ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
Dr.Prakash.H.Patil 1, Anuja A.Kokil 2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
We survey the performance analysis of the suboptimal detectors in terms of probabilities of detection and false alarm, and selection of detection threshold and number of samples. With the prior knowledge that the primary user is highly likely idle and the primary signals are digitally modulated, Here a Bayesian detector (BD) for digitally modulated primary signals to maximize the spectrum utilization, without the prior information on the transmitted sequence of the primary signals is proposed. The proposed method makes use of the prior statistics of PU activity and the signalling information of the PU such as symbol rate and modulation order to improve the SU throughput and the overall spectrum utilization of both PUs and SUs.
Keywords |
| Cognitive Radio, Spectrum Sensing, Bayesian Detector |
INTRODUCTION |
| Wireless communications and the utilization of the radio frequency spectrum have witnessed a tremendous increase during the past few decades. The multitude of different wireless devices and technologies, the dramatic boom in the number of wireless subscribers, the continuous demand for higher data rates , and the advent of new applications are all reasons for the radio frequency spectrum becoming more and more crowded. Wireless communication and radar systems must collect information about the radio. spectrum in order to adapt their operation and behaviour to provide a better match to the prevailing conditions. The radio frequency spectrum is divided to frequency bands that are then allocated to different systems. The allocations are decided by the regulatory authorities in each country such as the Federal Communications Commission (FCC) in the United States [1]. Most of the spectrum has already been allocated to different systems. Moreover, the allocations vary from country to country. Whenever a new wireless system is introduced a frequency band needs to be made available for it, which may require worldwide collaboration. Hence, although the current frequency allocation policy guarantees low interference because each system operates in a different band, it is also very rigid and inflexible. This has resulted in apparent spectrum scarcity that realizes as heavy congestion in certain frequency bands. However, many of the frequency bands have been allocated to legacy systems that are rarely used or to systems whose degree of frequency band utilization varies sharply from time to time and location to location. Hence, there is still plenty of spectrum available. Merely because of the fixed frequency allocation policy it cannot be exploited. Consequently, the radio frequency spectrum is very inefficiently utilized depending on time, frequency band, and location. Thus, spectrum sensing is becoming increasingly important to modern and future wireless communication and radar systems for identifying underutilized spectrum and characterizing interference, and consequently, achieving reliable and efficient operation. Software defined radio (SDR) is the technique of processing wireless radio communication signals completely inside a computer using software. Traditionally, radios are built in hardware to allow for real- time processing of the radio signals. In order to create a new instance of a traditional radio requires a large amount of time, effort, and cost to develop this hardware. Advances in processor technology, such as increased CPU processing speeds, and multi-core computer architectures, allows this same development for a new radio to occur, in software, on general-purpose processors. By developing a radio in software, we can reduce these previously mentioned problems. Also, a SDR has the relation to dynamically reconfigure radio parameters, such as modulation family type, and this ability is a desirable feature for highly dynamic radio environments. Cognitive radios are radios that are capable of learning their surrounding environment in order to adapt its internal parameters to improve its ability to reliably communicate. The observed environment will guide the decision making process of a cognitive radio. |
| Determining when and where, in time and in frequency, to transmit, or sensing other radio interferers are examples of the types of decisions that can be made by a cognitive radio. Spectrum sensing is the process used by a cognitive radio to identify available channels of both licensed and unlicensed spectrum in order to wirelessly communicate. The frequency spectrum is a dynamic system that changes with time and location. The availability of a channel in the licensed spectrum depends on the activity of the primary user, which has priority to the licensed spectrum. The underutilization of the licensed spectrum presents an opportunity for secondary communication systems to transmit on these unused channels. This type of capability is the research motivation of spectrum sensing. For example, the IEEE 802.22 standard requires a secondary user to vacate the channel or reduce power within two seconds of a primary user becoming active. Thus, the cognitive radio must quickly detect this appearance to prevent interfering with the primary user, which implies that a cognitive radio must constantly perform spectrum sensing. |
 |
| Cognitive radio is a term that refers to an intelligent radio that is aware of its surrounding environment. Moreover, a cognitive radio is capable of learning and adapting its behaviour and operation to provide a better match to its surrounding environment as well as to the user’s needs. Learning is based on the feedback received from the environment. The feedback is realized as the outcome of the cognitive radio’s decisions and actions. Current spectrum regulation is based on a fixed frequency allocation policy |
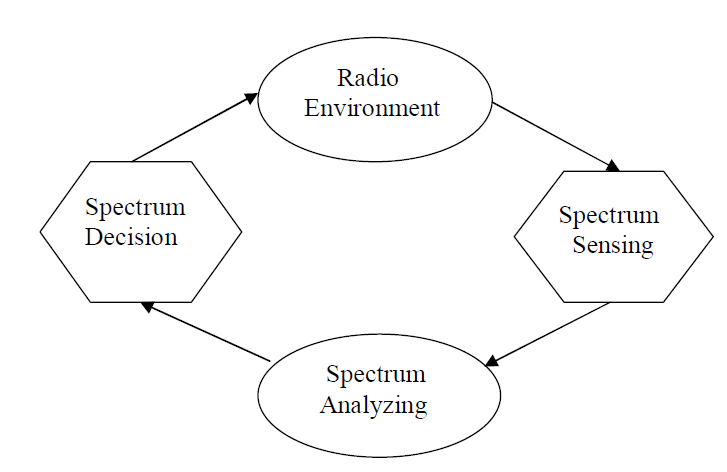 |
| It reports that the temporal and geographical variations in the utilization of the assigned spectrum range from 15% to 85%. [2].The measurement results in suggest that most of the allocated frequencies (ranging from 80 MHz to 5850 MHz) are heavily under-utilized except for the frequency bands allocated for broadcasting and cell phones. The similar observation in also shows that there is a high probability that the primary users are likely idle for most of the time. Using cognitive radios (CRs), the secondary users (SUs) are allowed to use the spectrum originally allocated to primary users (PUs) as long as the primary users are not using it temporarily this operation is called opportunistic spectrum access (OSA). To avoid interference to the primary users, the SUs have to perform spectrum sensing before their attempts to transmit over the spectrum. Upon detecting that the PU is idle, the SUs can make use of the spectrum for transmission, and the overall utilization efficiency of the spectrum is enhanced. Many detection methods, for example, energy detector , covariance based detector , cyclostationarity based detector , matched filter based detector and wavelet-based sensing method [1][3], have been proposed and studied extensively . Energy detector and covariance based detector assume that the primary signals are random. Cyclostationarity based detection exploits the cyclostationarity features of the primary signals, however, it does not make full use of the characteristics of the modulated signals. Matchedfilter based detection requires the complete knowledge of the primary signals, which makes it infeasible for practical applications. In this paper, we survey a Bayesian detector (BD) for digitally modulated primary signals to maximize the spectrum utilization, without the prior information on the transmitted sequence of the primary signals. The proposed method makes use of the prior statistics of PU activity and the signaling information of the PU such as symbol rate and modulation order to improve the SU throughput and the overall spectrum utilization of both PUs and SUs. It is shown that the Bayesian detector has the exact same structure as Neyman- Pearson detector , but the design principle of Neyman- Pearson detector is to maximize the detection probability for a given maximal false alarm probability, which results in the difference in detection threshold selection for the two schemes. Spectrum sensing is a key component in cognitive radio networks. Recently there has been intense research progress in eigenvalue based sensing method based on distribution of the largest eignvalue of the covarience matrices described. |
II.SYSTEM DESIGN |
| In this paper we have referred the mathematical model of Shoukang Zheng[2],In spectrum sensing, there are two hypotheses: âÃâÃâ¹0 for the hypothesis that the PU is absent and H1 for the hypothesis that the PU is present. There are two important design parameters for spectrum sensing: probability of detection (PD), which is the probability that SU accurately detects the presence of active primary signals, and probability of false alarm (PF ), which is the probability that SU falsely detects primary signals when PU is in fact absent. We define spectrum utilization as |
| P( H0)( 1 – PF )+P( H1)PD (1) |
| and normalized SU throughput1 as |
| P(H0)( 1 – PF ) (2) |
| Respectively. Note that P(H1)PD is PU throughput when there are primary signals and the SUs detect the presence of the primary signals. |
| To determine whether the spectrum is being used by the primary user, the detection statistic TD is compared with a predetermined threshold ÃÂõ. Probability of false alarm PF is the probability that the hypothesis test chooses âÃâÃâ¹1 while it is in fact H0: |
| PF = P(TD > ÃÂõ| H0). |
| Probability of detection PD is the probability that the rest correctly decides H0 when it is H1: |
| PF = P(TD > ÃÂõ| âÃâÃâ¹1). |
A. SIGNAL MODEL |
| Following the signal model, we consider time-slotted primary signals where N primary signal samples are used to detect the existence of PU signals. The PU symbol duration is T which is known to the SU and the received signal r(t) is sampled at a rate of 1/T at the secondary receiver. For MPSK modulated primary signals, the received signal of k-th symbol at the CR detector, r(k) |
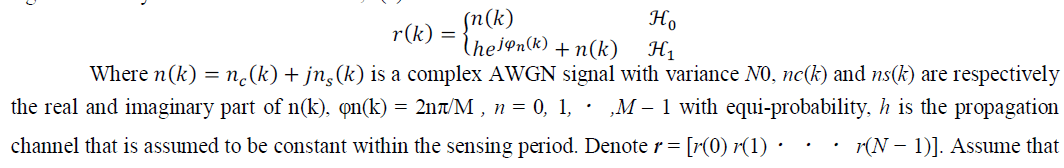 |
| the SU receiver has no information with regards to the transmitted signals by the PU and φn(k), k = 0, 1, ãÃÆû ,N − 1 are independent and identically distributed (i.i.d.) and independent of the Gaussian noise. |
| The detection statistics of energy detector (ED) can be defined as the average energy of observed samples as |
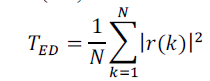 |
| Although energy detector does not require the knowledge of the symbol rate, we assume that the sample rate is identical to the symbol rate. |
| identical to the symbol rate. It is well-known that the optimal detector for binary hypothesis testing based on Bayesian rule or Neyman- Pearson theorem is to compute the likelihood ratio and then make its decision by comparing the ratio with the threshold. The likelihood ratio test (LRT) of the hypotheses and can be defined as |
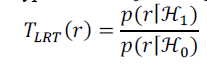 |
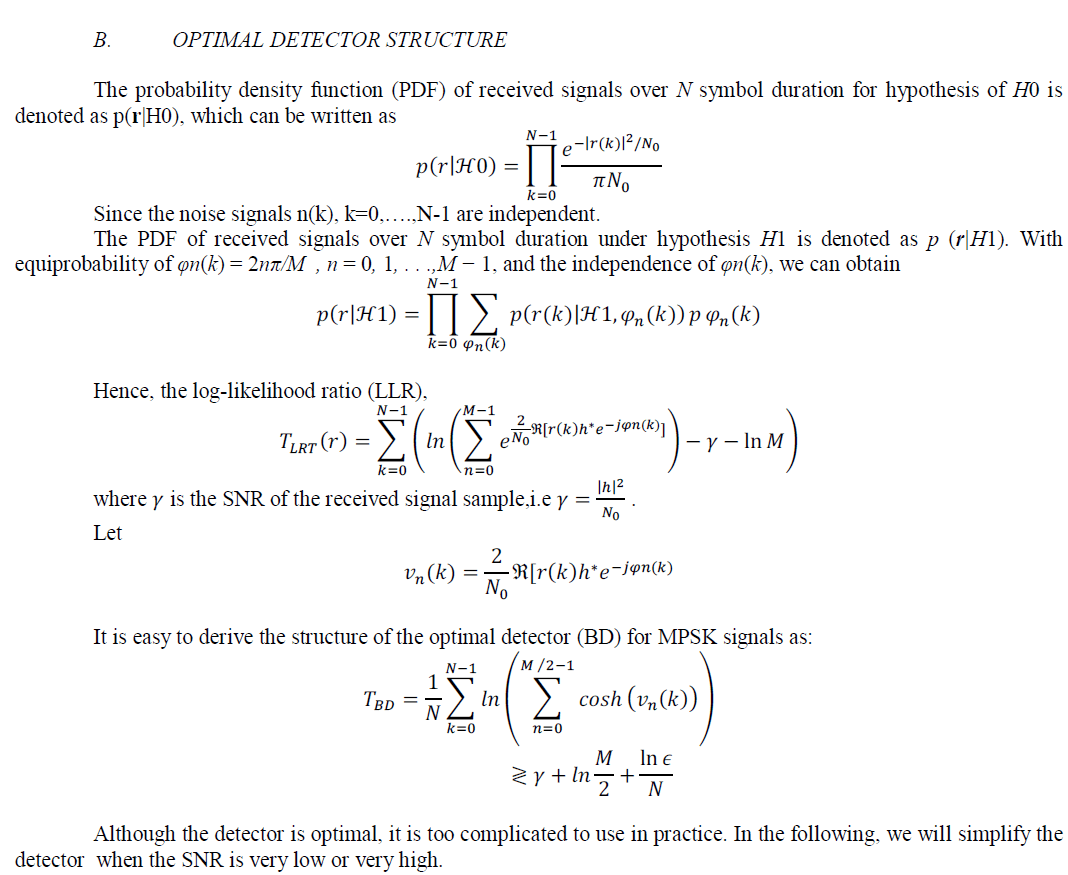 |
 |
 |
III.APPLICATIONS |
A. APPLICATION |
| Geo-location and Networking Applications: |
| New capabilities are enabled when a CR knows where it is and where it is going. This information may be obtained through dedicated sensors such as an Inertial Navigation Unit, a GPS receiver, or through relative geo-location techniques built into the waveforms or configuration of an SDR channel to receive and process GPS signals. |
| An inertial navigation unit keeps track of location relative to an initial known location through the use of accelerometers and time. The accuracy of this technique deteriorates in time, but re-synchronization with GPS receivers mitigates this characteristic. Through a combination of Inertial Navigation and GPS, a CR can sense its location with good precision, even indoors. from using the CR. Since a radio is usually used for voice communications, there is a microphone in the system. The captured signal is encoded with a VoCoder and transmitted. The source radio can authenticate the user and add the known identity to the data stream. |
| Authentication Applications: |
| Cognitive Radio can learn the identity of its user(s). Authentication applications can prevent unauthorized users At the destination end, decoded voice can be analyzed for the purposes of authentication. Recently cell phones have been equipped with digital cameras. This sensor coupled with facial recognition software may be used to authenticate a user |
ADVANTAGES |
| ïÃâ÷ Useful for high-rate, emerging wireless communication |
| systems such as WiMAX. |
| ïÃâ÷ Spectral efficiency. |
| ïÃâ÷ Utilization of spectrum |
IV.CONCLUSION |
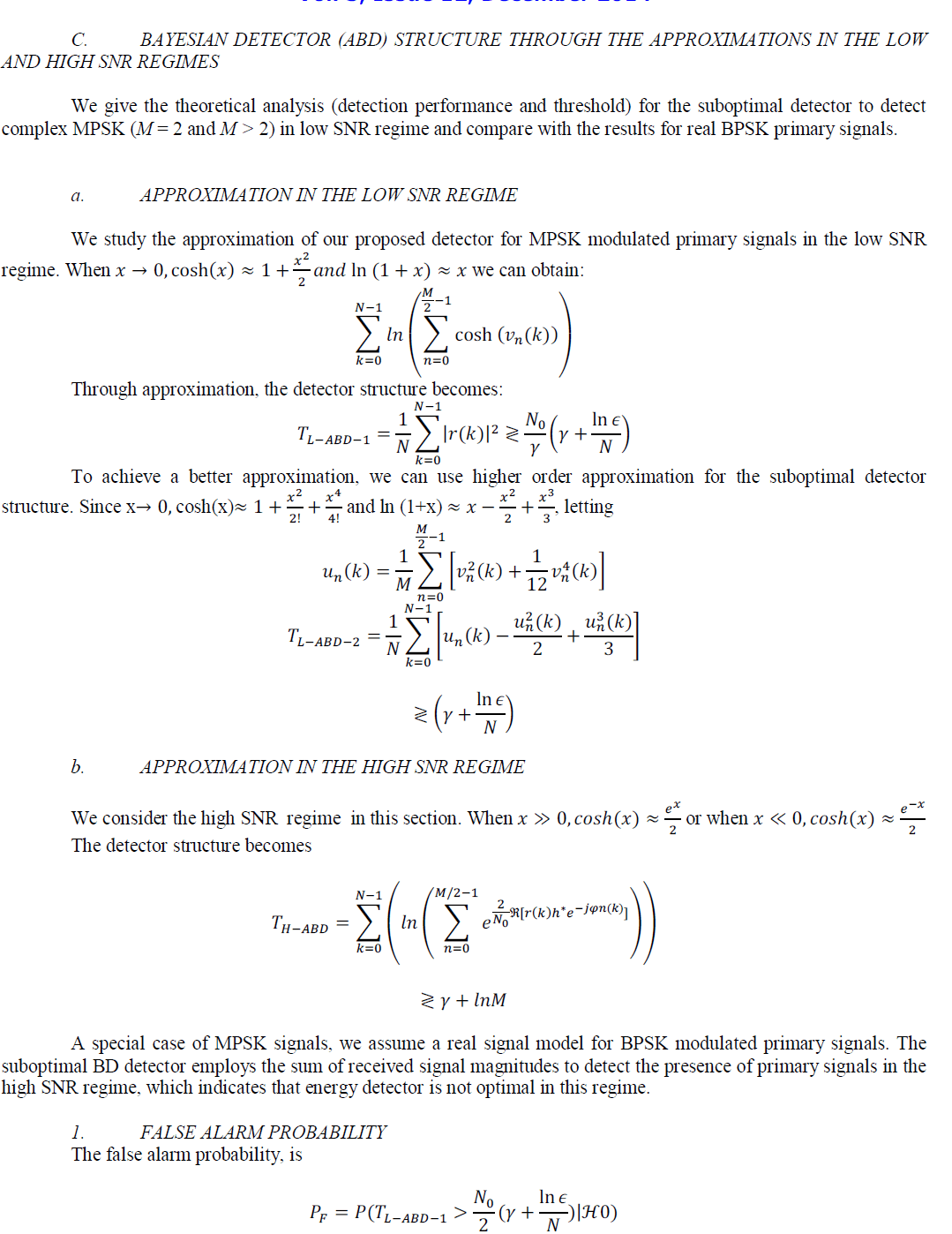
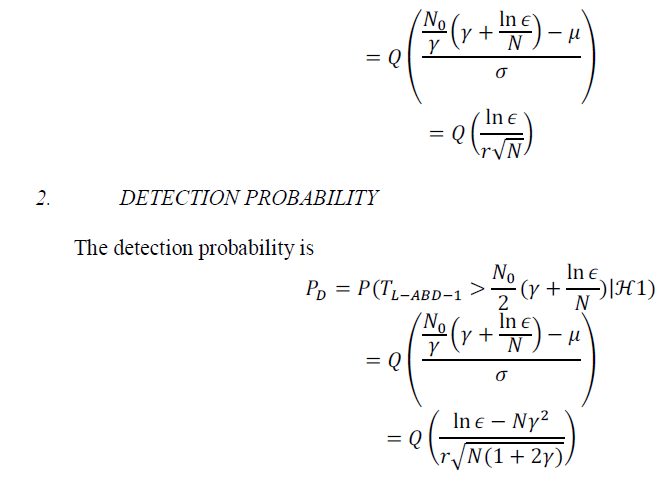
| In this paper, we surveyedon an optimal Bayesian detector structure to detect known order MPSK modulated primary signals over AWGN channels, based on Bayesian decision rule. Through approximations, we find out the suboptimal detector structure for BPSK signals, which is an energy detector in the low SNR regime and applies the sum of signal magnitudes in the high SNR regime. For MPSK (M > 2) signals, the suboptimal detector is also an energy detector in low SNR regime. We analyses the suboptimal detector for complex MPSK signals and real BPSK signals in the low SNR regime, in terms of probabilities of detection and false alarm, detection threshold and number of samples. The proposed Bayesian detector has the performance similar to the energy detector that is designed to maximize the spectrum utilization, for complex MPSK signals in the low SNR regime. But they are different in high SNR regime, where Bayesian detector has a better performance in terms of spectrum utilization and secondary users’ throughput. |
References |
|