The field of wireless sensor networks has received widespread acceptance because of the ease deployment of nodes, no prior installation of infrastructure before deployment and low cost of operation. This has caused research in WSN to diversify and not only focus on energy conservation but to also look at ways to enhance the data performance of the network. QoS parameters such as reliability, loss, latency and bandwidth are now at the center stage of research. This paper focused on reliability in wireless sensor networks. A survey is performed on existing MAC protocols that provide reliability and they shall be classified according to the nature of the reliability they provide. There are protocols that provide node to node reliability and those that provide end to end reliability. We shall then analyze challenges associated with these existing mechanisms then propose future research directions.
Keywords |
| Wireless Sensor Network; Reliability; MAC Protocols, QoS, Survey |
INTRODUCTION |
| Therehas been a marked increase in the number of applications for wireless sensor networks in recent years. This can
be attributed to factors such as the low cost, no upfront setup in the environment prior to deployment, the ability to be
deployed in adhoc fashion and still manage to communicate without challenges amongst many others. Initial research
was targeted at maximizing the network lifetime whilst trading off factors such as the bandwidth, latency, reliability
and loss. |
| New application are now making demands that have shifted research to other areas such as the data transport
performance. Reliability is one such factor and we are going to discuss in this paper. The MAC layer is the most
important layer in the protocol stack for WSNs because most control mechanisms are implemented in this layer. In
applications where strict data delivery must be enforced mechanisms must be put in place to ensure that data is
delivered in a reliable manner. This paper is going to focus on MAC layer protocols that provide reliability. |
| The remainder of this article is structured as follows: Reliability and classification of reliable protocols are discussed in
section II. Section III discusses approaches taken by various MAC protocols to achieve reliability. In section IV we
highlight challenges faced by existing protocols, identify potential research directions and conclude. |
RELIABILITY IN WSN |
| Reliability is the ability of the WSN to guarantee that the data is always delivered. The time the data is delivered is
not a major concern but the data must always reach the intended recipient. Reliability in WSN is often dealt with in
upper layers such as routing but we can also deal with it in the MAC layer by reducing packet loss [8].The following
factors are the reasons why mechanisms to provide reliability are in place: |
| • Constrained resources |
| • Radio frequency interference |
| • Synchronization |
| The MAC layer has several methods to enforce reliability and the list below gives possible methods that can be used. |
| • Improve the reliability of individual components |
| • Increase the number of paths between the source and destination |
| • Decrease the number of intermediate links |
| • Improve channel quality and remove link errors |
| Reliable MAC protocols can be said to provide two kinds of reliability: node to node reliability and source to
destination reliability. |
| Node to node reliability – in this circumstance the reliability is small scale and it is being enforced between two
adjacent nodes. The protocol can increase the reliability or guarantee the delivery. |
| End to end reliability –the reliability is enforced at a large scale and it is from the source to the destination not only at
two adjacent nodes. The protocol can increase the reliability or guarantee the delivery. |
RELIABLE MAC PROTOCOLS |
| In this section we are going to analyse a number of protocols and explain how they provide reliability. |
Rainbow: Reliable Data Collection MAC for WSN |
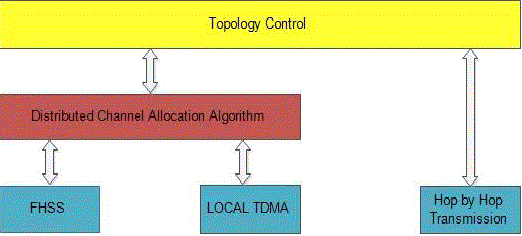
| This increases the Hop to Hop reliability in a WSN that has a tree topology [1]. The MAC layer in Rainbow enhances
the reliability by reducing the radio frequency (RF) interference in the wireless medium. To achieve this it uses a local
TDMA scheme coupled with a frequency-hopping spread spectrum (FHSS). The combination of TDMA and FHSS
control channel access. |
| The FHSS is responsible for reducing collision, increasing throughput and preventing interference. Whenever a
collision occurs the node uses a technique called temporal diversity to change the frequency to ensure that the collision
does not reoccur An Algorithm called PUNCH is used to prevent collisions by allocating exclusive time frequency
channels to each node. |
On-Demand Reliable MAC (RMAC) |
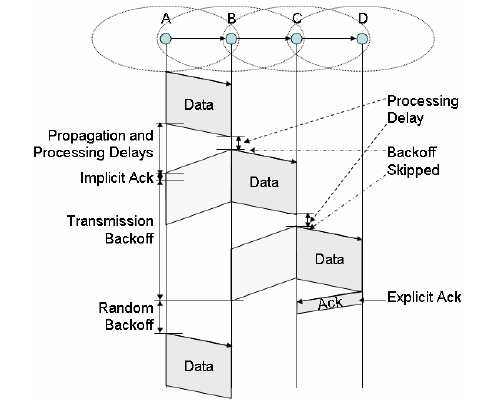
| This is a CSMA/CA bases MAC protocol that increases the node to node reliability [2]. It works in an error prone
medium. To enforce reliability it uses implicit and explicit ACKs. |
| When a node wishes to transmit a packet it first waits for a random back-off to check if the channel is in use. If the
channel is busy it waits again until the channel becomes free. The back-off waiting time is obtained using the formula: |
| RB=[0.2cw * slotTime] (1) |
| On transmission if the message is at an intermediate node the node does not send an ACK to the previous node. The
previous node will receive an implicit ACK when it overhears the node forwarding the message. If it is the destination
node it will send an explicit ACK. In the event that an implicit or explicit ACK is not received retransmission will
occur. The number of retransmissions is proportional to the channel error rate. The formula for calculating
retransmissions is: |
| Retransmission Attempts = TX-ATTEMPS +(1/(1 - Pe)) (2) |
| Where TX-ATTEMPS – maximum number of retransmissions
Pe- Packet error rate |
Energy Efficient On-Demand Reliable MAC (E2RMAC) |
| This is an enhancement of RMAC that introduces energy efficiency by using two radios a wake up radio and a
transmission radio [6]. It also increases the node to node reliability. Reliability in this protocol is also enforced by
implicit and explicit ACKs but the mechanism differs. When an intermediate node receives a message it does not
perform back-off before it accesses the channel it automatically sends a wake up signal to the next node on the wakeup
radio and when the node wakes up it begins transmission. The wakeup signal is an implicit ACK to the sender. |
| When a sender fails to receive an ACK it retransmits the packet after waiting for a back-off period. If the message has
reached the final destination the receiving nodes sends a wakeup tone to the sending node as an explicit ACK. A
mechanism is put in place to prevent collisions between two adjacent nodes that have communicated recently. When a
sender receives an ACK, explicit or implicit it does not transmit for a period that is equal to the time it takes to transmit
a message and receive an ACK. During this time the node will not accept wake up signals. Since the wireless medium is a broadcast medium, nodes around two communicating nodes overhear the communication between the two nodes
setting up communication they sleep for a period that allows communication between these nodes and if they want to
transmit they wake up after this period. |
Adaptive Power Transmission Control (ATPC) |
| This is an algorithm that uses feedback to adjust the power of the signal in order to control the quality of the link [3].
This algorithm increases the node to node reliability. The algorithm considers the spatial and temporal effects of the
environment on the link. Each node has a model for each neighbour that it uses to control the transmission power based
on the link quality. Feedback history between the two nodes is used to establish the model. This history is used to
gauge the transmission power required to ensure better link quality and reliability. |
| The spatial effect of the environment is used to find the minimum power to use to send data maintaining a quality link
using constant factors of that environment such as terrain and the distance between the nodes. The temporal effects are
the sudden changes in the environment that may or may not be permanent but require the transmission power to be
adjusted to maintain a quality link such as weather or the appearance of an obstruction between the two nodes. Any
change in the transmission power is a direct response to changes in the environment. ATPC not only enhances the
reliability of the network but also improves the lifetime of the network because energy is optimally used by the sensor
during transmission. ATPC uses received signal strength indicator (RSSI) and link quality indicator (LQI). RSSI is an
averaged measurement of the signal strength. LQI is the chip error rate. A relationship between link quality and
RSSI/LQI is studied to establish an effective power control mechanism. |
QoS MAC |
| This is a TDMA based MAC protocol that increases the node to node reliability [4]. The nodes are arranged in a tree
topology with the root being the sink node. All the nodes in the tree are synchronized. A time period called an epoch is
the base time unit for this protocol. The epoch is then divided into slots that can be equally divided amongst the
available nodes (k*n slots). Each slot is large enough to transmit data and receive an ACK. The nodes are not randomly
deployed such that slot assignment is preconfigured before the deployment to enforce synchronization. No collisions
will occur in this setup. |
| A node is assigned k successive slots in each epoch. When a node’s slot arrives it must always send a message in its
first transmission slot for that epoch. That message can contain either data meant for another node or a control message
if it has no data to send. A packet will be retransmitted in the node’s next slot in the event that the node has not
received an ACK. |
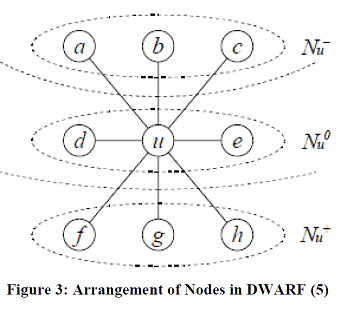
Delay-aware Robust Forwarding for Energy Constrained WSN (DWARF) |
| DWARF increases the end to end reliability. It uses unicast based partial flooding coupled with a greedy node selection
strategy to forward the data towards the sink node [5]. The nodes in DWARF are arranged in a graph structure with
each node having parents, peers and children. Node selection in DWARF is determined by the wake up time and the
relative position with respect to the sink node. |
| In the event that a node wants to transmit an alarm message it has to forward the message k times redundantly to
different nodes to ensure that the message is reliably sent. The nodes that this message is sent to are selected form the
list of parents and the list of peers of the node. The parent list is the first to be chosen from and if it is exhausted before
k is reached nodes will then be chosen from the neighbour list. In each list the node that is chosen is the next node to
wake-up and it is removed from the list after a message has been transmitted to it. If a message is lost during
transmission for any reason the packet is retransmitted to and during this retransmission it is sent to a new destination
to ensure that the message is not delayed because of one node. Each node also sends a status message to its
neighbouring nodes so that they know that it is alive. This status message also contains a list of the nodes that it knows
to be alive. The status message is propagated from the last nodes in the network towards the sink. Each node adds the
nodes it knows to this list and by the time it reaches the sink a list of all the nodes known to be existing is obtained by
the sink node giving it a picture of the network state. |
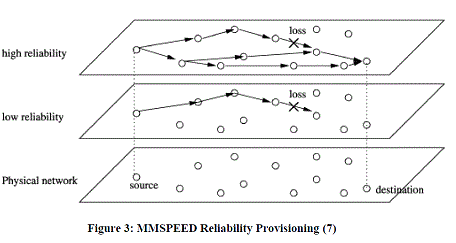
Multipath Multi-SPEED Protocol (MMSPEED) |
| This enforces a probabilistic end to end delivery guarantee [7]. It provides a differentiated reliability guarantee for each
transmission flow. |
| A packet is sent on multiple paths to ensure that it reaches the destination on a lossy and erroneous channel.
MMSPEED increases the number of paths proportionally to the level of reliability required. It uses two techniques to
achieve this |
| • Dynamic compensation |
| • Multipath forwarding |
| A node maintains a link quality metric eijto each neighbour. This metric is used to calculate the end to end reachability. |
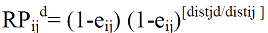 |
| From this reachability we can calculate the number of forwarding paths using |
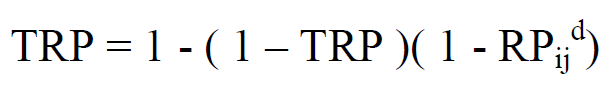 |
CONCLUSION AND FUTURE WORK |
| A lot of research has been carried out on improving the data and transport performance of data in WSN. In this paper
we have analyzed existing MAC protocols and the measures they have put in place to increase reliability. The majority
of the protocols deal with reliability on a node to node basis. For the protocols that deal with reliability on an end to end
basis DWARF increases the end to end reliability and MMPEED provides probabilistic reliability guarantees. There is
still a lot of research that needs to be carried out on end to end reliability because with it we can get source to
destination delivery guarantee. |
| |
Figures at a glance |
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
|
| |
References |
- Yang, Yang, and Weidong Yi. "Rainbow: Reliable data collecting MAC protocol for wireless sensor networks." In Wireless Communications and Networking Conference (WCNC), 2010 IEEE, pp. 1-6, 2010.
- Biswas, Ratnabali, et al. "On-demand reliable medium access in sensor networks." Proceedings of the 2006 International Symposium on World of Wireless, Mobile and Multimedia Networks. IEEE Computer Society, pp. 251-257, 2006.
- Lin, Shan, et al. "ATPC: adaptive transmission power control for wireless sensor networks." Proceedings of the 4th international conference on Embedded networked sensor systems. ACM,pp. 223-236, 2006.
- Suriyachai, Petcharat, UtzRoedig, and Andrew Scott. "Implementation of a MAC protocol for QoS support in wireless sensor networks." Pervasive Computing and Communications, 2009. PerCom 2009. IEEE International Conference on. IEEE,pp. 1-6, 2009.
- Strasser, Mario, et al. "Dwarf: Delay-aware robust forwarding for energy-constrained wireless sensor networks." Distributed Computing in Sensor Systems. Springer Berlin Heidelberg, pp. 64-81, 2007.
- Jain, Vivek, Ratnabali Biswas, and Dharma P. Agrawal. "Energy-efficient and reliable medium access in sensor networks." World of Wireless, Mobile and Multimedia Networks, 2007. WoWMoM 2007. IEEE International Symposium on a. IEEE, pp. 1-8,2007.
- Felemban, Emad, Chang-Gun Lee, and EylemEkici. "MMSPEED: multipath Multi-SPEED protocol for QoS guarantee of reliability and Timeliness in wireless sensor networks." Mobile Computing, IEEE Transactions on 5.6, pp. 738-754, 2006.
- Suriyachai, Petcharat, UtzRoedig, and Andrew Scott. "A survey of MAC protocols for mission-critical applications in wireless sensor networks." Communications Surveys & Tutorials, IEEE 14.2, pp. 240-264, 2012.
- Rasmus Hahn, Christian Bizer, Christopher Sahnwaldt, Christian Herta, Scott Robinson, Michaela Bürgle, Holger Düwiger and Ulrich Scheel, ?Faceted Wikipedia Search?. Business Information Systems, Lecture Notes in Business Information Processing, Vol. 47, pp. 1?11, 2010.
- Ning Yan, Chengkai Li, Senjuti B. Roy, Rakesh Ramegowda and Gautam Das, ?Facetedpedia: enabling query-dependent faceted search for wikipedia?, In Proceedings of the 19th ACM international conference on Information and knowledge management (CIKM ?10), pp. 1927?8, 2010.
- Meiqun Hu, Ee-Peng Lim, Aixin Sun, Hady Wirawan Lauw and Ba-Quy Vuong, ?On improving wikipedia search using article quality?, In Proceedings of the 9th annual ACM international workshop on Web information and data management (WIDM ?07), pp. 145?52, 2007.
- Tomasz Boi´nski and Adam Brzeski, ?Towards Facts Extraction from Texts in the Polish Language?, International Journal of Innovative Research in Computer and Communication Engineering, Vol. 2, No. 8, 2014.
- Julian Szyma´nski, ?Self?Organizing Map Representation for Clustering Wikipedia Search Results?, Intelligent Information and Database Systems, Lecture Notes in Computer Science, pp. 140?9, 2011.
- Julian Szyma´nski, ?Wikipedia Articles Representation with Matrix?u?, Distributed Computing and Internet Technology, Lecture Notes in Computer Science, pp. 500?10, 2013.
- Pum-Mo Ryu, Myung-Gil Jang and Hyun-Ki Kim, ?Open domain question answering using Wikipedia-based knowledge model?, Information Processing and Management, Vol. 50, No. 5, pp. 683?92, 2014.
- Jennifer Chu-Carroll and James Fan, ?Leveraging Wikipedia Characteristics for Search and Candidate Generation in Question Answering?, In Proceedings of the Twenty-Fifth AAAI Conference on Artificial Intelligence, 2011.
|