ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
Harmandeep Singh1, Manpreet Singh2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
Wireless or mobile network is the new generation of wireless network that is different from the wired approach in many aspects like power and energy efficient routing protocols, routing configuration, network infrastructure. There are several protocols proposed for the deployment of MANETs in fields like government, military etc. In this paper we are proposing a technique to identify attack i.e. black hole attack and solution to avoid the black hole attack by discover a safe route for secure transmission. In this paper we focus on improving the security of the one of the popular MANET Routing Protocol namely as AODV.
Keywords |
| Ad Hoc Network, Black Hole, security, AODV. |
INTRODUCTION |
| Wireless networks have poor constrained like bandwidth and resources with no infrastructure. Time to time every node in such network has to take care of its routing module itself that enhance the importance of security in mobile ad-hoc network due to high probability of attacks[7]. A collection of independent mobile users is called a Mobile Ad Hoc network. In this network nodes can communicate with available bandwidth and limited power constraints. Mobile nodes in MANETs change the network topology rapidly. There is a no central role in the MANETs[6] so the possibility of attacks[7] in various manners that breech the security and any security approach may be disqualify due to this that rely on recovery administrative services. |
ROUTING PROTOCOLS |
| In ad-hoc network nodes are moving freely from one location to another so mobility of node the path established by a source may not be exist after a short interval of time. Routing determines the path from source to destination so that the nodes can communicate[4]. Routing Protocols for ad-hoc networks are reactive, proactive and hybrid. |
| Reactive protocols are also known as demand driven protocol because they find path when necessary. These protocols discover the new route by sending route request (flooding) and receiving route reply. Only the active route is maintain by the nodes. Due to route discovery the major drawback of these protocols is delay[12]. |
| Proactive protocols are also known as Table Driven Protocols. The network topology is constantly maintained by these protocols. In a network every node keeps the information of the neighbours in advance. The different tables are used to keep the routing information and these tables are updated according to the changes in the network topology. The topology information is also exchange by the nodes so that they can have route information any time when they needed[5]. |
| The combination of proactive protocols with reactive protocols is a hybrid protocols. They use distance-vector for more precise metrics to establish the best paths to destination networks. In this network each node has its own routing zones and the size of the zone is defined by a zone radius i.e. number of hops in one zone[6]. Each node keeps a record of routing information for its own zone. In hybrid protocols, routers only maintain information about the adjacent routers. Source initiate the establishment of routes to a given destination on demand during reactive operation. |
A. AODV PROTOCOL |
| Ad-hoc On-Demand Distance Vector (AODV) [13] Routing Protocol is used for finding a path to the destination in an ad-hoc network. To find the path to the destination all mobile nodes work in cooperation using the routing control messages. The most distinguishing feature of AODV[1] compared to the other routing protocols is that it uses a destination sequence number for each route entry. The destination sequence number is generated by the destination when a connection is requested from it. Using the destination sequence number ensures loop freedom. AODV makes sure the route to the destination does not contain a loop and is the shortest path. Route Requests (RREQs), Route Replay (RREPs), Route Errors (RERRs) are control messages used for establishing a path to the destination, sent using UDP/IP protocols. When the source node wants to make a connection with the destination node, it broadcasts an RREQ message[8],[9]. This RREQ message is propagated from the source, received by neighbors (intermediate nodes) of the source node. The intermediate nodes broad cast the RREQ message to their neighbors. This process goes on until the packet is received by destination node or an intermediate node that has a fresh enough route entry for the destination. Figure 1show how the RREQ message is propagated in an ad-hoc network[2]. |
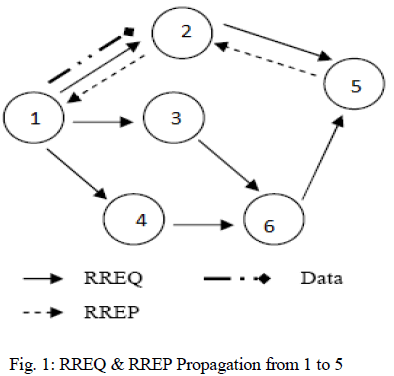 |
| Fresh enough means that the intermediate node has a valid route to destination formed a period of time ago, lower than the threshold. While the RREQ packet travels through the network, every intermediate node increases the hop count by one. If an RREQ message with the same RREQ ID is received, the node silently discards the newly received RREQs, controlling the ID field of the RREQ message[2]. When the destination node or intermediate node that has fresh enough route to the destination receive the RREQ message they create an RREP message and update their routing tables with accumulated hop count and the sequence number of the destination node. Afterwards the RREP message is unicasted to the source node. |
BLACK HOLE ATTACK |
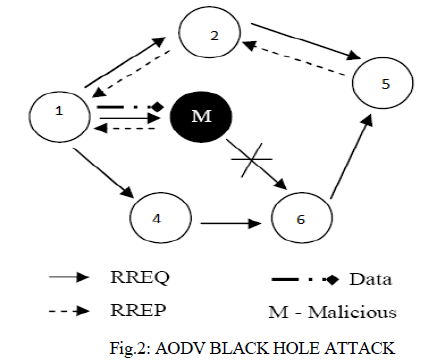
| In the following illustrated figure 2, imagine a malicious node „MâÃâ¬ÃŸ. When node „AâÃâ¬ÃŸ broadcasts a RREQ packet; nodes „2âÃâ¬ÃŸ „4âÃâ¬ÃŸ and „MâÃâ¬ÃŸ receive it. Node „MâÃâ¬ÃŸ, being a malicious node, does not check up with its routing table for the requested route to node „5âÃâ¬ÃŸ. Hence, it immediately sends back a RREP packet, claiming a route to the destination. Node „1âÃâ¬ÃŸ Receives the RREP from „MâÃâ¬ÃŸ ahead of the RREP from „2âÃâ¬ÃŸ and „4âÃâ¬ÃŸ.Node „1âÃâ¬ÃŸ assumes that the route through „MâÃâ¬ÃŸ is the shortest route and sends any packet to the destination through it. When the node „1âÃâ¬ÃŸ sends data to „MâÃâ¬ÃŸ, it absorbs all the data and thus behaves like a „Black holeâÃâ¬ÃŸ[7,12]. |
 |
PROPOSED SOLUTION |
| To avoid Black Hole Attack[7] we enhance the basic AODV routing protocol. In this paper we proposed a solution to prevent any alternation in the default operation of either the intermediate node or that of the destination node. We basically modify the working of the source node by using additional function P_ReceiveReply(Packet P). We also added a new table C_RREP_T, a timer M_WAIT_T and a variable M_Node to the data structures in the basic AODV protocol. |
| In AODV the source node accepts the first RREP request coming to it. According to our work we store all the RREPs in the newly created table i.e. C_RREP_T until the time, M_WAIT_T and we initialize this to be the half value of RREP_WAIT_TIME i.e. the time for which the source node wait for RREP control messages before regenerating RREQ. But according to our solution after receiving the first RREP control message source node has wait for M_WAIT_T and save all the coming RREP control messages in C_RREP_T table. |
| The source node analyses all the stored RREPs from C_RREP_T table and discard the request reply having very high destination sequence number. The node who sent the high sequence number is identify as malicious node and after that the source node selects a reply having highest destination sequence number from the C_RREP_T table. So with the help of our proposed solution the malicious node as M_Node is identified and in future source node can discard the message coming from that node and routing table for that node is not maintained[2]. |
 |
 |
| The control messages are not added in the existing AODV so the normalized routing have minimum chance i.e. the ratio of number of control packets to data transmission in a simulation. The proposed solution is overhead in time in terms of the M_WAIT_T and the time required to execute the Pre_receivereply(). |
SIMULATION ENVIRONMENT |
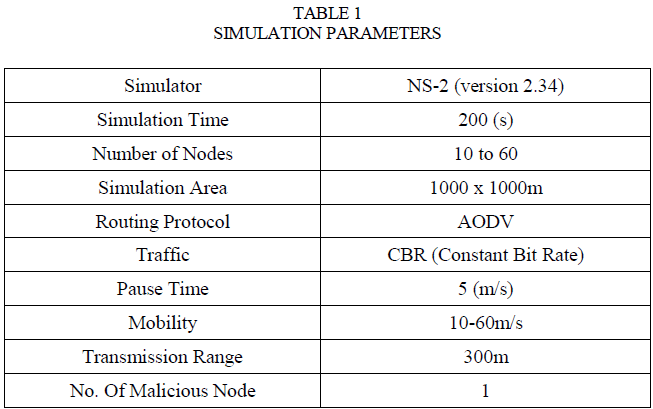
| A. Criteria: For simulation, we have used NS-2[2.34] network simulator[10]. Mobility scenarios are generated by using a random way point model by varying 10 to 100 nodes moving in simulation area of 1000m x 1000m. We have used the following parameters. |
 |
| B. Metrics: The metrics used to evaluate the performance are given below: |
| 1.) Packet Delivery Ratio: It is the ratio between the number of packets send by the sources and the number of packets received by the destination. |
| 2.) Average End-to-End Delay: This is the average delay between the sending of the data packet by the sourceand its corresponding receiver. It includes all the delays caused during route acquisition, buffering andprocessing at intermediate nodes, retransmission delays in milliseconds. |
| 3.) Throughput: Also known as normalized throughput. It is the ratio of overall the number of packets received by the CBR sink to the number of packets sent by the CBR source. |
SIMULATION RESULTS |
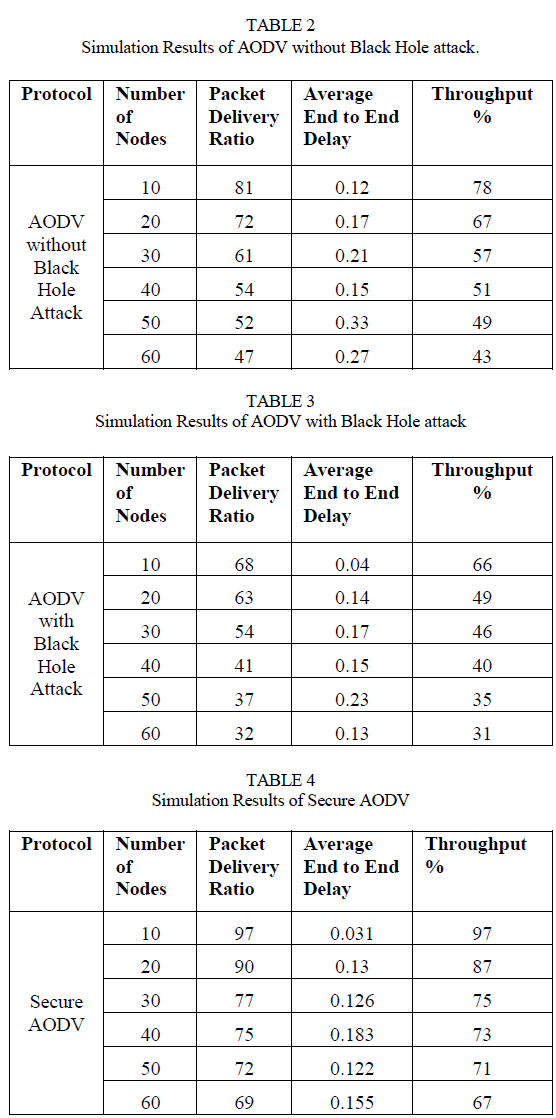
| After taking into consideration the simulation parameters mentioned in Table 1 we came across the following results: |
 |
CONCLUSION |
| In this study we analyzed the effects of back holes in ad hoc wireless networks. We implemented an AODV protocol that simulates the behaviour of a black hole in NS-2.In this method we have used very simple and effective way of providing security in AODV against black hole attack that causes the interception and confidentiality of the ad hoc wireless networks. The solution detects the malicious nodes and isolates it from the active data forwarding. As from the graphs illustrated in results we can easily infer that the performance of the normal AODV drops under the presence of black hole attack. Though the algorithm is implemented and simulated with AODV routing algorithm, we believe that the solution can also be used by other routing algorithm as well. |
ACKNOWLEDGMENT |
| I express my sincere gratitude to my guide Mr. Manpreet Singh, for his valuable guidance and advice. Also I would like to thanks all the faculty members and colleagues for their continuous support and encouragement. |
References |
|