Keywords
|
| MANET, DSR, DSDV, AODV, mobility models, NS2. |
I.INTRODUCTION
|
| Routing protocols are used in ad hoc network must automatically adjust to environment that can vary between the limit of high mobility with low bandwidth, and low mobility with high bandwidth. The performance of MANET is connected to the efficiency of these routing protocols in adapting to frequently changing network topology and link status. Routing is a fundamental engineering task. It consists of finding a path from source to destination host. Complications in routing are become larger if network is large because of many intermediate destinations, a packet might transverse before reaching to its destination [1]. To decreases complexity the network in divided into smaller province. Considering each domain individually makes the network more manageable. In ad hoc network, there are various techniques for tracking changes in the network topology and re-discovering new routes when older routes are break. Since ad hoc networks have no infrastructure these operations should be performed with collective cooperation of all nodes. |
II. AN OVERVIEW OF PROTOCOLS
|
| Routing protocol in MANET, are divided into three basic classes: Table driven (Proactive) routing protocols, on demand (Reactive) routing protocols and Hybrid routing protocols [2]. The proactive routing (e.g. AODV) protocols are table-driven (e.g. DSDV). They usually use link-state algorithms flooding the information of link. Link state algorithms maintain a full or partial copy of the network topology and costs for all known links. The reactive routing protocols (e.g. DSR) create and maintain routes only if these are required, on demand. They usually use distance-vector routing algorithms that retain only information about the next hops to adjacent neighbours and costs for path to all known targets. Thus, link-state routing algorithms are more genuine, less bandwidth-intensive, but also more complex and compute-intensive and memory-intensive. The hybrid routing protocols try to combine proactive and reactive approaches based on certain conditions. ZRP for example defines a zone around nodes. Zone proactive routing is used within zone; outside of it nodes use reactive routing [3]. The following subsections briefly describe these three ad hoc routing protocols which are considered in this paper. The first one (AODV) is fully on-demand based, next is destination sequence distance vector (DSDV) is based on table driven. The last one is (DSR), has adopted some of the characteristics of the both table driven and on-demand categories. |
| A) DSDV is the table driven routing protocol that is enhanced version of distributed Bellman-ford algorithm. DSDV uses bidirectional links. It works on hope by hope basis. In this, each node maintain a list of all destination and number of hopes of each and every destination [4]. Every entry is marked with a sequence number to provide loop freedom. To keep table up to date they are exchanged between neighbouring nodes at regular intervals or when a significant topology changes are observed. In practice updates are sent in every few seconds. The route labelled with highest sequence number is always used. To minimize the traffic generated, there are two types of packets in system. One is “full dump” and another is “incremental”. First packet carries all the information about a variance. However, at the time of particular movement, second type is used, which will carry the changes only, thereby increasing the overall efficiency of the system. The data broadcasted by each and every mobile node will contain the new sequence number, number of hopes to reach the destination, destination’s address. |
| B) AODV is a reactive routing protocol designed for ad hoc networks up to thousands of nodes. It uses route discovery process to cope with routes on-demand basis. In this, nodes maintain traditional routing tables specifying the next hop to take to reach the target. If there is no information in the routing table of the source then a route request is broadcasted. A node that receives the route request and has an up-to-date path to the destination will return it to the source and all nodes on the return path will update their routing tables. If there is no valid path is present in an intermediary multiple paths to the destination, the one with the highest adequacy is chosen. For route maintains nodes periodically send 'hello' messages from an acquaintance nodes [5-6]. If a node fails to receive three consecutive 'hello' message from an acquaintance, it concludes that link to that specific node is down. A node that detects a broken link is sends a Route Error message to any upstream node. When a node receives a Route Error message it will initiate a new source discovery process. Link break detection can also be done by using second way, it is detected by a link signalling mechanism when the link is used. If a link break is detected, then the end nodes (source and destination) are informed and it is up to them to find a new path. |
| C) DSR is a fully reactive routing protocol. The major difference between DSR and other on demand routing protocols is that, beacon are less in DSR and hello packets are not required. It is a source routing protocol meaning that a packet carried in the network contains an ordered list of all nodes through which the packet must be routed. Nodes in a networks using DSR routing are required to maintain so called route Cache where a learned routes to any given node in the network exist [7]. DSR uses two basic mechanisms; one is Route Discovery and second is Route Maintenance. Consider a source node that does not have a route to the destination. When it has a data packet to be sent to that destination, then it initiates a Route Request packet. Route Request is flooded through the network. Every node upon receiving a Route Request broadcasts the packet to its acquaintances if it has not forwarded already or if the node is not the destination node. All Route Requests carries a sequence number generated by the source node and the path it as traversed. A node, upon receiving a Route Request packet, checks the sequence number on the packet before forwarding it. The packet is forwarded only if it is not a duplicate Route Request packet. Thus, all the nodes except the destination node, forwards a Route Request packet during the route construction phase. A destination node upon receiving the Route Request packet, replies to the source node through the reverse path the Route Request packet had transverse. |
III. MOBILITY MODELS
|
| In this paper, three mobility models are designed to take a wide range of mobility patterns for ad hoc networks applications. We choose three different classes based mobility models, including random, path based and group based mobility’s. |
| A) Random way point model is widely accepted mainly, because of its simplicity of implementation and analysis. Each node chooses random destination within the given simulated field and a speed between minimum and maximum bound. Then node moves to the destination, pauses are also there for a fixed period of time, and after that node chooses new destination [8]. However, it is supposed that, this model is insufficient to capture spatial dependence of movements of nodes, temporal dependence of movements of nodes over a time and existence of barriers constraining mobility. |
| B) Column Mobility Model is useful for scanning and searching purposes [9]. In this model a set of MNs that moves around a given line or column, which is moving in a forward direction or in backward direction. A small modification of the Column Mobility Model allows the individual MNs to follow one another. For the implementation of this model, an initial reference grid is defined [10]. Each MN is placed in relation to its reference point in the reference grid; the MN is then allowed to move randomly around its reference point via an entity mobility model. The new reference point for a given node is defined as:- |
| New reference point = old reference point+ advanced vector |
| Old reference point is the previous reference point of mobile node and advance vector is a predefined offset that moves the reference grid. The predefined offset that moves the reference grid is calculated by using a random distance and random angel. In this mobility model, the MNs roam closely around their respective reference points. When the reference grid moves, the MNS follow the grid and then continue to roam around their respective points. |
| C) The Reference Point Group Mobility model represents the random motion of nodes in a group as well as the random motion of each individual MNs within the group [11]. Movements of group are based upon the path travelled by a logical centre of a group. The centre of the group is used to calculate group motion by using a group motion vector. The motion of the group canter is completely characterizes the movement of its corresponding MNS group, including their direction and speed. In this mobility model individual MNS randomly move about their own pre-defined reference points, whose movement depends on the movement of group. The individual reference points are moves from time’t’ to’t+1', and their locations are updated according to the group's logical centre. When the updated reference points are calculated, they are combined with the random motion vector, to represent the random motion of all MNs about its individual reference point. The Reference Point Mobility model was designed to illustrate scenarios such as an avalanche rescue. Throughout an avalanche recue, the responding team consisting of men and canine members work cooperatively. The men guides tend to set a general path for the monkeys to follow, however they usually know the approximate location of victims. The monkeys each create their own “random” paths around the general area selected by their men counterparts. |
IV.SIMULATION ENVIORNMENT
|
| In this work, we analyse the performance of Reactive and Proactive routing protocols within simulation time for different mobility (Random Waypoint Mobility model, Column Mobility model, Reference Point Group Mobility model) models. Simulation has been carried out by using Network Simulator (NS2). Constant Bit Rate (CBR) is used. Simulation environment area as 1000m x 1000m was selected with time 30 second for fixed maximum speed of 20m/s. |
| A) Simulation Parameters |
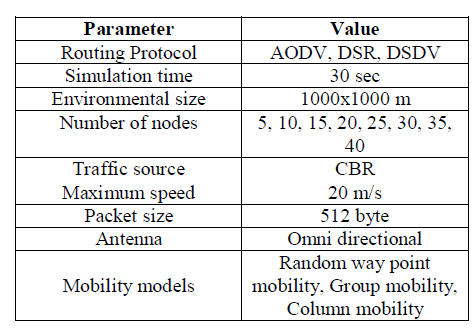 |
| B) Performance Metrics |
| For the simulation results, we have selected the following parameters as a metrics to evaluate the performance of the different protocols: |
| 1. Throughput: It is defined as the total number of packets received by the destination, or how much data packets correctly delivered to the destination. |
| 2. Packet delivery ratio: It is the ratio of the number of data packets delivered to destination. In other words, it depicts the level of delivered data to destination. |
| PDR = Σnumber of packet receive / Σnumber of packet sent |
| 3. End to end delay: It is the average amount of time taken by a packet to reach from source to destination. All possible delays are included due to retransmission delays, route discovery latency and transfer times. |
| Σ (arrive time-send time)/ Σnumber of connections |
| 4. Normalized routing load: is the fraction of all routing control packets sent by each node over the number of received data packets at the destination nodes. We can say that, it is the ratio among the total number of routing packets sent over the network to the total number of data packets received. |
V. RESULT AND DISCUSSION
|
| The simulation results are focused to analyse the performance of routing protocols based on throughput, end to end delay, normalized routing load and packet delivery ratio. The results are compared between AODV, DSDV and DSR protocols on the basis of three different mobility models. |
| A) Average Throughput |
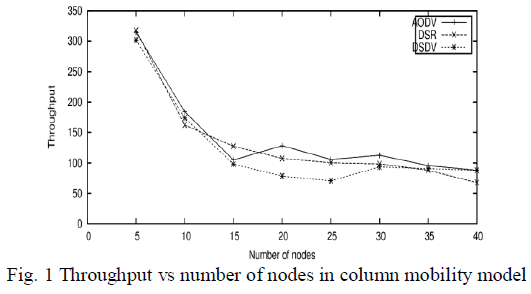
| Throughput indicate rate of communication per unit time. Throughput in this experiment evaluate for AODV, DSDV and DSR for all these three mobility models. Fig. 1 shows the throughput (bytes per simulation time 30 sec) versus increasing number of nodes of protocols by using column mobility of nodes in given environment. In this AODV perform better than other protocols, but in lesser number of nodes performance of all protocols is almost same. |
 |
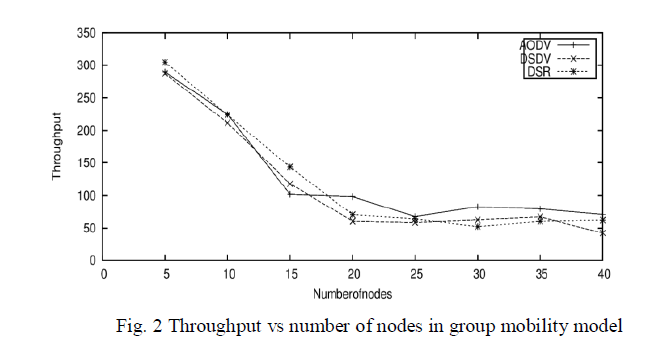
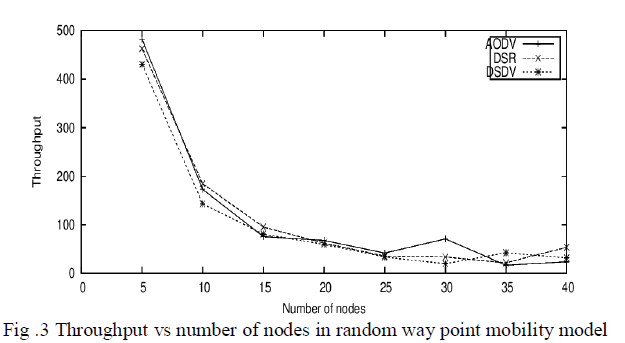
| Throughput of protocols with respect increasing nodes for group mobility model is shown in Fig. 2. It shows that throughput of AODV is good than DSR, and DSDV perform least. In Fig. 3, throughput by using random mobility model is much better than other two mobility models. In this case all three protocols perform better but AODV is much better. |
 |
 |
| B) Packet delivery ratio |
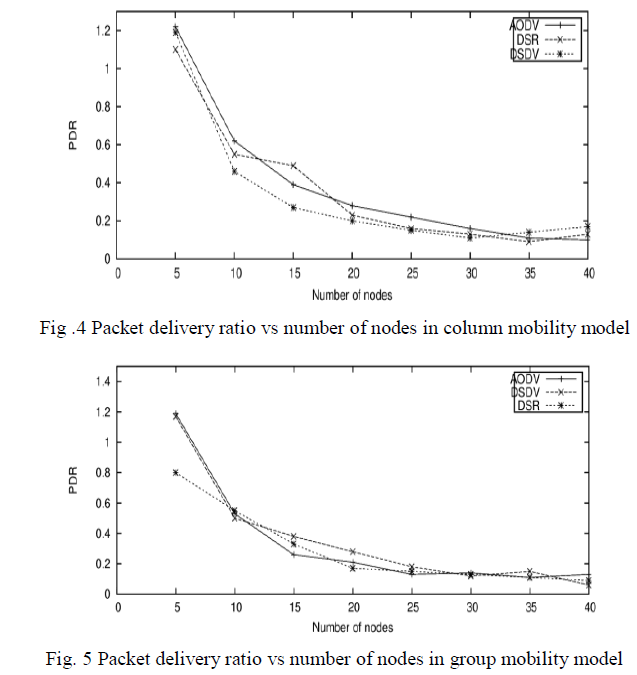
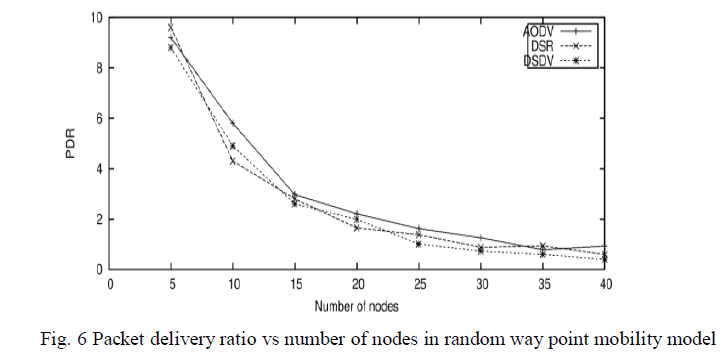
| It is the ratio of data packets delivered to the destination to those generated by the source. It is calculated by dividing the number of packet received by the destination through the number of packet originated by the source. The packet delivery ratio of AODV, DSDV and DSR versus increasing number of nodes, Fig. 4 shows the PDR by using column mobility model of nodes. PDR of AODV is good for lesser number of nodes but when nodes increase then PDR fall down. In case of group mobility model shown in Fig. 5 DSR have highest PDR, but DSR have lowest value of PDR. Fig. 6 shows the PDR of random waypoint mobility model, which have very highest value of PDR with all protocols. AODV have high value of PDR but DSR and DSDV have almost same but lower then AODV. |
 |
 |
| C) End to end delay |
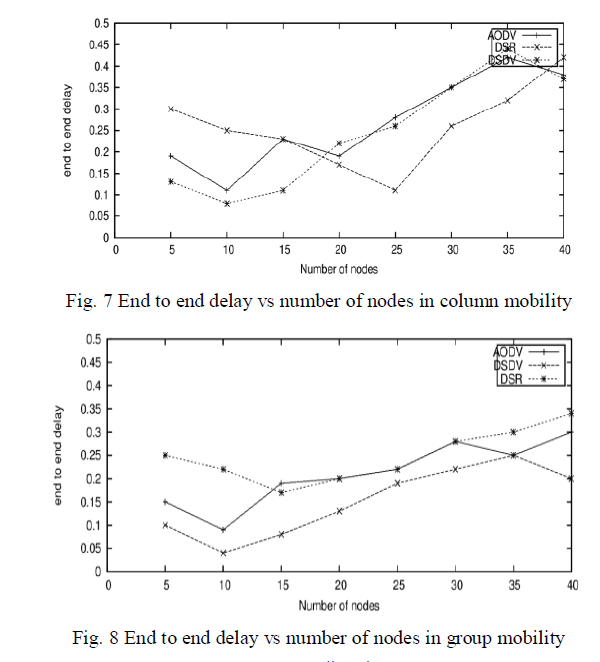
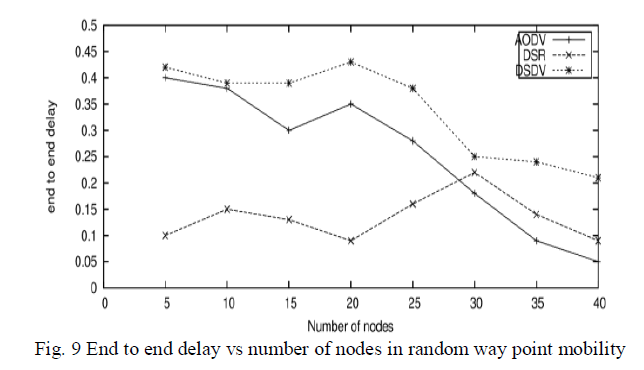
| It is the amount of time taken by packet to reach from one node to other. Fig. 7 shows end to end delay versus increasing number of nodes by using column mobility model. At lesser number of nodes the e2e delay of DSR is at its peak value but DSDV at its least value, after increasing number of nodes e2e of DSR start decreasing but oppositely DSDV and AODV start increasing. Fig. 8 shows e2e delay when group mobility model is used, DSR have higher e2e delay but DSDV have least. Fig. 9 shows random way mobility have higher values of delay. DSR is on its lowest value and DSDV have its largest point. With the increasing number of nodes the delay of these protocols gradually decreasing. |
 |
 |
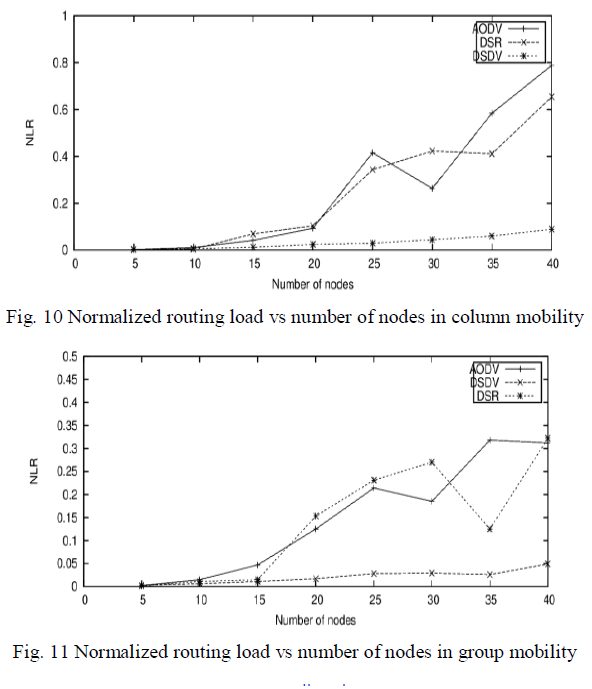
| D) Normalized routing load |
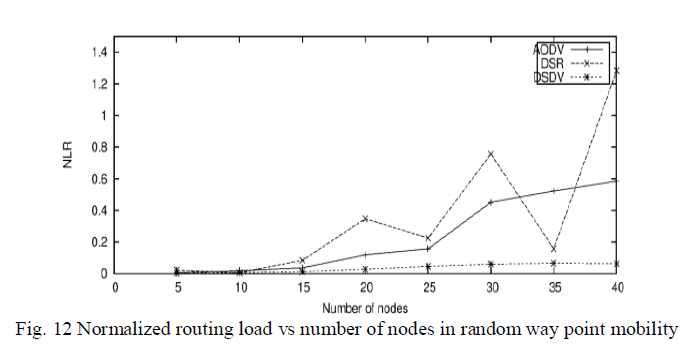
| It is the metadata and network routing information sent by a source node to destination node, which uses a portion the available bandwidth of a protocol. Fig. 10 shows the NLR versus number of nodes when column mobility model was used. In this AODV have a higher NLR but DSV is on bottom. Initially value of NLR is zero, but with number of nodes it’s gradually starts increasing. Value of NLR in DSDV is very lesser. In case of group mobility model shown in Fig.11, NLR is high when routing protocol is DSR and less when DSDV. Figure12 shows the normalized routing load when random way point mobility model is used. It shows a less values of DSDV but high value of DSR and AODV. |
 |
 |
VI.CONCLUSION
|
| It is observed that AODV has better throughput in all models, but random waypoint performs better in case of throughput than other models, i.e. AODV is more scalable. PDR is satisfactory in DSDV when group mobility model is used, but in other models AODV perform better. Delay to send the packet at the destination is less in group mobility model and column mobility model when protocol is DSDV, DSR has lesser delay when random mobility model is used. At last, for normalized routing load DSDV has most satisfactory performance among all three mobility models. |
References
|
- Elizabeth M. Royer, Santa Barbara nand Chai-keongToh, “A Review of current Routing protocols for Ad Hoc Mobile Wireless Networks”,IEEE Personal Communications, vol. 6, pp. 46-55, April 1999.
- Hongobo Zhou, “A survey on routing protocols in MANERs”, MSU-CSU, pp. 03-08, March 2003.
- R. Mkhija and R. Saluja, “Performance Comparison of Ad-hoc Routing Protocol in Different Network Size”, Proc. Of 2nd National Conf.Mathematical Techniques: Emerging Paradigms in Electronics and IT Industries, Sep 2008.
- Charles E. Perkins, PravinBhagwat. “Highly Dynamic Destination-Sequence Distance-Vector Routing (DSDV) for Mobile”. Proceedings ofthe SIGCOMM 94, August 1994.
- Charles E. Perkins, Elizabeth M. Royer, and Samir R. Das, “Ad hoc on-demand distance vector (AODV) routing.” IETF INTERNET DRAFT,MANET working group, July 2003.
- C. Siva Ram Murthy and B.S. Manoj, “Ad Hoc Wireless Networks: Architectures and Protocols,” Prentice Hall Communication Engineeringand Emerging Technologies Series, 2004.
- David B. Johnson, David A. Maltz, Yih-Chun Hu. “The Dynamic Source Routing Protocol for Mobile Ad hoc Networks (DSR).” InternetDraft, IETF MANET Working Group, April 2003.
- Jungkeun Yoon, Mingyan Liu, Brain Nobel, “Random waypoint Considered Harmful”, IEEE INFOCOM, Feb 2003.
- Anuj K. Gupta, Harsh Sadawarti, Anil K. Verma, “Performance analysis of MANET Routing Protocols in different mobility models”, IJITCSvol. 5, pp. 73-82, May 2013.
- Karen H. Wang, Baochun Li, “Group Mobility and Partition Prediction in Wireless Ad hoc Networks”, IEEE, pp. 1017-1021, Feb 2002.
- X. Hong, M. Gerla, G. Pei and C. Chiang, “A group mobility model for Ad hoc wireless networks”, Proceeding of the ACM InternationalWorkshop on Modeling and Simulation of Wireless and Mobile System (MSWiM), Aug 1999.
|