of a router. |
| • Loss rate and delay – The communication medium of wireless networks, electromagnetic waves, encounter
during their propagation many interference coming from objects which are in the propagation way of the waves or
from other transmitting wireless devices. Therefore we have in MANETs a higher loss rate and delay than in wired
networks. |
| • Topology – Since the nodes in an Ad-hoc network are mobile the chance of frequent changes in the topology of
the network is high. Algorithms for Ad-hoc networks have to take these topological changes into account. |
| • Security – Because the computer communicates over the air, every node, equipped with the necessary utilities,
inside the transmitting area of a sending node, can receive the sent messages. For this reason wireless network are
less secure than wired ones. |
| • Capacity – At the moment is the amount of data which a link of a wireless network is able to transmit per unit of
time smaller than the one of a wired network. |
AD-HOC ON-DEMAND VECTOR (AODV) |
| AODV stands for Ad-hoc On-Demand Distance Vector and is, as the name already says, a reactive protocol, even though it
still uses characteristics of a proactive protocol. AODV takes the interesting parts of DSR and DSDV, in the sense that it uses the concept of 8 route discovery and route maintenance of DSR and the concept of sequence numbers and sending of
periodic hello messages from DSDV. Routes in AODV are discovered and established and maintained only when and as
long as needed. To ensure loop freedom sequence numbers, which are created and updated by each node itself, are used.
AODV takes advantage of route tables. In these it stores routing information as destination and next hop addresses as well
as the sequence number of a destination. Next to that a node also keeps a list of the precursor nodes, which route through it,
to make route maintenance easier after link breakage.uses the concept of 8 route discovery and route maintenance of DSR and the concept of sequence numbers and sending of
periodic hello messages from DSDV. Routes in AODV are discovered and established and maintained only when and as
long as needed. To ensure loop freedom sequence numbers, which are created and updated by each node itself, are used.
AODV takes advantage of route tables. In these it stores routing information as destination and next hop addresses as well
as the sequence number of a destination. Next to that a node also keeps a list of the precursor nodes, which route through it,
to make route maintenance easier after link breakage. |
ROUTE DISCOVERY |
| When a node wants to communicate with another node it first checks its own routing table if an entry for this destination
node exists. If this is not the case, the source node has to initialize a route discovery. This is done by creating a RREQ
message, including the hop count to destination, the IP address of the source and the destination, the sequence numbers of
both of them, as well as the broadcast ID of the RREQ. This ID and the IP address of the source node together form a
unique identifier of the RREQ. When the RREQ is created the source node broadcasts it and sets a timer to wait for reply.
All nodes which receive the RREQ first check by comparing the identifier of the message with identifiers of messages
already received. If it is not the first time the node sees the message, it discards silently the message. If this is not the case
the node processes the RREQ by updating its routing table with the reverse route. If a node is the destination node or has
already an active route to the destination in its routing table with sequence number of the destination host which is higher
than the one in the RREQ, it creates a RREP message and unicasts it to the source node. This can be done by analyzing the
reverse route for the next hop. Otherwise it increments the RREQ’s hop count and then broadcasts the message to its
neighbors. When the source node receives no RREP as a response on its RREQ a new request is initialized with a higher
TTL and wait value and a new ID |
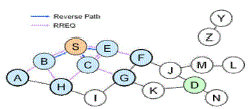
| Suppose S would like to communicate with D Figure 1, the node broadcasts a RREQ to find a route to the destination. S
generates a Route Request with destination address, Sequence number and Broadcast ID and sent it to his neighbour nodes.
Each node receiving the route request sends a route back (Forward Path) to the node. |
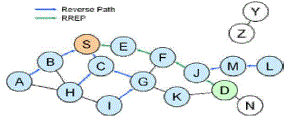
| The route is made available by unicasting a RREP back to D and is written in the routing table from S . After receiving the
route reply every node has to update its routing table if the sequence number is more recent. |
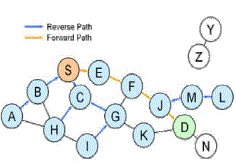
| Now node S can communicate with node D |
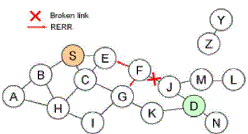
| When a link break in an active route is detected, the broken link is invalid and a RERR message is sent to other nodes,
Figure 5. If the nodes have a route in their routing table with this link, the route will be erased. Node S sends once again a
route request to his neighbour nodes. Or a node on the way to the destination can try to find a route to D. That mechanism
is called: Local Route Repair. |
ROUTE MAINTENANCE |
| When a route has been established, it is being maintained by the source node as long as the route is needed. Movements of
nodes effect only the routes passing through this specific node and thus do not have global effects. If the source node moves
while having an active session, and loses connectivity with the next hop of the route, it can rebroadcast an RREQ. If though
an intermediate station loses connectivity with its next hop it initiates an Route Error (RERR) message and broadcasts it to
its precursor nodes and marks the entry of the destination in the route table as invalid, by setting the distance to infinity.
The entry will only be discarded after a certain amount of time, since routing information may still be used. |
| When the RERR message is received by a neighbor it also marks its route table entry for the destination as invalid and
sends again RERR messages to its precursors. The node N4 moves to N4’ and so node N3 cannot communicate with it
anymore, connectivity is lost. N3 creates a RERR message to N2, there the route is marked invalid and unicasts the
message to N1. The message is unicast since we have only route passing through each node. N1 does the same thing and
unicasts the message to the source node. When the RERR is received at the source node and it still needs the route to the
destination it reinitiates a route discovery. Figure 4.3.1 II shows the new route from the source to the destination through node N5. Also if a node receives a data packet for a node which it does not have an active route to, it creates a RERR
message and broadcasts it as described above. |
QOS |
| Quality of service (QoS) is the overall performance of computer network, particularly the performance seen by the users
of the network. To quantitatively measure quality of service, several related aspects of the network service are often
considered, such as error rates, bandwidth, throughput, transmission delay, availability, jitter, etc. |
| Quality of service is particularly important for the transport of traffic with special requirements. In particular, much
technology has been developed to allow computer networks to become as useful as telephone networks for audio
conversations, as well as supporting new applications with even stricter service demands. |
Parameters |
| End-to-End Delay |
| End-to-end delay refers to the time taken for a packet to be transmitted across a network from source to destination. |
| dend-end= N[ dtrans+dprop+dproc] |
| where, |
| dend-end=end-to-end delay |
| dtrans=transmission delay |
| dprop= propagation delay |
| dproc= processing delay |
| dqueue= Queuing delay |
| N= number of links (Number of routers + 1) |
| Each router will have its own dtrans, dprop, dproc hence this formula gives a rough estimate. |
Packet Delivery Fraction |
| The ratio of the data packets delivered to the destinations to those generated by the CBR sources is known as packet
delivery fraction. |
| Constant bitrate (CBR) is a term used in telecommunications, relating to the quality of service, Compared with variable
bitrate. . CBR is useful for streaming multimedia content on limited capacity channels since it is the maximum bit rate that
matters, not the average, so CBR would be used to take advantage of all of the capacity. CBR would not be the optimal
choice for storage as it would not allocate enough data for complex sections (resulting in degraded quality) while wasting
data on simple sections. |
Throughput |
| The relative throughput is the ratio of the number of packets (or bits) delivered to the different destinations to the number
of packets (or bits) that are attempted to be sent. While throughput first increases, then decreases with offered load, relative throughput pretty much decreases monotonically. From this ratio, one can determine the range of acceptable loads and
decide how to avoid slipping into overload. |
Normalized Routing Load |
| The number of routing packets transmitted per data packet delivered at the destination. Each hop -wise transmission of a
routing packet is counted as one transmission. The first two metrics are the most important for best-effort traffic.
The routing load metric evaluates the efficiency of the routing protocol. |
Simulator |
| Network Simulator (Version2) is used to perform extensive simulations to evaluate the performance of the considered
routing protocols in different scenarios. It is simply an event driven simulation tool that has proved useful in studying the
dynamic nature of communication networks. Simulation of wired as well as wireless network functions and protocols (e.g.,
routing algorithms, TCP, UDP) can be done using NS2. In general, NS2 provides users with a way of specifying such
network protocols and simulating their corresponding behaviors. |
RESULTS |
Analysis of performance matrices |
| 1. Packet Delivery Fraction |
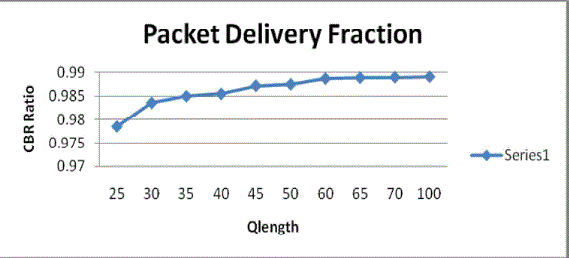 |
| The ratio of the data packets delivered to the destinations to those generated by the CBR sources is known as packet
delivery fraction. Here five routing nodes are taken into consideration and different values of qlength is taken. With the
increase of the Qlength it is seen that the CBR ratio is also increasing. And therefore this will consequently have an effect
on the packet delivery fraction. |
| 2. Average End to End Delay |
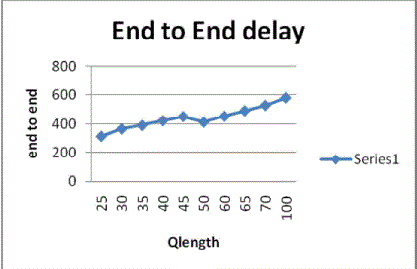 |
| End-to-end delay refers to the time taken for a packet to be transmitted across a network from source to destination.
Taking into consideration of five routing nodes the qlength is changed and the different values of the end-to-end delivery is
obtained. With the change in the qlength the delay also varies. |
3. Average Throughput |
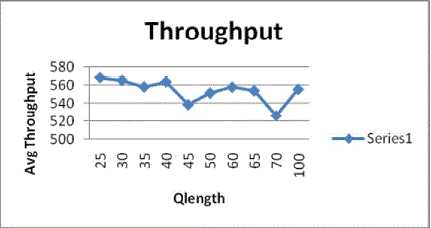 |
| The relative throughput is the ratio of the number of packets (or bits) delivered to the different destinations to the number
of packets (or bits) that are attempted to be sent. With the change in the qlength the average throughput is also affected. |
4. Normalized Routing Load |
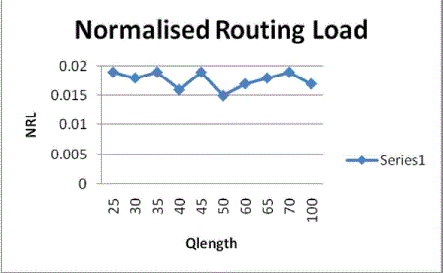 |
| The number of routing packets transmitted per data packet delivered at the destination. Each hop -wise transmission of a
routing packet is counted as one transmission. The above graph shows the variation in normalized routing load with respect
to different values of qlength. |
CONCLUSION |
| In this project, we have studied about MANET, different protocols, QOS and their parameter and the analysis of their
parameters. |
| In this project, the performance evaluation of the AODV routing protocol in Mobile Ad- Hoc Network, an important kind
of evaluation was done since reality is reflected. This report presents the results we obtained from our experiments to
evaluate AODV, where we set our interest on Packet Delivery Fraction, End-to-End delay, Communication Throughput and
Normalized Routing Load. |
| We have analyzed ten implementations using the same protocol and hence we studied the performance of AODV protocol. |
Figures at a glance |
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
|
| |
References |
- Charles E. Perkins, “Mobile Ad-hoc Networks,” Addison-Wesley, 2000.
- J. Jubin and J. Tornow, “The DARPA Packet Radio Network Protocols”, Proc. IEEE, vol.75, no. 1, pp. 21-32.1987.
- C. E. Perkins and E. M. Royer, “Highly Dynamic Destination-Sequenced Distance- Vector Routing(DSDV) for Mobile Computer,” Proceedings of the 1994 ACM Special Interest Group on Data Communication, London, UK,. pp. 234-244. Sep. 1994.
- C. C. Chiang, “Routing in Clustered Multihop, Mobile Wireless Networks with Fading Channel,” Proc. IEEE SICON ’97, pp.197-211. Apr.1997
- C. E. Perkins, E. M. Royer, S. R. Das, 1999, “Ad Hoc On-demand Distance Vector (AODV) Routing,”, Mobile Computing Systems and Applications, Proceedings. WMCSA’99. Second IEEE Workshop on 25-26 Feb. PP: 90-100
- D. B. Johnson, D. A. Maltz, Y-C.Hu, 2001, “The Dynamic Source Routing (DSR) Protocol for Mobile Ad Hoc Networks,”, Internet Draft, IETF MANET working group.
- Z. Hass and M. Pearlman, “The Performance of Query Control Schemes for the Zone Routing Protocol,” ACM SIGCOMM, , pp. 167-177. Aug. 1998
- J. B. Postel, “Transmission Control Protocol”,. IETF RFC793, Sep 1981.
- A. Al. Hanbali, E. Altman, P. Nain,” A survey of TCP over and hoc networks” Communication Surveys & Tutorials, IEEE, 2005
- K. Chandran, S. Raghunathan, S. Venkatesan and R. Prakas,“ A feedback based scheme for improving TCP performance in Ad-hoc wireless networks”, Personal Communications, vol.8, pp.34-39, Feb. 2001.
- Dongkyun Kim, C.-k. Toh, Yanghee Choi, “TCP-BuS: improving TCP performance in wireless Ad Hoc networks”, IEEE International Conference on Communications, vol.3, pp.1707- 1713, June 2000.
- The Network Simulation ns-2, http://www.isi.edu/nsnam/ns/
- D. Kim, C. K. Toh and Hong-Jong Jeong, “An Early Retransmission Technique to Improve TCP Performance for Mobile Ad Hoc Networks”, IEEE International Conference on Communications, vol.04, pp.2695-2699, 2004
- D. Johnson, D. Maltz, and Y. Hu, “The Dynamic Source Routing Protocol (DSR) for Mobile Ad Hoc Networks for IPv4”, IETF Internet Draft. http://www.ietf.org/rfc/rfc4728.txt, February 2007.
- D. Johnson et al., Dynamic Source Routing for Mobile Ad Hoc Networks, IEFT MANET Draft, April 2003
- Charles E. Perkins, Destination- Sequence Distance- Vector Protocol, Ad Hoc Networking, ISBN 0-201-30976-9, pp. 53- 74
- C.-K. Toh, Associativity- Based Routing, IEEE Transactions on wireless communications, Vol. 1, No. 3, July 2002
|