Providing reliable and efficient communication under fading channels is one of the major technical challenges in wireless sensor networks (WSNs), especially in industrial WSNs (IWSNs) with dynamic and harsh environments. Reliable Reactive Routing Enhancement (R3E) to increase the resilience to link dynamics for WSNs/IWSNs. R3E is designed to enhance existing reactive routing protocols to provide reliable and energy-efficient packet delivery against the unreliable wireless links by utilizing the local path diversity. A biased back off scheme has been introduced, during the route-discovery phase to find a robust guide path, which can provide more cooperative forwarding opportunities. Along this guide path, data packets are greedily progressed toward the destination through nodes’ cooperation without utilizing the location information. R3E remarkably improves the packet delivery ratio, while maintaining high energy efficiency and low delivery latency.
Keywords |
| ERMECR , WANET , MDR , MAC |
INTRODUCTION |
| A wireless sensor network (WSN) consists of spatially distributed autonomous sensors to monitor physical or
environmental conditions, such as temperature, sound, pressure, etc. and to cooperatively pass their data through the
network to a main location. The more modern networks are bi-directional, also enabling control of sensor activity. The
development of wireless sensor networks was motivated by military applications such as battlefield surveillance; today
such networks are used in many industrial and consumer applications, such as industrial process monitoring and
control, machine health monitoring. Wireless Sensor Network (WSN) is a collection of spatially deployed wireless
sensors by which to monitor various changes of environmental conditions (e.g., forest fire, air pollutant concentration,
and object moving) in a collaborative manner without relying on any underlying infrastructure support. Recently, a
number of research efforts have been made to develop sensor hardware and network architectures in order to effectively
deploy WSNs for a variety of applications. The main characteristics of a WSN include: |
| • Power consumption constrains for nodes using batteries or energy harvesting |
| • Ability to cope with node failures |
| • Mobility of nodes |
| • Communication failures |
| • Heterogeneity of nodes |
| • Scalability to large scale of deployment |
| • Ability to withstand harsh environmental conditions |
| • Ease of use |
| The base stations are one or more components of the WSN with much more computational, energy and communication
resources. They act as a gateway between sensor nodes and the end user as they typically forward data from the WSN
on to a server. Other special components in routing based networks are routers, designed to compute, calculate and
distribute the routing tables. |
RELATED WORK |
| In [1] several routing schemes proposed for ad hoc mobile networks. Authors provide a classification of these schemes
according to the routing strategy (i.e., table-driven and on-demand) and presented a comparison of these two categories
of routing protocols, highlighting their features, differences, and characteristics. Finally, they have identified possible
applications and challenges facing ad hoc mobile wireless networks. While it is not clear that any particular algorithm
or class of algorithm is the best for all scenarios, each protocol has definite advantages and disadvantages, and is well
suited for certain situations. [2] Wireless multi-hop networks often experience severe performance degradations when
legacy routing algorithms are employed, because they are not optimized to take advantage of the peculiarities of
wireless links. Indeed, the wireless channel is intrinsically a broadcast medium, making a point-to-point link abstraction
not suitable. Furthermore, channel conditions may significantly differ both in time and space, making routing over
predetermined paths inadequate to adapt the forwarding process to the channel variability. Motivated by these
limitations, the research community has started to explore novel routing paradigms and design principles dealing with
the wireless diversity as an opportunity rather than a shortcoming. Within this large body of research, opportunistic
routing and network coding are emerging as two of the most promising approaches to exploit the intrinsic
characteristics of multi-hop wireless net- works, such as multi-user diversity. The aim of this survey is to examine how
opportunistic forwarding and network coding can achieve performance gains by performing hop-by-hop route
construction and by encoding data packets at intermediate nodes. Authors present a taxonomy of existing solutions, and
describe their most representative features, benefits and design challenges. [3] In this paper authors proposes COPE, a
new architecture for wireless mesh networks. In addition to forwarding packets, routers mix (i.e., code) packets from
different sources to increase the information content of each transmission. We show that intelligently mixing packets
increases network throughput. Our design is rooted in the theory of network coding. Prior work on network coding is
mainly theo- retical and focuses on multicast traffic. Authors aims to bridge theory with practice; it addresses the
common case of unicast traffic, dynamic and potentially bursty flows, and practical issues facing the integration of
network coding in the current network stack. Authors evaluated the design on a 20-node wireless network, and
discussed the results of the first test bed deployment of wireless network coding. In this paper [4] authors presents a
protocol for routing in ad hoc networks that uses dynamic source routing. The protocol adapts quickly to routing
changes when host movement is frequent, yet requires little or no overhead during periods in which hosts move less
frequently. Based on results from a packet-level simulation of mobile hosts operating in an ad hoc network, the
protocol performs well over a variety of environmental conditions such as host density and movement rates. For all but
the highest rates of host movement simulated, the overhead of the protocol is quite low, falling to just 1% of total data
packets transmitted for moderate movement rates in a network of 24 mobile hosts. In all cases, the difference in length
between the routes used and the optimal route lengths is negligible, and in most cases, route lengths are on average
within a factor of 1.01 of optimal. [5] Wireless Sensor and Actor Networks (WSANs) are characterized by the
collective effort of heterogenous nodes called sensors and actors. Sensor nodes collect information about the physical
world, while actor nodes take action decisions and perform appropriate actions upon the environment. The
collaborative operation of sensors and actors brings significant advantages over traditional sensing, including improved
accuracy, larger coverage area and timely actions upon the sensed phenomena. However, to realize these potential
gains, there is a need for an efficient trans- port layer protocol that can address the unique communication challenges
introduced by the coexistence of sensors and actors. |
PROPOSED ALGORITHM |
Description of the Proposed Algorithm: |
| The formal description of the Reliable Reactive Routing Enhancement (R3E) to increase the resilience to link
dynamics for WSNs/IWSNs. It inherits the advantages of opportunistic routing. R3E is designed . Reliable route
discovery finds and maintains the route information for each node. During the route discovery phase, each node
involved in the cooperative forwarding process stores the downstream neighborhood information. when a node serves
as a forwarder, the potential forwarder selection already knows the next-hop forwarding candidates along the
discovered path. Prioritization are responsible for the runtime forwarding phase. When a node successfully receives a
data packet, the forwarding decision module checks whether it is one of the intended receivers. If yes, this node will
cache the incoming packet and start a backoff timer to return an ACK message, where the timer value is related with its
ranking in the intended receiver list (called forwarding candidate list). If there is no other forwarder candidate with higher prioritytransmitting an ACK before its backoff timer expires, it will broadcast an ACK and deliver the packet to
the upper layer, i.e., trigger a receiving event in the network layer. The potential forwarder selection and prioritization
module attaches the ordered forwarder list in the data packet header for the next hop. The outgoing packet will be
submitted to the MAC layer and forwarded towards the destination. |
PSEUDO CODE |
 |
SIMULATION RESULTS |
| The simulation analysis for R3E while the data transmission and certificate revocation based security is implemented
using Network Simulator NS2 |
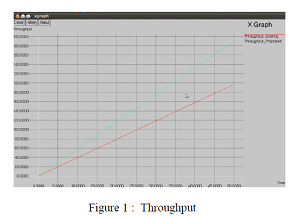
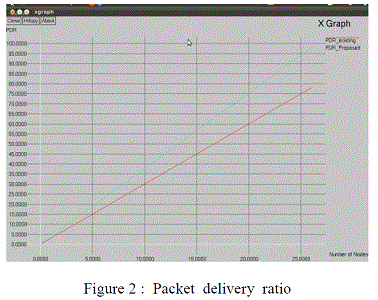
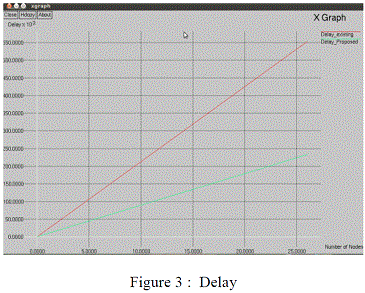
| The simulation is done for Throughput , Packet delivery ratio and Delay using R3E whose results are shown in
Figure 1 , 2 & 3 respectively. |
| From Figure 1 we have seen that the throughput of the proposed system is higher than the existing system. |
| From Figure 2 we have seen that the packet delivery ratio of the proposed system is higher than the existing
system. |
| From Figure 1 we have seen that the delay of the proposed system is lower than the existing system. |
CONCLUSION AND FUTURE WORK |
| The R3E can augment most existing reactive routing protocols inWSNs/IWSNs to provide reliable
and energy-efficient packet delivery against the unreliable wireless links. A biased backoff scheme has been introduced
in the route discovery phase to find a robust virtual path with low over-head. Without utilizing the location information,
data packets can still be greedily progressed toward the destination along the virtual path. Therefore, R3E provides very
close routing performance to the geographic opportunistic routing protocol. Extended AODV with R3E to demonstrate
its effectiveness and feasibility. AODV-R3E can effectively improve robustness, end-to-end energy efficiency, and
latency. |
| |
Figures at a glance |
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 1a |
|
| |
References |
- E. Royer and C.-K. Toh, âÃâ¬ÃÅA review of current routing protocols for ad hoc mobile wireless networks,âÃâ¬Ã IEEE Pers. Communication., vol.6, issue no. 2, pp. 46âÃâ¬Ãâ55, 1999.
- R. Bruno and M. Nurchis, âÃâ¬ÃÅSurvey on diversity-based routing in wireless mesh networks: Challenges and solutions,âÃâ¬Ã Computer Communications., vol. 33, issue no. 3, pp. 269âÃâ¬Ãâ282, Feb. 2010.
- S. Katti, H. Rahul, W. Hu, D. Katabi, M. Medard, and J. Crowcroft, âÃâ¬ÃÅXORs in the air: Practical wireless network coding,âÃâ¬Ã IEEE/ACM Trans. Networks, vol. 16, issue no. 3, pp. 497âÃâ¬Ãâ510, Jun. 2008.
- D. B. Johnson and D. A. Maltz, âÃâ¬ÃÅDynamic source routing in ad hoc wireless networks,âÃâ¬Ã International Journal on Mobil Computing,vol 8 issue 4, pp. 153âÃâ¬Ãâ181, 1996.
- V. Gungor, O. Akan, and I. Akyildiz, âÃâ¬ÃÅA real-time and reliable transport protocol for wireless sensor and actor networks,âÃâ¬Ã IEEE/ACM Transactions on Networks , vol. 16, issue no. 2, pp. 359âÃâ¬Ãâ370, Apr. 2008.
- K. Zeng, W. Lou, J. Yang, and D. Brown, âÃâ¬ÃÅOn geographic collaborative forwarding in wireless ad hoc and sensor networks,âÃâ¬Ã international Journal of Computer Networks and Wireless Communications, Vol.2, Issue 4, pp. 450-455, 2012.
- X. Mao, S. Tang, X. Xu, Li X.-Y, and H. Ma, âÃâ¬ÃÅEnergy-efficient opportunistic routing in wireless sensor networks,âÃâ¬Ã IEEE Trans. Parallel Distributed .Systems, vol. 22, issue no. 11, pp. 1934âÃâ¬Ãâ1942, Nov. 2011.
- AlGabri Malek, Chunlin LI, Z. Yang, Naji Hasan.A.H and X.Zhang ,âÃâ¬ÃÅRSS-based routing protocol for industrial wireless sensor networks,âÃâ¬Ã International Journal of Computer Networks , Vol.3, Issue 3, pp. 159-166, 2011.
- K. A. Agha, M.-H. Bertin, T. Dang, A. Guitton, P. Minet, T. Val, and J.-B. Viollet, âÃâ¬ÃÅwireless technology for industrial wireless sensor networks - the development of Ocari technology,âÃâ¬Ã IEEE Transactions Ind. Electron., vol. 56, issue no. 10, pp. 4266âÃâ¬Ãâ4278, Oct. 2009.
|