ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
Sangeetha C P1, Dr. C.D. Suriyakala2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
Wireless sensor networks are becoming increasingly common due to the proliferation of very small, integrated lowpowered sensors and mobile devices capable of gathering critical, real-time information for remote surveillance, continual monitoring, distributed target tracking etc. Studies have shown that, the deployment of such sensor networks has increased in recent years and will improve dramatically in the near future due to the advent of two standards by IEEE and ZigBee Alliance, named as IEEE 802.15.4 standard and ZigBee standard respectively. ZigBee is the only standard uniquely designed for low-power, a low-cost, low-data rate based wireless technology network, that provides network security, and application support services operating on top of the IEEE 802.15.4 Medium Access Control (MAC) and Physical (PHY) Layer wireless standard. The survey report of performance analysis of IEEE 802.15.4/ZigBee sensor networks shows that the unreliability is the major limitation of such networks, which is also termed as MAC unreliability problem. The studies highlighted that, this unreliability problem is due to the default MAC parameter settings suggested by the standard itself. Different solutions have come up to improve the reliability problem, such as setting a pre-defined value for parameters which is suitable only for static conditions, an adaptive technique for dynamic conditions based on mathematical model etc. This paper surveys a comprehensive review of causes and its available solutions to the MAC unreliability problem for IEEE 802.15.4/ZigBee sensor networks
Keywords |
| Cross-layer, IEEE 802.15.4, Reliability, ZigBee, Delivery ratio |
INTRODUCTION |
| Wired sensor networks have been around for decades, with an array of gauges measuring temperature, fluid levels, humidity, and other attributes on pipelines, pumps, generators, etc. Many of these run as separately wired networks, sometimes linked to a computer but often to a control panel that flashes lights or sounds an alarm when a temperature rises too high or a machine vibrates too much. Now advances in silicon radio chips, coupled with cleverly designed routing algorithms and network software, wireless sensor networks have come up to eliminate those wires and their installation and maintenance costs. Mesh network topologies will let these wireless networks route around nodes that fail or whose radio signal is degraded by interference from heavy equipment. |
| A wireless sensor network contains a large number of tiny sensor nodes that are densely deployed either inside the phenomenon to be sensed or very close to it. Sensor nodes consist of sensing, data processing, and communicating components. Wireless sensor networks can use several different wireless technologies, including IEEE 802.11 WLANs, WPANs, Bluetooth etc. But at present most of the applications are of low-power radios having a range of about 30 to 200 feet and data rates of up to around 300 kbps. IEEE 802.15.4 is the approved low-rate standard for a simple, shortrange wireless network whose radio components could run several years on a single battery. The low rate (LR) wireless personal access network (WPAN) (IEEE 802.15.4/LRWPAN) is intended to serve a set of industrial, residential, and medical applications with very low power consumption, low cost requirement, and relaxed needs for data rate and QoS. The low data rate enables the LR-WPAN to consume little power [11]. |
| ZigBee technology is such a low data rate, low power consumption, low cost, wireless networking protocol targeted toward automation and remote control applications. The IEEE 802.15.4 committee and ZigBee Alliance worked together and developed the technology commercially known as ZigBee. It is expected to provide low-cost and lowpower connectivity for devices that need battery life as long as several months to several years but does not require data transfer rates as high as those enabled by Bluetooth. ZigBee can be implemented in mesh (peer- to-peer) networks and can operate in the unlicensed RF worldwide (2.4 GHz global, 915 MHz America, or 868 MHz Europe) bands. The data rate is 250 kbps at 2.4 GHz, 40 kbps at 915 MHz, and 20 kbps at 868 MHz [12]. |
| As far as a sensor network is concerned, the three key factors to be considered while deployment is energy efficiency, reliability and scalability. The survey report [1]-[12] of performance analysis of IEEE 802.15.4/ZigBee sensor networks shows that the unreliability is the major limitation of such networks, which is also termed as MAC unreliability problem. The studies highlighted that, this unreliability problem is due to the default MAC parameter settings suggested by the standard itself. Different solutions have come up to improve the reliability problem, such as setting a pre-defined value for parameters which is suitable only for static conditions, an adaptive technique for dynamic conditions based on mathematical model etc. |
II. OVERVIEW OF IEEE 802.15.4 AND ZIGBEE |
A. IEEE 802.15.4 Standard |
| IEEE 802.15.4 [4] is a standard for low-rate, low-power, and low-cost Personal Area Networks (PANs). The IEEE 802.15.4 physical layer offers a total of 27 channels, one in the 868MHz band, ten in the 915MHz band, and sixteen in the 2.4GHz band . The bit rates on these three frequency bands are respectively 20 kbps, 40 kbps and 250 kbps [12]. The 802.15.4 standard defines two different channel access methods: a beacon enabled mode and a non-beacon enabled mode. |
| The non-beacon enabled mode is useful for light traffic between the network nodes. The channel access and contension are performed using an unslotted CSMA-CA mechanism. In a beacon enabled network, the coordinator sends periodic beacons containing information that allows network nodes to synchronize their communications, and information on the data pending for the different network nodes. In this mode, the nodes communicate over the network through a super frame structure as shown in Figure 1. |
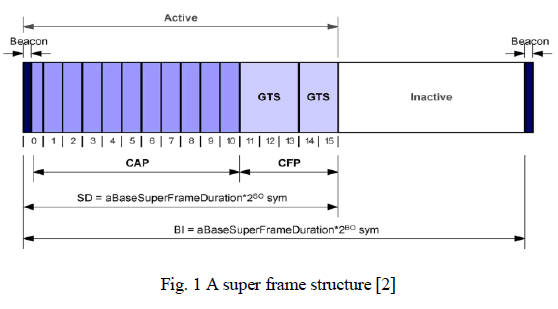 |
| Each super frame has an active period, during which nodes can attempt to communicate using slotted CSMA/CA, and an inactive period during which devices may turn off in order to conserve energy. The active period is composed of three parts: a Beacon, a Contention access period (CAP) and a Contention free period (CFP) [2]. |
| Beacons are special synchronization frames generated periodically by the coordinator node(s). The time between two consecutive beacons is called Beacon Interval (BI), and is defined through the Beacon Order (BO) parameter (BI=15.36ms*2BO, with 0≤BO≤14). The Active Period is denoted by Superframe Duration (SD) and its duration is defined by the Superframe Order (SO) parameter (SD=15.36ms*2SO, with 0≤SO≤BO≤14). |
| During the CAP, a slotted CSMA/CA algorithm is used for channel access, while in the CFP communication occurs in a Time-Division Multiple Access (TDMA) style by using a number of Guaranteed Time Slots (GTSs), pre assigned to individual nodes. During the GTS, nodes are allowed to transmit without any contention with other devices [2]. |
| 1) CSMA/CA Algorithm: The slotted CSMA/CA backoff algorithm mainly depends on three variables: (1) the backoff exponent (BE) enables the computation of the backoff delay, which is the slot periods a device must wait before attempting to access the channel; (2) the contention window (CW) represents the number of backoff periods during which the channel must be sensed idle before the transmission can start; (3) the number of backoffs (NB) represents the number of times the CSMA/CA algorithm is required to backoff while attempting to access the channel [1]. |
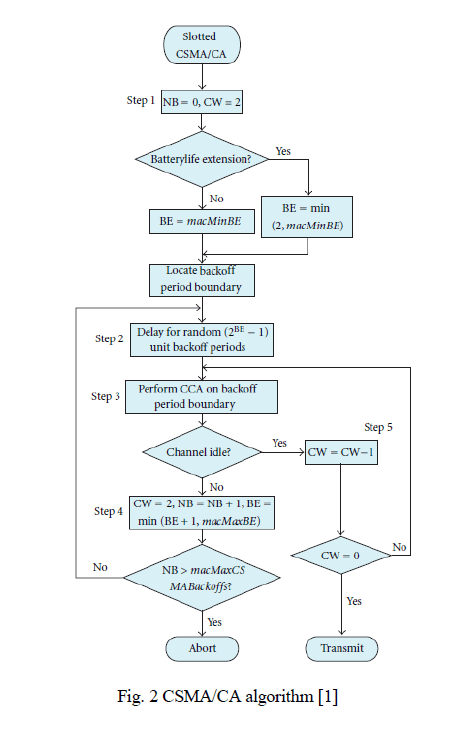 |
| Upon receiving a data frame to be transmitted, the slotted CSMA/CA algorithm performs the following steps. |
| Step 1. A set of state variables is initialized: NB = 0, CW = 2, and BE = macMinBE. If the battery life extension variable is set, the maximum value of BE can be only 2. |
| Step 2. The MAC layer delays for a random number of complete slot periods in the range 0 to 2BE − 1, which is generated to initialize a backoff timer. |
| Step 3. After the completion of the backoff periods, a clear channel assessment (CCA) is performed to check the state of the wireless medium. |
| Step 4. If the channel is busy, the state variable are updated as follows: NB = NB + 1, BE = Min(BE + 1, macMaxBE), and CW = 2. If the maximum number of backoffs (NB = macMaxCSMABackoffs = 5) is reached, the algorithm shall terminate with a channel access failure status. Otherwise, it falls back to Step 2. |
| Step 5. If the channel is assessed to be idle, the MAC sub layer must ensure that the contention window is expired before starting transmission. For this, the MAC sub layer first decrement CW by one. If CW = 0, then the frame is transmitted. Otherwise, the algorithm must go back to Step 3 to perform a second CCA. Figure 2 represents the above steps graphically. |
B. ZigBee Specifications |
| The ZigBee specifications [10] provide standard solutions for sensor and control systems. Its protocol stack is grounded on the physical and MAC layers as defined by the IEEE 802.15.4 standard, and consists of the network and the application layers. |
| The network layer provides means for network management, security and routing. Network management deals with how to create a network and handle the addition and removal of devices. This is accomplished through an association or disassociation procedure which enables nodes to become members of a network or rather leaves it. Different network topologies are supported, such as star, cluster-tree, and mesh. The application layer is composed of two major elements: ASL and AF. The Application Support Layer (ASL) provides device and service discovery, as well as binding mechanisms between devices and services. On the other hand, the Application Framework (AF) contains the higher layer components, namely the Application Objects (AOs), which implement the specific application as defined by the user. |
III. EFFECT AND CAUSES OF THE MAC UNRELIABILITY PROBLEM |
A. Effect of MAC Unreliability Problem |
| The unreliability problem has been analyzed [3] considering a star network with performance index as delivery ratio. For comparison purposes, the messages are generated by both Periodic and Poisson process, with and without the power management. |
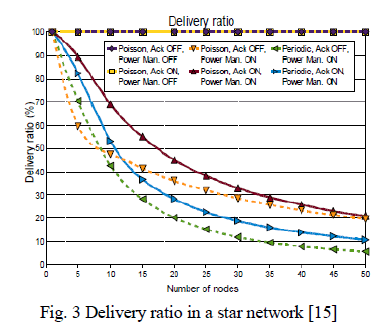 |
| When messages are generated according to a Poisson process and if all sensor nodes are active, the delivery ratio is close to 100% even without acknowledgments and retransmissions. When power management is enabled, the delivery ratio drops sharply with the number of nodes. This is because, for Poisson traffic, when nodes are always active, messages are transmitted just after their generation. Since generation times are spread along the Beacon Interval there is almost no contention among sensor nodes. But, when power management is enabled, data transmissions are deferred to the beginning of the next Active Period, where all nodes wake up at the same time. Therefore, channel access attempts tend to become synchronized and this increases the amount of contention among nodes. Figure 3 shows the delivery ratio as a function of as a function of the number of nodes for both Periodic and Poisson message arrivals. In the case of periodic message generation process, messages are generated just before the beginning of the Active Period so as to minimize the latency. Therefore, channel accesses are perfectly synchronized which increases the amount of contention among nodes and thereby decreasing the delivery ratio. |
| Therefore, we can point out that, when power management is enabled, the 802.15.4 MAC protocol is not able to manage contentions efficiently, even when a limited number of nodes wake up and try to access the wireless channel simultaneously. This problem becomes more noticeable as the message size and/or message generation rate increases. This issue is referred as the 802.15.4 MAC unreliability problem in IEEE 802.15.4 networks. |
B. Causes of MAC Unreliability Problem |
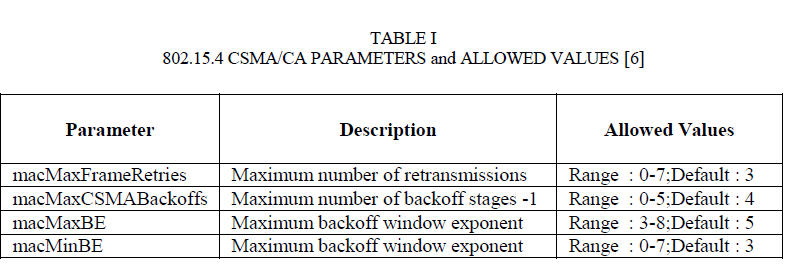
| A number of studies have highlighted that the unreliability problem in IEEE 802.15.4 MAC protocol is mainly due to the CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance) algorithm used by the 802.15.4 MAC protocol for channel access, which is not able to efficiently handle contention when the number of simultaneously contending nodes is relatively high. This is a common problem for all contention-based MAC protocols except those using a time-division or polling scheme. However, in the 802.15.4 MAC it is made more severe than in other similar MAC protocols due to the CSMA/CA parameter values specified by the standard [2]. It is very important to properly understand the ultimate reasons that originate the MAC unreliability problem since it may severely affect the data collection process in 802.15.4 sensor networks. Therefore, a thorough analysis of CSMA MAC parameters should be done in order to mitigate or reduce the unreliability problem. Table I summarizes the MAC parameters introduced and the allowed (and default) values defined in the standard (according to 2006 released version of the standard) [5]. |
 |
C. Impact of MAC parameters |
| A star network with 15 sensor nodes is considered and the impact of each single MAC parameter is evaluated, in terms of delivery ratio [3]. In the conducted experiment, it is assumed that the message generation process is Periodic, power management is enabled and sensor nodes use acknowledgments and retransmissions to improve the reliability. The observations are: |
| 1) Maximum number of retransmissions: The maximum number of retransmissions is defined by the macMaxFrameRetries parameter. Since the percentage of messages successfully transmitted by sensor nodes to the sink is low (below 40% with 15 nodes), an increase in this parameter would improve the delivery ratio. Therefore, vary macMaxFrameRetries in the range [0, 7] (0 means that the retransmission mechanism is disabled), while setting all other MAC parameters to their default values. The results observed in this study is shown in Table II |
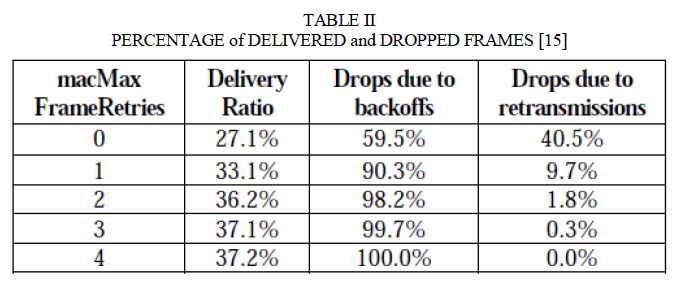 |
| 2) Maximum number of backoff stages: The CSMA/CA algorithm performs a new backoff stage whenever the medium is found busy. At each stage the backoff window is doubled until the maximum value (defined by macMaxBE) is reached, after which remains constant. The macMaxCSMABackoffs parameter specifies the maximum allowed number of backoff stages. To analyze its effect, this parameter is varied in the range [0-10], even if the standard allowed range is [0-5], and set all the other MAC parameters to their default values. The impact of macMaxCSMABackoffs on delivery ratio is reflected in Figure 4. |
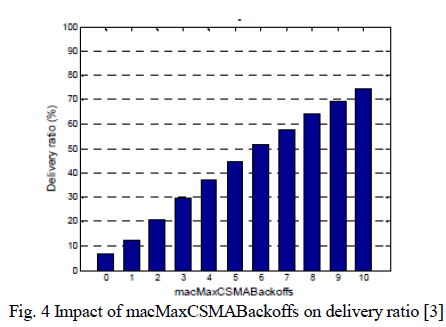 |
| As expected, the delivery ratio increases with macMaxCSMABackoffs. Increasing the macMaxCSMABackoffs value results in a significant improvement in terms of network performance, but it does not solve the MAC unreliability problem. The delivery ratio remains below 80% even when 10 backoff stages are allowed. This limited contribution can be explained by observing that, when using the default values for macMinBE (3) and macMaxBE (5), the backoff window reaches its maximum value after only 3 backoff stages. By allowing a larger maximum backoff-window size, a considerable improvement could also be obtained. |
| 3) Maximum backoff window: To analyze the impact of the maximum backoff window size vary macMaxBE in [3,10] (the allowed range is [3,8]) and set macMinBE and macMaxFrameRetries to their default values. The macMaxCSMABackoffs, macMaxBE and macMinBE are bounded by the following constraint [3]: |
| macMaxCSMABackoffs ≥ macMaxBE – macMinBE (1) |
| This inequality shows that any variation in macMaxBE will have corresponding change in macMaxCSMABackoffs. The variation of delivery ratio with macMaxBE is highlighted in Figure 5. It is observed that the delivery ratio significantly improves when macMaxBE increases, with the combined effect of a larger backoff window size and a higher number of backoff stages. When using macMaxBE > 9, reliability is nearing to almost 100% . |
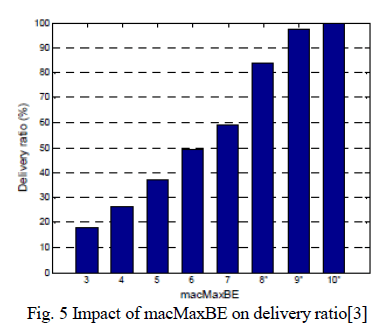 |
| 4) Minimum backoff window: The macMinBE parameter determines the minimum backoff window size. The correct parameter setting requires the condition: macMinBE < macMaxBE, [3] considered three different set of values for macMinBE, corresponding to three different macMaxBE values (i.e., 5, 8 and 10). Fix macMaxBE and vary macMinBE in the range [1, macMaxBE-1]. In addition, set macMaxCSMABackoffs according to Equation (1), and macMaxFrameRetries to its default value. The improvement of delivery ratio with macMinBE may be studied with Figure 6. |
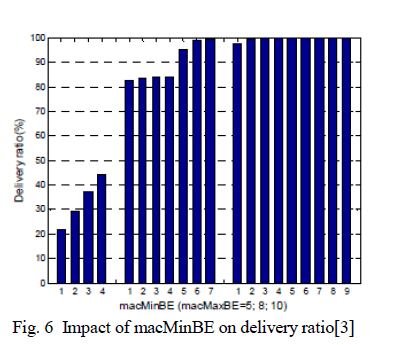 |
| For a fixed value of macMaxBE, the delivery ratio tends to improve with increase in the minimum backoff window size. This is because a larger initial backoff window reduces the collision probability in the first backoff stages. |
| From the survey results, we may conclude that, increasing the maximum number of retransmissions does not provide additional reliability because the wireless channel is assumed to be ideal and sensor nodes are never hidden to each other. Instead, the delivery ratio is found to be on better side (nearing to 100%), by increasing one or more of the other MAC parameters, i.e., macMinBE, macMaxBE, and macMaxCSMABackoffs. |
IV. POSSIBLE SOLUTIONS FOR MAC PARAMETER SETTINGS |
| In order to mitigate the unreliability problem, a number of solutions have been proposed in literature survey. It has been shown in [3] that, with a more appropriate MAC parameters setting like Standard Parameter Set(SPS:- i.e., macMaxCSMABackoffs, macMinBE, and macMaxBE, are set to the maximum values allowed by the standard, while macMaxFrameRetries is set to its default value.) and Non-standard Parameters Set (NPS:- i.e., set of values is not compliant with the 802.15.4 standard; macMaxCSMABackoffs, macMinBE, macMaxBE, are set to values beyond the maximum ones allowed by the standard, while macMaxFrameRetries is still set to its default value), it is possible to achieve the desired level of reliability. However, [3] is based on static (i.e., pre-defined) settings for the MAC parameters, hence they are not flexible enough to support dynamic operating conditions. In addition, a static parameter setting typically results in energy consumption higher than necessary. |
| An adaptive mechanism for reliable and adaptive data collection in IEEE 802.15.4-basedWSNs has been detailed in [8]. This solution is based on an optimization problem built on top of an analytical model of the IEEE 802.15.4 standard. As a result, the proposed approach has significant computational and storage overheads, which make it unsuitable for implementations on real sensors. |
| In [7] an ADaptive Access Parameters Tuning (ADAPT) algorithm has been proposed for dynamically adjusting the MAC parameters, based on the desired level of reliability and actual operating conditions experienced by the sensor nodes. The ADAPT algorithm is fully distributed such that it is suitable for multi-hop WSNs. Moreover, it is lightweight because it requires only little computational and storage demands at each node. In addition, ADAPT does not require any modification to the MAC protocol itself, since it relies on the management functions available in the IEEE 802.15.4 standard. This was explained using single hop star topology. |
| An extension to the above mentioned solution is presented in [6], where the ADAPT algorithm is implemented in both single-hop and multi-hop networks. They also utilized the concept of cross layering in order to minimize the power consumption. Specifically, they introduced a framework which involves an energy-aware adaptation module that captures the application’s reliability requirements, and autonomously configures the MAC layer based on the network topology and the traffic conditions for reduced energy consumption. |
| A more recent paper [9] has categorized the optimal parameter setting solutions in to three different algorithms namely offline computation, model-based adaptation, and measurement-based adaptation. Offline algorithm is based on analytical model of IEEE 802.15.4 CSMA/CA algorithm, based on a Discrete Time Markov Chain (DTMC). The model based adaptive algorithm is also based on a DTMC model of the sensor network. However, it can be solved by sensor nodes with limited computational and memory resources. In particular, sensor nodes estimate some congestion indexes through online measurements, instead of deriving them analytically from the model. The main limitation of a model-based approach is that, its effectiveness strongly depends on the accuracy of the related model, and it typically takes a long time to solve the model and provide the optimal solution. An alternative strategy is using a measurement - based approach, as in the ADaptive Access Parameters Tuning (ADAPT) algorithm which is discussed earlier. They have found that both the adaptive algorithms perform well, however the model-based approach has some limitations that make it unsuitable for practical scenarios, where operating conditions typically vary over time and transmission errors cannot be neglected. Instead, the measurement-based algorithm does not suffer from such limitations. |
| After the thorough survey study, we put forward an innovative adaptive scheme using ADAPT(Adaptive Access Parameters Tuning) for reliability improvement and cross layering for energy efficiency, and we strongly anticipate this will result the totality improvement in the performance of IEEE 802.15.4/ZigBee sensor networks. |
V. CONCLUSION |
| In this paper we have done an intensive survey of the works/findings done by various researchers on IEEE 802.15.4/ZigBee standards, and many of the works pointed out that the limitation of such networks is the MAC unreliability problem. They also pointed out that it may severely affect the data collection process in 802.15.4 sensor networks and it is a prime factor to be considered while analyzing such networks. We have explained the root causes for the unreliability problem and found that it is originated by the CSMA/CA MAC protocol, which is unable to efficiently manage contensions for channel access. Subsequently, we have listed the possible solutions that can alleviate the unreliability problem such as predefined parameter settings, adaptive mechanisms etc. and we also recommend that adaptive schemes along with cross layering will perform much better than the existing schemes. |
ACKNOWLEDGMENT |
| The ongoing related work based on the suggested solutions could not have been possible without Mr. George M. Jacob, Lab Instructor, Toc H Institute of Science and Technology who have encouraged us throughout to address the problem. We thank him for his constant help and support. |
References |
|