ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
| K.Kavitha Assistant Professor, Department of MCA , Adhiparasakthi Engineering College, Melmaruvathur,Tamilnadu,India |
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
Cloud is a metaphor to describe web as a space where computing has been preinstalled and exist as a service; such as information ,infrastructure , applications, storage and processing power exist on the web ready to be shared. To the users, cloud computing is a Pay-per-Use-On-Demandmode that can easily access shared IT resources through the Internet. Where the IT resources include server, storage, network, application, service and so on and they can be deployed with much fast and easy manner and less management and also provide interactions with serviceproviders. Cloud computing can much improve the availability of IT resources and owns many advantages over other computing techniques.Cloud computing is the emerging technology which emphasizes commercial computing. Cloud is a platform providing dynamic resource pools, virtualization & high availability. It‟s the concept implemented to overcome our regular computing problem like hardware software resource availability and related aspects. Cloud computing makes it easy to have high performance computing. Cloud computing is a service which is easily available on market when you want it you can start the service and when you don't want you stop the service and you pay it for what you use, you need a computer or a laptop to access the Cloud Services.Cloud services are becoming popular in terms of distributed technology because they allow cloud users to rent well-specified resources of computing, network, and storage infrastructure. Users pay for their use of services without needing to spend massive amounts for integration, maintenance, or management of the IT infrastructure.
Keywords |
| Cloud Computing, IAAS, PAAS, SAAS, Security. |
INTRODUCTION |
| In October 2007, Cloud computing became “popular” in the presence of other computing techniques used before (Wikipedia, 2012 a; Foster &Kesselman, 1998; Raleigh & Armonk, 2007; Naone, 2007; Reimer, 2007). The popularity was due to the partnership of IBM and Google to work under a domain ( Lohr., 2007; View, Calif& Armonk., 2007) followed by the entry of (Wikipedia, 2012b; Vouk, 2008). Cloud Computing was a new idea that uses internet and remote servers for maintaining data and applications. It offers through internet dynamic virtualized resources, bandwidth and on-demand softwareâÃâ¬ÃŸs to consumers and promises the distribution of many economical benefits among its adapters. It helps consumers to reduce the usage of hardware, software license and system maintenance. Hence by using internet consumers are able to use service application on clouds (Ren& Lou, 2009). Moreover by using cloud computing consumers can get benefit in the form of cost, on-demand self services that reply rapidly, and can access broad network. |
 |
RELATED WORKS |
| Gartner 2008 identified seven security issues that need to be addressed before enterprisesconsider switching to the cloud computing model. They are as follows: (15) privileged user access- information transmitted from the client through the Internet poses a certain degree of risk,because of issues of data ownership; enterprises should spend time getting to know theirproviders and their regulations as much as possible before assigning some trivial applications firstto test the water, (16) regulatory compliance - clients are accountable for the security of theirsolution, as they can choose between providers that allow to be audited by 3rd partyorganizations that check levels of security and providers that don't (3) data location – dependingon contracts, some clients might never know what country or what jurisdiction their data is located(18) data segregation - encrypted information from multiple companies may be stored on the samehard disk, so a mechanism to separate data should be deployed by the provider. (19) recovery -every provider should have a disaster recovery protocol to protect user data (6) investigativesupport - if a client suspects faulty activity from the provider, it may not have many legal wayspursue an investigation long-term viability - refers to the ability to retract a contract and alldata if the current provider is bought out by another firm.[2] The Cloud Computing Use CaseDiscussion Group discusses the different Use Case scenarios and related requirements that mayexist in the cloud model. They consider use cases from different perspectives includingcustomers, developers and security engineers.[17] ENISA investigated the different security risksrelated to adopting cloud computing along with the affected assets, the risks likelihood, impacts,and vulnerabilities in the cloud computing may lead to such risks.[18] Balachandra et al, 2009discussed the security SLAâÃâ¬ÃŸs specification and objectives related to data locations, segregationand data recovery.[5] Kresimir et al, 2010 discussed high level security concerns in the cloudcomputing model such as data integrity, payment and privacy of sensitive information.[21] Berndet al, 2010 discuss the security vulnerabilities existing in the cloud platform. The authors groupedthe possible vulnerabilities into technologyrelated, cloud characteristics-related, security controls related.[21] Subashini et al discuss the security challenges of the cloud service delivery model,focusing on the SaaS model.[22] et al, (2010) discussed the management of security inCloud computing focusing on GartnerâÃâ¬ÃŸs list on cloud security issues and the findings from theInternational Data Corporation enterprise.[23] Morsy et al, 2010 investigated cloud computingproblems from the cloud architecture, cloud offered characteristics, cloud stakeholders, and cloudservice delivery models perspectives. A recent survey by Cloud Security Alliance(CSA)&IEEE indicates that enterprises across sectors are eager to adopt cloud computing butthat security are needed both to accelerate cloud adoption on a wide scale and to respond toregulatory drivers. It also details that cloud computing is shaping the future of IT but the absenceof a compliance environment is having dramatic impact on cloud computing growth.[25] Severalstudies have been carried out relating to security issues in cloud computing but this workpresents a detailed analysis of the cloud computing security issues and challenges focusing onthe cloud computing deployment types and the service delivery types. |
CLOUD COMPUTING |
| Cloud computing is a computing model based on networks, especially based on the Internet, whose task is to ensure that users can simply use the computing resources on demand and pay money according to their usage by a metering pattern. Therefore, a new business model is being created where the services it provides are becoming computing resources. In recent years, cloud computing as a new kind of advanced technology accelerates the innovation for the computer industry. Cloud computing is a computing model based on networks, especially based on the Internet, whose task is to ensure that users can simply use the computing resources on demand and pay money according to their usage by a metering pattern similar to water and electricity consumption. Therefore, it brings a new business model, where the services it provides are becoming computing resources[5]. |
A. TYPES OF CLOUD |
| There are four types of cloud computing models listed by NIST (2009): private cloud, public cloud, hybrid cloud and community cloud[2][3]. |
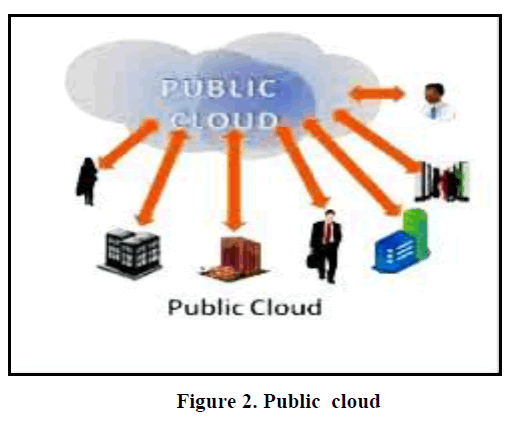
| 1. Public Cloud: it is for the general public where resources, web applications, web services are provided over the internet and any user can get the services from the cloud,. Public Organizations helps in providing the infrastructure to execute the public cloud. |
 |
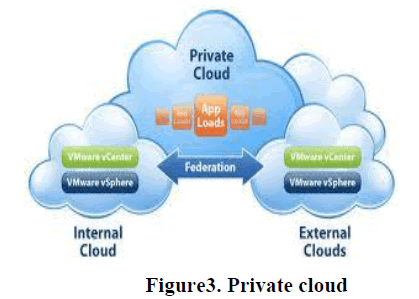
| 2. Private Cloud: It is used by the organizations internally and is for a single organization, anyone within the organization can access the data, services and web applications but users outside the organizations cannot access the cloud. Infrastructure of private cloud are completely managed and corporate data are fully maintained by the organization itself.[7] |
 |
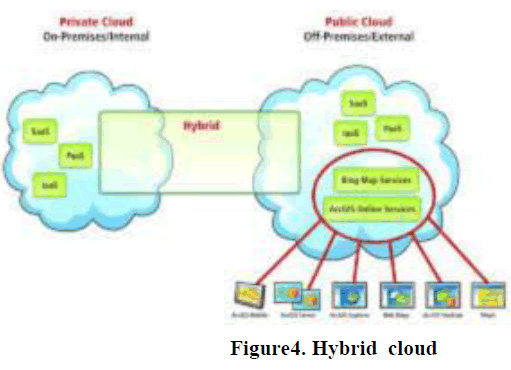
| 3. Hybrid Cloud: The Cloud is a combination of two or more clouds (public, private and community). Basically it is an environment in which multiple internal or external suppliers of cloud services are used in various environmnts. It is being used by most of the organizations (IBM and Junipers Network, 2009).I |
 |
| 4.Community Cloud: The cloud is basically the mixture of one or more public, private or hybrid clouds, which is shared by much organization for a single cause (mostly security).Infrastructure is to be shared by several organizations within specific community with common security, compliance objectives. It is managed by third party or managed internally.Its cost is lesser then public cloud but more than private cloud.[2] |
 |
CLOUD SERVICE MODELS |
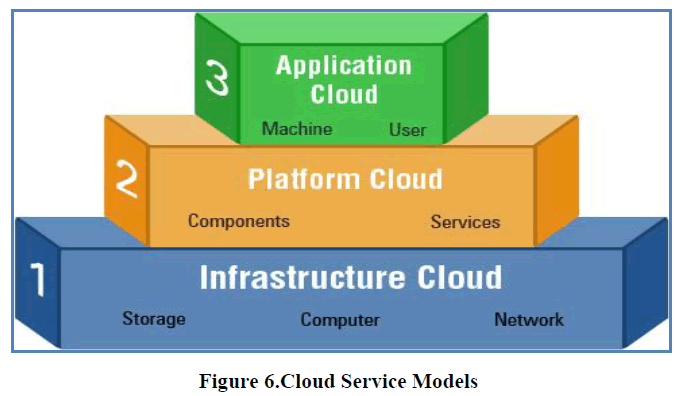
| Once a cloud is established, how its cloud computing services are deployed in terms of business models can differ depending on requirements. Cloud service delivery is divided among three archetypal models and various derivative combinations [20]. The three fundamental classifications are often referred to as the “SPI Model,” where „SPIâÃâ¬ÃŸ refers to Software, Platform, Infrastructure (as a Service), respectively[5]. |
1. Infrastructure as a Service (IaaS) |
| The infrastructure cloud provides storage and compute resources as a service which can be used by developers and IT organizations to deliver business solutions. IaaS has evolved from virtual private server (vps) concept. It provides complete flexibility to consumers in choosing desktops, servers or network resources. Consumers can customize the entire infrastructure package by selecting CPU hours, storage space, bandwidth etc. Rather than buying expensive servers and taking headache of setting up the data centers, IaaS cloud helps business in reducing IT CAPEX and OPEX by big proportion.[12] |
| IaaS contains sub-categories: Public, Private and Combination. Public cloud consists of shared resources, managed by service provider. By contrast, private cloud provides secure access to your resources and managed by organization it serves. The hybrid cloud is maintained by both internal and external providers. |
| Basic characteristics of IaaS: |
| Resources distributed as a service |
| Dynamic, on-demand scaling of resources |
| Utility based pricing model |
| Concurrent users on a single piece of hardware |
| 2. Platform as a Service (PaaS) Next level up in the pyramid is Platform cloud. PaaS delivers development/operating environments as a service. It includes set of tools and services designed to make coding and deploying the applications quickly and efficiently. PaaS is similar to SaaS except that, rather than being software delivered over the web, it is a platform for the development/deployment of that software, delivered over the web. |
| Prime examples include Salesforce.com's Force.com, Azure from Microsoft and Google App Engine. |
Basic characteristics of PaaS: |
| Single environment to develop, test, deploy, host and maintain applications |
| Web based UI designing tools to create, modify, test and deploy different UI scenarios |
| Multi-tenant architecture facilitating concurrent users |
| Load balancing, security and failover capabilities for application to be deployed |
| OS and Cloud programming APIs to create new apps for cloud or to cloudify the current apps |
| Tools to handle billing and subscription |
3. Software as a Service (SaaS): |
| Top most layer of pyramid is functional layer or SaaS layer. This type of cloud delivers a single application through the browser to multiple users using a multitenant architecture. With SaaS, a provider sells an application to customers on license basis, in a “pay-as-you-go” model.[13] |
| On the customer side, they do not have to do upfront investment in servers or software development; on the provider side, with just one app to maintain, costs are low compared to conventional hosting. Salesforce.com, SRM, ERP as most common examples of SaaS based applications. |
| Characteristics of SaaS: |
| Centralized web based access to company and commercial software |
| Entire business process shifting to cloud giving superior services to client |
| No hassle of software upgrades and patches as they are managed by Service provider |
| Application Programming Interfaces (APIs) allow integration with different applications |
 |
BENEFITS OF CLOUD COMPUTING |
| As cloud computing [1][2] are booming in market, several major benefits have become evident. The following are some of the benefits for those who offer cloud computing-based services and applications [4][7]. |
| i). Cost Savings |
| The cloud promises to cut the cost of acquiring, delivering, and maintain computing power, a benefit of particular importance in times of economic uncertainty. By enabling SME to purchase only the computing services needed, instead of investing in complex and expensive IT infrastructures, SME can cut down the costs of developing, testing, and maintaining new and existing systems. |
| ii). Mobile Access |
| The cloud computing enables to access high-powered computing and storage resources for anyone with a network access device. Capabilities of cloud computing helps to facilitate Tele-network initiatives, as well as bolster an agencyâÃâ¬ÃŸs continuity of operations (COOP) demands. |
| iii). Scalability and Capacity |
| Cloud Computing main benefit is scalability and capacity. By using of public cloud we can scale up and won as per our requirement and the capacity also. But in private itâÃâ¬ÃŸs not possible. Traditional computing also doesnâÃâ¬ÃŸt support scalability. |
| iv). Resource Maximization |
| Cloud computing has reduce burden of IT resources to many companies and agencies by maximizing the resources from cloud computing pool. |
| v). Collaboration |
| Collaboration is a term where a group of people can work together through online. By using cloud computing environment online, collaboration is easier than before a good example is Google docs. |
vi). Customization |
| Cloud computing is a platform where we can modify to our needs with being redevelopment. It offers a platform for creating and amending applications to address a diversity of tasks and challenges. |
CLOUD COMPUTING CHALLENGES |
| i). Security and Privacy |
| The most challenging issue in cloud computing is security and privacy. Storing of data in cloud seems to less secure than any other else. High risk is seen where any third party might get access to data in cloud environment. Even our all data are stored in our own allocated space but as it shared publicly any intruder may try to access it for the safety private cloud is available[6]. |
| ii). Lack of Standards |
| Lots of standards development work is going on. Open grid forum, open cloud consortium is looking on this issue and working on cloud computing standards and practices. |
| iii). Continuously Evolving |
| User requirements are continuously evolving, as are the requirements for interfaces, networking, and storage. This means that a “cloud,” especially a public one, does not remain static and is also continuously evolving. |
| iv).Compliance Concerns |
| Question were ask by many user who want to adopt cloud computing is. What information is stored on a system? Where is the information stored? Who can access the system? What they canaccess? Is the access appropriate? CSP are having difficulty in answering question, a user from china will not like there data to be stored at India[8]. |
CONCLUSION |
| Cloud computing is a new term that is introduced in business environment where users can interact directly with the virtualized resources and safe the cost for the consumers. Cloud computing provides scalable and efficient means to manage IT resources in organizations. It has several models to protect its data for the business users. An organization usedprivate clouds within its organization to prevent from loss of data. Cloud computing have several deploymentmodels that help in retrieving the information. SAAS, PAAS, IAAS are the three models for cloud computing.Security in cloud computing consist of security abilities of web browsers and web service structure The flexibility the cloud brings in has some disadvantages over privacy and security[9][10]. As and when the issues around security and privacy are elucidated cloud computing will be accepted widely. |
References |
|