ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
| Anu. K, Jagan .S Department of Computer Science and Engineering, G.K.M College of Engineering and Technology, Chennai, India |
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
A new approach for enhancing security and privacy in certain RFID applications where by location. On the tag side, are designs a location-aware selective unlocking mechanism using which tags can selectively respond to reader interrogations rather than doing so promiscuously. On the server side, are design a locationaware secure transaction verification scheme that allows a bank server to decide whether to approve or deny a payment transaction. One Advantage is that there is no external user involvement.
Index Terms |
| RFID, RFID reader, Relay attack, Location sensing. |
INTRODUCTION |
| Radio frequency identification (RFID) is a rapidly growing technology that has the potential to make great economic impacts on many industries. At its most basic, RFID systems consist of small transponders, or tags, attached to physical objects. RFID tags may soon |
| become the most pervasive microchip in history. A Radio Frequency Identification (RFID) is an automatic identification method, relying on storing and remotely retrieving data using devices called RFID tags or transponders. The two major problems faced by organizations are time consuming manual attendance and wastage of electrical power. Our project is going to solve these problems by using RFID technology. A typical RFID system consists of tags, readers, and/or back-end servers. Tags are miniaturized wireless radio devices that store information about their corresponding subject. This renders sensitive tag information easily subject to unauthorized reading. Information (might simply be a plain identifier) gleaned from a RFID tag can be used to track the owner of the tag. Consequently, solutions designed for RFID systems need to satisfy the requirements of the underlying RFID applications in terms of not only efficiency and security, but also usability. |
PROBLEM DEFINITION |
| The system having lack of security due to its leakage of confidential information such as username, password and also entire details about the particular authorized user. If this information is easily hacked by the attacker by choosing the random possibilities of username and password and this will lead to the inconvenience of the authorized user. A large number of these threats are due to the tag’s promiscuous response to any reader requests. This renders sensitive tag information easily subject to unauthorized reading.A primary RFID security concern is the illicit tracking of RFID tags. |
SYSTEM ARCHITECTURE |
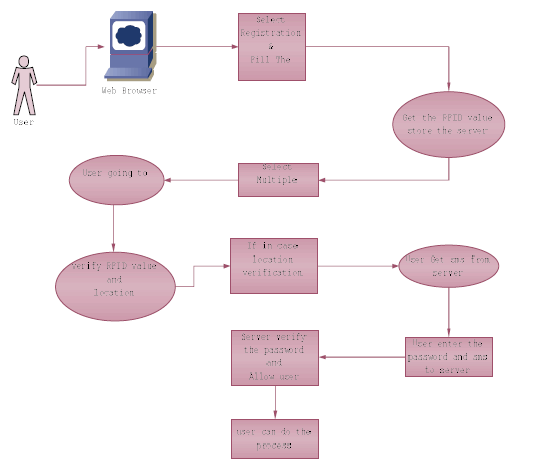 |
TECHNICAL DESCRIPTION |
SELECTIVE UNLOCKING |
| In this Technique the tags can selectively respond to reader interrogations rather than responding promiscuously to queries from any readers, a tag can utilize location information and will only communicate when it makes sense to do so, thus, raising the bar even for sophisticated adversaries without affecting the RFID usage model. |
TRANSACTION VERIFICATION |
| This Technique is used to find the location information. This is based on a straightforward observation that, under normal scenarios, both the legitimate tag and legitimate reader are in close physical proximity, at roughly the same location. |
CONCLUSION |
| RFID are basedon a current technological advancement that enables many RFID tags with lowcost sensing capabilities. The payment card stores card details such as the credit card number, name of the owner, andexpiration date. It also stores a symmetric key shared with its issuer bank. To demonstrate the feasibility of our location-aware defense mechanisms, integrated a low-cost GPS receiver with a RFID tag (the Intel’s WISP) and conducted relevant experiments to acquire location and speed information from GSM. |
References |
|