ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
| N.Anantharaj1 M-TECH (IT) Final Year, Department of IT, Dr.Sivanthi Aditanar College of Engineering, Tiruchendur, Tamilnadu, India1 |
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
As society has become increasingly depend upon digital images to communicate visual information. Image would provide better impact in convincing someone of something rather than pure description by word. Nowadays one of the principal means for communication is digital visual media. Digital image widely used in various field like medical imaging, journalism, scientific manipulation and digital forensics. Digital image forgery creates more problems on real world. In most digital image communication the main problem is its authenticity. Digital image forensics is a brand new research field which aims at finding the authenticity of images by recovering information. There are several different tampering attacks but, surely, one of the most common and immediate one is copy-move. COPY-MOVE forged detection identified by the visual local feature of images. SIFT method are find the local feature and cluster the related close points, and Geometric transformation are used to identified the similarity and dissimilarity of the images. Then identified the Tampering on images. This Tampering detection is used to identify image Authentic or not.
INTRODUCTION |
| Digital Technology (image and video) has matured to become predominant technology for creating, processing, transmitting and storing a information form of knowledge and intellectual assets. Multidimensional knowledge and intellectual assets are produced and represented in various forms such as audio, video, text , image , all together we can call it as a multimedia forms, finally all forms are stored as a digital bits and byte forms i.e.) digital content . Digital images are widely used in our society. From newspapers to the magazines, scientific journals, physicians in medical field, fashion industries, court rooms and other outlets heavily depend on digital images. Information integrity is fundamental in many fields. |
| Today’s digital technology has begun to erode this trust. Even though tampering with photograph is not new, during past few years, tampered images are appearing with frequency and sophistication, this development of increasingly sophisticated digital image processing software; it has been becoming easy to create image forgery from one or multiple images without leaving visible clues. |
| Digital crime is growing at a rate that far ahead of defensive measure. This crime has caused many problems, including legal and ethical issues. Multimedia forensics deals with developing technological instruments which generally allow determining, without any additional information inside the image (e.g. Watermark). |
II. HISTORY OF IMAGE FORGERY IN WORLD |
| Image forgery’s are not new, history has recorded that is happen on early as on 1840. Hippolyta banayrd, the first person to create fake image. |
| In 1860, this nearly iconic portrait (in the form of a lithograph) of U.S. President Abraham Lincoln is a composite of Lincoln’s head and the Southern politician John Calhoun’s body. |
| In 1865, In this photo by famed photographer Mathew Brady, General Sherman is seen posing with his Generals. General Francis P. Blair (far right) was added to the original photograph. The photo on the left is another image from the same sitting, at which General Blair was not in attendance. |
| In 2011,Osama bin Laden was killed by US forces in Pakistan on May 2nd, 2011. A photo reported to be of Bin Laden was shown on Pakistani television. This photo[FIGURE1] was also published in the British newspapers Mail, Times, Telegraph, Sun, and Mirror. The photo, however, is a composite of two separate photos: The lower portion is of an alive Bin Laden, and the top portion is of another person. |
 |
| Figure 2.1Clone and Paste Fake Image For Bin Laden |
| Figure 2.1 shows the combination of images clearly show that the beard and the lower part of the image was most probably cloned and pasted on the image of a body that doesn't belong to bin Laden, making the picture on the left a fake |
III. EXISTING SYSTEM |
| As discussed earlier, copy-move manipulations involve concealing or duplicating one region in an image by overlaying portions of the same image on it In order to address the problem, researchers have developed various techniques which can be classified in to two main categories: block-based and visual feature-based methods. |
Block Based Method |
| These methods seek a dependence between the image original area and the pasted one, by dividing the image into overlapping blocks and then applying a feature extraction process in order to represent the image blocks through a lowdimensional representation. Different block-based representations have been previously proposed in the literature such as principal component analysis (PCA) discrete cosine transform (DCT) and discrete wavelet transform (DWT) for both tasks of copy-move detection and image splicing. Recently, in the study of the authors proposed a duplication detection approach that can adopt two robust features based on DWT and kernel principal component analysis (kPCA). A different kind of features are used in fact the authors choose the averages of red, green and blue components with other four features, computed on overlapping blocks, obtained by calculating the energy distribution of luminance along four different directions. |
| Recently, methods more robust to reflection, rotation and scaling have been proposed in the literature. In overlapping blocks of pixels are mapped into log-polar coordinates, and then summed along the angle axis, to obtain a onedimensional descriptor invariant to reflection and rotation. |
IV. PROPOSED METHOD |
| In this paper, we are interested in studying the copy-move forgery detection on scaling and transformation image based on the SIFT features and k-means clustering. The first step consists of SIFT feature extraction and key point matching, the second step is devoted to the clustering and forgery detection, while the third one localizes the copied region, if a tampering has been detected. |
| The proposed system is based on SIFT algorithm to extract feature and identified the key points and clustering. Geometric transformation applied to rotation and scaling. |
V. MODULE |
| 1. Sift Feature Extraction And Matching |
| 2. Clustering And Forgery Detection |
| 3. Duplicated Region And Localization |
| 4. Localization Result |
MODULE DESCRIPTION |
| 1)Sift Feature Extraction And Matching |
| SIFT is (Scale Invariant Feature Transform) used to match the image based on the feature key points (scale and rotation invariance). The SIFT algorithm is one of the most widely used methods for image feature extraction. Sift algorithm are used to find the key points on the images,in this method include the sift description and sift descriptor.sift feature are discard the low response features |
| 2) Clustering And Forgery Detection |
| One of the most frequently used local features are SIFT features. They are quite robust and invariant to translation, scaling and rotation. We might want to observe an image as a set of objects in a scene. K-means is one of the simplest unsupervised learning algorithms that solve the well known clustering problem. The procedure follows a simple and easy way to classify a given data set through a certain number of clusters (assume k clusters) fixed a priori. The main idea is to define k centroids, one for each cluster. These centroids should be placed in a cunning way because of different location causes different result. So, the better choice is to place them as much as possible far away from each other. The next step is to take each point belonging to a given data set and associate it to the nearest centroid. When no point is pending, the first step is completed and an early group age is done. |
| 3)Duplicated Region And Localization |
| Bag of feature are used to find the value key points after finding the key points a cluster is formed by key point and mean is calculated by using the set key point which are present in cluster. A geometric transformation is an image processing operation that redefines the spatial relationship between points in an image .This transformation are provide the Transformation applied on the coordinates of the pixels. In forensic hash table in the values of on image is compared with values presented in bag of feature. The value in both are same or above or below some threshold value are accepted and Similar images displayed. |
| 4) Localization Result |
| Feature Extraction process show the related image on the database and then compare with the input image and show the tampered area or clone area |
VI. RESULT |
| In this proposed method provide the result on the copy-move forgery detection on the digital images. |
| In this Section, snapshoot of my project is briefly explained are as follows, |
 |
| Fig 6.1: Input image |
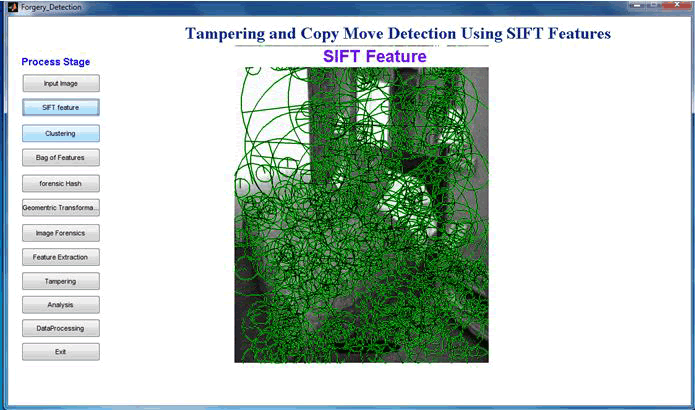 |
| Fig 6.2: Sift feature |
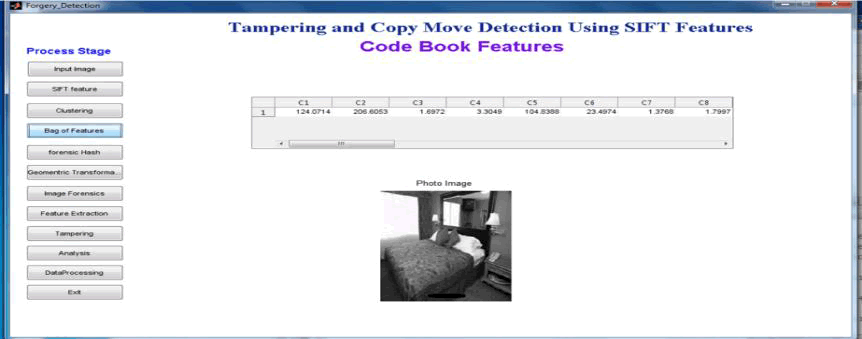 |
| Fig 6.3 : Bag of feature |
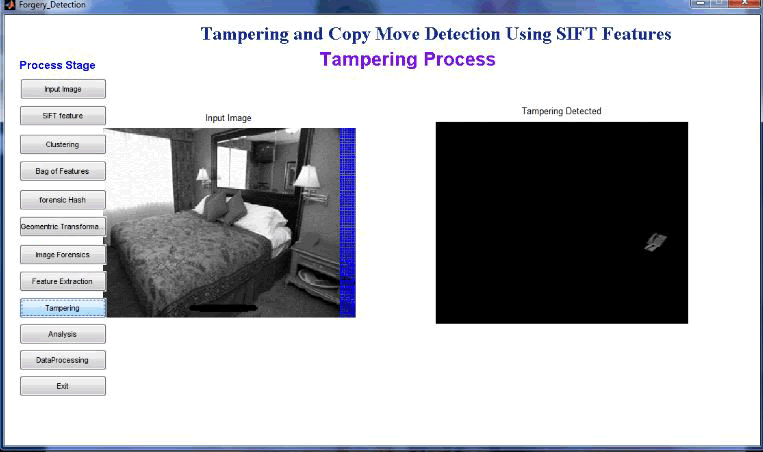 |
| Fig 6.4: Clone area localization |
VII. CONCLUSION |
| Digital images have been widely used in our daily life However, with the wide availability of sophisticated photoediting software’s and the ease of distributing digital images thorough internet. The main novelty of the works introducing detect the copy-move image forgery. And also this new techniques based on SIFT feature to detect the local feature of image and effective clustering. Geometric transformation are overcome the rotation, scaling and detect the multiple cloning. Experimental tests have been carried out on different datasets containing various types of fake and real images. Result shows that the proposed method outperforms other similar techniques. As part of our future work is examining copy-move image forgery to identify tampered region on reduce the false match rate. |
References |
|