ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
J.Sai Harsha1, B.VivekVardhan2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
We proposed a novel approach for highly secure, stable and simplified communication system. — In this paper we use 2 level DWT and DCT watermarking to bring a complex and secure system. Other main aim of the paper is to implement watermarking of several images under single cover. The paper also review the advantages of using proposed system in particular watermarking of several (4) images under single cover reduces the bandwidth required to transmit the data. This paper describes the proposed algorithm, implementation and results. Four images and single cover is used to test the system and the results are much efficient than existing systems.
Keywords |
| DCT, DWT, Watermarking, Compression |
INTRODUCTION |
| We are living in the era of information where billions of bits of data is created in every fraction of a second and with the advent of internet, creation and delivery of digital data (images, video and audio files, digital repositories and libraries, web publishing) has grown many fold. Since copying a digital data is very easy and fast too so, issues like, protection of rights of the content and proving ownership arises. There are many encrypting systems to overcome copyright and also for security purpose. |
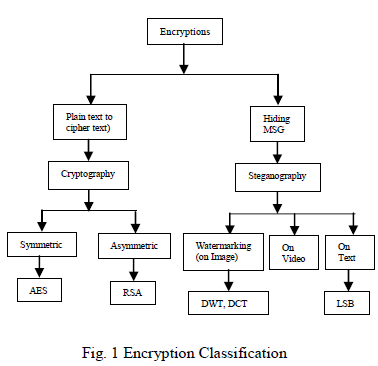 |
| The classification of encrypting system can be described by above Figure 1. |
| For efficient protection against copyrights and also for secure and efficient communication we proposed this approach, it is a combination of Watermarking and Bandwidth Conservation Scheme. This proposed system will satisfies most important aims of cyber world i.e., Security, Stability and Simplicity. |
| Security and Stability can be increased by complicating the encryption system. That is why I used 2 level DWT and DCT watermarking in encoding process. Stability can also be improved by changing the format of encrypted image into other format such as .mat, which cannot be accessed by others. |
| Simplicity means reducing the size of data that to be transmitted i.e. bandwidth conservation. In general to implement watermark on an image we need a cover (i.e. for single image we need single cover). If we want to implement watermark on two or more images we require two or more covers, this lead to increase the data size enormously. But in this system I used single cover for multiple images for watermarking, this in return reduces the size of datathat to be transmitted. |
EXISTING WATERMARKING SYSTEM (2 LEVEL DWT & DCT) |
| Presently for each secure image that to be transferred we use a cover for single image, to transfer more images we required more cover images. |
| For each image we use watermarking, that watermarking involves three steps |
| 1. Decomposition of colour image into its RGB channels. |
| 2. Each colour channel is decomposed into three spatial components using DWT. |
| 3. Applying DCT to convert these components into respective frequencies. |
| The input cover image is decomposed into its R, G and B colour channels. For each colour channel, spatial components (LH, HL, HH) are generated by using DWT transform. Further, frequency components can be generated by applying DCT to every spatial component. Among these frequencies, mid frequencies are used to embed the watermark. To enhance security, a code can be created in which the coefficients of one colour channel signify the indices of the other colour channel. |
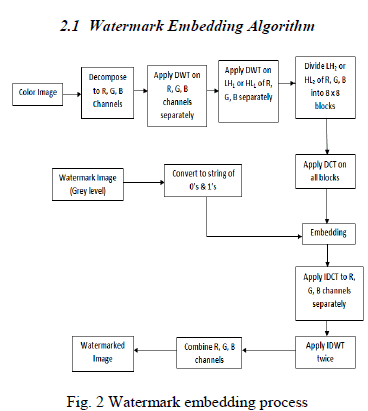 |
| Figure 2 shows the block diagram of watermark embedding algorithm. |
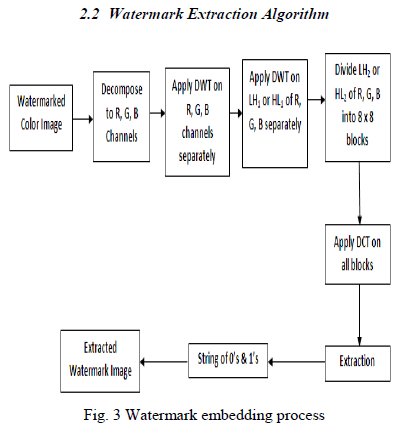 |
| Figure 3 shows the block diagram of watermark extraction algorithm. |
PROPOSED SYSTEM & EXPERIMENTAL RESULTS |
| Our proposed method will provide secure and efficient communication. This method uses single cover image to secure many confidential images. |
| In this project we considered four secure images that is Watermarked under single cover. |
| Our proposed method involves four steps |
| 1. Create a blank image. |
| 2. Combine four images into one image. |
| 3. Use 2 level DWT & DCT method of watermarking on blue component of cover. |
| 4. Send the Watermarked image to the receiver. |
 |
 |
Create a Blank Image |
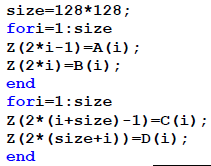
| Create a blank image of size equal to 4 times single image considered. |
| Size of each image (considered) is 128*128. |
| Therefore size blank image is 4*128*128 = 256*256. |
| fori=1:256 |
| for j=1:256 |
| Z(i,j)=0; |
| end |
| end |
Combined Four Images |
| 1. Take four confidential images A, B, C and D. |
| 2. Resize each image into 128*128 resolution. |
| 3. Replace the pixels of blank Z image with pixels of four images, such that first pixel with A, next pixel with B repeat this process until all pixels in A and B are completed. |
| 4. Now replace the remaining pixels of Z with pixels of C and D as in the point 4 until all pixels in C and D are completed. |
 |
 |
| The result of above algorithm is shown in figure 9. |
Apply 2 level DWT & DCT method of watermarking on blue component of cover |
| Modify the existing watermark system as prescribed below. |
Watermark embedding over cover |
| Step involved in watermark embedding are |
| 1) Select any color image as cover image, denote it by âÃâ¬ÃâI‘. Obtain R, G and B channels of cover image âÃâ¬ÃâI‘. |
| 2) Apply DWT to B channel separately to get the multi-resolution sub-bands LL1, HL1, LH1, and HH1. |
| 3) Apply DWT again to HL1 (or LH1) sub-bands of R, G and B channels and select HL2 (or LH2)sub-bands of B channel.(Decomposition is continued only up to 2 levels as the energy becomes 0 at the third level.) |
| 4) Divide the HL2 (or LH2) sub-bands of R, G and B channels into blocks of size 4X4. |
| 5) Apply DCT to each of the blocks obtained in previous step. |
| 6) Convert the watermark âÃâ¬Ãâw‘ into string of 0‘s and 1‘s. |
| 7) To embed bits, first calculate average of middle band coefficients of first block of B component. |
| 8) Repeat this process for all bits of the watermark. |
| 9) Apply IDCT to the blocks of B channels. |
| 10) Apply IDWT for 2 levels to B channels. |
| 11) Combine R, G and B channels to get watermarked image ‘WI’ |
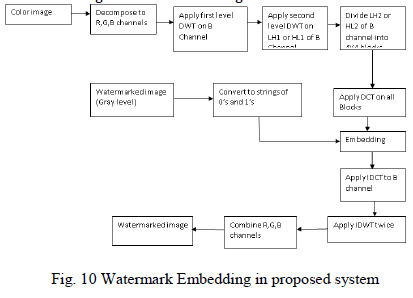 |
| Modified watermark embedding process is as shown in figure 10 (Watermark Embedding in proposed system) |
Watermark Extraction |
| Steps involved in watermark extraction from cover are |
| 1) Obtain R, G and B channels of watermarked image âÃâ¬ÃâWI‘. |
| 2) Apply DWT to B channel to obtain the multi-resolution sub-bands LL1, HL1, LH1, and HH1. |
| 3) Apply DWT again to HL1 sub-bands of B channel and select HL2 sub- B channel. |
| 4) Divide the HL2 sub-bands of B channel into blocks of size 4×4. |
| 5) Apply DCT to B block obtained in previous step. |
| 6) Water marking bits are extracted from first block of B channel and repeat this process until extraction of all bits from all 4X4 blocks |
| 7) Then apply IDCT to all 4X4 blocks to get the watermarked image. |
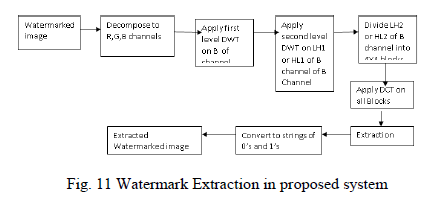 |
| Modified watermark extraction process is as shown in figure 11 (Watermark Embedding in proposed system) |
Experimental inputs and Results |
| Cover image and Watermark image (Z) are shown in figures 12 and figure 13 respectively. |
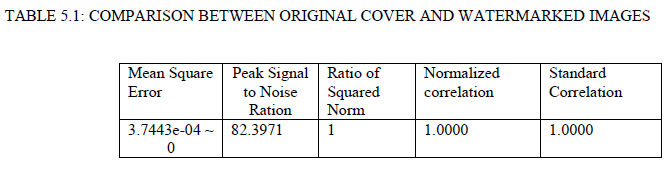
| By using this system, watermarked image is same as of cover image, no human eye can distinguish them. This makes the image appears as normal image with no significant information. |
 |
| Resultant of Watermarking is shown in figure 14 |
 |
Decoding Process |
| Decoding Process is exactly the reverse process of Encoding. |
| Decoding Process is exactly the reverse process of Encoding. |
| Steps |
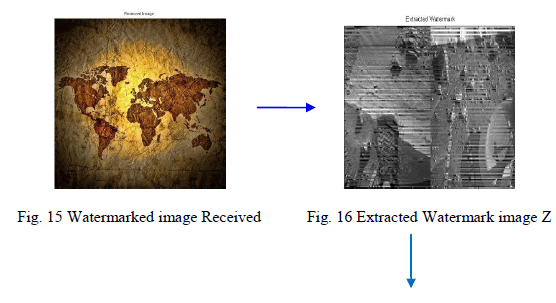
| 1. Extracting Watermark image Z. |
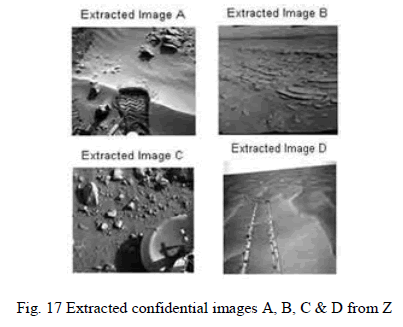
| 2. Extract four confidential images from Z. |
| Extracting each images from Z can be implemented using below code. |
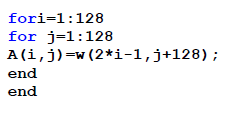 |
Experimental Results |
| The decoding architecture (process) of proposed system is as shown in figures below. |
 |
 |
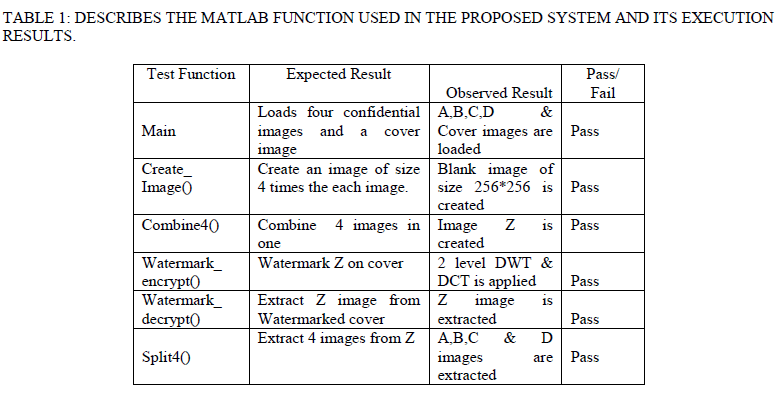
FUNCTIONS USED FOR PROPOSED SYSTEM & EXECUTION RESULTS |
 |
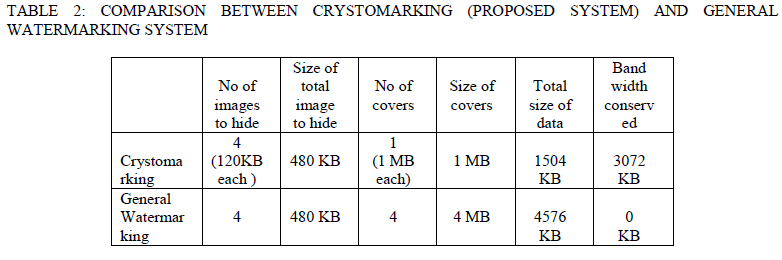
COMPARISON OF RESULTS |
| In my proposed system we need single cover to transmit many images (4). |
| In this paper I used 4 images of each 120 KB and a cover image of 1MB. The resultant output size is 1MB. |
| In general four images require 4 covers i.e. 4 images of each 120KB require 4MB of covers (4 covers of each 1MB). |
| Thus data is compressed logically which results in efficient communication. |
 |
 |
CONCLUSION AND FUTURE WORK |
| This paper introduces the effective and efficient method of communication in unreliable environment that can modify the previous techniques. This method is simpler to use and very reliable. Special configuration (hardware) is not a necessity. Using this method efficient bandwidth consumption for transmitting the data worked out practically and the results are displayed. |
| The above proposed method can be made more secure, stable, and efficient by implementation of the best lossless compression algorithm and also by providing a biometric or face recognition as an authentication to access this algorithm. |
ACKNOWLEDGMENTS |
| We would like to acknowledge the help from all my classmates and faculty especially Dr. P. Siddaiah (Principal& H.O.D), Dr. E. Srinviasa Reddy (Dean), Er.S.NagakishoreBhavanam (Asst Prof) and Mr.GouthamBommidi. |
References |
|