ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
Ashwini W. Nagpurkar 1, Siddhant K. Jaiswal 2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
The integration of Wireless Sensor Network (WSN) and Radio Frequency Identification (RFID) is an emerging technology which utilizes identified advantages of both systems making it more efficient and reliable. The Hybrid network formed by integration of WSN and RFID systems provide excellent infrastructure to process, acquire and distribute data in decentralized dynamic environments. The integrated network involves various challenges among which redundant data is critical as it is coupled with time delay and energy consumption which results in waste of various network resources. In this paper redundant data issue is taken into consideration and it is eliminated further to improvise the performance of the Hybrid network. Redundant data cleaning is discussed in detail along with its effects on system. An algorithm is proposed to overcome redundant data problem which performs efficient redundant data filtration. Proposed algorithm is compared with previous available technique. Simulation results show that the proposed algorithm reduces data redundancy maintaining the integrity of original data.
KEYWORDS |
| Redundant data, Data filtering, Integration, Radio Frequency Identification (RFID), Wireless Sensor Network (WSN). |
I. INTRODUCTION |
| Wireless Sensor Network (WSN) and Radio Frequency Identification (RFID) has received great attention due to their phenomenal advances in very large integrated systems, micro-electro-mechanical systems and highly integrated low power digital electronics. They are emerging as the most ubiquitous computing technology due their broad applicability and various noteworthy advantages [2]. The evolution of WSNs and RFID has followed separate development and research path which has led to distinct technologies. |
| WSN is a network consisting of a Sink Node also known as base station and a number of small, light weight and wireless nodes called sensor nodes. These sensor nodes sense the environmental conditions like temperature, humidity, pressure, light, sound, and vibration and accordingly collect the information [3]. The sensor nodes has computational capabilities allowing processing of collected information. This collaboratively collected and processed information is further transmitted to the base station. WSNs provide cost effective monitoring of critical applications including border monitoring, industrial control, military, environmental monitoring and healthcare application [4]. In contrast RFID technology enables detection and identification of an object. An RFID network consists of readers and tags. A tag consisting of a chip and an antenna is incorporated on a target object. A reader obtains information by scanning these tags and accordingly transmits information to the server. General applications of an RFID systems are supply chain management, highway toll collection, controlling building access, public transportation, developing smart home appliances, animal tracking etc [4]. |
| RFID technology is been extensively adopted in industrial applications and on the other hand, sensor networks found important applications in harsh environment conditions. Nevertheless, there are many applications where information retrieved by sensing environmental conditions is not sufficient and additional information like identity or the location of an object is important [3]. Though sensor networks can be used in these environments as well, but the location and identity of an object still remain critical. In these cases, integration of both WSN and RFID technologies is the optimal solution as they complement each other. The integration of RFID and WSNs maximizes their effectiveness and give innovative perspectives to a broad range of applications [4]. |
| The Hybrid network formed by integration of WSN and RFID networks has various identified challenges viz. energy conservation, data cleaning and filtering, real-time performance, anti-collision, localization, and authentication [5]. Among all above challenges, Data cleaning and filtering is important to circumvent inefficient utilization of network resources [6]. In an RFID network, a reader interrogates tags multiple times to increase the observed read rate due to which several copies are attached to single object. Also the sensor nodes and RFID tags are densely deployed in an area of interest in order to cover each and every section of area under observation. This results in data redundancy as some sections of area are covered by more than one device node. Redundant data is nothing but repeated readings or duplicate copies of reading. The filtration of this redundant data is essential as it does not provide any useful information but unnecessarily consumes valuable resources. The process of removing redundant information from gathered information is known as data cleaning. More precisely, redundant data cleaning is a process of modifying, replacing or deleting the inaccurate, incorrect or irrelevant part of data [7]. |
| The remainder of this paper is as follows. Section II consists of related work. Section III provides a brief idea about the architecture used for evaluating the performance of proposed scheme. Section IV deals with a detailed description of proposed technique. Simulation result performance analysis is provided in Section V and finally Section VI concludes the paper. |
II. RELATED WORK |
| Shawn R. Jeffery in [8] addressed various shortcomings of static smoothing filters to correct missed readings and proposed SMURF algorithm which employs adaptive smoothing scheme for RFID data filtration. It is the first declarative algorithm and act as adaptive smoothing filter for data cleaning. SMURF aims at two cleaning mechanism viz; Per tag cleaning and Multi tag cleaning. As SMURF is an adaptive smoothing scheme, there is no need to set the window size as it adjusts its size automatically considering the characteristic of data streams. In order to adapt window size automatically, the algorithm should be able to differentiate between tag movement and dropped reading. A statistical sampling-based approach is used by SMURF to achieve above goal and thus produces accurate data streams with appropriate balance between tag motion and missed reading. |
| Extensible receptor Stream Processing (ESP) proposed by Shawn R. Jeffery [9] is a declarative query based framework. It is designed to clean data streams produced in sensor network. ESP is a pipeline framework for data processing which cleans data of receptor data streams online.ESP organizes the receptor data stream into five stages: Point - Smooth - Merge - Arbitrate - Virtualize. It exploits spatial and temporal aspects of receptor data streams by processing multiple receptor streams and produces more enhanced and accurate data stream. ESP provides considerable development over raw sensor data and accurately reflects the physical world. |
| In [6] EIFS i.e. Energy Efficient In-Network RFID Data Filtering Scheme proposed by Dong-Hyun Lee, redundant data is divided into two types: inter-cluster and intra-cluster cases. The type of RFID data packet received by the cluster head is decided from its f field. The sender is an intra cluster node if the value of f is 1and cluster head should carry out data filtering. After data cleaning the field f is set to 0.Thus packets with field f 0 will not be filtered again by any cluster head which reduces computation cost. After intra-cluster filtering, CHs send their data towards sink. EIFS algorithm first detects the inter-cluster redundant data and accordingly sends a feedback messages to intermediate nodes which results in reduction in unnecessary transmissions. If a redundancy is detected by a cluster head then through feedback it informs to its intermediate CHs. Then according to the feedback, updation of tag list is carried out. |
| Efficient In-Network Redundancy Filtering EIRF proposed in [10] by Ali Kashif Bashir, make use of hash tables to determine the redundancy in data streams. It also utilizes height-balanced tree to revise the expired chronological data which is faster than previous methods. EIRF has less network delay and processing latency. Barjesh Kochar have proposed a novel data cleaning technique along with data transformation and data loading techniques in [6]. The cleaning is been performed on the basis of the probability of response of the tags and the window size. The window size is enlarged if the strength of the dirty data is low and decreased if it is high in the past window of interrogation. |
| In Improved Cross Redundant Cleaning Algorithm (ICRDC) proposed by Li Wang in [5], a structure called cross tags list (CTL) which consists of tuple queue ensuring inserting and deleting operation needs to be maintained in the memory. Then a verification operation can be carried out to determine whether the tag of waiting arbitration is nearby the reference tags in CTL. If there are no such arbitration tags then Euclidean distance of waiting arbitration tag can be calculated and with minimum relative position method the cross redundant data can be eliminated. If there are some waiting arbitration then based on sliding window mechanism the tuple cache queue in tuple groups can be detected and check for redundancy. This CTL tuple containing redundant data is filtered and thus a reasonable memory can be maintained. |
III. ARCHITECTURE |
| Figure1. shows the architecture of RFID and WSN integrated network. The architecture consists of four types of nodes [11]: |
| ïÃâ÷ Conventional sensor node (CSN) |
| ïÃâ÷ Cluster head sensor node (CH) |
| ïÃâ÷ Sensor tag (ST) |
| ïÃâ÷ Hybrid Sensor node (HSN) |
| Conventional sensor nodes are the most fundamental and simple component of integrated network. CSN are normal sensor nodes which sense physical conditions of the environment and accordingly transfer information to the cluster head (CH). The main role of CSN is to act as relays while providing additional information about the environment [11]. CH nodes are identical to CSN but perform certain additional functions like data aggregation and processing of information. Each sensor cluster contains one CH. |
| A sensor tag (ST) is the node formed by the integration of RFID tag and Sensor. Thus it has sole identity due to RFID tag and sensing capability due to Sensor incorporated in it. There three types of ST, viz. Active, Passive and Semi-active. A Passive sensor tags are used in above architecture which do not utilize battery power for sensing and communication purpose. Another key component is Hybrid Sensor Node (HSN) which is a combination of a sensor node and an RFID reader in one single node. The resultant device can perform: |
| ïÃâ÷ Sensing of environmental conditions. |
| ïÃâ÷ Wireless communication with each other |
| ïÃâ÷ Reading of identification numbers from tagged objects or persons |
| ïÃâ÷ Transmission of this information to the sink or next HSN node. |
| As the integrated network consists of four different types of node, successful communication between them is important. Entire network is divided into clusters. This clustering is achieved by Data Density Correlation Degree Clustering Method. Thus the formation of cluster takes place considering the density of data in particular region. The clusters of Sensor tags and wireless sensor nodes are formed, where a CH is elected. A cluster may or may not contain an HSN. CSN transfer data to its respective CH. The CH aggregates the entire received data along with its own sensed data and forward it to Base Station (BS). The CH can forward data to BS directly or via another CH whichever is more efficient. Sensor tags are located within HSN reading range. The integrated sensor tags form their own clusters and HSN acts as its CH. The role of HSN is similar to CH. The CH and HSN can communicate with each other and they can also act as a relay for each other to transfer information to BS in an efficient manner. |
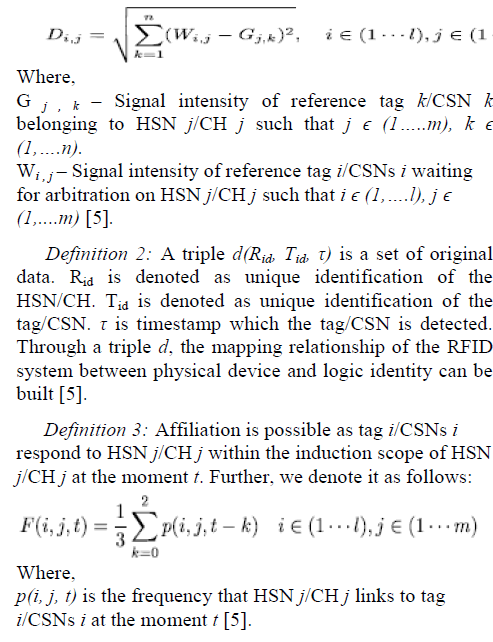
IV. PROPOSED ALGORITHM |
| A. Assumption |
| There are: |
| 1. m Hybrid sensor node (HSN)/cluster head (CH) |
| 2. m × n fixed reference tags/Conventional Censor Nodes |
| 3. l tags/CSNs for arbitration. |
| The attributes of the reference tags/CSNs are known and each HSN/CH can detect and locate reference tags/CSNs in its working area [5]. |
| B. Definitions |
| Definition 1: Di j is the Euclidean distance between the signal intensity of tag i/CSNs i waiting for arbitration on HSN j/CH j and the signal intensity of m reference tags/CSNs of HSN j/CH j. If the value of Di j is small to HSN j/CH j, it more likely will belong to HSN/CH of the tag i / CSNs i: |
 |
 |
| C. Conditions |
| Cross redundant data is produced by some nodes which are located in the same working area. Following conditions are satisfied by cross redundant data: |
 |
V. SIMULATION RESULTS AND PERFORMANCE ANALYSIS |
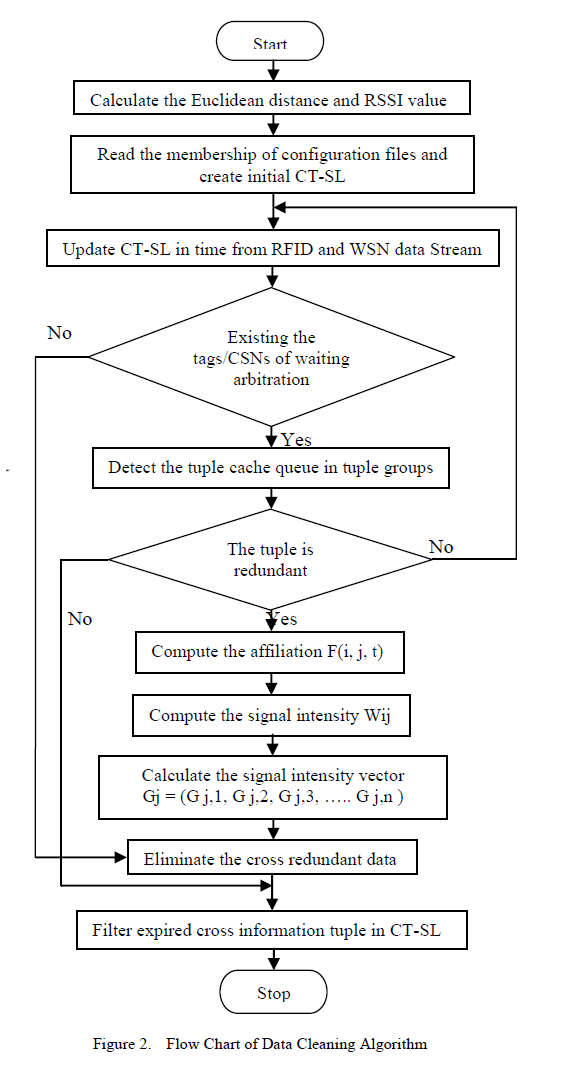
| Modified ICRDC algorithm is similar to ICRDC with minor modifications as follows: |
| 1. First, the HSN and CH calculates the Euclidean distance of each and every node present within its cluster. |
| 2. The RSSI value of every incoming data packet is calculated and only data packets having RSSI value above threshold value are forwarded for further process. |
| 3. The initial CT-SL is formed in accordance to the Euclidean distance of node and it contains data packets having appropriate RSSI value. |
| With these modifications the Modified ICRDC scheme is implemented in Integrated Network and its simulation is carried out in Network Simulator-2 (NS-2). The integrated network is similar to the network developed by researchers in [11] which is described in section III. It consists of total 75 nodes among which some are sensor nodes and some are integrated nodes (refer section III). The performance of the Modified ICRDC algorithm is tested in terms of Compressibility and Accuracy. |
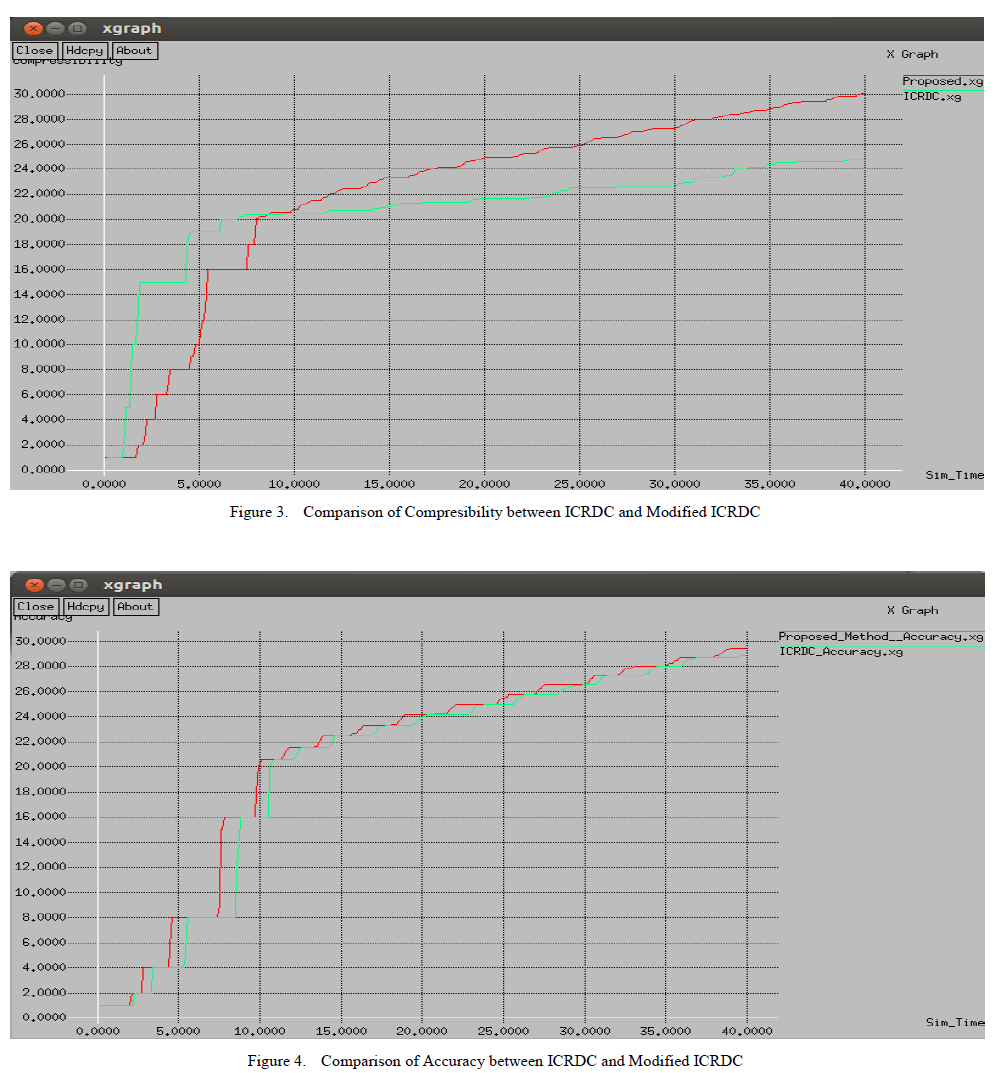
| Figure 3 shows the Compressibility graph plotted against simulation time. The compressibility parameter here denotes the amount of compression achieved in gathered information due to elimination of redundant data. In graph, red line represents the behaviour of proposed scheme and green line indicates ICRDC behaviour in Integrated Network. The generated graph shows that initially, the performance of ICRDC is better than the proposed technique but as the time progresses modified ICRDC continuously overcome ICRDC. This shows that though the ICRDC performs well in the primary stage, the overall performance of Modified ICRDC is superior. |
 |
| Figure 4 shows the comparison between ICRDC and proposed technique in terms of accuracy. Redundant data cleaning is a critical task in a sense since data integrity must be maintained simultaneously with redundancy elimination. For this purpose, the accuracy of redundant data cleaning algorithm is important. The accuracy parameter over here denotes how accurately the data filtering algorithm performs redundant data elimination. In graph, red line indicates the behaviour of proposed scheme and green line shows ICRDC behaviour in Integrated Network. A little improvement is achieved in terms of accuracy as comparison to ICRDC. |
VI. CONCLUSION |
| In this paper, the issue of redundant data in WSN and RFID integrated network is taken into consideration. Redundant Data transmission causes waste of time, energy and other network resources. To overcome this problem a Modified ICRDC technique is proposed which is build upon ICRDC algorithm. Also a brief information is provided about the architecture where the proposed scheme is implemented. Simulation result obtained validates the efficiency of the proposed algorithm. The proposed scheme successfully performs redundant data filtration making integrated network a resource efficient network. |
References |
|