ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
Swathi.K1, Ramudu.K2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
In the digital world copyright protection and authentication have become more significant; in order to achieve this digital different watermarking techniques are introduced for the security. We propose an algorithm in wavelet domain using wavelet transformation for a digital invisible watermarking is to embedded into a QR code image. In our method we embedded a binary image Annamacharya Educational Trust logo considered as watermark embedded into one of selected wavelet subband. The experimental results show that our method has more robustness to attacks in different considerations and it can achieve a viable copyright protection and authentication.
Keywords |
| QR code, Watermark technique, SWT |
I. INTRODUCTION |
| Barcode becomes widely known because of their accuracy, and superior functionality characteristics. QR Code is a Kind of 2D (two dimensional) barcode. It contains information both in vertical and horizontal directions, where as a 1D (one dimensional) barcode contains data in one direction only. QR Code holds a considerably greater volume of information than a 1D Barcode. QR Code developed by Denso Wave [1]. Bar codes are linear one-dimensional codes and can only hold up to 20 numerical digits, whereas QR codes are two-dimensional (2D) matrix barcodes that can hold 7,089 numeric characters and 4,296 alphanumeric characters, and 1,817 kanji characters of information [4]. |
| In this paper, we describe a novel method to embed the QR code into still digital images. Most of the recent work in watermarking can be grouped into two categories: spatial domain methods, and frequency domain methods. Frequency domain methods have better robustness than spatial domain; almost all techniques embed watermarks in the frequency domain, such as DWT and SWT [2], [3]. To increase robustness against JPEG degradation of the watermarked image, we embed the watermark in low frequency domains of SWT. |
II. BACK GROUND |
| A.QR code [5] |
| QR (Quick Response) Codes are 2-dimensional bar codes that encode text strings and were introduced by the Japanese corporation Denso Wave Incorporated [6]. QR codes are considered as the evolution of the one dimensional barcodes. They are able to encode information in both vertical and horizontal direction, thus able to encode several times more information than the one dimensional barcodes. A QR code consists of black modules (square dots) arranged in a square grid on a white background, which can be read by an imaging device, such as a camera or mobile. |
| B.QR Code structure |
| Here we use as an example version 2, see Figure 1, which is the size that is most widely used, and based on analyze the structure of the QR Code. |
 |
| – (1) Finder Pattern: The three identical structures that are located in the upper corners and in the bottom left corner enable the decoder software to recognize the QR code and determine the correct orientation. These patterns also allow 360 degree (omni-directional) high-speed reading of the code. These structures consist of a 3 X 3 black square surrounded by white modules that are again surrounded by black modules. |
| – (2) Separators: The white separators that surround the Finder Patterns have width of one pixel and make it easier to distinguish the patterns. |
| – (3) Timing pattern: A sequence of black and white modules that help the decoder software to determine the width of a single module. |
| – (4) Alignment Pattern: This pattern allows the QR reader to correct for distortion when the code is bent or curved. The alignment pattern appears on version 2 and higher and the number of alignment patterns used depends on the version selected for the encoding. |
| – (5) Format Information: This section consists of 15 bits and contains the error correction rate and the selected mask pattern of the QR code. The error correction level can be identified from the first two modules of the timing pattern. The format information is read first when the QR code is decoded. |
| – (6) Data: After the data is converted into Reed-Solomon-encoded data bits, it is stored in 8 bit parts (code words) in the data section. |
| – (7) Error Correction: The data code words are used in order to generate the error correction (EC) code words, which are stored in the error correction section. |
| – (8) Remainder Bits: This section contains empty bits if the data or the error correction bits cannot be divided into 8 bit code words without a remainder. |
III. THE PROPOSED WATERMARKING PROCESS |
| In this paper we have chosen a watermark as binary image of Annamacharya Educational Trust logo. In the frequency domain we perform the embedding process on QR code image using watermark. We have to decompose the QR code image by one level using one-dimensional wavelet transformation. To recover the embedded watermark we do not need the original QR code image subsequently |
| In our algorithm have two steps: watermark embedding and watermark extraction. |
| A.Watermark Embedding |
| The following outlined procedure is for the embedding process (Fig.2) |
| Step of watermark image with secret key |
| i. The watermark image was produced as a bit sequence of watermark S. The data and background values were set to 1 and –1, respectively. |
 |
| II. A watermark was then embedded in subband LL or HH. According to the rule: |
| Where ïÿýïÿýïÿýïÿý is input image. ïÿýïÿýïÿýïÿý ′ is output image with watermark. ïÿýïÿý is a magnitude factor which is a constant determining the watermark strength. |
| III. After that, the inverse SWT (ISWT) was then applied to obtain the watermarked image. |
| IV. Compute PSNR. |
 |
| B. Watermark Extraction |
| The watermark extraction algorithm did not use the original QR code image. A prediction of the original value of the pixels is however needed. Thus, a prediction of the original value of the pixels was performed using noise elimination technique. In this paper, we use an averaging 3×3 mask whose elements were fixed to 1/9. The extraction processes are outlined as follows (Fig.3): |
| I.The predicted image ïÿýïÿýïÿýïÿý ïÿýïÿýcould be obtained by smoothing the input image ïÿýïÿýïÿýïÿý ∗ with a spatial convolution mask. The prediction of the original value can be defined as: |
 |
| Where c is the size of the convolution mask. The watermarked image and the predicted image were DWT transformed independently. |
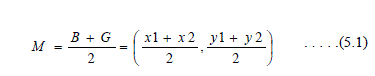 |
 |
IV.EXPERIMENT RESULTS |
| A. Performance Evaluation |
| To evaluate the performance of the algorithm, a similar measurement between the original watermark (S) and the extract watermark (S′) was computed by using normalized correlation (NC), as in below eq. |
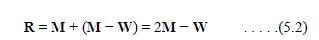 |
| B. Simulation and Results |
| A QR code image, of size 256x256 pixel was used for the experiment in Fig 5(a). The watermark image was a binary image of Annamacharya Educational Trust, as depicted in Fig 5(b).The watermarking was tested with the following parameters: magnitudes factor (α) are 2, 5, 10, 15… 50 and the key is 100. In Table 1, the PSNR, NC and MAE of the QR code image with difference in magnitude factor embedded in HH subband. A high magnitude factor value on one hand could result in low PSNR, high MAE and On the other hand, it increases NC value in watermark extraction (as shown in Table: 1), thereby lowering the noise. In Table 2, it can be noted accordingly that the differences in PSNR are negligible, while the NC and MAE value of HH yeild the watermark that is most resemblant to the original image. The following experiment is therefore carried out with the watermark embedded in HH.Once applied with the SWT; the significant information is aggregate within the low-frequency subband. As a result, embeding the watermark in the higher frequency band does not destroy much of the information, hence resulting in higher NC than otherwise. We tested the robustness of our algorithm with some attacks such as Salt and Pepper noise, Gaussian noise, JPEG, and Scaling and Rotating in Fig.6 a). Fig. 6 b) shows extracted watermark with difference magnitude factors. All extracted watermark images contain some visual noise because of the watermark extracting process did not employed the original QR code image In practices, the transmission of an image can be corrupted by unpredictable noise contaminated in the network communication. Table 3 shows Comparison of PSNR, NC and MAE of LH, HL, HH subband with α =25 |
 |
 |
 |
V.CONCLUSION |
| This paper presented a digital watermarking technique, whereby a binary image is watermarked an embeded in a QR Code image. The embedding process is presented in a LH, HL or HH subband based on wavelet transform. The experimental results demonstrated that the algorithm can be recovering the watermark with an acceptable visual quality. The objective measures such as PSNR, NC and MAE are subject to magnitude factor. As the future work, the quality of the watermarked video Compared to original video was measured based on the Peak Signal to Noise Ratio (PSNR), Normalised Correlation (NC) and Mean Absolute Error (MAE). |
References |
|