ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
Niloufer Rafath1, Wahaj Ghouri2, Syed Raziuddin3
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
Cipher text-Policy Attribute-based Encryption (CP-ABE) is considered as one of the most suitable scheme for data access control in cloud storage. Despite that the existing Outsourced ABE solutions are able to offload some intensive computing tasks to a third party, the verifiability of results returned from the third party has yet to be addressed. Aiming at tackling the challenge above, a new Secure Outsourced ABE system is proposed, which supports both secure outsourced key-issuing and decryption. This new method offloads all access policy and attribute related operations in the key-issuing process or decryption to a Key Generation Service Provider (KGSP) and a Decryption Service Provider (DSP), respectively, leaving only a constant number of simple operations for the attribute authority and eligible users to perform locally. In addition, for the first time, an outsourced ABE construction is proposed which provides checkability of the outsourced computation results in an efficient way.
KEYWORDS |
| Access Control, Attribute-Based Encryption, CP-ABE, Outsourcing Computation, Key Issuing, Checkability. |
I. INTRODUCTION |
| In ABE system, users‘ private keys and ciphertextsare labeled with sets of descriptive attributes and access policies respectively, and a particular key can decrypt a particular ciphertext only if associated attributes and policy are matched. Until now, there are two kinds of ABE having been proposed: key-policy attribute-based encryption (KPABE) and ciphertext-policy attribute-based encryption (CP-ABE). In KP-ABE, the access policy is assigned in private key, whereas, in CP-ABE, it is specified in ciphertext. |
| Recently, as the development of cloud computing, users‘ concerns about data security are the main obstacles that impede cloud computing from wide adoption. These concerns are originated from the fact that sensitive data resides in public cloud, which is maintained and operated by untrusted Cloud Service Provider (CSP). ABE provides a secure way that allows data owner to share outsourced data on untrusted storage server instead of trusted server with specified group of users. This advantage makes the methodology appealing in cloud storage that requires secure access control for a large number of users belonging to different organizations. |
| When a large number of users call for their private keys, it may overload the attribute authority. Moreover, key management mechanism, key revocation in particular, is necessary in a secure and scalable ABE system. In most of existing ABE schemes, the revocation of any single private key requires key-update at attribute authority for the remaining unrevoked keys which share common attributes with the one to be revoked. All of these heavy tasks centralized at authority side would make it an efficiency bottleneck in the access control system. Aiming at eliminating the most overhead computation at both the attribute authority and the user sides, an outsourced ABE scheme is proposed that not only supports outsourced decryption but also enables delegating key generation. |
| In addition, it is observed that when experiencing commercial cloud computing services, the CSPs may be selfish in order to save its computation or bandwidth, which may cause results returned incorrectly. In order to deal with this problem, checkabilityis done on results returned from both KGSP and DSP. |
II. RELATED WORK |
| Identity-Based Encryption (IBE) allows a sender to encrypt a message to an identity without access to a public key certificate. The ability to do public key encryption without certificates has many practical applications. For example, a user can send an encrypted mail to a recipient, e.g. bobsmith@gmail.com, without requiring either the existence of a Public-Key Infrastructure or that the recipient be on-line at the time of creation. |
| In this paper a new type of Identity-Based Encryption [1] is proposed that we call Fuzzy Identity-Based Encryption in which we view identities as a set of descriptive attributes. Fuzzy-IBE gives rise to two interesting new applications. The first is an Identity-Based Encryption system that uses biometric identities. Secondly, Fuzzy IBE can be used for an application that is called as âÃâ¬Ãâ¢attribute-based encryptionâÃâ¬Ãâ. |
| In this application a party will wish to encrypt a document to all users that have a certain set of attributes. For example, in a computer science department, the chairperson might want to encrypt a document to all of its systems faculty on a hiring committee. In this case it would encrypt to the identity {âÃâ¬Ãâ¢hiring-committeeâÃâ¬Ãâ,âÃâ¬Ãâ¢facultyâÃâ¬Ãâ,âÃâ¬Ãâ¢systemsâÃâ¬Ãâ}. Any user who has an identity that contains all of these attributes could decrypt the document. |
| Cloud computing is a promising technology, which is transforming the traditional internet computing paradigm and IT industry. With the development of wireless access technologies, cloud computing is expected to expand to mobile environments [4], where mobile devices and sensors are used as the information collection nodes for the cloud. However, users‘ concerns about data security are the main obstacles that impede cloud computing from being widely adopted. These concerns are originated from the fact that sensitive data resides in public clouds, which are operated by commercial service providers that are not trusted by the data owner. Thus, new secure service architectures are needed to address the security concerns of users for using cloud computing techniques. |
III. PROPOSED SYSTEM |
| Since some users may change their associate attributes at some time, or some private keys might be compromised, key revocation or update for each attribute is necessary in order to make systems secure. The user revocation can be done via the proxy encryption mechanism together with the CP-ABE algorithm. Attribute group keys are selectively distributed to the valid users in each attribute group, which then are used to re-encrypt the ciphertext encrypted under the CPABE algorithm. In addition, as the user revocation can be done on each attribute level rather than on system level, more fine-grained user access control can be possible. Even if a user is revoked from some attribute groups, he would still be able to decrypt the shared data as long as the other attributes that he holds satisfy the access policy of the ciphertext. Therefore, the proposed scheme is the most suitable for the data sharing scenarios where users encrypt the data only once and upload it to the data-storing centers, and leave the rest of the tasks to the data-storing centers such as re-encryption and revocation. |
| This new method offloads all access policy and attribute related operations in the key issuing process or decryption to a Key Generation Service Provider (KGSP) and a Decryption Service Provider (DSP), respectively, leaving only a constant number of simple operations for the attribute authority and eligible users to perform locally. |
| Checkability on results returned from both KGSP and DSP is done so that the users obtain the correct results. The idea of appending redundancy and having checksum while sending and receiving the data will fight against the dishonest actions of KGSP and DSP. |
| The system model for outsourced ABE scheme consists of Data User, Attribute Authority (AA), Key Generation Service Provider (KGSP), Decryption Service Provider (DSP) and Storage Service Provider (SSP).This new method offloads all access policy and attribute related operations in the key issuing process or decryption to a Key Generation Service Provider (KGSP) and a Decryption Service Provider (DSP), respectively, leaving only a constant number of simple operations for the attribute authority and eligible users to perform locally. |
| DATA USER |
| Data User is he who has successfully registered himself and having his own ID and password using which he can login to the website in order to access the data. If a user possesses a set of attributes satisfying the access policy of the encrypted data, and is not revoked in any of the valid attribute groups, then he will be able to decrypt the cipher-text and obtain the data. |
| ATTRIBUTE AUTHORITY |
| Here Attribute Authoritymay also be known asdata owner. He allows to upload it into the external data-storing center for ease of sharing or for cost saving. A data owner is responsible for defining (attribute-based) access policy, and enforcing it on its own data by encrypting the data under the policy before distributing it. The data owner logins to the website using his credentials and then he can upload the file to the Storage Service Provider (SSP). While uploading the file the data owner will define the access policy which is based on attribute. Then the data owner also have the checksum of that file so that the CSP may not return results incorrectly. The redundant data is also attached to the ciphertext to fight against dishonest actions of KGSP and DSP. |
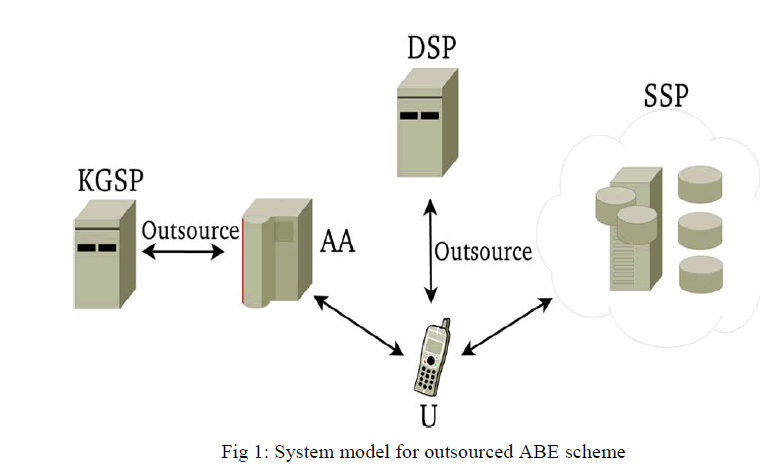 |
| KEY GENERATION SERVICE PROVIDER |
| Aiming at eliminating the most overhead computation at both the attribute authority and the user sides, an outsourced ABE scheme is proposed that not only supports outsourced decryption but also enables delegating key generation. KGSP is to perform aided key-issuing computation to relieve AA load in a scale system when a large number of users make requests on private key generation and key update. It is in charge of issuing, revoking, and updating attribute keys for users. KGSP is in charge of generating the encrypted password and sending it to the mail-ID of the user. At the time of downloading the file, the session password is required which is generated by KGSP. |
| DECRYPTION SERVICE PROVIDER |
| DSP is used for generating the decrypted key when the user requests for the decryption of the encrypted key. Then the DSP asks for the ID and encrypted key of the user and then sends the decrypted key to the user. It is used for decrypting the ciphertext which is obtained from the user. When the data owner uploads the file which is in encrypted format, then the DSP will decrypt it when the authorized user who satisfies the access policy and who have suitable attributes requests for downloading the file. The DSP will then send the file in the decrypted format to the authorized user so that the user can gain access to that data. |
| STORAGE SERVICE PROVIDER |
| SSP is in charge of controlling the accesses from outside users to the storing data and providing corresponding contents services. All the uploaded data will be stored in Storage service provider. SSP will be in charge of controlling the access to that data from outside users. It will be storing all the data and provides the data only to authorized users.The files which are uploaded by the Data Owner will be stored in the SSP. When the authorized user wants to access that file, the SSP will then sends the file to the user so that user can download it by entering session password (OTP). |
| A. ELLIPTIC CURVE CRYPTOGRAPHY (ECC) |
| Using Elliptic Curve Cryptography (ECC) algorithm data is encrypted and decrypted. Elliptic curve cryptography is a set of algorithms for encrypting and decrypting data and exchanging cryptographic keys. ECC is an approach to publickey cryptography based on the algebraic structure of elliptic curves over finite fields. One of the main benefits in comparison with non-ECC cryptography is the same level of security provided by keys of smaller size. ECC is based on properties of a particular type of equation created from the mathematical group (a set of values for which operations can be performed on any two members of the group to produce a third member) derived from points where the line intersects the axes. |
| Equations based on elliptic curves have a characteristic that is very valuable for cryptography purposes: they are relatively easy to perform, and extremely difficult to reverse. An elliptic curve is the set of points that satisfy a specific mathematical equation. |
| The equation for an elliptic curve looks something like this: |
| y2 = x3 + ax + b |
| B. ALGORITHM OF ECC DIFFIE-HELLMAN KEY EXCHANGE |
 |
| C. PROPOSED ALGORITHM |
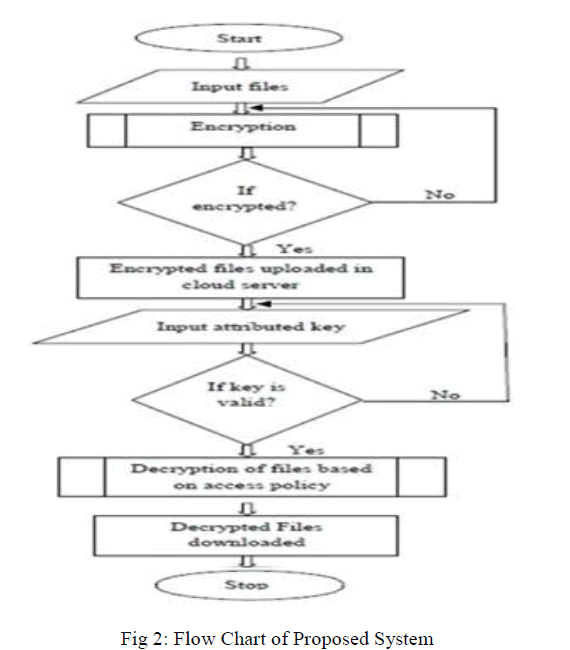
| The following algorithm is used in the proposed system |
| Step-1 The data owner logins the system using his ID and password. |
| Step-2 The data owner defines the access policy for the data which is to be placed on the public cloud. |
| Step-3 The data owner chooses the file to be uploaded and define the access policy for that file. |
| Step-4 The data owner defines the access policy using Attribute Based Encryption. |
| Step-5 The file gets encrypted using ECDH algorithm. |
| Step-6 The owner then finds out the checksum of the data which is being uploaded in order to provide checkability. |
| Step-7 The file then finally gets uploaded to the database on the cloud and the data owner gets the message after the file gets uploaded. |
| Step-8 The registered user logins to the system with the valid ID and key. |
| Step-9 The user then search for the file he wants to download. |
| Step-10 The file will be displayed to the user only if he is having suitable attributes that satisfy the access policy, otherwisethe file will not be displayed. |
| Step-11 Then in order to download the file the user search for the key. |
| Step-12 The session key will be generated by KGSP to the user only if he is having suitable attributes. |
| Step-13 Then using the session key, the user requests for downloading of the file. |
| Step-14 Then DSP will decrypt the encrypted file which is placed on the database and returns the decrypted file to the user. |
| Step-15 Then the user will be able to download the file on the local machine. |
 |
IV. PERFORMANCE ANALYSIS |
| To evaluate the performance of CP-ABE outsourcing scheme, encryption time, key generation time and decryption time are calculated. The time taken by CP-ABE outsourcing scheme is calculated on Integrated Development Environment (IDE) Visual Studio (C#.Net) while the database is kept in Microsoft Azure Database. |
| Performance analysis is done by calculating Encryption and upload time, Decryption and download time and key generation time. Performance analysis is done using different file sizes and the results are obtained by noting down the time taken for encrypting those files with different sizes, time taken for decrypting those files and time taken for key generation. |
| A. ENCRYPTION AND UPLOAD TIME |
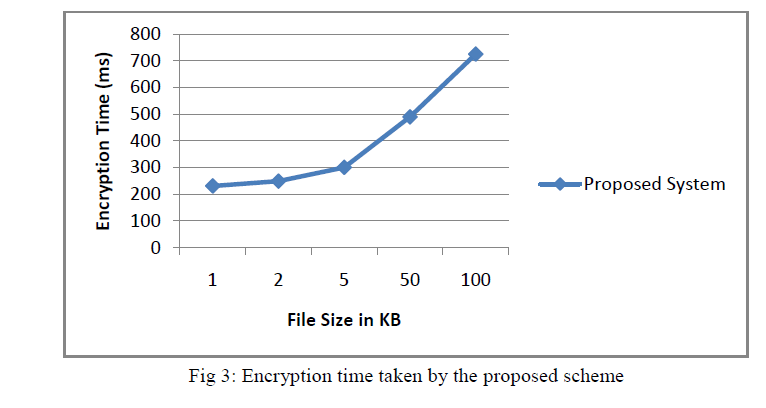
| To evaluate CPABE performance, I have measured time taken to encrypt and upload the file on the SQL Azure Database by using different file sizes—1 KB, 2 KB, 5 KB, 50 KB, 100 KB. To capture time used for encryption and uploading the file, i have used the following code. |
 |
| I have written this code in the essential class files of my project and then execute it. This code will take the current system time and then run the code and the query in it and then captures the time which it takes for doing so. Then it subtracts that system time from the time it captures and returns the result in the label which is placed for that purpose Fig 3 shows the encryption time taken by the proposed system i.e. outsourcing ABE. It is clear from the figure that as the file size increases, the encryption time also increases. |
| Here the encryption time indicates the time to encrypt and upload the file on the Microsoft Azure. |
| B. KEY GENERATION TIME |
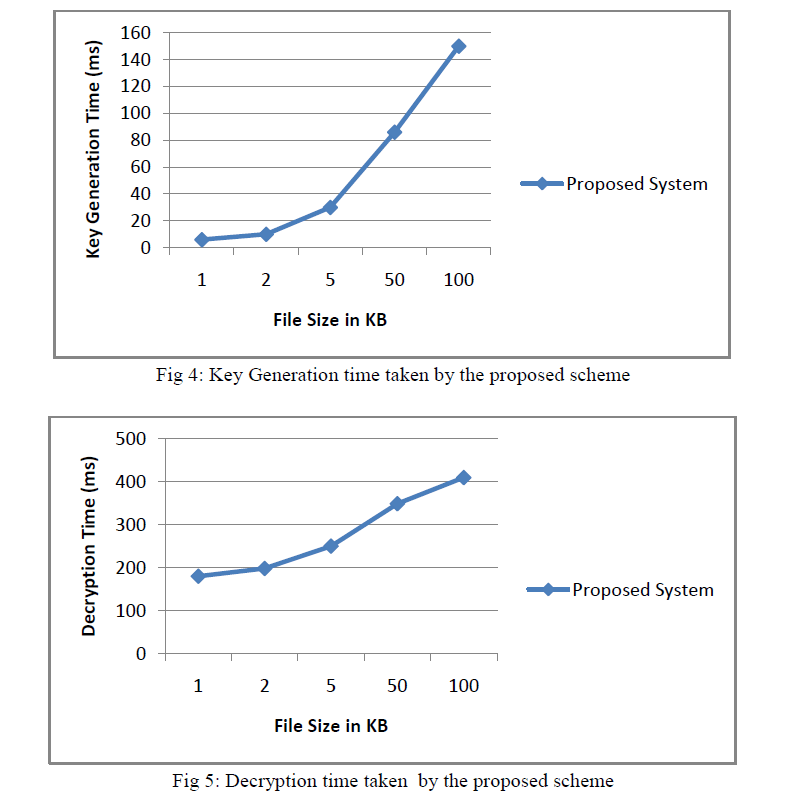
| The Key generation time returns the time to generate the keys. I have used same files for performing tests in order to capture the time taken to generate the secret key. Using this key only the users will be able to download the files. The file sizes which I have used for testing are 1KB, 2KB, 5KB, 50KB, 100KB. Fig 4 shows the key generation time taken by the proposed scheme. |
| C. DOWNLOAD AND DECRYPTION TIME |
| Same files were used for performing tests for capturing time taken to download and decrypt these files using both proposed system (CPABE) and existing system (IBE). |
| Same files were used for performing tests for capturing time taken to download and decrypt these files using both proposed system (CPABE) and existing system (IBE). |
| -Encrypted file is downloaded from file storage service to local machine. |
| -Requested file is decrypted using private key of the user. |
| It is shown in Fig 5 that the decryption time of Outsourcing ABE increases as the file size increases. |
 |
 |
VI.CONCLUSION AND FUTURE WORK |
| A new outsourced ABE scheme is proposed that simultaneously supports outsourced key-issuing and decryption. With the aid of KGSP and DSP, this scheme achieves constant efficiency at both authority and user sides. Performance analysis shows that the proposed system i.e. outsourced ABE takes less encryption time and decryption time and the time increases as the file size increases. The time taken by the proposed scheme for encryption and decryption and key generation is in milliseconds.To sum up, this outsourced ABE scheme achieves efficiency at both attribute authority and user sides during key-issuing and decryption without introducing significant overhead compared to the original approach. |
| In this paper, the data owner acts as the only authority in every cryptosystem. In large-scale systems, it is desirable to provide decentralized access control in the sense that the existence of multiple authorities in an application is allowed. |
| When encryption provides data confidentiality, it also greatly limits the flexibility of data operation. To address this issue, it is needed to combine ABE with cryptographic primitives such as searchable encryption, private information retrieval and homomorphic encryption to enable computations on encrypted data without decrypting. |
References |
|