ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
Roopali Garg1, Himika Sharma2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
In Sybil attack, attackers use several identities at a time or they take-off identity of some trustworthy node present in the network. This attack can create lots of misinterpretation in the network like decrease the trust of legitimate node by using their identities, disturbs the routing of packets so that they cannot reach to its desired destination, and many more. Like this it disturb the communication among the nodes present in the network. Sybil attack is very much destructive for mobile ad-hoc network. In this research, we implemented the Lightweight Sybil Attack Detection technique which is used to detect the Sybil nodes in the network and also discussed the proposed work with implementation which is used to improve the existing Lightweight technique. Simulation tool used for the implementation is MATLAB.
Keywords |
| MANET: Mobile Ad hoc Network, DCA: Distributed Certificate authority, RSS: Received Signal Strength, UB: Upper bound |
INTRODUCTION |
| MANET is an autonomous system consists of numerous nodes. These nodes communicate with each other through wireless links. Due to infrastructure less nature of MANET and as there is no central authority to maintain and control the network makes it vulnerable to various attacks. There is an attack which causes so much destruction to a network called Sybil attack [1] [2]. In Sybil attack attackers spoof the identities of other nodes or create its own identity. Like this it creates false relation with other nodes and decreases the trust of legitimate nodes present in the network. It does not allow the packets to reach its destination, misuse the information which it get from legitimate nodes and many more damages which it cause to a network. It has a great effect on normal functioning of the network. So it is very much necessary to eradicate this attack from the network. |
| There are some security goals to check whether MANET is safe or not [3]. These are discussed following: |
| 1. Availability: It means all services should be provided to all nodes at proper time. So that they can do secure communication with other nodes present in the network. |
| 2. Confidentiality: Some important data is only accessed by authorized authorities. This can protect the nondisclosure data from attackers. |
| 3. Integrity: It provides the assurance that data which is transferred from sender to receiver will not be degraded. Receiver receives the same data as it is send by the sender without any modifications. |
| 4. Non repudiation: In this, receivers and senders do not refuse that they didn’t get or delivered the data. |
| 5. Authentication: This goal is used to check that participants or nodes which are performing or participating in a network are authenticated or fake. |
RELATED WORK |
| Security is important part of any network. If there is security then only there is secure communication and good output of network. The work done to remove Sybil attack in MANET is following: |
| Piro et al. [4] proposed a scheme to detect the Sybil nodes by examine the behaviour of nodes. According to this scheme, the nodes which move freely, independently in different directions are considered as legitimate nodes and the nodes which moves together are suspected as Sybil nodes and it keeps observing these suspected nodes. This scheme gives high false positives results when group of nodes move in same direction. In [4] [5] two approaches are discussed to detect the Sybil attacks. First is proactive approach which includes economic incentives [6] [7] and pre key distribution [8] [9] techniques. Second is reactive approach which is based on testing of resources and location of nodes. |
| J. Newsome et al. [10] proposed a scheme in which radio resource testing and randomly pre key distribution is done to detect the Sybil nodes. |
| In [11] [12] authors proposed DCA scheme. In this scheme, certificates are distributed to all nodes present in the network and nodes use these certificates as a proof of their identities. It helps to prevent the Sybil attacks.AthichartTangpong et al. [13] proposed a technique known as Robust Sybil attack detection technique. In this technique the behaviour of the nodes are examined. The nodes having the similar path are detected as the Sybil nodes.Hongbo Zhou [14] proposed a secure prophet address allocation scheme. In this scheme unique address is distributed to all nodes present in the network. If some new node enters a network, then unique address is provided to that node which does not match with address of any node present in the network. This helps to prevent the Sybil attack. |
LIGHTWEIGHT SYBIL ATTACK DETECTION TECHNIQUE |
| This technique is known as lightweight as it does not use any extra hardware or antennae for its implementation. It is used to detect Sybil Attacks [15]. |
| It includes three steps: |
| 1) Types of Sybil nodes: There are two types of Sybil nodes. In first type it simultaneously use many identities at a time either by spoofing others identities or by creating its own identities. In second type it uses one identity at a time. |
| 2) Threshold value: In this authors supposed that normal nodes do not have speed greater than 10m/s. The nodes whose speed is greater than 10m/s are detected as Sybil nodes. |
| 3) Comparison: In this RSS (Received Signal Strength) upper bound threshold value is calculated. The upper bound value is calculated as average of RSS value when nodes are moving at 10m/s speed. When new node enters in a network then its RSS value is compared with RSS upper bound value, if it is greater or equal to upper bound RSS value then it is detected as Sybil node. |
| Algorithm 1: |
| 1) Set Threshold Value of Speed = 10m/s. |
| 2) Calculate RSS UB_THRESHOLD value |
| 3) Address of the node is checked in table. |
| 4) Node address is not present in table |
| THEN |
| If RSS (node)>= RSS UB_THRESHOLD |
| { |
| Add it into malicious list |
| } |
| Else |
| { |
| Add its address in table of legitimate nodes |
| } |
| End |
| In Algorithm1, First of all network is created which consists of nodes. Then the threshold value of speed is set to 10m/s. The nodes moving with speed greater than 10m/s are considered as Sybil nodes otherwise as legitimate nodes. After this RSS upper bound threshold value is calculated and it is calculated by taking average of RSS values of nodes which are moving at speed of 10m/s. When some node enters in a network then its address is checked in the table that whether it is present in the table or not. If it is not present in the table then its RSS value is compared against RSS upper bound value. If its RSS value is greater or equal to upper bound value then it is considered as Sybil node otherwise as legitimate node. |
PROPOSED LIGHTWEIGHT SYBIL ATTACK DETECTION TECHNIQUE |
| It is the improved version of Lightweight Sybil Attack detection technique. In above lightweight technique, sometimes there is Sybil nodes whose speed is less than 10m/s and these nodes are detected as legitimate nodes. To remove this drawback of above technique, it is modified. In above lightweight technique only one parameter is used i.e. speed. Here we added two more parameter i.e. energy and frequency. By using these two parameters it is giving better results than previous. In this threshold value of speed is taken as same i.e.10m/s and threshold value of energy and frequency are set as average energy of network and average frequency of network. |
| Algorithm 2: |
| 1) Set threshold value of Speed= 10m/s |
| 2) Set threshold value of Energy= avg_energy of network. |
| 3) Set threshold value of Frequency= avg_frequency of network. |
| 4) Node enters in a network. |
| 5) Node address is checked in table. |
| 6) Address is not present in table |
| Then |
| If node speed>= 10 | node energy >=avg_energy of network | node frequency >= avg_frequency of network |
| { |
| Add address of node in malicious list |
| } |
| Else |
| { |
| Add address of node in malicious list |
| } |
| End |
| In Algorithm2 three parameters are taken i.e. Speed, energy and frequency. Threshold value of speed is set to 10m/s whereas threshold value of energy is set to average energy of network and threshold value of frequency is set to average frequency of network. In this, if new node enters a network then its Speed, Energy and frequency value should be less than threshold value, only then that node is considered as legitimate node otherwise as Sybil node. When node enters in a network, firstly it is checked whether its address is present in the table or not. If it is not present in the table then its Speed, Energy and frequency parameters values are checked. And if Speed, Energy and frequency parameters values are less than threshold values then it is considered as legitimate node otherwise as Sybil node. |
RESULT AND DISCUSSION |
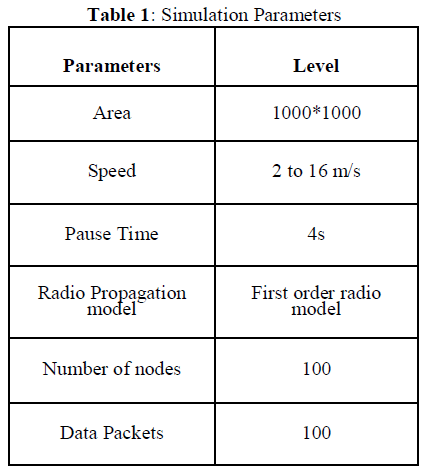
| The simulation tool used for implementation is MATLAB R2010a. In this we implemented the proposed lightweight Sybil attack detection technique i.e.Algorithm2 by using parameters mentioned in Table 1 and also used energy and frequency parameters. |
| Parameters used for performance measurement are following: |
| 1. Throughput: It is calculated as ratio of delivered packets to total number of sent packets. |
| 2. BER (Bit error rate): BER is calculated as number of bit errors divided by total number of bits sends by sender. |
 |
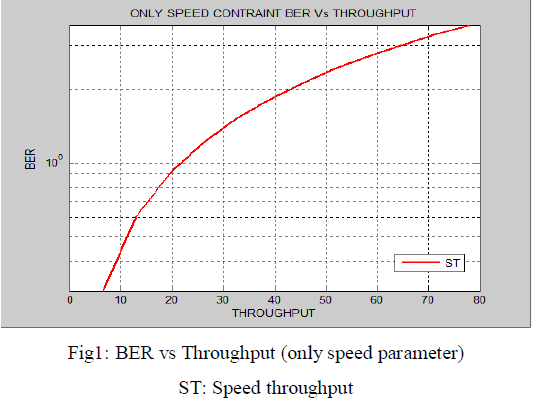 |
| In Fig1 graph is plot between BER vs Throughput, when only speed parameter is used. Threshold value of speed parameter is set to 10m/s.When BER= 100.5599 then throughput is coming 78.22. |
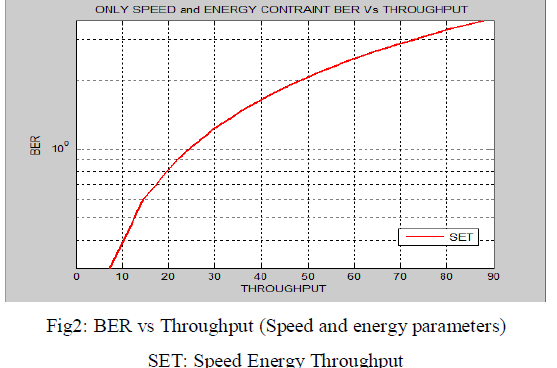 |
| In Fig2 graph is plot between BER vs Throughput when two parameters are used i.e. Speed and energy. Threshold value of speed is set to 10m/s and of energy is set to average energy of network. In this graph when BER= 100.5599 then throughput= 88.12. By using one more parameter i.e. energy, performance or throughput is improved by 12.65% with respect to fig 1 in which only speed parameter is used. |
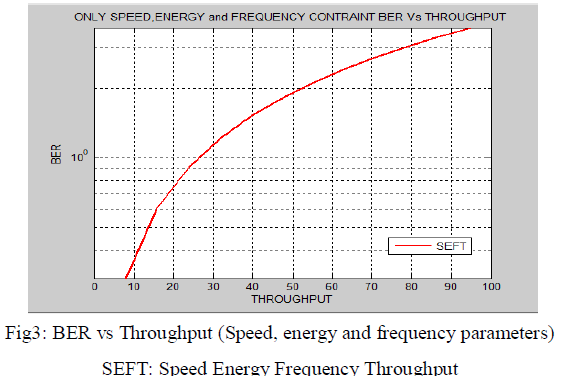 |
| In Fig3 graph is plot between BER vs throughput when three parameters are taken i.e. speed, energy and frequency.In this, when BER is 100.5599 then throughput is coming 95.05. When three parameters are used then performance is improved by 21% with respect to Lightweight Sybil attack technique where only one parameter is used i.e. speed.It shows that by increasing the constraints i.e. parameters, the number of malicious nodes decreasein the network. As a result network security increases. |
CONCLUSION |
| In lightweight Sybil attack detection technique only one parameter speed is used to detect the malicious node but sometimes there is Sybil nodes whose speed is less than 10m/s are also detected as legitimate nodes. To provide more security, technique is proposed in which two more parameters are used i.e. energy and frequency. In proposed technique when node enters a network, then it’s all three parameters are checked i.e. speed, energy and frequency and if value of all these parameters are less than threshold value then node is considered as legitimate node otherwise as Sybil node. It improves the performance or throughput of network by 21% than lightweight Sybil attack detection technique. |
References |
|