Keywords
|
| Watermarking, DCT wavelet, column transform, row transform, binary distribution, Gaussian distribution, run lengthnoise |
INTRODUCTION
|
| Internet and high speed computer networks have explored new ways of transmitting and receiving digital data for various purposes and in different forms. It has also led to ease of alteration and duplication of digital contents sent over the network. To protect digital contents from such duplications and manipulations has created opportunities for research in the domain of digital data security or protection. Digital watermarking is one of such popular technique of copyright protection. It hides certain details of owner of digital data in the data itself. These details can be hidden in the form of digital image, audio signals, video signals or text which determines the nature of digital watermarking. If the secret information is hidden in the form of digital image into another image, it is termed as digital image watermarking. Digital image watermarking can be performed in two domains, spatial domain and frequency domain. When directly pixel values of image are altered in order to hide the secret information, it is spatial domain watermarking. When image is converted into frequency components and these frequency components are used to hide the secret information, it is frequency domain watermarking. Though spatial domain watermarking is easy to perform, it is more vulnerable to malicious attacks and hence less robust than frequency domain watermarking. In contrast, frequency domain watermarking is more robust at the cost of its computational complexity. Computational cost is definitely acceptable instead of sacrificing the robustness or security of watermarking. In recent years, lot of work has been carried out in frequency domain watermarking using transforms like DCT, DWT, DFT and SVD and it is still going on. A good watermarking technique is expected to have following characteristics |
| ïÃâ÷ Robustness- robustness refers to the ability of recovering embedded watermark even after performing intentional or non-intentional processing of watermarked image. |
| ïÃâ÷ Imperceptibility- imperceptibility refers to the perceptual similarity between host image and watermarked image |
| ïÃâ÷ Security- security refers to protection of embedded watermark against various attacks which try to eliminate the watermark. |
| ïÃâ÷ Capacity- capacity refers to the amount of information embedded in the host image as a watermark for protection of copyright of an image |
| Though they are desirable characteristics, they are contradictory sometimes. Achieving robustness may lead to compromising imperceptibility. Whereas, increasing capacity may lead to less robustness in watermarking. While using Discrete Wavelet Transform, selection of appropriate frequency band plays an important role as it affects robustness and imperceptibility. Low frequency bands are normally major information contents of an image. Any modification to low frequency components therefore causes degradation into host image which is easily perceptible to Human Visual System. However, in literature there are many methods of watermarking have been proposed which embed watermark in lower frequency components without losing imperceptibility of watermarked image. High frequency components in an image carry minimal information contents but they are responsible for edges in image. Since they carry minimum information about an image, alteration of these components due to embedding watermark is not easily sensed by human visual system. But it leads to high susceptibilityto attacks like lossy image compression which eliminates high frequency components from image. However it may prove more robust to other image processing attacks. To eliminate drawbacks of altering low frequency and high frequency components and to achieve benefits in terms of imperceptibility, selection of mid-frequency components is getting more attention in watermark embedding. |
| In this paper, a blind watermarking for digital images is proposed using DCT wavelet transform. DCT wavelet transform matrix of desired size NxN can be generated from DCT matrices of sizes PxP and QxQ where P and Q are factors of N and N is power of 2 using KekreâÃâ¬ÃŸs algorithm for generating wavelet transform from orthogonal transform proposed in [1]. Simulation work is conducted by applying DCT wavelet for embedding and extracting watermark in three different ways: full DCT wavelet transform, Column DCT wavelet transform and Row DCT wavelet transform. Embedding is performed in mid frequency components. Instead of embedding all frequency coefficients of watermark, high frequency coefficients are eliminated from watermark. Embedding of such compressed watermark causes less visual degradation in watermarked image. Performance of three approaches is compared against various attacks like cropping, compression, resizing and noise attacks. |
| Remaining paper is organized as follows: section II briefly covers related work done so far in digital image watermarking. Section III gives short description about DCT wavelet transform, row and column transform. Section IV describes the proposed method of watermarking. Section V gives the analysis of results obtained using full, column and row DCT wavelet transforms. Section VI gives conclusion of the simulation work conducted. |
RELATED WORK
|
| SangeetaJadhav in [2] has introduced a watermarking system for color images using Blind Source Separation. The system is implemented in hybrid domain: for host it is in wavelet domain and for watermark it is in spatial domain. Texture analysis of host image is carried out based on its energy contents which make it image adaptive. Textured region block is selected based on its energy and its wavelet transform is obtained. LL1 band is used for further processing if it is single level wavelet decomposition. For higher level decomposition, corresponding LL frequency bands are selected. Spatial domain watermark is hidden in textured region by obtaining mixing matrix through Quasi- Newton algorithm(add reference). Performance of the system is evaluated for various color spaces like YIQ, HSI andYCbCr.Better results are obtained for Y channel in YIQ space. An efficient digital image watermarking algorithm was presented by HumingGao, LiyuanJia, Meiling Liu in [3]. Color image is first separated into color channels R G and B. These color components are then subjected to two level wavelet decomposition. Embedding positions for watermark are determined by comparing energy values in low frequency sub-bands in green and blue channels. Watermark is encrypted using Arnold transform and then is embedded into appropriate positions obtained. Pooja Malhotra, MeenakshiMoza, JyotiVerma proposed a DWT-SVD based watermarking scheme in [4]. Host image is divided into four frequency bands using wavelet transform. Singular values of HL and HH sub-band are obtained. Watermark is divided into two halves. Each of them is embedded into HL and HH bands by modifying their singular values by appropriate scaling factor. Image normalization based robust watermarking technique is proposed by Ibrahim Alsonosi Nasir, Ahmed b. Abdurrman in [5,]. Watermark is embedded in Luminance component i.e. Y channel or blue channel if RGB color space is used. Circular image is obtained from blue channel and then it is rotation normalized. A square sub image is obtained from rotation normalized image and decomposed till L levels using DWT. Watermark is embedded in highest level of wavelet decomposition excluding the coarsest LL sub band. Image normalization technique reduces the effect ofsynchronization errors caused by geometric attacks such asrotation.A. Umaamaheshvari and K. Thanushkodi in [6] proposed a watermarking method which is mix of feature based and transform based method. Harris Laplacian detector is used to extract primary features from cover image which are suitable for watermark embedding. To enhance the resistance, set of auxiliary features are used to embed watermark. These auxiliary features are obtained using Knapsack algorithm. DCT is used to extract embedded watermark.An easy way to comply with the conference paper formatting requirements is to use this document as a template and simply type your text into it. |
| K.Chaitanya, E. Sreenivasa Reddy, K.Gangadhara Rao proposed DWT- DCT based method for watermarking of color images in [7]. Host and watermark images are separated into R, G and B channels. Two-level DWT is applied to blue channel of host. HL2 sub-band obtained through this decomposition is divided into 8x8 blocks. DCT is taken of each block. DCT is applied to each channel of watermark. One pixel from every channel of watermark is embedded into each block of HL2. Reverse procedure is followed to extract the watermark. In [8], Shahin Shaikh, ManjushaDeshmukh proposed a DCT based digital image watermarking technique for grayscale images. Both host and watermark image are divided into 8x8 blocks. DCT of each block is computed. For each block of host, texture, edge, luminance and corner information is computed. DCT of each block of watermark image is computed. All DCT coefficients of host image blocks are replaced by using DCT coefficients of watermark and JND mask.YashovardhanKelkar, Heena Shaikh, Mohd.Imran Khan proposed a DWT-DCT-SVD based hybrid digital image watermarking technique for color images in [9]. In their proposed technique, host image is decomposed into LL, LH, HL and HH frequency bands. DCT is applied to the frequency band selected for watermark embedding. Singular value decomposition of DCT transformed sub-band is obtained. Similar procedure is followed for watermark image. Singular values of host are then replaced by singular values of watermark. Four sub-bands can be used to embed same watermark or four different watermarks.In[10], Gursharanjeet Singh Kalra, Rajneesh Talwar, Harsh Sadawarti proposed DWT and DCT based watermarking technique. In their proposed technique, original image is decomposed up to third level of wavelet decomposition. HL3 band is selected for embedding watermark. HL3 band is further decomposed into 8x8 blocks and DCT of these blocks is computed. Watermark which is chosen to be a binary image is subjected to Arnold transformation followed by chaos transformation. Each bit of watermark is embedded into DCT coefficients of original image by using standard deviation of original image and depth of watermark. The technique is found to be robust enough to handle the attacks like JPEG, filtering, and different types of noise attacks.RoshanJahan has introduced a watermarking scheme using DWT-SVD and chaotic encryption based on optimized genetic algorithm in [11]. First host image is decomposed into LL, LH, HL and HH frequency bands using DWT. Singular values of LH and HL band are obtained. These singular values are replaced by scaled singular values of watermark. Before embedding, Watermark is encrypted using chaotic encryption and genetic algorithm which adds to the security and robustness of their proposed scheme. In [12] Ambika Agarwal, Neha bora and Nitin Arora proposed a DWT-SVD based algorithm for watermarking. Here host image is decomposed into two levels of wavelet decomposition. However, instead of LL band, HL band is used for next level decomposition. Singular values of second level decomposed HL band are replaced with scaled watermark image. |
| Mohd Rizal Mohd Isa and Salem Aljareh proposed a DCT based watermarking scheme in [13] to protect the biometric images especially for face recognition. Addition of watermarking scheme does not highly affect the recognition rate and better recognition rate is observed by authors under various attacks on biometric images.Jagdish C. Patra, Jiliang E. Phua and DeepuRajan in [14] presented a novel Chinese Remainder Theorem (CRT) based watermarking scheme that works in the Discrete Cosine Transform (DCT) domain. Host image is divided into 8x8 blocks and DCT is applied to them. To embed watermark bits appropriate co-prime values are selected in CRT algorithm.DongyangTeng, Renghui Shi, Xiaoqun Zhao proposed the DCT image watermarking technique based on the mix of time-domain in [15]. Host image is divided into blocks and mixed with orthogonal matrices in time domain. A host image mixed in the time domain is subjected to DCT and watermark is embedded in frequency domain. Combination of pre-transformation in time-domain with DCT, disperse the noise and make the recovered watermarking image clearer. B.L. Gunjal and R.R.Manthalkar in [16] presented strongly robust digital image watermarking scheme based on „Discrete Wavelet Transform, by embedding scrambled watermark in middle frequency sub band. The security levels are increased by generating PN sequence depending on periodicity of watermark image. The image scrambling is applied by Arnold Transform. The decomposition is done with Haar which is simple, symmetric and orthogonal wavelet and the direct weighting factor is used in watermark embedding and extraction process.Gerardo Pineda Betancourth in [17] presented a fragile watermarking scheme for image authentication. It has the ability to localize the tampered regions. In their proposed scheme, only few number of wavelet coefficients are watermarked but all are implicitly protected. This reduces embedding distortion. Other key features of this method are that it is key dependent, content based and nondeterministic neighborhood-dependent method. Hence it can resist attacks like transplantation attacks and vector quantization attacks. |
| In [18], Ezz El-Din Hemdan, Nawal El-Fishaw, GamalAttiya, and FathiAbd El-Samii proposed hybrid watermarking technique which is based on DWT and SVD. Before embedding, two watermarks primary and secondary are fused using wavelet fusion algorithm. This fused watermark is embedded into singular values of one level wavelet decomposed cover image using appropriate scaling factor. This technique improved both the capacity of the embedded information and robustness without affecting the perceptual quality of the original image. In [19], Nagaraj V. Dharwadkar, B. B. Amberker&AvijeetGorai proposed a non-blind watermarking scheme for color images. In their proposed scheme, watermark is embedded in blue channel of cover image. Blue channel of cover image is subjected to wavelet decomposition and then singular values of each sub band are obtained. Singular values of watermark are embedded in these singular values of blue channel. Embedding watermark in all four sub bands makes it very difficult to remove. M.A. Dorairangaswamy proposed a blind watermarking scheme in [20]. Their research work presents a robust and blind watermarking scheme for copyright protection against piracy of digital images. It makes use of a binary image as watermark data for protecting the copyrights of the digital image. Here, for every pixel of the host image, a binary watermark image pixel is embedded on the basis of the gain factor and the generated random matrix. The embedded binary watermark is extracted from the watermarked image using watermark image size and the correlation coefficient. K.C. Liu, C.H. Chou proposed a robust and transparent watermarking scheme for color images in [21]. Watermark is embedded in perceptually significant sub bands of luminance and chrominance components of color image in wavelet domain. The higher perceptual redundancy in each color component of the color image indicates that the great strength of the watermark can be embedded into the color image for higher robustness without resulting in visible distortion. Robust watermarking scheme is proposed by Yasunori Ishikawa, KazutakeUehira and Kazuhisa Yanaka in [22]. In their proposed technique of optical watermarking in which size of pixel blocks is varied by a trade-off in the efficiency of embedded watermarking. 4x4, 8x8, and 16x16 pixels were used in one block to embed one bit of watermark. A detection accuracy of 100% was obtained by using a block with 16x16 pixels. H. B. Kekre, TanujaSarode, ShachiNatu presented a DWT-DCT-SVD based hybrid watermarking method for color images in [23]. In their method, robustness is achieved by applying DCT to specific wavelet sub-bands and then factorizing each quadrant of frequency sub-band using singular value decomposition. Watermark is embedded in host image by modifying singular values of host image. Performance of this technique is then compared by replacing DCT by Walsh in above combination. Walsh results in computationally faster method and acceptable performance. Imperceptibility of method is tested by embedding watermark in HL2, HH2 and HH1 frequency sub-bands. Embedding watermark in HH1 proves to be more robust and imperceptible than using HL2 and HH2 sub-bands. In [24] and [25] Kekre, Sarode, and Natu presented DCT wavelet and Walsh wavelet based watermarking techniques. In [24], DCT wavelet transform of size 256*256 is generated using existing well known orthogonal transform DCT of dimension 128*128 and 2*2. This DCT Wavelet transform is used in combination with the orthogonal transform DCT and SVD to increase the robustness of watermarking. HL2 sub-band is selected for watermark embedding. Performance of this proposed watermarking scheme is evaluated against various image processing attacks like contrast stretching, image cropping, resizing, histogram equalization and Gaussian noise. DCT wavelet transform performs better than thier previously proposed DWT-DCT-SVD based watermarking scheme in [23] where Haar functions are used as basis functions for wavelet transform. In [25] Walsh wavelet transform is used that is derived from orthogonal Walsh transform matrices of different sizes. 256*256 Walsh wavelet is generated using 128*128 and 2*2 Walsh transform matrix and then using 64*64 and 4*4Walsh matrix which depicts the resolution of host image taken into consideration. It is supported by DCT and SVD to increase the robustness. Walsh wavelet based technique is then compared with DCT wavelet based method given in [24]. Performance of three techniques is compared against various attacks and they are found to be almost equivalent. However, computationally Walsh wavelet was found preferable over DCT wavelet. Also Walsh wavelet obtained by64*64 and 4*4 is preferable over DCT wavelet and Walsh wavelet obtained from corresponding orthogonal transformmatrix of size 128*128 and 2*2. In [26], other wavelet transforms like Hartley wavelet, Slant wavelet, Real Fourier wavelet and Kekre wavelet were explored by H. B. Kekre, TanujaSarode and ShachiNatu. Performance of Slant wavelet and Real Fourier wavelet were proved better for histogram Equalization and Resizing attack than DCT wavelet based watermarking [24] and Walsh wavelet based watermarking presented in [25]. |
DCT WAVELET TRANSFORM, COLUMN TRANSFORM AND ROW TRANSFORM
|
| DCT wavelet transform matrix is generated from orthogonal DCT transform using algorithm proposed in [1]. In the proposed method, host images of size 256x256 and watermark of size 128x128 have been used. Hence we require DCT wavelet matrix of size 256x256 and 128x128. These matrices can be generated using various combinations of component orthogonal DCT matrix. In the presented work, 256x256 size DCT wavelet matrix is generated using two 16x16 DCT matrices and 128x128 size DCT wavelet matrix is generated using 16x16 and 8x8 size DCT matrices. For an image f, transform of image is given by |
 |
PROPOSED TECHNIQUE
|
| Proposed technique is experimented on ten host images using five watermarks in Matlab R2012. Host images and watermark images used in experimental work are shown in Figure 1 and Figure 2. |
Figure 1: Host images used for experimental work |

Figure 2: Watermarks used for experimental work |
| Proposed technique is divided into two phases namely watermark embedding and watermark extraction. In watermark embedding phase, host image is separated into R, G and B channel and column DCT wavelet of each channel is taken. This results into energy compaction of image towards upper rows. Column DCT wavelet of each channel of watermark is also obtained. Watermark is compressed with compression ratio 2.67 and is embedded in mid frequency components of host image. Before embedding watermark coefficients are normalized and the normalization coefficient is saved. Then it is scaled by appropriate factor such that it will strengthen the watermark and also embedment of watermark will be visually imperceptible. In the proposed technique, this scaling factor selected is 25. Compression ratio for watermark is selected by trial and error method to give good visual quality of watermark to be embedded without significant loss of information from it. Scaling factor is also chosen by trial and error method so that embedding will result into good imperceptibility of embedded watermark into host image. Figure 3 andFigure 4 below show the embedding and extraction procedures respectively. These steps are repeated for row transform and full DCT wavelet transform for comparison. |
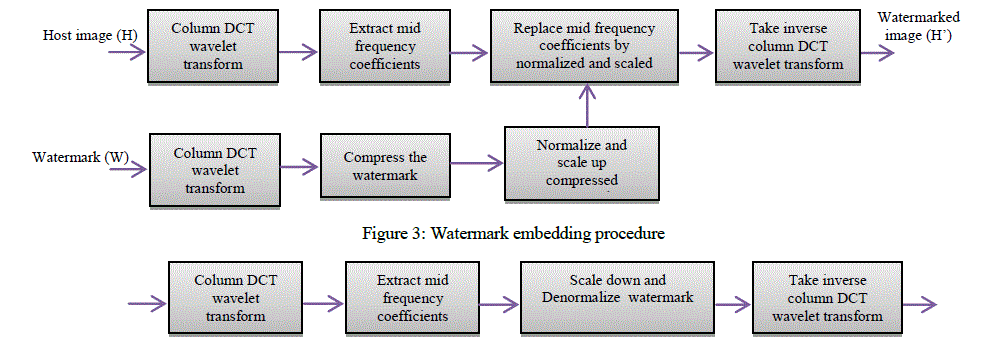
Figure 4: Watermark extraction procedure |
RESULTS AND DISCUSSION
|
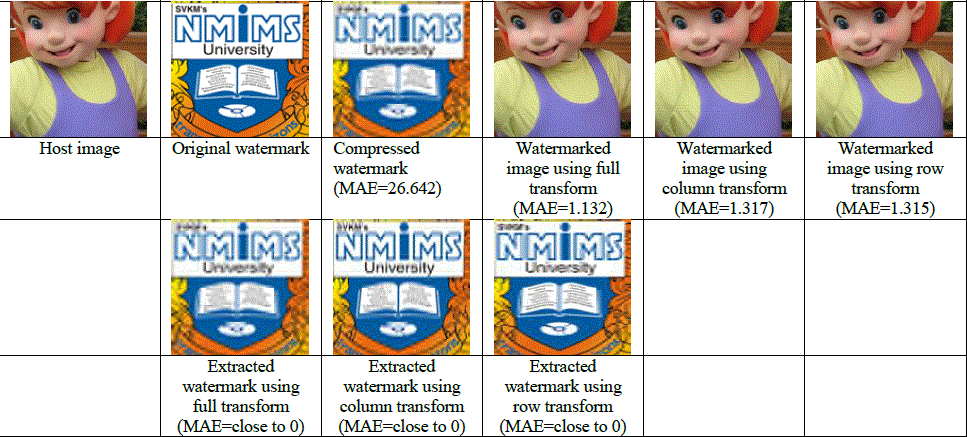
Figure 5: Original host and watermark images, compressed watermark and watermarked images and extracted watermarks using Full, column and row DCT wavelet |
| Various types of attacks performed on watermarked images are cropping, compression, resizing and noise attack. |
| A. Cropping |
| Watermarked images are subjected to three types of cropping attacks- cropping squares of 16x16 size at four corners, cropping squares of 32x32 size at four corners and cropping 32x32 square at the centre of an image. Result images for these attacks are shown in following figure 6. |
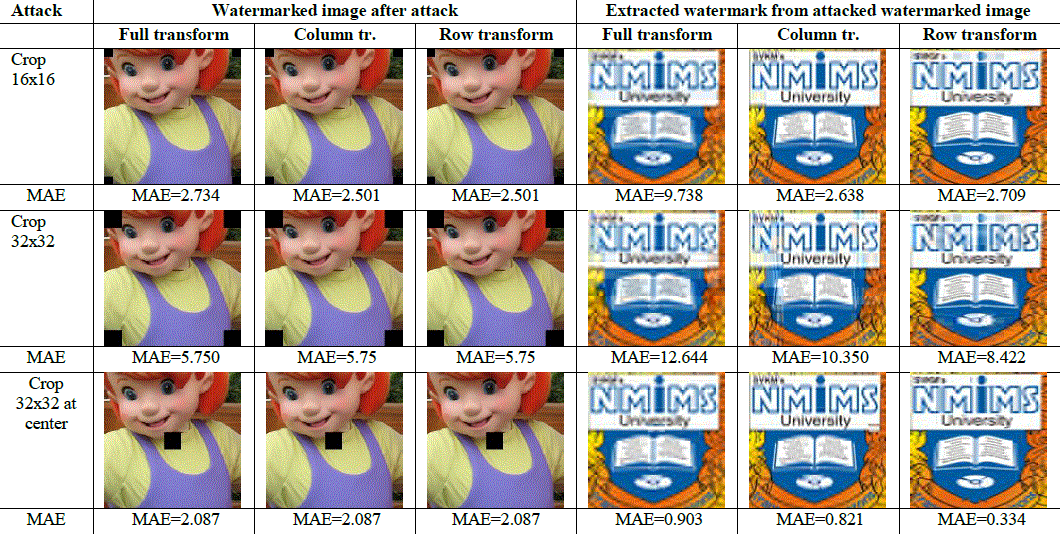
Figure 6: Result images for 16x16, 32x32 cropping at corners and 32x32 cropping at centre using Full DCT wavelet, column DCT wavelet and Row DCT wavelet |
| MAE values between embedded and extracted watermarks for cropping 16x16 attack using Full, Column and Row transform are compared in the following Figure 7. |
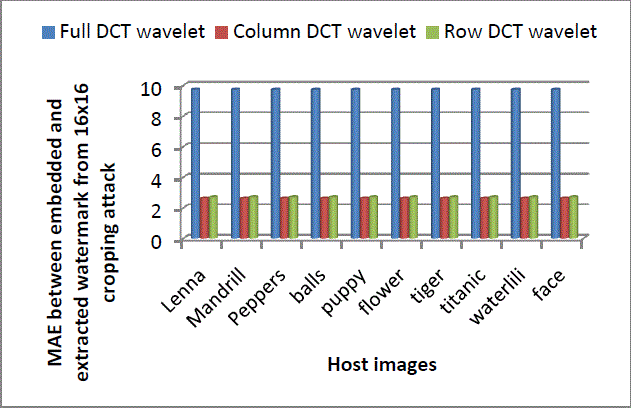 |
| Figure 7: comparison of MAE values between embedded and extracted watermark for cropping 16x16 square at corners using Full, Column andRow DCT wavelet |
| From Figure 7 it can be easily observed that, for full transform, MAE values between embedded and extracted watermarks are nearly four times higher than in case of column and row transform. For row transform these values are slightly higher than column transform for all host images. So for 16x16 cropping done at corners of an image, Column DCT wavelet transform gives best performance. However, for 32x32 cropping done at the corners of an image, row transform gives best robustness among the three as shown in Figure 8. Figure 8 indicates that MAE values between embedded and extracted watermarks for full transform are 1.22 times higher than column transform values and 1.5 times higher than row transform values. Also MAE values obtained from column transform are 1.22 times higher than in case of row transform. |
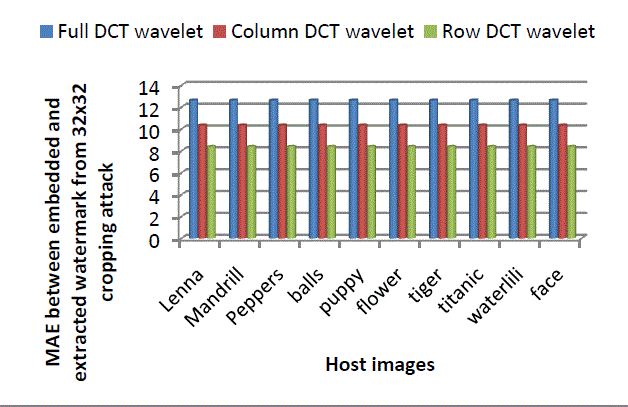 |
| Figure 8: comparison of MAE values between embedded and extracted watermark for cropping 32x32 square at corners using Full, Column and Row DCT wavelet |
| Performance comparison for robustness against cropping 32x32 square at the centre of an image using full, column and row transform are shown in following Figure 9. Row transform proves the most robust approach for this type of cropping attack also. Another important thing that can be observed from Figure 7, Figure 8 and Figure 9 is that for cropping done at the centre of an image, least MAE is observed between embedded and extracted watermark for all three types of applying DCT wavelet transform. |
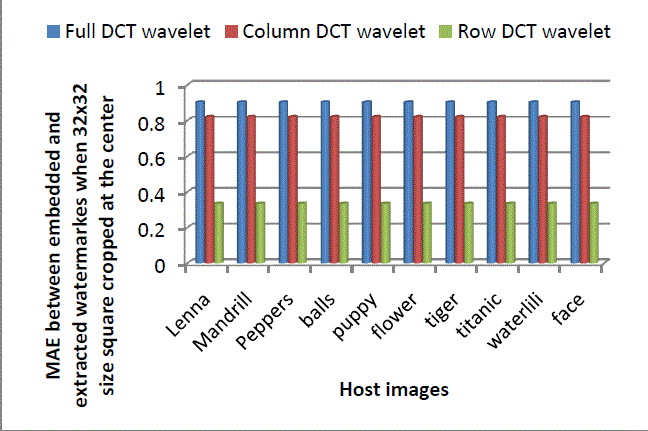
Figure 9: Comparison of MAE values between embedded and extracted watermark for cropping 32x32 square at centre using Full, Column and Row DCT wavelet |
| B. Compression |
| Watermarked images are compressed using DCT wavelet transform for compression ratio 1.95 and using DCT, DST and Walsh for compression ratio 1.14. |
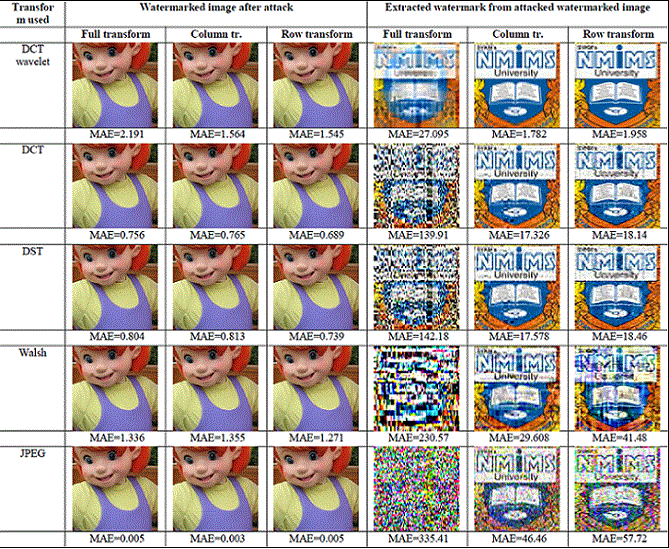
Figure 10: Result images for compression using DCT wavelet, DCT, DST and Walsh using Full DCT wavelet, column DCT wavelet and Row DCT wavelet. |
| From above Figure 10, it can be observed that when the transform used for watermark embedding and compression is same, the proposed technique is more robust. Robustness level gets degraded when any other transform is used for compression. For JPEG compression, full DCT wavelet transform does not withstand but column and row DCT wavelet show better robustness. |
| Following Figures Figure 11 to Figure 14 show performance of full, column and row DCT wavelet transform against compression using DCT wavelet, DCT, DST and Walsh. Column and row transform are found to be more robust than full transform in all the cases. For DCT wavelet, row DCT wavelet transform shows slightly less robustness than column DCT wavelet transform. MAE values obtained by column transform are 15 times less and obtained by row transform are 13.5 times less than that of full transform. |
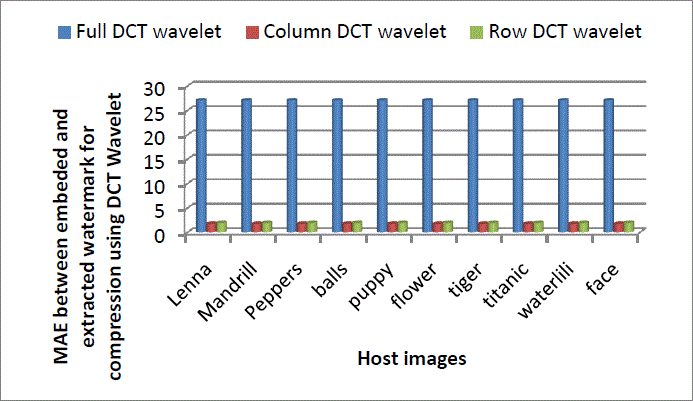
Figure 11: Comparison of Full, Column and Row DCT wavelet for compression attack using DCT wavelet |
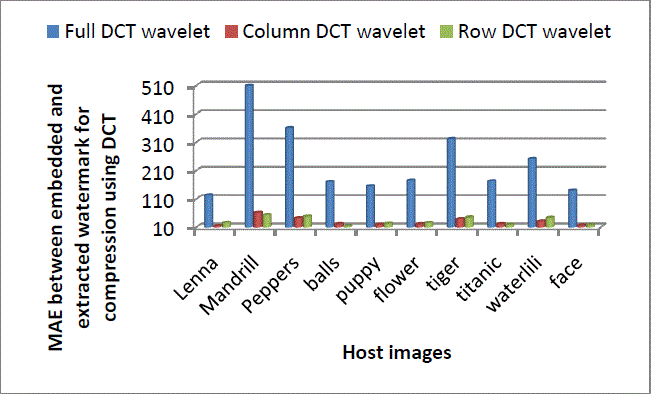
Figure 12: Comparison of Full, Column andRow DCT wavelet for compression attack using DCT |
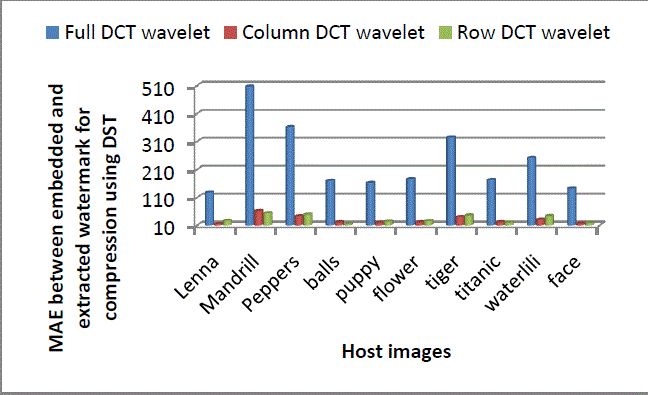 Figure 13: Comparison of Full, Column and Row DCT wavelet for compression attack using DST Figure 13: Comparison of Full, Column and Row DCT wavelet for compression attack using DST |
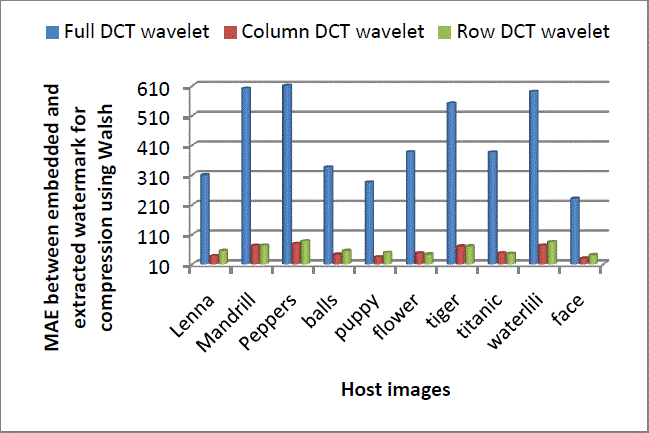
Figure 14: Comparison of Full, Column and Row DCT wavelet for compression attack using Walsh |
| From Figure 12, 13 and 14, it can be seen that on an average column DCT wavelet gives more robustness than row DCT wavelet when watermarked images are compressed by using DCT, DST and Walsh |
| C. Resizing |
| Watermarked images are resized using bicubic interpolation. First its size is increased by four times and then reduced back to its original size. Another way of performing resizing attack is watermarked image size is doubled and then reduced back to original size. Result images for resizing attack are shown in Figure 15. |
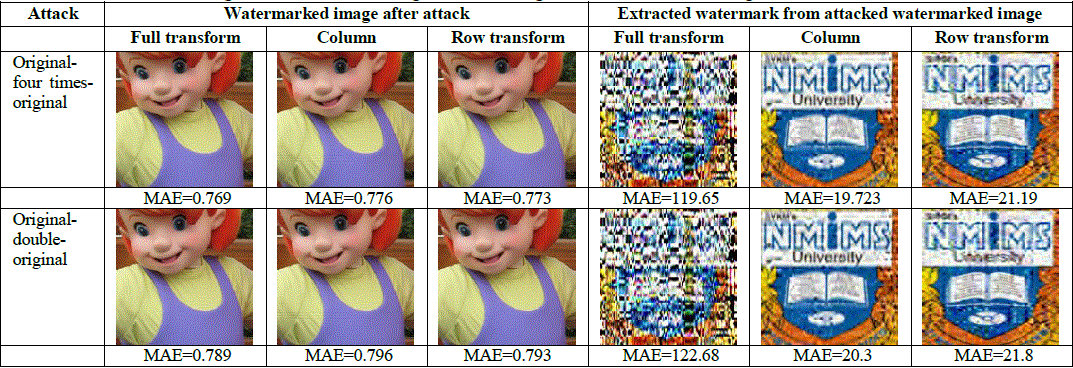
Figure 15: Result images for resizing attack using bicubic interpolation using Full DCT wavelet, column DCT wavelet and Row DCT wavelet. |
| Figure 16 and Figure 17 show performance comparison of full, column and row DCT wavelet for original-four times-original resizing and original-double-original resizing attack respectively in terms of MAE between embedded and extracted watermark. Full transform gives much higher values of MAE than column and row transform. Among column and row transform, column transform shows better robustness i.e. less MAE values. |
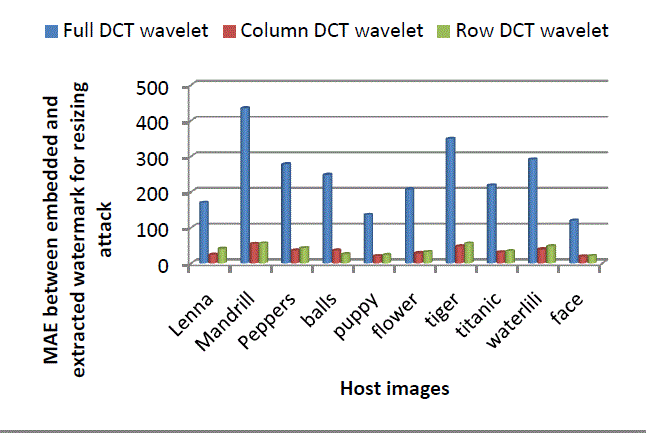 |
| Figure 16: Comparison of Full, Column and Row DCT wavelet for resizing attack |
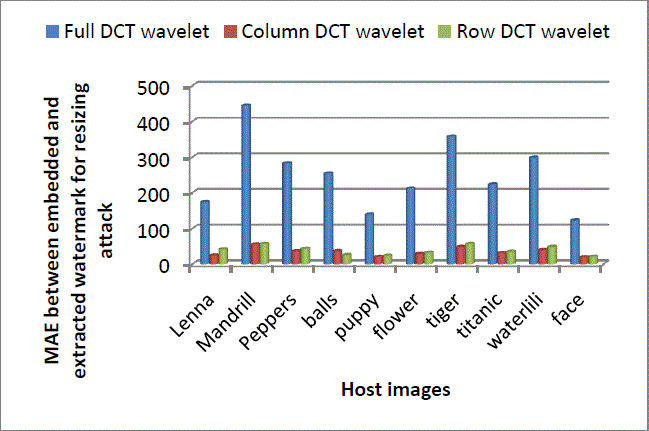
Figure 17: Comparison of Full, Column and RowDCT wavelet for resizing attack |
| D. Noise attack |
| Binary distributed run length noise is generated having magnitude -1 or 1 and random run length between 1 to 10, 5 to 50 (in multiples of 5) and 10 to 100 (in multiples of 10). This noise is added to watermarked image. Gaussian distributed run length noise is generated with magnitude ranging between -2 to 2 and random run. Results are shown in following Figure 18. |
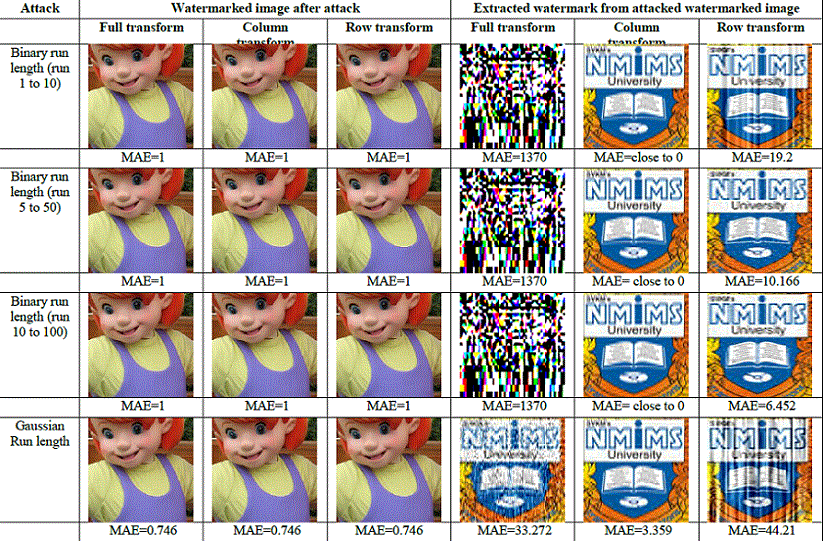
Figure 18: Result images for binary distributed run length noise with run 1 to 10, 5 to 50 in multiple of 5 and 10 to 100 in multiple of 10 and Gaussian distributed run length noise attack using Full DCT wavelet, column DCT wavelet and Row DCT wavelet. |
| Figure 18 above indicates that for binary distributed run length noise, as length of run is increased, extracted watermark is closer to embedded one in case of row DCT wavelet transform. However, for full and column DCT wavelet transforms, there is no change in MAE values. Figure 19 below shows the performance comparison of full, column and row DCT wavelet transform for Gaussian distributed run length noise attack. |
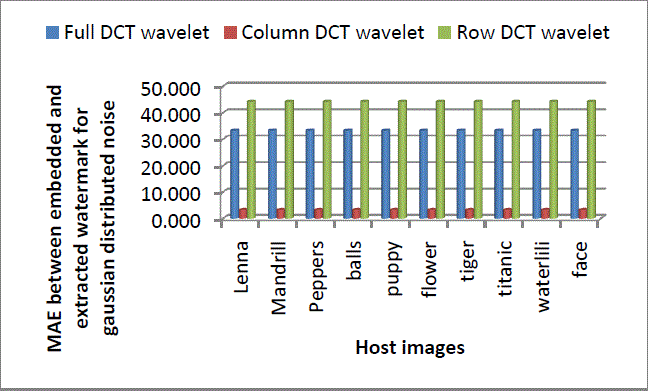
Figure 19: Performance comparison for Gaussian distributed run length noise attack using Full DCT wavelet, column DCT wavelet and Row DCT wavelet. |
| From Figure 19 it can be concluded that, column transform when used for embedding and extracting watermark, performs best under Gaussian distributed run length noise attack. It gives MAE values nearly 10 times less than full transform and 13 times less than row transform. Row DCT wavelet fails to provide better robustness than full DCT wavelet. |
CONCLUSION
|
| Column DCT wavelet transform and Row DCT wavelet transform are computationally efficient than full DCT wavelet transform. While embedding watermark in host image, on an average, column DCT wavelet causes less perceptual quality degradation than full and row transform. However, in all three cases, extracted watermark is very close to the embedded one with MAE value close to zero. For majority of attacks tested in the proposed work, column and row DCT wavelet transforms give significantly better robustness than Full DCT wavelet transform. |
| For 32x32 cropping attack, row transform gives best performance. For 16x16 cropping attack, row transform shows slightly higher MAE values for extracted watermark. |
| For Gaussian distributed run length noise attack, column DCT wavelet is observed to give outstanding robustness. Also for resizing attack, column transform performs better than full and row transform. |
| Full DCT wavelet transform cannot sustain binary distributed run length noise attack and JPEG compression attack. Whereas, for binary distributed run length noise attack, column DCT wavelet constantly outperforms irrespective of the run length of noise. For row DCT wavelet transform, change in run length of binary distributed noise affects the robustness. As length of run is increased, row DCT wavelet improves in robustness. |
| For compression attack using DCT wavelet, DCT, DST and Walsh, Column and row transform are found to be more robust than full transform in all the cases. MAE values obtained by column transform are 15 times less and obtained by row transform are 13.5 times less than that of full transform in compression using DCT wavelet. |
| For resizing attack, column DCT wavelet is more robust than row DCT wavelet transform. Full DCT wavelet transform does not give sustainable performance against resizing attack. |
| In all different attacks, it is observed that column and row transforms give far better performance as compare to full DCT wavelet transform. Among row and column DCT wavelet transform, column DCT wavelet transform is better. |
References
|
- H.B.Kekre, ArchanaAthwale, DipaliSadavarti, “Algorithm to Generate Wavelet Transform from an Orthogonal Transform”, InternationalJournal of Image Processing, Vol.4, Issue 4, pp. 444-455, 2010.
- Dr. SangeetaJadhav, “A digital color image watermarking system using blindsource separation”, International Conference on Digital ImageProcessing and Vision, December 2013, pp. 109-116.
- Huming Gao, LiyuanJia, Meiling Liu, “A Digital Watermarking Algorithm for Color Image based on DWT”, TELKOMNIKA, Vol. 11, No. 6,June 2013, pp. 3271- 3278.
- Pooja Malhotra, MeenakshiMoza, JyotiVerma, “ A DWT-SVD Based Watermarking Techniques For Digital Images”, International Journal ofComputational Engineering Research Vol. 03 Issue 6, June 2013, pp. 1-5.
- Ibrahim Alsonosi Nasir, Member, IAENG, Ahmed b. Abdurrman, “A Robust Color Image Watermarking SchemeBased on ImageNormalization”,Proceedings of the World Congress on Engineering 2013 Vol III,July 2013
- A. Umaamaheshvari and K. Thanushkodi, “A robust digital watermarking technique based on feature and transform method”, Academicjournals, Scientific research and essays, vol. 8 (32), pp. 1584-1593.
- K.Chaitanya, E. Sreenivasa Reddy, K.Gangadhara Rao, “Digital Color Image Watermarking using DWTDCT Coefficients in RGB Planes”,Global Journal of Computer Science and Technology Graphics & Vision, Volume 13 Issue 5 Version1.0 Year 2013, pp. 17-21.
- Shahin Shaikh, ManjushaDeshmukh, “Digital Image Watermarking In DCT Domain”, International Journal of Emerging Technology andAdvanced Engineering, Volume 3, Issue 4, April 2013, pp.289-293.
- YashovardhanKelkar, Heena Shaikh, Mohd.Imran Khan, “Analysis of Robustness of Hybrid Digital Image Watermarking Technique underVarious Attacks”, International Journal of Computer Science and Mobile Computing Vol.2 Issue. 3, March- 2013,pg. 137-143.
- Gursharanjeet Singh Kalra, Rajneesh Talwar, Harsh Sadawarti, “ Comparative Analysis of Blind Digital Image Watermarking Utilising DualEncryption Technique in Frequency Domains”, World Journal of Computer Application and Technology 1(2), 2013, pp. 35-40.
- RoshanJahan, “Efficient and Secure Digital Image Watermarking Scheme using DWT-SVD and Optimized Genetic Algorithm based ChaoticEncryption”,International Journal of Science Engineering and Technology Research, vol. 2, issue 10, 2013, pp. 1943-1946.
- Ambika Agarwal, Neha bora and Nitin Arora, “Goodput Enhanced Digital Image Watermarking Scheme Based on DWT and SVD”,International Journal of Application or Innovation in Engineering & Management, vol. 2 issue 9, 2013, pp. 36-41.
- Mohd Rizal Mohd Isa and Salem Aljareh, “Biometric Image Protection Based on Discrete Cosine Transform Watermarking Technique”, InIEEE Proc. of International Conference on Engineering and Technology (ICET), 2012 , pp.1-5.
- Jagdish C. Patra, Jiliang E. Phua and DeepuRajan in, “DCT domain watermarking scheme using Chinese remainder theorem (CRT) for imageauthentication”, In IEEE Proc. of ICME, 2010, pp. 111-116.
- DongyangTeng, Renghui Shi, Xiaoqun Zhao proposed the DCT image watermarking technique based on the mix of time-domain, “DCTImage Watermarking Technique Based on the Mix of Time-domain”, In IEEE Proc. of International Conference on Information Theory andInformation Security (ICITIS), 2010, pp. 826-830.
- B.L. Gunjal and R.R.Manthalkar, “Discrete Wavelet Transform based Strongly Robust Watermarking Scheme for Information Hiding inDigital Images”, In IEEE Proc. of 3rd International Conference on Emerging Trends in Engineering and Technology (ICETET),2010, pp. 124-129.
- Gerardo Pineda Betancourth, “Fragile Watermarking Scheme for Image Authentication”, In IEEE Proc. of 5th International Conference onHuman System Interactions, 2012, pp. 168-174.
- Ezz El-Din Hemdan,Nawal El-Fishaw, GamalAttiya, FathiAbd El-Samii,“Hybrid Digital Image Watermarking Technique for Data Hiding”,2013, pp. 220-228.
- Nagaraj V. Dharwadkar, B. B. Amberker&AvijeetGorai, “Non-blind Watermarking scheme for color images in RGB space using DWTSVD”,In Proc. of IEEE Proc. of International Conference on Communications and Signal Processing (ICCSP), 2011, pp. 489-493.
- M.A. Dorairangaswamy, “Protecting Digital-Image Copyrights: A Robust and Blind Watermarking Scheme”,In IEEE Proc. of FirstInternational Conference on Networked Digital Technologies, 2009, pp. 423-428.
- K.C. Liu, C.H. Chou, “Robust and transparent watermarking scheme for colour images”, IET Image Processing, Vol. 3, Issue 4, 2009, pp.228–242.
- Yasunori Ishikawa, Kazutake U ehira and Kazuhisa Yanaka, “Robust Optical Watermarking Technique by Optimizing the Size of PixelBlocks of Orthogonal Transform”, In IEEE Proc. of Industry Applications Society Annual Meeting (IAS), 2011, pp. 1-6.
- H. B. Kekre, TanujaSarode, ShachiNatu, “Performance Comparison of DCT and Walsh Transforms for Watermarking using DWT-SVD”,International Journal of Advanced Computer Science and Applications, Vol. 4, No. 2, 2013, pp. 131-141.
- Dr. H. B. Kekre, Dr. TanujaSarode, ShachiNatu, “Hybrid Watermarking of Colour Images using DCT-Wavelet, DCT and SVD”, InternationalJournal of Advances in Engineering and Technology, vol.6, Issue 2. May 2013.
- Dr. H. B. Kekre, Dr. TanujaSarode, ShachiNatu,“Robust watermarking using Walsh wavelets and SVD”, International Journal of Advances inScience and Technology, Vol. 6, No. 4, May 2013.
- Dr. H. B. Kekre, Dr. TanujaSarode, ShachiNatu,“ Performance Comparison of Wavelets Generated from Four Different OrthogonalTransforms for Watermarking With Various Attacks”, International Journal of Computer and Technology, Vol. 9, No. 3, July 2013, pp. 1139-1152.
|