Keywords
|
| Social network analysis, Interpersonal organization investigation, information mining, informal community protection. |
INTRODUCTION
|
| Social Networks are online applications that allow their customers to interface by strategy for distinctive association sorts. As a real part of their offerings, these frameworks license people to once-over bits of knowledge about themselves that are essential to the method for the framework. For example, Facebook is a general-use interpersonal association, so solitary customers list their most cherished activities, books, and films. Then again, LinkedIn is a master framework; because of this, customer’s subtle element inconspicuous components which are related to their master life (i.e., reference letters, past occupation, and so on.) In light of the way that these districts gather wide individual information, interpersonal association application suppliers have an exceptional open entryway: quick use of this information could be important to patrons for prompt advancing. |
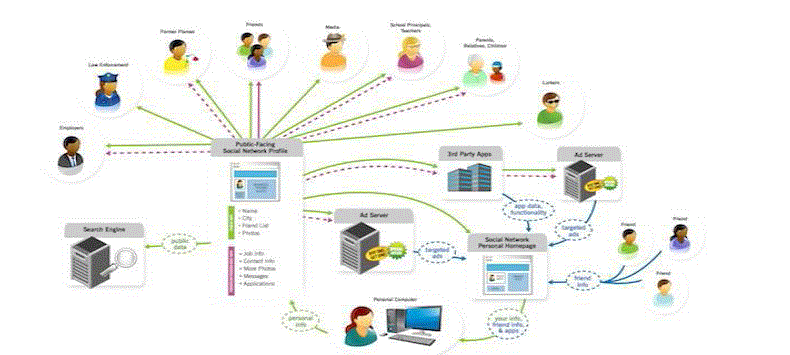
| Of course, in practice, insurance concerns can keep these tries. This conflict between the fancied use of data and individual security presents an opportunity for insurance sparing Informal communities data mining—that is, the divulgence of information and associations from Interpersonal organizations data without misusing security. Security concerns of people in a Social Networks in Fig 1 can be grouped into two classifications: assurance after data release, and private information spillage. Instances of security after data release incorporate the ID of specific individuals in data set subsequent to its release to the general populace or to paying customers for a specific utilization. Possibly the most illustrative specimen of this kind of security burst (and the repercussions thereof) is the AOL looks for data insult. |
| Private information spillage, then again, is related to bits of knowledge around an individual that are not unequivocally communicated, in any case, rather, are accumulated through diverse purposes of investment released and/or associations with individuals who may express that detail. A frivolous representation of this kind of information spillage is a circumstance where a customer, says John, does not enter his political partnership because of security concerns. Nevertheless, it is unreservedly open that he is a piece of the "approve the same sex marriage." Utilizing this straightforwardly accessible data as for a general social affair interest, it is smoothly guessable what John's political association is. To a degree more unobtrusive is the most cherished film " The End of the Spear.1" It message that this is an problem both in live information (i.e., starting now on the server) and in any released data. In Interpersonal organizations data mining, it explore two cases in which customers inside an interpersonal association may need to guarantee their security. |
| A. Our Contributions |
| In order to secure protection, we clean both subtle elements and the hidden connection structure of the chart. That is, we erase some data from a client's profile and evacuate a few connections between companions. We additionally analyze the impacts of summing up subtle element qualities to more bland qualities. We then study the impact these strategies have on battling conceivable derivation assaults and how they may be utilized to guide sterilization. We further demonstrate that this disinfection still permits the utilization of other information in the framework for further assignments. Also, we talk about the idea of "flawless security" in interpersonal organizations and give a formal protection definition that is appropriate to derivation assaults examined in this paper. |
| B. Overview |
| The rest of this paper is composed as takes after: In Section 2, we depict past work in the region of informal community anonymization. In Section 3, we display our definition for protection and also portray the strategies that we created to anonymize informal organization information. In Section 4, We give a general diagram of the speculation handle in Algorithm. In Section 5, we depict our analyses and the results we acquired. In Section 6, we propose some conceivable future work here. |
RELATED WORK
|
| In this paper, we touch on numerous regions of research that have been intensely examined. The zone of security inside an interpersonal organization includes a vast broadness, in light of how protection is characterized. In [5], Backstrom et al. consider an assault against an anonymized system. In their model, the system comprises of just hubs and edges. Subtle element qualities are excluded. The objective of the aggressor is just to distinguish individuals. Further, their issue is altogether different than the one considered in this paper on the grounds that they overlook subtle elements and don't consider the impact of the presence of points of interest on privacy.hay et al. [6] and Liu and Terzi [7] consider a few methods for anonymizing informal communities. Nonetheless, our work concentrates on deriving subtle elements from hubs in the system, not independently recognizing people. |
| Different papers have attempted to construe private data inside informal communities. In [8], He et al. consider approaches to derive private data through fellowship connects by making a Bayesian system from the connections inside an interpersonal organization. While they creep a genuine interpersonal organization, Live Journal, they utilize speculative credits to break down their learning calculation. Likewise, contrasted with [8], we give methods that can help with picking the best subtle elements or connections that need to be uprooted for securing protection. At last, we investigate the impact of aggregate derivation systems in conceivable induction assaults. In [9], Zheleva and Getoor propose a few techniques for social diagram anonymization, concentrating essentially on the thought that by anonymizing both the hubs in the gathering and the connection structure, that one subsequently anonymizes the chart in general. Nonetheless, their techniques all concentrate on obscurity in the structure itself. Case in point, through the utilization of k- namelessness or t-closeness, contingent upon the semi identifiers which are picked, a significant part of the uniqueness in the information may be lost. Through our technique for obscurity conservation, we keep up the full uniqueness in every hub, which permits more data in the information postrelease. |
PROPOSED ALGORITHM
|
| Recently created differential security definition [12] gives intriguing hypothetical sureties. Essentially, it promises that the after effect of a differential private algorithm are very much alike with or without the information of any single client. As it were, differentially protection ensures that the change in one record, does not change the result excessively. Then again, this definition does not secure against the building of a precise information mining model that can foresee touchy data. Really a lot of people differentially private information mining calculations have been produced [13] that has comparable exactness to non differentially private variants. Since our objective is to discharge rich informal community information set while forestalling touchy point of interest exposure through information mining systems, differential protection definition is not straightforwardly material in our situation. |
| A. Formal Privacy Definition |
| The above protection definition could be connected to different areas. Consider the situation where we need to choose whether to discharge some private data (e.g., dietary patterns, way of life), and joined with some open data (e.g., age, postal district, reason for death of progenitors) or not. We may be concerned that whether the revealed data could be utilized to manufacture an information mining model to anticipate the probability of an individual getting an Alzheimer's sickness. Most people would consider such data to be delicate for instance, when seeking wellbeing protection or work. Our security definition could be utilized to choose whether to unveil the information set or not because of potential surmising issues. |
| B. Manipulating Details |
| Clearly, points of interest can be controlled in three ways: adding subtle elements to hubs, changing existing subtle elements and expelling subtle elements from hubs. In any case, we can comprehensively order these three routines into two classifications: bother and anonymization. Including and adjusting points of interest can both be viewed as systems for annoyance that is, presenting different sorts of "clamor" into D to decline order exactnesses. Uprooting hubs, notwithstanding, can be viewed as an anonymization strategy. |
| C. Manipulating Link Information |
| Obviously, subtle elements can be controlled in three ways: adding points of interest to hubs, changing existing points of interest and expelling points of interest from hubs. On the other hand, we can comprehensively characterize these three strategies into two classifications: bother and anonymization. Including and altering subtle elements can both be viewed as routines for bother that is, presenting different sorts of "clamor" into D to abatement order correctnesses. Uprooting hubs, be that as it may, can be viewed as an anonymization system. |
PSEUDO CODE
|
| Algorithm Generalize( Ω,G) |
| Step 1: G1 ← G |
| Step 2: while Classify(G) - Classify( G1) <= Ω do |
| Step 3: S ← all details that can be further generalized |
| Step 4: s ← getHighestInfoGainAttrib(S) |
| Step 5: Gen(s; G1) |
| Step 6: end while |
| Step 7: return G1 |
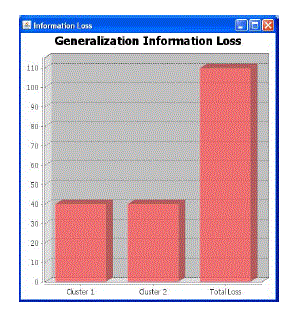
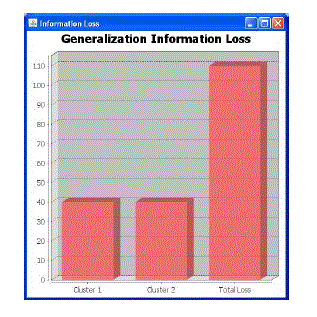
| We give a general layout of the speculation prepare in Algorithm 1. At each one stage, we sum up each one point of interest sort by one level [lines 3-5] by figuring out which qualities can be further summed up without complete evacuation and keep a rundown of the exactness of this speculation. Toward the end of each round, we "forever" store the individual point of interest sort that gives the best security reserve funds [line 4]. At the point when the changed chart, G1, meets the picked security prerequisite, we think of it as prepared for discharge. |
SIMULATION RESULTS
|
| A. Data Gathering |
| We composed a project to creep the Facebook system to assemble information for our investigations. Written in Java 1.6, the crawler stacked a profile, parsed the subtle elements out of the HTML, and put away the points of interest inside a Mysql database. At that point, the crawler stacked all companions of the current profile and put away the companions inside the database both as companion boat joins and as could be allowed profiles to later slither. On account of the sheer size of Facebook's informal organization, the crawler was constrained to just slithering profiles inside the Dallas/Forward Worth (DFW) system. This implies that if two individuals impart a typical companion that is outside the DFW system, this is not reflected inside the database. Additionally, some individuals have empowered protection confinements on their profile which kept the crawler from seeing their profile points of interest. The aggregate time for the slither was seven days. |
| Since the information inside a Facebook profile is free structure content, it is basic that the info be standardized. For instance, most loved books of "Holy book" and "The Spiritual text" ought to be viewed as the same subtle element. Further, there are frequently spelling missteps or varieties on the same thing. The standardization system we utilize is based upon a Watchman stemmer introduced in [14]. To standardize a point of interest, it was broken into words and each one saying was stemmed with a Doorman stemmer then recombined. Two points of interest that standardized to the same worth were viewed as the same for the reasons of the learning calculation. Our aggregate creep brought about in excess of 167,000 profiles, very nearly 4.5million profile subtle elements, and in excess of 3million friendshiplinks. In the diagram representation, we had one substantial focal gathering of associated hubs that had a most extreme way length of 16. Just 22 of the gathered clients were not inside this gathering. |
| B. Experimental Setup |
| In our experiments, We characterize two arrangement assignments. The primary is that we wish to figure out if an individual is politically "progressive" or "liberal." The second characterization undertaking is to figure out if an individual is "hetero" or "gay person." It is paramount to note that we consider people who would likewise be viewed as "androgynous" as "gay person" for this test. We start by pruning the aggregate diagram of 160,000 hubs down to just those hubs for which we have a recorded political association or sexual introduction to have sensible tests for the exactness of our classifiers and the effect of our purification. This decreases our general set size to 35,000 hubs for our political alliance tests and to 69,000 hubs for our sexual introduction tests. We then lead an arrangement of analyses where we uproot various subtle elements and a different arrangement of examinations where we evacuate various connections. We direct these evacuating up to 20 points of interest and connections, individually. |
| C. Detail Removal |
| As can be seen from the results, our systems are by and large effective at diminishing the precision of grouping errands. Fig.1shows that evacuating the subtle elements most profoundly associated with a class is precise over the points of interest and normal classifiers. Nonsensically, maybe, is that the precision of our connections classifier is likewise diminished as we evacuate points of interest. Then again, as examined in Area 4.4, the subtle elements of two hubs are contrasted with discover a likeness. As we expel points of interest from the system, the set of "comparative" hubs to any given hub will likewise change. This can represent the lessening in precision of the connections classifier. |
| Additionally, we see that in Fig. 2a there is a serious drop in the arrangement precision after the evacuation of a solitary subtle element. In any case, when taking a gander at the information, this can be clarified by the evacuation of a detail that is extremely characteristic of the "moderate" class esteem. When we uproot this detail, the likelihood of being "traditionalist" definitely diminishes, which prompts a higher number of inaccurate groupings. When we evacuate the second detail, which has a comparative probability for the "Liberal" grouping, then the class esteem probabilities start to pattern descending at a much smoother rate. |
| While we don't see this conduct in Fig. 2b, we do see an a great deal more unstable grouping exactness. This seems, by all accounts, to be as a consequence of the more extensive class size uniqueness in the basic information. Since more or less 95 percent of the accessible hubs are "hetero" and there are not subtle elements that are as exceptionally characteristic of sexual introduction as there are of political connection, even minor changes can influence the characterization exactness in unusual ways. For example, when we uproot five subtle elements, we have brought down the characterization precision, yet for the sixth and seventh points of interest, we see an increment in order exactness. At that point, we again see an alternate decline in precision when we evacuate the eighth subtle element. |
| D. Link Removal |
| As seen in Figs. 2c , when we evacuate joins, we have a by and large more steady descending pattern, with just a couple of special cases in the "political connection" tests. |
| E. Combined Removal |
| While each one measure gives a decline in grouping exactness, we additionally test what happens in our information set in the event that we evacuate both subtle elements and connections. To do this, we direct further tests where we test order precision in the wake of uprooting 0 points of interest and 0 connections (the gauge exactness), 0 subtle elements and 10 connections, 10 subtle elements and 0 connections, and 10 points of interest and 10 connections. We pick these numbers on the grounds that in the wake of uprooting 12 connections, we observed that we were starting to make various segregated gatherings of few hubs or single, separated hubs. Furthermore, when we evacuated 13 points of interest, 44 percent of our "political association" information set and 33 percent of our "sexual introduction" information set had less than four subtle elements remaining. Since some piece of our objective was to keep up utility after a potential information discharge, we decided to evacuate less subtle elements and connections to help this. |
| We allude to these sets as 0 points of interest, 0 connections; 10 subtle elements, 0 connections; 0 points of interest, 10 connections; 10 subtle elements, 10 connections evacuated, separately. Emulating this, we need to gage the exactness of the classifiers for different proportions of named versus unlabeled diagrams. To do this, we gather a rundown of the majority of the accessible hubs, as talked about above. We then get an irregular stage of this rundown utilizing the Java capacity implicit to the accumulations class. Next, we separate the rundown into a test set and a preparation set, in light of the wanted proportion. |
| F. Generalization Experiments |
| Each one subtle element can be categorized as one of a few classes: religion, political connection, exercises, books, music, citations, shows/films, and gatherings. Because of the absence of a dependable subject power, that is, a source who could authoritatively classify a given citation without extra human info, citations were disposed of from all examinations. To produce the DGH for every action, book, and show/film, we utilized Google registries. To produce the DVD for Music, we utilized the Last.fm labeling framework. To produce the chain of command for Gatherings, we utilized the order criteria from the Facebook page of that gathering. |
| G. Effect of Sanitization on Other Attack Techniques |
| We further test the evacuation of subtle elements as an anonymization method by utilizing a mixed bag of distinctive arrangement calculations to test the viability of our system. For each one number of subtle elements uprooted, we started by evacuating the showed number of points of interest as per the technique as portrayed in Area 4. We then performed tenfold cross approval on this set 100 times, and conduct this for 0-20 subtle elements evacuated. The consequences of these tests are indicated in Figs. 3a and 3b. As can be seen from these figures, our strategy is viable at lessening the order of systems for those subtle elements which we have delegated touchy. |
| While the particular precision lessening is fluctuated by the quantity of subtle elements uprooted and by the particular calculation utilized for characterization, we see that we do truth be told decrease the exactness over a wide scope of classifiers. We see that direct relapse is influenced the slightest, with roughly a 10 percent decrease in exactness. Additionally that choice trees are influenced the most, with an approximately 35 percent diminishment in grouping precision. This shows that by utilizing a Bayesian classifier to perform purification, which makes it simpler to distinguish the individual points of interest that make a class mark more probable, we can diminish the precision of a far bigger set of classifiers. |
CONCLUSION AND FUTURE WORK
|
| The diverse issues related to private information spillage in interpersonal associations. It exhibit that using both relationship associations and purposes of investment together gives preferred suspect limit over inconspicuous components alone. In like manner, it examined the effect of removing purposes of investment and associations in expecting sensitive information spillage. All the while, it discovered circumstances in which total inference does not improve using a fundamental close-by game plan framework to recognize centres. When it join the results from the aggregate affecting ramifications with the individual results, it start to see that discharging unpretentious segments and kinship interfaces together is the absolute best technique to decrease classifier precision. This is likely infeasible in keeping up the use of interpersonal associations. Then again, it moreover exhibit that by clearing simply purposes of investment, it hugely diminish the accuracy of adjacent classifiers, which accommodate us the most great precision that it had the limit accomplish through any mix of classifiers. |
| It in like manner acknowledged full use of the outline information when picking which purposes of enthusiasm to conceal. Accommodating examination may be conceivable on how individuals with confined access to the framework could pick which unobtrusive components to stow away. Similarly, future work could be regulated in perceiving key centre points of the chart structure to check whether removing or modifying these centers can lessen information spillage. |
Figures at a glance
|
 |
 |
 |
| Figure 1 |
Figure 2a |
Figure 2b |
 |
 |
 |
| Figure 2c |
Figure 3a |
Figure 3b |
|
| |
References
|
- Raymond, H., Murat, K., and Bhavani, T., “Preventing Private Information Inference Attacks on Social Networks”, IEEE Transactions on Knowledge and Data Engineering, Vol. 25, pp.8-18, 2013.
- Facebook Beacon, 2007.
- Zeller, T., “AOL Executive Quits After Posting of Search Data,” The New York Times, No. 22, http://www.nytimes.com /2006/08/22/ technology/22iht-aol.2558731.html?pagewanted=all&_r=0, 2006.
- Heussner,K.M., “Gaydar’ n Facebook: Can Your Friends Reveal Sexual Orientation?” ABC News,http://abcnews.go.com/Technology /gaydarfacebook- friends/story?id=8633224#. UZ939UqheOs, 2009.
- Johnson, C., “Project Gaydar,” The Boston Globe, 2009.
- Backstrom, L., Dwork, C. and Kleinberg, J., “Wherefore Art Thou r3579x?:Anonymized Social Networks, Hidden Patterns, and Structural Steganography,” Proc. 16th Int’l Conf. World Wide Web (WWW ’07), pp. 181-190, 2007.
- Hay, M., Miklau, G., Jensen, D., Weis, P. and Srivastava, S., “Anonymizing Social Networks,” Technical Report 07-19, Univ. of Massachusetts Amherst, 2007.
- Liu, K., and Terzi, E., “Towards Identity Anonymization on Graphs,” Proc. ACM SIGMOD Int’l Conf. Management of Data (SIGMOD ’08), pp. 93-106, 2008.
- He, J., Chu, W., and Liu, V., “Inferring Privacy Information from Social Networks,” Proc. Intelligence and Security Informatics, 2006.
- Zheleva, E., and Getoor, L., “Preserving the Privacy of Sensitive Relationships in Graph Data,” Proc. First ACM SIGKDD Int’l Conf. Privacy, Security, and Trust in KDD, pp. 153-171, 2008.
- Gross, R., Acquisti, A. and Heinz, J.H.,“Information Revelation and Privacy in Online Social Networks,” Proc. ACM Workshop Privacy in the Electronic Soc. (WPES ’05), pp. 71-80, http:// dx.doi.org/10.1145/1102199.1102214, 2005.
- Jones, H., and Soltren, J.H., “Facebook: Threats to Privacy,” technical report, Massachusetts Inst. of Technology, 2005.
- Sen, P., and Getoor, L., “Link-Based Classification,” Technical Report CS-TR-4858, Univ. of Maryland, Feb. 2007.
- Tasker, B., Abbeel, P., and Daphne, K., “Discriminative Probabilistic Models for Relational Data,” Proc. 18th Ann. Conf. Uncertainty in Artificial Intelligence (UAI ’02), pp. 485-492, 2002.
- Menon, A., and Elkan, C., “Predicting Labels for Dyadic Data,”Data Mining and Knowledge Discovery, vol. 21, pp.327-343,2010.
|