ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
K.Ramu1 and Dr.V.Padmaja2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
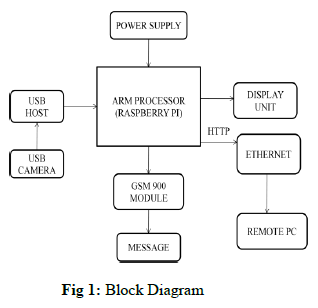
In this paper, a solution about secure provenance transmission for streaming data is introduced based on Raspberry Pi processor is presented. The embedded system, video capture, short message service (SMS) alarm, and video monitor are introduced. Video 4 Linux is used to get the camera video data, which is transferred to the Web Server, and the data is displayed on the client browser. The main aim of this paper is the designed system have USB camera it will continuously capturing in front of the people then processes the captured images via USB host to the Raspberry Pi to the display device unit, and the parallel connection Ethernet module, web page is created the remote pc using HTTP protocol because HTTP protocol provides secure data transmission. And for more security we are creating some IP address to view the live streaming data on remote pc and when the person entered infront of camera the processor collect the information and the processor will activated the GSM, through GSM send message to the authorized person. In this processes in USB camera captured images face are detected by using LBP accurately and stored temporarily in our database to check or recognize is this person is right person to use or not. Compared with video capture system based on digital signal processor (DSP), this system has the advantage of fewer modules, lower cost, higher intelligence, higher system stability, and higher security. This paper presented design system will integrate ARM11, USB cam, GSM, remote pc, Display monitoring unit, and Ethernet. The entire paper proves continuous, and surveillance secured system.
Keywords |
| Security, Raspberry Pi (ARM11), Face detection, GSM, Ethernet, HTTP |
INTRODUCTION |
| The proliferation of the Internet, embedded systems, and sensor networks has greatly contributed to the wide development of streaming applications. Examples include real-time financial analysis, location-based services, control of automated systems. This diversity of data sources accelerates the importance of data provenance to ensure secure and predictable operation of the streaming applications. Data provenance is considered as an effective tool for evaluating data trustworthiness, since it summarizes the history of the ownership and the actions performed on this data. As an example considered a battlefield surveillance systems gathers enemy locations from various sensor deployed in vehicles, air-crafts, satellites, etc.., and manages queries over these data. Now a day’s research people’s are mostly preferred data mining applications used so many areas such as web service, communication and security in surveillance systems. The biometric applications are very popular in security all areas in that one of the best one is face recognition, here in captured image human faces are detected by using LBP algorithm for further verification and security purposes. In this paper one of the challenging task is human face is tracking and recognition is one the main role in this designed system. This automatic face recognition conditions by using CCTV ongoing research to overcome so many problems before it can be require the strength of human perception systems. Here the image quality is very important for both recognition and tracking human faces. For this face detection mainly three approaches are generally used for face detection: feature based, template matching, Eigen values based. In this paper we used LBP technique for face detection on captured images effectively then compared to existing methods. In this paper , we use high performance Raspberry Pi processor. Video data is captured from a USB camera, the captured images sent to Raspberry Pi and transferred over Internet through Ethernet under the control of the ARM11 chip, and then the monitor client will receive the compressed data frame to restructure, and recompose video images by using HTTP protocol. |
PROPOSED METHOD |
| The proposed method is used to overcome the drawback present in the existing method. The design for the video encoding system involves various aspects such as selection of the hardware platform and the embedded operating system. Before transferring the data through internet first of all we are transferring some password to particular file. Based on this file will not be hacked and we can provide security for each and every file. |
| We can capture the live video of the particular location by using webcam which is interfaced to ARM board. This camera will continuously capture the images and sent it to ARM board. After that the controller will send the video on internet through Ethernet technology in the form of frame by frame and stores those images into internal memory of the micro controller. Then create IP address in order to globalize the uploaded video. By using HTTP protocol the controller can transfer the updated images on to PC. By trying an IP address on web page, the updated image will display HTML page in PC. So it will reduce the power consumption when compared to the normal video detecting systems. When the person entered infront of camera the camera capture the image and sent to the processor and the processor will activated the GSM900 mobile and sent message alerts to authorized persons. |
| In this paper remote control of human face detection and recognition for ATM centers and other video survilleiance system using ARM1176JZF-S 700 MHz processor. The device which is able to perform the task is a Raspberry Pi processor. Then he will take care all those things in real time surveillance systems. |
 |
HARDWARE DESIGN OF PORTABLE DEVICE |
USB CAMERA: |
| A webcam or USB camera is a video camera that feeds its image in real time to a computer or computer network. Unlike an IP camera which uses a direct communication using Ethernet or Wi-Fi, a USB camera is generally connected by USB cable, FireWire cable, or similar cable. |
| The common uses as a video camera for the World Wide Web gave the webcam its name. Other popular uses include security surveillance, computer vision, video broadcasting and recording social videos. Webcams are known for their low manufacturing cost and flexibility, making them lowest cost form of video telephony. |
| They have also become a source of security and privacy issues, as some built in webcams can be activated via spyware. |
RASPBERRY PI |
| In the proposed ALPR system we used the Raspberry Pi is a credit-card sized single board computer developed in the UK by the Raspberry Pi foundation. The Raspberry Pi has Broadcom BCM2835 system on chip(SoC), which includes an ARM1176JZF-S 700 MHz processor. |
| Video Core IV GPU, and was originally with 256 megabytes of RAM, later upgraded to 512 MB. It does not include a built in hard disk or solid state drive. but uses an SD Card for booting and long term storage. |
 |
GSM |
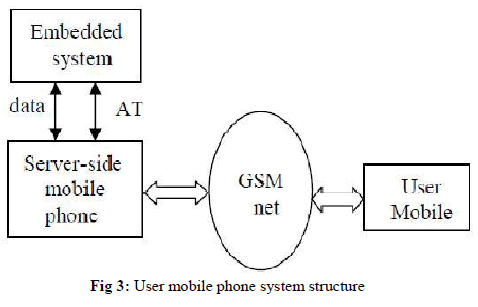
| GSM, which stands for Global System for Mobile Communication, reigns as the world’s most widely used cell phone technology. GSM is a globally accepted standard for digital cellular communication. This system integrates SMS alarm and monitoring components, and makes the mobile phone to bind to it. When alarm system is detected the by the system, it will notice the user of the mobile phone in the form of the text. |
| In general, many phones have a GSM network module. It is associated with the operating system through a serial port, supporting GSM07.07 of the AT commands and using the AT instructions to realize SMS transreceiver, alarm and query. |
 |
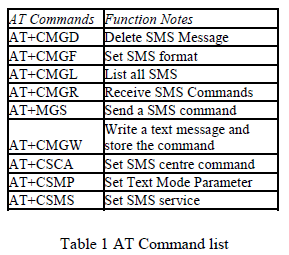
| It is need to use the SMS protocol description unit (PDU) encoding and serial communication class libraries for communication between systems and mobile phones, and the realization of SMS receiving and sending requires AT commands. The AT commands list is shown in Table 1 |
 |
SOFTWARE DESIGN |
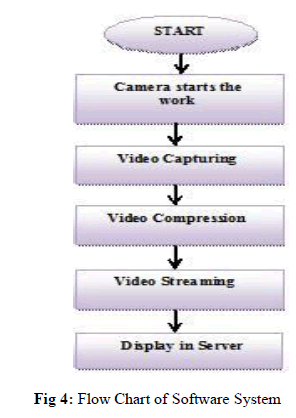
| The system selected Linux operating system as software platform, the build environment using ARM-Gcc cross compiler debug mode, use embedded Linux 2.6.38 kernel and there are mainly three functional modules as follows Video capture module, Video Compression module, and Video Streaming module. The flow chart system software shown in Figure 5 |
 |
Embedded Operating System |
| Here the software tools required for this are arm linux tool chain, latest kernel source and rootfile system from which we build the U-Boot and kernel image binary files which are flashed into the first partition of Sdcard and rootfile system which will work as an operating system also flashed into second partition of Sdcard which is used to run the application of video streaming. The drivers and modules are included in the kernel source. |
DESIGN OF MAIN FUNCTIONAL MODULES |
Video Capture Module |
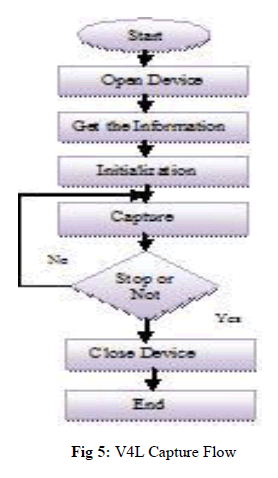
| A. Video Capture Based Video4Linux Video4 Linux (referred to as "V4L")[2] is a Linux kernel on the video device driver, which is for video equipment. After the board starts up, the necessary drivers are loaded using modprobe command. The corresponding supported modules are USB and Video4linux.When USB Logitech Quick cam Messanger with Device ID:046d:08f0 is connected to the board, it is get registered with USB. Application programming interface functions are provided to system. The basic process of video capture shown in Figure 3.V4L USB camera using the programming on the need to use Linux system calls ioctl() and mmap(). |
Video Compression |
| The increasing demand to incorporate video data into telecommunications services, the corporate environment, the entertainment industry, and even at home has made digital video technology a necessity. A problem, however, is that still image and digital video data rates are very large, typically in the range of 150Mbits/sec. Data rates of this magnitude would consume a lot of the bandwidth, storage and computing resources in the typical personal computer. For this reason, Video Compression standards have been developed to eliminate picture redundancy, allowing video information to be transmitted and stored in a compact and efficient manner. Mainly the compression of video must be done because some mobile devices allow only some restricted amount of packet size between the server and themselves. |
 |
LBP(Local Binary Pattern) |
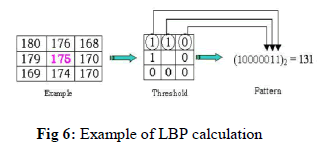
| The main objective of this LBP technique is for face detection and recognition. The Local Binary Pattern technique is a easy and it provides efficient texture information based on thresholding technique to get binary results. One of the most important property of LBP scheme in real time applications it’s more robustness then compared to other schemes, monotonic gray scale variations are getting by illumination changes. Another important property is very simple and possible to analyze real time challenging images |
 |
LBP based Facial representation |
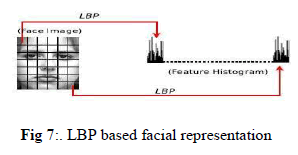
| Each face image can be considered as a composition of micro-patterns which can be effectively detected by the LBP operator. Ahonen et al. introduced a LBP based face representation for face recognition. To consider the shape information of faces, they divided face images into M small non-overlapping regions R0, R1, ..., RM (as shown in Figure 4). The LBP histograms extracted from each sub-region are then concatenated into a single, spatially enhanced feature histogram defined as: |
| where i = 0, ... , L-1, j = 0, ..., M-1. The extracted feature histogram describes the local texture and global shape of face image |
 |
EXPERIMENTAL RESULTS |
| Secure provenance transmission for streaming data using Raspberry Pi ARM1176JJZF-S 700 MHz processor was implemented successfully. We can see the results of the project as shown in figures. |
| Figure 8 shows snap shot of the overall project secure provenance transmission for streaming data |
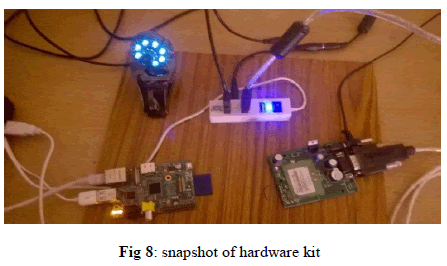 |
| After switch on the power supply, USB camera continuously capturing the video and it is stored in Raspberry Pi and the raspberry pi acts as a sever and the video displayed in remote pc by using HTTP protocol. And whenever person face detected it will automatically send message alerts to GSM Modem |
| The processed stream data packet are uploaded into server using HTTP protocol and transmitted through Ethernet cable, so that user input the corresponding IP address http://192.168.1.225/.html which is specific to router and then webpage is opened and the login page created with user name and password. If you entered correct login details it will open and video displayed. Otherwise incorrect login details message displayed. |
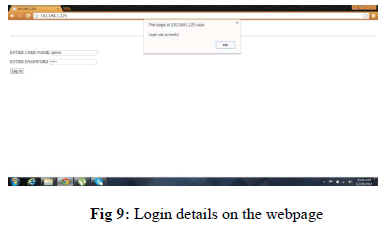 |
| After entered login details correctly then the webpage is opened and the output of video is streaming as shown in below figure 10 |
 |
CONCLUSION |
| In this paper secure provenance transmission for streaming data based on Raspberry Pi , it will succeeds in network video monitoring and upgraded towards home automation or security automation system. This system has low-cost good openness and portability and is easy to maintain and upgrade. It has advantage at low power consumption. In the future, this can be extended in 4 ways as mentioned below: |
| • Maintain a separate database system for network remote video so that we can monitor the video at any instant of time. |
| • Maintain an alarm system so that the security can be increased. |
| • Extracting key frames from the captured raw video which are stored and streamed into the server. |
| • We can upgrade the system by incorporating multiple cameras to cover large number of places. |
References |
|