Ad-hoc networking is a concept in computer communications characterized by connectivity through a collection of wireless nodes and fast changing network topology. In a wireless scenario, nodes are free to move hence maintaining path (route) is a difficult task comparatively wired scenario. Routing protocols have central role in a wireless scenario. We analyse AODV Protocol by extensive simulations in ns-2 simulator with various performance matrixes such as Packet Delivery Ratio, End-to-End Delay, Routing Overhead, throughput under wired and wireless scenarios.
Keywords |
| AODV, Routing Protocol, CBR, Request, Source, Destination, Path, Performance Evaluation. |
INTRODUCTION |
| The need for Internet access through mobile devices, anywhere and anytime, has caused the development of model
which is different in comparison to access based on a previously set fixed infrastructure over which wireless devices
connect to the Internet nowadays. The new model is called Mobile Ad Hoc Network (MANET). MANET is a
collection of wireless mobile nodes that communicate with each other using multi-hop wireless links without any
existing network infrastructure or centralized administration [2]. Each node in the network behaves as a router and
forwards packets for other nodes.Essentially the protocol describes the communication, i.e., sending and receiving
information (called packets), between the nodes of a network. Ad-hoc networking is a rather new and hence not
thoroughly explored technology. The protocol is a complex and changes constantly as the technology evolves.
Therefore it offers us a good test-case for exploring requirements change. We omit a detailed description of the entire
protocol and present small excerpts from it. Since the topology of an ad-hoc network is volatile, sending data from one
node to another requires establishing a route between these nodes. Each node in the network is uniquely identified. It
stores and updates a routing table containing routes already found from this node, called source, to the other nodes,
called destinations, in the network. When the route is requested at the first time, node inserts it into its routing table
with the status unknown. When the route is found it is marked as valid which means it can be used for sending packets.
However, it can also become invalid when network topology changes. When node wishes to send a packet to the
destination marked in the route, it sends the packet to the node which is listed as a next node from the observed source
node in the route. In this way, packets are propagated toward destination nodes. Packets are buffered. Buffering allows
the node to not process packets with the same identifier more than once. |
AODV - AD HOC ON-DEMAND DISTANCE VECTOR |
| AODV protocol is defined by the RFC 3561, written by Charles Perkins and Elizabeth [4]. AODV has some similar
features as the Bellman-Ford distant vector algorithm, but it has been improved to work in a mobile environment [7].
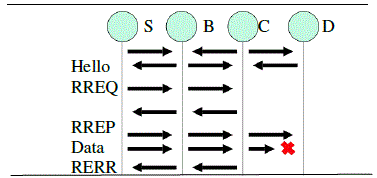
AODV uses hop-by-hop routing (AODV Route Discovery Process – Figure 6). Every node forwards data packets
towards a destination node according to its routing table (Figure 1). The routes in the AODV routing table are kept up
to date as long as they are needed by the source. AODV maintains a single path per a destination. The routing is
divided into two basic mechanisms. The first one is the route discovery. It is responsible for finding a route to the
destination if none is currently available in the routing table of the node. The second one is the route maintenance
which keeps the routes up-to-date, e.g. removes broken paths.AODV protocol also works in a network where the
communication links are bidirectional because if an (intermediate) node receives either a Route REQuest (RREQ) packet or a Route REPly (RREP) packet, it caches the previous node in its routing table (figure 1) as a next hop to the
end nodes. |
AODV PROTOCOL - CONTROL PACKETS |
| AODV uses four types of routing messages [1]. They are explained as follows: |
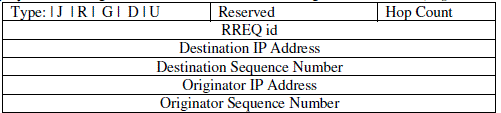
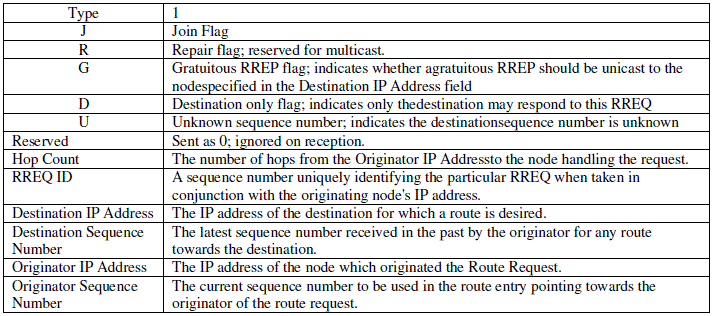
| RREQ : If a node wants to communicate with other node but no route is available, the source node starts a
route discovery by broadcasting a Route REQuest (RREQ) message in the network.(Figure 2 and 2-1) |
| The fields of Route REQuest message are: |
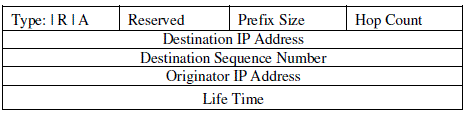
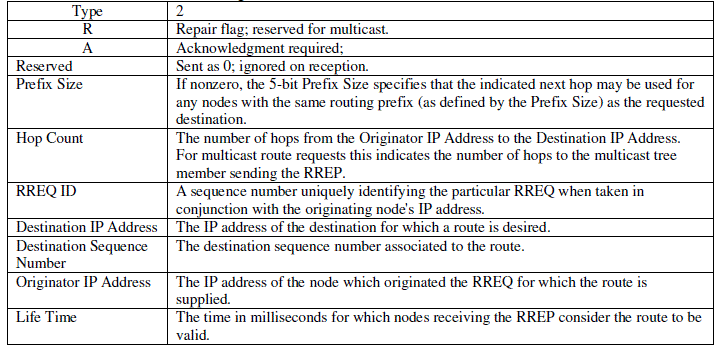
| RREP : If it is a destination node or an intermediate node has a valid route to the desired destination, it replies
to a RREQ by unicasting a Route REPly (RREP) message back to the source node.(Figure 3 and 3-1) |
| The fields of Route RREP message are: |
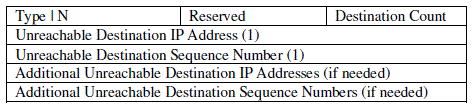
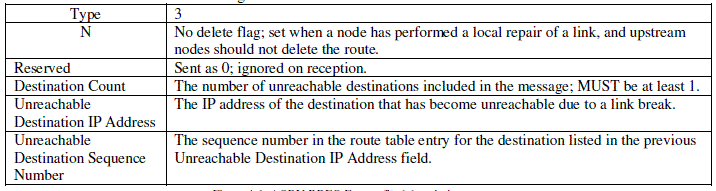
| RERR: If a path breaks, the intermediate node generates a Route ERRor (RERR) message to inform its end
nodes of the occurred link break. The RERR message is sent whenever a link break causes one or more
destinations to become unreachable from some of the node's neighbour’s.(Figure 4 and 4-1) |
| The fields of Route RERR message are: |
| HELLO: Each node broadcasts periodically a message with time to live (TTL) = 1, in order to maintain its
neighbour list. |
AODV ROUTE DISCOVERY |
| If a source has no entry for a destination in its routing cache, it starts a route discovery process. It floods a
RREQ packet in the network. The RREQ includes header fields with the following parameters: request ID,
source node ID, destination node ID, hop count, sequence number of the source node, sequence number of the
destination node and TTL (time-to-live). If an intermediate node receives a RREQ packet, it checks if it is the
destination node. If not, it checks if it has seen this RREQ before by checking the request ID and source node ID. If
this is the case the node just drops the packet and does not forward the RREQ any further. This avoids loops in the
route. If the RREQ packet is not dropped, the intermediate node searches in its route cache table. If there is an active
route to the destination, it sends back a RREP with its route entity. Otherwise it just rebroadcasts the received RREQ.
If the destination node has received the RREQ, it generates a RREP packet and sends it back in reverse way to the
source [8]. |
| If an intermediate node receives either a RREQ or a RREP packet, it stores information about the previous
node from which the packet was received in its routing table (Figure 1). With this mechanism, hop-by-hop routing, a
node can therefore decide which next hop it can use to reach a destination node. [1] |
AODV ROUTE MAINTENANCE |
| If a node tries to forward a message, but detects that there is a link break, i.e., the next node is not more
reachable, the forwarding node sends back a RERR message towards the source node. Whenever a node receives a
RERR message, it deletes all routes containing this broken link in its routing table. When the source receives the
RERR packet, it also updates its routing table, but it does not send the RERR packet anywhere. If the data session has
not yet been completed and the source does not have any other route to the destination, the node starts the route
discovery process [2]. |
CACHING IN AODV |
| We saw that AODV finds new routes by making a route request broadcast which travels through various
intermediate nodes before reaching the destination node. These requests carry a lot of information about the network
topology as they pass through different nodes but due to lack of caches at intermediate nodes, this information cannot
be tapped by the nodes to be used later. So by providing all the nodes with an extra cache and by making changes in
the RREQ packet such as to enable them to carry the information about the nodes through which they pass,
intermediate nodes can save the information about the network topology contained in the RREQ packets. This reduces
the time and overhead to find new routes in cases of route failure. From now on, we will call the AODV with cache
enabled as AODV-WC and AODV without caching as AODV-WOC. |
PERFORMANCE MATRIC & NETWORK PARAMETERS: |
| The simulations were performed using Network Simulator Ns-2 (www.isi.edu/nsnam/ns), popular in the adhoc
networking community. The mobility model used is Random Way point Model. The traffic sources are CBR
(continuous bit –rate), number of data connections is 10, data packet size is 512 byte and data sending rate is 4
packet/second. The source-destination pairs are spread randomly over the network in a rectangular filed of 700 m X
500 m. During the simulation, each node starts its journey from a random spot to a random chosen destination. Once
the destination is reached, the node takes a rest period of time in second and another random destination is chosen after
that pause time. This process repeats throughout the simulation, causing continuous changes in the topology of the
underlying network. The simulation time is 500 seconds and maximum speed of nodes is 10 m/s. The interface queue
is 150- packet drop-tail priority queue. Three types of network scenario are generated [3]. |
| 1. Wireless scenario with fixed position of nodes. |
| 2. Wireless scenario with movable nodes (traffic generated by cbrgen and setdest. |
| 3. Wireless scenario with movable nodes giving time slices for communication. |
| For network simulation, there are several performance metrics which is used to evaluate the performance. In simulation
purpose we have used three performance metrics [5],[6]. |
| 1. Packet Delivery Ratio: Packet delivery ratio is the ratio of number of packets received at the destination to the
number of packets sent from the source. The performance is better when packet delivery ratio is high. |
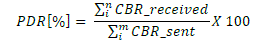 |
| 2 Average end-to-end delay: This is the average time delay for data packets from the source node to the destination
node. To find out the end-to-end delay the difference of packet sent and received time was stored and then
dividing the total time difference over the total number of packet received gave the average end-to-end delay for
the received packets. The performance is better when packet end-to-end delay is low. |
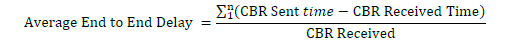 |
| Where n is number of received packets. |
| 3. Normalized Routing Load: Number of routing packets “transmitted” per data packet “delivered” at destination.
Each hop-wise transmission of a routing is counted as one transmission. It is the sum of all control packet sent by
all node in network to discover and maintain route. |
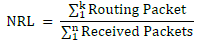 |
| Where n is number of received packets and k is number of routing packets. |
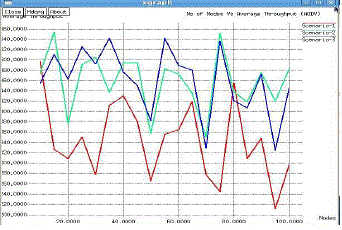
| 4. Average throughput: It is the ratio of total amount of data which reaches the receiver from sender to the time it
takes for receiver to receive the last packet. It is represented in bits per seconds. |
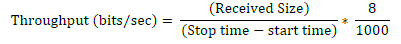 |
| Where n is number of received packets and m is number of send packets. |
RESULT AND DISCUSSION |
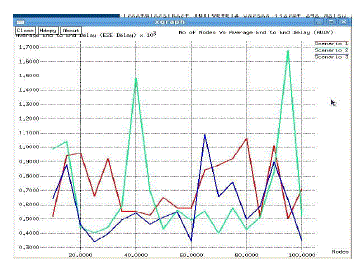
| Average end-to-end Delay:Average end–end delay in AODV is low with fixed position of ad-hoc nodes (Scenario-1)
as compared to movable nodes/ large number of nodes particularly (Scenario-2). (Figure 7) |
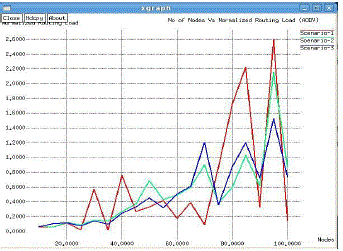
| Normalized Routing Load:With low number of sources/nodes (say 10) AODV performs better. But as mobility and
large number of nodes/sources, performance of AODV concerned to normalized routing load degrades (Figure 8). |
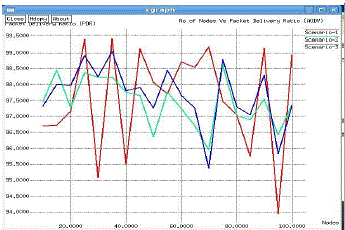
| Packet delivery ratio:AODV shows consistence performance in mobile nodes as compared to nodes with fixed
positions. In case of fixed nodes (wireless), an AODV protocol fluctuates (Scenario-1 of Figure 9) |
CONCLUSION |
| AODV shows low routing load and high packet delivery ratio for less number of sources, and better throughput for less
number of mobile nodes. AODV is a flat reactive (or on-demand) protocol, set up a path between the sender and the
receiver only if a communication is waiting. An advantage of a reactive protocol is its scalability as long as there is
only light traffic and low mobility. The disadvantages are: (a) the initial search latency may degrade the performance of
the interactive applications, (b) the quality of the path is unknown in advance, and (c) route caching mechanism is
useless in high mobility networks as routes change frequently. |
FUTURE WORK |
| Performance analysis of AODV, DSR, DSDV routing protocols for performance measures like throughput, end to end
delay, packet delivery ratio, normalized routing load. Then to analysis these parameters by varying pause time /
mobility of nodes (speed). |
Figures at a glance |
 |
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 2-1 |
Figure 3 |
Figure 3-1 |
 |
 |
 |
 |
 |
| Figure 4 |
Figure 4-1 |
Figure 5 |
Figure 5-1 |
Figure 6 |
 |
 |
 |
 |
| Figure 7 |
Figure 8 |
Figure 9 |
Figure 10 |
|
References |
- http://www.ietf.org/rfc/rfc3561.txt
- Ian D. Chakeres and Elizabeth M. Belding-Royer. AODV Routing Protocol Implementation Design, International Journal of Wireless and Mobile Computing (IJWMC) Issue 2/3, 2005
- Gao, Fang, Lu, Yuan, Zhang, Qingshun and Li, Chunli. Simulation and Analysis for the Performance of the Mobile Ad Hoc Network Routing Protocols.
- Charles E. Perkins and Elizabeth M. Belding-Royer, Ad hoc On-Demand Distance Vector (AODV) Routing, 19 January 2002, [Online] http://tools.ietf.org/html/draft-ietf-manet-aodv-10
- Wang Lin-zhu, FANG Ya-qin and SHAN Min, ?Performance comparison of Two Routing Protocols for Ad Hoc Networks?, WASE International conference on Information Engineering, 2009.
- Mohammed Bouhorma, H.Bentaouit and A.Boudhir, ?Performance comparison of Ad hoc Routing protocols AODV andDSR? ,IEEE2009.
- MainakChaudhuri, Mark Heinrich, Chris Holt, ?Latency, Occupancy, and Bandwidth in DSM Multiprocessors: APerformanceEvaluation?, IEEE TRANSACTIONS ON COMPUTERS, VOL. 52, NO. 7, JULY 200
- Amita Rani and Mayank ?Performance Evaluation of Modified AODV for Load Balancing?, Journal of Computer Science 3 (11):
863-868, 2007
|