ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
| Pooja P* M.Tech Student, Dept. of Computer Science and Engineering, STJIT, Ranebennur, India |
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
With fast-growing consumer demands and rapidly-developing mobile technologies, portable mobile devices are becoming a necessity of our daily lives. However, existing mobile devices rely on the wireless infrastructure to access Internet services provided by central application providers. This architecture is inefficient in many situations and also does not utilize abundant inter device communication opportunities in many scenarios. This paper proposes the human network (HUNET), a network architecture that enables information sharing between mobile devices through direct interdevice communication. We design B-SUB, an interest-driven information sharing system for HUNETs. In B-SUB, content and user interests are described by tags, which are human-readable strings that are designated by users. An experiment is performed to demonstrate the effectiveness of this tag-based content description method. To facilitate efficient data dissemination, we invent the Temporal Counting Bloom filter (TCBF) to encode tags, which also reduces the overhead of content routing. Comprehensive theoretical analyses on the parameter tuning of B-SUB are presented and verify B-SUB’s ability to work efficiently under various network conditions. We then extend B-SUB’s routing scheme to provide a stronger privacy guarantee. Extensive real-world trace-driven simulations are performed to evaluate the performance of BSUB, and the results demonstrate its efficiency and usefulness.
Keywords |
| Content-based publish/subscribe, interest-driven information sharing, human network, bloom filter |
INTRODUCTION |
| Recently, a new architecture of networking portable wireless devices has emerged, which is called the delay tolerant networks (DTNs). DTNs adopt a “store-carry and- forward” model, which significantly expands the communication capability of mobile device. Driven by the new application demands and the limitations of the existing architecture, we envision a new type of dynamic networking service called human networks (HUNETs). Physically, a HUNET is composed of human-carried mobile devices, which have the same structure as DTNs. These devices use short-range wireless communication technologies, such as Wi-Fi or Bluetooth, to communicate with each other. Functionally, HUNETs enable information sharing between users in a completely decentralized manner without the aid of an wireless communication infrastructure. |
| We present B-SUB, an interest-driven information sharing system for HUNETs, which stands for the bloomfilter- based publish/SUBscribe. B-SUB is designed for small to medium sized networks composed of dozens of devices restricted in a limited physical area where interdevice communication opportunities are abundant. Typical application scenarios are researchers inside a conference room, students inside a department building, visitors in a recreation center, and so on. The distinctive features of B-SUB are as follows: First, B-SUB employs content-based networking to achieve infrastructure less communication. B-SUB routes and forward messages based on their content instead of addresses, which enables autonomous access to interested information for users without an end-to-end addressing mechanism. Second, BSUB is much more efficient than traditional content-based publish/subscribe. Mobile devices have weak processors and are powered by batteries. Their computational capability is rather limited. Additionally, the memory capacity and bandwidth of the nodes in a HUNET are also scarce. Traditional content-based networking systems, however, are complex and consume excessive memory and bandwidth. |
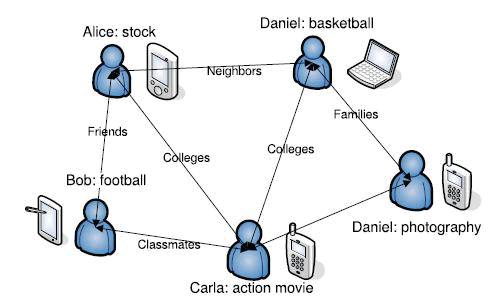 |
| FIGURE 1: A HIGH-LEVEL ILLUSTRATION OF THE HUNET |
II. RELATED WORK |
| DTN [1] enables various novel applications that were deemed impractical before. HUNET follows the same lineage of utilizing the “store-carry-and-forward” communication paradigm to provision a personal information sharing service. An important property of HUNETs that is different from DTNs is its inherent social network structure. The analysis of human contact patterns reveals that community structures are prevalent, which is used to facilitate efficient routing. In our previous work [8], we proposed an optimal forwarding rule based on the optimal stopping theory and the long-term relationships between users. All of these routing protocols require a stable contact pattern between nodes, and need a complex and time-consuming preprocessing to gather routing information. However, HUNETs usually exist in short term, which makes these procedures difficult to perform in HUNETs, and makes these protocols unable to work in HUNETs. A similar work to ours which studies the user-centric data dissemination in DTN. |
| Content-based networking is used in an interest-driven opportunistic data diffusion application. Other issues in mobile content sharing, including energy efficiency, scalability, and privacy are studied in. TACO-DTN is a pub/sub system for DTNs that utilizes stationary infrastructure to facilitate more efficient content distribution, a similar system for vehicular network is presented in [7], [6]. In [2], a content-based pub/sub system for wireless ad hoc networks is presented. |
III. EXISTING SYSTEM |
| A new architecture of networking portable wireless devices has emerged, which is called the delay tolerant networks DTNs adopt a “store-carry-and-forward” model, which significantly expands the communication capability of mobile device. Driven by the new application demands and the limitations of the existing architecture, we envision a new type of dynamic networking service called human networks (HUNETs). Physically, a HUNET is composed of human-carried mobile devices, which have the same structure as DTNs. These devices use short-range wireless communication technologies, such as Wi-Fi or Bluetooth, to communicate with each other. Functionally, HUNETs enable information sharing between users in a completely decentralized manner without the aid of an wireless communication infrastructure. A high-level illustration of this architecture is presented . |
Disadvantages: |
| • Mobile devices have weak processors and are powered by batteries. Their computational capability is rather limited. |
| • TCBF has false positives in their queries, which causes useless messages to be forwarded to nodes that are not really interested in their content. |
| We propose HUNET, a novel network architecture that facilitates efficient information sharing between portable mobile devices. We design B-SUB, an interest-driven information sharing system for HUNETs, a content-based publish/subscribe that achieves infrastructure-less communication between mobile devices. |
| We invent the TCBF, an extension to the counting Bloom filter. |
| We conduct extensive theoretical analyses and real world trace driven simulations to evaluate the performance of B-SUB. |
| Advantages: |
| • This provides stronger privacy guarantee. |
| • Gives better protect user privacy. |
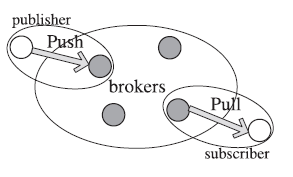 |
| Figure 2: The Architecture of HUNETs |
V. SIMULATION RESULTS |
| Real-world trace-driven simulations are used to evaluate the performance of B-SUB. We present the results of the delivery performance and the overhead. Two human contact datasets: Cambridge/haggle/Infocom06 [11] and MIT/reality are used. We present the results of the former. The results of MIT/reality are in the available online supplemental material. The results indicate that the optimal value of the decay cycle heavily depends on contact patterns. |
| Algorithms in comparison. We compared B-SUB and B-SUB-P with two other techniques: PUSH and PULL. PUSH works like epidemic routing or flooding. A node replicates all of the messages in its message buffer to every node that it encounters without duplication. In the simulation, every message is assigned a 32-bit ID by hashing its content to help nodes detect duplicate messages. In PULL, a node only forward a message to another node that is interested in the message. |
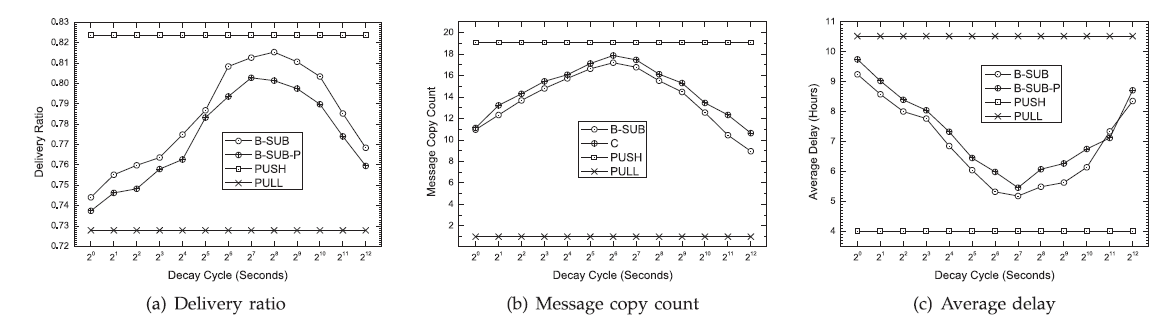
| We present the delivery ratio and the average delay of delivered messages in this section. In these figures, B-SUBP shows a noticeable performance degradation, which is caused by the imprecision of the processing of the TCBFs. |
| Delivery ratio: Fig. a presents the delivery ratios of the four protocols in the Infocom06 trace. The results of PUSH and PULL are not affected by the decay cycle. B-SUB and BSUB- P approach PUSH’s performance when the decay cycle increases. Both B-SUB and B-SUB-P outperform PULL because they utilize multihop forwarding. B-SUB and BSUB- P suffers from a performance degradation when the decay cycle grows beyond a threshold. This is mainly caused by the counter overflow of the TCBF. |
| Average message copy count: Fig. b presents the message copy counts of the delivered messages of the Infocom06 trace. The message copy count of a delivered message is counted by finding out how many nodes (including the source and the receivers) have relayed the message, i.e., have possessed a copy of the message. PUSH has the worst results. |
| B SUB can maintain a relatively lower copy count than PUSH. However, B-SUB-P tends to propagate user interests in a wider range compared to B-SUB, which slightly increases message copy count. |
| Delay: Fig. c shows the average delay of the delivered messages of the Infocom06 trace. The delay of a delivered message is measured as the time interval from the time when the message is generated to the time when it is delivered to a node that is interested in it. The delay behaves similarly to the delivery ratio. Initially, increasing the decay cycle expands the propagation of user interests and helps messages find more paths to reach interested nodes. However, similar to the delivery ratio, messages can be trapped when the decay cycle grows beyond a certain threshold, which results in a longer delay. |
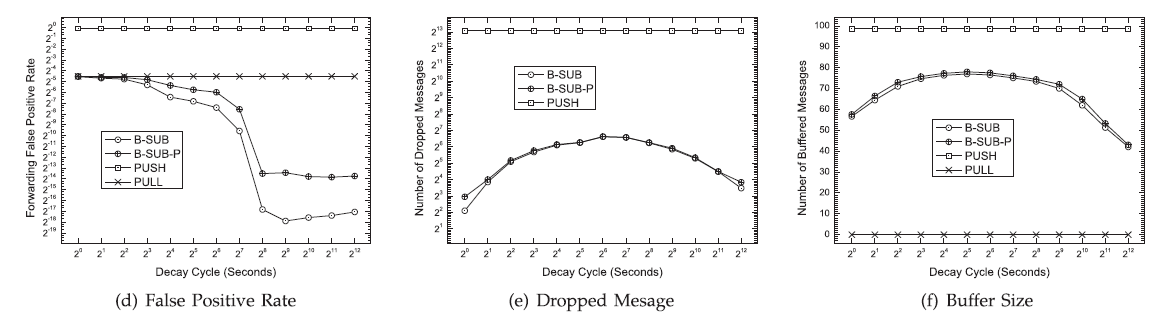
| Forwarding false positive rate: Fig. 9d presents the forwarding FPR of the four methods of the infocom06 trace. Forwarding FPR is measured as the ratio of the number of falsely forwarded messages to the total number of messages being forwarded. |
| Dropped message count: Fig. e presents the number of dropped messages of the four protocols of the infocom06 trace. The dropped message count is measured as the average number of messages being dropped per node in the entire simulation session. As discussed previously, dropped messages are not treated as message copies. In fact, the sum of the message copies and dropped messages is the total overhead induced by forwarding messages. |
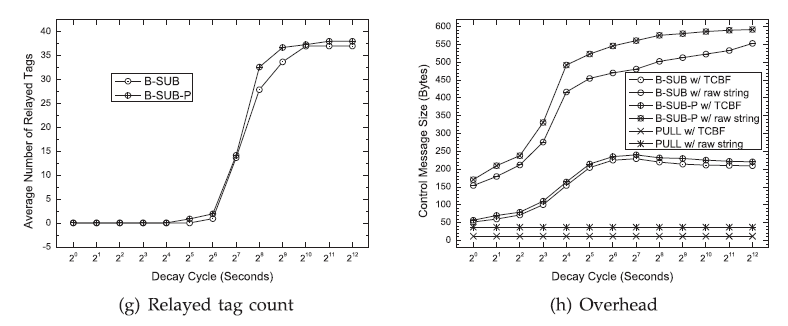
| Relayed tag count: Fig. g presents the average number of relayed tags by each node at the end of the simulation session of the infocom06 trace. The relayed tag count is tracked in the entire simulation to ensure accuracy. The results are measured at the end of the simulation to make sure that it is stable. |
| Control message size: Fig. h presents the average size of all of the control messages being sent in each contact of the infocom06 trace. The control messages only include the ones that are used to represent user interests. |
 |
 |
 |
VI. CONCLUSION AND FUTURE WORK |
| We present B-SUB, an interest-driven information sharing system for HUNETs. B-SUB employs content-based networking to achieve infrastructure-less communication between mobile devices. Specifically, BSUB employs a tagbased content description model. A novel data structure, the TCBF, is invented to compress user interests and guide content routing. |
| The use of TCBF reduces the memory and bandwidth consumption of B-SUB. We systematically analyze the impact of several parameters of B-SUB on its behaviors and performance. An extension of B-SUB called B-SUB-P is then proposed to better protect user privacy. Extensive real-world trace-based simulations are performed to verify the performance of B-SUB and B-SUB-P. The results have proven that B-SUB and B-SUB-P archive similar delivery ratio and delay as the optimal method (PUSH), but consumes much less resources. |
VII. ACKNOWLEDGEMENT |
| I consider it is a privilege to express my gratitude and respect to all those who guiding me in the progress of my paper. POOJA P |
References |
|