ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
Monika Patel, Dr. Priti Srinivas Sajja
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
Now days due to advancement of technology & high speed internet, the access and transfer of digital media such as image, text, audio and video becomes easy for everybody. Because of the increased use of internet, the need of security and authenticity has become essential. To secure the multimedia data, digital watermarking techniques have become key tool to tackle the challenges faced by the rapid distribution of digital content over the internet. Digital watermarking is a branch of information hiding which is used to hide proprietary information in digital media like photographs, digital music, digital video etc. In this paper we have developed image watermarking model based on discrete wavelet transform. In this technique, we embed and extract biometric watermark using the alpha blending technique in low frequency band. This paper illustrates a general architecture and modified algorithm for DWT based digital watermarking. To demonstrate working of the aforementioned architecture and algorithm, an experimental system is also developed with different value of alpha at 1,2 and 3 level of DWT. This paper also describes output of the experimental system with their comparison.
KEYWORDS |
| Digital Watermarking, DWT, Alpha Blending, Biometric Watermark |
I. INTRODUCTION |
| In the past several years there has been an explosive growth in multimedia technology and its applications. This growth has escalated the necessity to build secure methods for legal distribution of the digital content. As digital multimedia like video, audio and images become available for retransmission, reproduction and publishing over the Internet. So a real need for protection against unauthorized copy and distribution is increased. Thus, there is a rise in apprehensions over copyright protection of digital contents [1]. As a solution of this, Digital Watermarking techniques are used with some biometrics parameters such as fingerprint, speech and iris which are "unique" to an individual and no one can be easily altered the digital media[2]. Digital Watermarking technology plays an important role in preventing copyright violation as it allows identifying the legitimate owner or detecting malicious tampering of the document. Digital watermarking is the process of embedding information into a digital signal. The signal may be audio, pictures or video. The embedded information is known as a watermark that can be extracted or detected whenever it is required. A watermark may be a digital signal or pattern which is inserted into a digital data. |
| A. USE OF BIOMETRIC WATERMARK: |
| Due to extend growth of Internet the use of Biometrics based personal identification techniques are becoming increasingly popular compared to traditional token-based or knowledge based techniques such as identification cards (ID), passwords, etc[4]. Recently biometrics is merged with watermarking technology to enhance the security of multimedia content. Biometric watermarking is a special case of digital watermarking in which the watermark content is biometric data. Access control or authenticity of legitimate user can be verified by both digital watermarking as well as by biometric authentication [28]. One of the main reasons for this popularity is the ability of the biometrics technology to differentiate between an authorized person and malicious users who fraudulently acquires the access privilege of an authorized person. Among various commercially available biometric techniques such as face, voice, fingerprint, iris, etc., fingerprint-based techniques are the most extensively studied and the most frequently deployed. So by combining watermarking with biometric features, we can develop more secured and confidential watermarking techniques for providing authenticity of multimedia content because as biometric features are unique for each individual. |
| B. Characteristics of Watermark: |
| There are a number of important characteristics that a watermark can exhibit [1, 9, 21, 17, 25, 27]. These include that the watermark is difficult to notice, survives common distortions, resists malicious attacks, carries many bits of information, can coexist with other watermarks, and requires little computation to insert or detect. The relative importance of these characteristics depends on the application. So the major properties of watermark are listed below: |
| 1) Robustness : Robustness is a measurement for the watermark which is embedded in data has the ability of surviving after a variety of image processing operations like contrast or brightness enhancement, gamma correction, compression, filtering, rotation, collision attacks, resizing, cropping etc., geometric transformation and malicious attack. The robustness of watermarking ensures that the embedded watermark will not be destroyed after such operations [1, 21, 17]. |
| 2) Transparency or Perceptibility: The digital watermark should not affect the quality of the original image after it is watermarked. Watermarking should not introduce visible distortions because if such distortions are introduced it degrade the quality of the content [25]. |
| 3) Capacity / Data Payload: Capacity / data payload of a watermark is the amount of information it contains which is encoded within the host data. Watermark should be able to carry enough information to represent the uniqueness of the image. It is very important to find the maximum amount of information that can be safely hidden in an image. Different application has different payload requirements [25]. If too much of the data is hidden in the image (much more than the payload capacity) then it is harmful for the quality of image as the resolution of the images reduces drastically [9]. |
| 4) Computational Cost: The watermarking scheme should not be computationally complex especially for applications where real-time embedding is desired. In a hospital environment for instance, where thousands of medical image are produced daily, watermarking process needs to be less time consuming so that the operation of the hospital is not affected. Reducing the number of computations also means lower cost for computer hardware. Generally, spatial domain watermarking schemes especially LSB takes shorter time than transform domain schemes [27]. |
| 5) Security: Watermark information owns the unique correct sign to identify, only the authorized users can legally detect, extract and even modify the watermark and thus be able to achieve the purpose of copyright protection. [1] |
II. LITERATURE SURVEY |
| Dr. Shubhangi et al., [10] has presented new fragile LSB based digital watermarking technique. LSB embedding also allows high perceptual transparency. However, there are many weaknesses when robustness, tamper resistance and other security issues are considered. Scaling, rotation, cropping, addition of noise, or lossy compression to the stego-image is very likely to destroy the message. Furthermore an attacker can easily remove the message by removing (zeroing) the entire LSB plane with very little change in the perceptual quality of the modified stegoimage. In her implementation she took text as a watermark instead of biometric data. Rajlaxmi Chouhan et al., [23] proposed Fingerprint Authentication by Wavelet-based Digital Watermarking. The DWT based technique has been found to give better robustness against noises, geometrical distortions, filtering and JPEG compression attack than other frequency domain watermarking techniques. Moreover the proposed method is compared with DCT based and hybrid DWT- DCT watermarking techniques, but as a resultant the performance of the proposed technique is better than the other compared techniques. Ameya Naik et al.,[3] proposed a Blind DCT Domain Digital Watermarking for Biometric Authentication. More ever the watermarked image obtained using mapping technique provides authentication of the host image because the face image is hidden in the fingerprint image itself. But this proposed technique works with only fixed size of fingerprint images only. V. Anitha et al.,[28] proposed authentication of digital documents using secret key biometric watermarking. In this paper biometric data iris is embedded in LSB bit of original document with the proper secret key. If the biometric watermarked document is extracted using invalid key, then the extracted watermark will be an image full of noise without any pattern. The proposed technique shows that 100% accuracy in authenticating the genuine documents and is resistant against attacks. Sandhya et al.,[24] proposed a text watermarking algorithm for fingerprint images. In this paper, the watermarking algorithm is designed to improve the recognition performance as well as the security of a fingerprint based biometric system. The proposed algorithm provides the effective solution of security issues regarding biometrics techniques without affecting the fingerprint quality. A K Jain et al.,[4] proposed watermarking of biometric data. They proposed a method to use biometric data to secure another type of biometric data to increase the overall security of the system. In this paper, two applications of watermarking are presented to secure the data. The first application is related to increasing the security of biometric data exchange, which is based on Steganography. In the second application, they embed facial information in fingerprint images. Van et al.,[22] proposed two LSB techniques. First replaces the LSB of the image with a pseudo-noise (PN) sequence, while the second adds a PN sequence to the LSB of the data. The problem with this paper is that data is highly sensitive to noise and is easily destroyed, image quality may be degraded by the watermark & watermark is not robust. Blossom et al.,[8] proposed a DCT based watermarking scheme which provides higher resistance to image processing attacks such as JPEG compression, noise, rotation, translation etc. In this approach, the watermark is embedded in the mid frequency band of the DCT blocks carrying low frequency components which shows that the watermark is robust. Nilanjan Dey et al.,[19] proposes a DWT based Steganographic technique. Cover image is decomposed into four sub bands using DWT. Encoded Secret image using spiral scanning is hidden by alpha blending technique in HH sub bands by alpha blending Technique. Encoded secret images are extracted to recover the original secret image. In this approach the generated stego image is imperceptible and security is high. Baisa Gunjal et al.,[6] propose a digital Image Watermarking with DWT-DCT combined approach which can significantly improve PSNR with compared to only DCT based watermarking methods. DWT-DCT based Image watermarking improves PSNR compared to only DCT based watermarking. |
| Akhil et al.,[2] proposed a robust image watermarking technique based on 1-level DWT (Discrete Wavelet Transform). This method embeds invisible watermark into the original image by using alpha blending technique. Experiment result shows that the embedding and extraction of watermark is depend only on the value of alpha. Barni et al.,[7] proposed a new approach to mask the watermark according to the characteristics of the human visual system (HVS). In contrast to conventional methods operating in the wavelet domain, masking is accomplished pixel by pixel by taking into account the texture and the luminance content of all the image sub bands. The watermark consists of a pseudorandom sequence which is adaptively added to the largest detail bands. As usual, the watermark is detected by correlation. This method is robust to various attacks but complex than other transform. Nikita et al., [18] proposed a robust image watermarking technique based on 3-level DWT. This method embeds invisible watermark into the original image by using alpha blending technique. Experiment result shows that the embedding and extraction of watermark is depend only on the value of alpha. Malika Narang et al.,[13] has presented 1-level discrete wavelet transform technique which is used for insertion and extraction of watermark in original image by using alpha blending. This technique is much simpler and robust than others. The insertion and extraction of watermark is achieved by DWT, IDWT and the alpha blending technique. The scaling factors A, B determines the quality of watermarked image and recovered watermark. The quality of watermark image depends on the value of scaling factor A and B both. Vandana Sthul et al.,[28] has implemented a robust image watermarking technique for the copyright protection based on 3-level discrete wavelet transform (DWT). In this technique a multi-bit watermark is embedded into the low frequency sub-band of a cover image by using alpha blending technique. The given experimental results show that the quality of the watermarked image and the recovered watermark are dependent only on the scaling factors k and q and also indicate that the three level DWT provide better performance than 1- level and 2- level DWT. Asma Ahmad et al.,[5] introduced a robust image watermarking technique based on 3-level discrete wavelet transform (DWT) for the copyright protection. In this method secret image is encoded in LL sub bands using spiral scanning with alpha blending technique. The experimental results demonstrate that the watermarks generated with the proposed algorithm are invisible and the quality of watermarked image and the recovered image are improved. The scheme is found robust to various image processing attacks such as JPEG compression, Gaussian noise, blurring, median filtering and rotation. Swamy T N et al.,[26] have implemented the digital watermarking technique on digital images based on 2-level Discrete Wavelet Transform and compared the performance of the proposed method with Level-1 and Level-2 and Level-3 Discrete Wavelet Transform using Alpha blending technique. The result shows that Level-2 DWT can preserve visual significant information for both secret image and original image and also makes the watermark robust with compared to further levels. |
III. GENERAL ARCHITECTURE OF DIGITAL WATERMARKING |
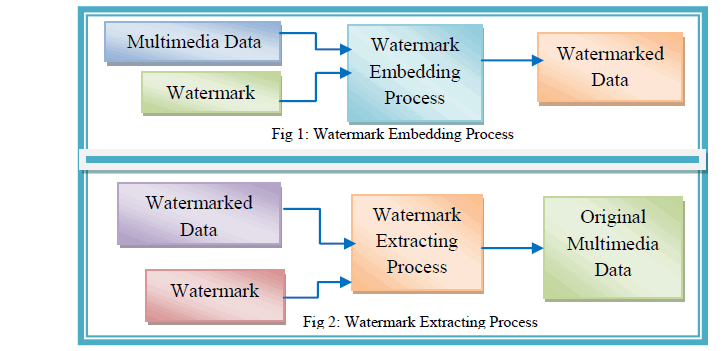
| A watermarking system is built up using watermark embedding module and a watermark extracting module. During Watermark Embedding process, user has to read multimedia content and watermark. The multimedia content can be image, audio, video or text. User can take any symbol, signature, logo or fingerprint as a watermark. During watermark embedding phase watermark is inserted into the original content. While during watermark extracting process watermark is extracted from the watermarked image. The embedding and extracting processes of watermarking are shown in figures 1 and 2. |
 |
| Digital watermarking techniques fall into two broad categories: Spatial Domain Watermarking and Frequency Domain Watermarking. In spatial domain watermark is embedded by directly modifying the pixel values of the original image. While Frequency domain techniques produce high quality watermarked image by first transforming the original image into the frequency domain by the use of Fourier Transform, Discrete Cosine Transform (DCT) or Discrete Wavelet transforms (DWT). The transform watermarking is comparatively much better than the spatial domain encoding. [6] |
V. DISCRETE WAVELET TRANSFORM (DWT) |
| Discrete Wavelet transform (DWT) is a mathematical tool for decomposing an image. It is a modern technique frequently used in digital image processing, compression, watermarking etc. It decomposes a signal into a set of basic functions, called wavelets. The wavelet transform decomposes the image into three spatial directions, horizontal, vertical and diagonal. Hence wavelets reflect the anisotropic properties of HVS more precisely. Magnitude of DWT coefficients is larger in the lowest bands (LL) at each level of decomposition and is smaller for other bands (HH, LH, and HL). The embedding watermark in the lower frequency sub-bands may degrade the image as generally most of the Image energy is stored in these sub-bands. However it is more robust. The high frequency part contains information about the edge of the image so this frequency sub-bands are usually used for watermarking since the human eye is less sensitive to changes in edges so this frequency sub-bands [19]. |
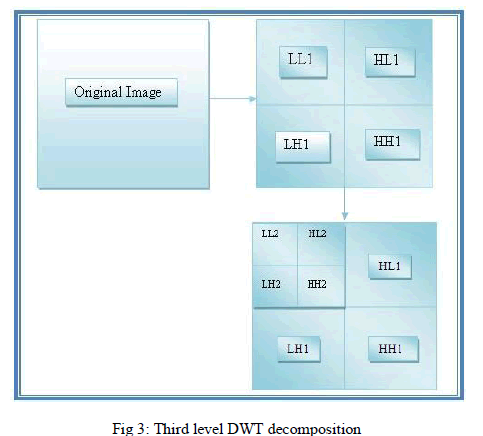 |
| The DWT splits the signal into high and low frequency parts. The low frequency part contains coarse information of signal while high frequency part contains information about the edge components. In two dimensional applications, for each level of decomposition, we first perform the DWT in the vertical direction, followed by the DWT in the horizontal direction. After the first level of decomposition, there are 4 sub-bands: LL1, LH1, HL1, and HH1. For each successive level of decomposition, the LL sub band of the previous level is used as the input. To perform DWT on 2 level we perform DWT on LL1 & for 3 Level decomposition we applied DWT on LL2 & finally we get 4 sub band of 3 level that are LL3, LH3, HH3, HL3. |
VI. PROPOSED WATERMARKING TECHNIQUE |
| In proposed watermarking technique we have taken biometric data thumbprint as a watermark for maintaining security of the images. Here digital watermarking contains two modules: Watermark Embedding and Watermark Extraction. |
| A. Watermark Embedding: |
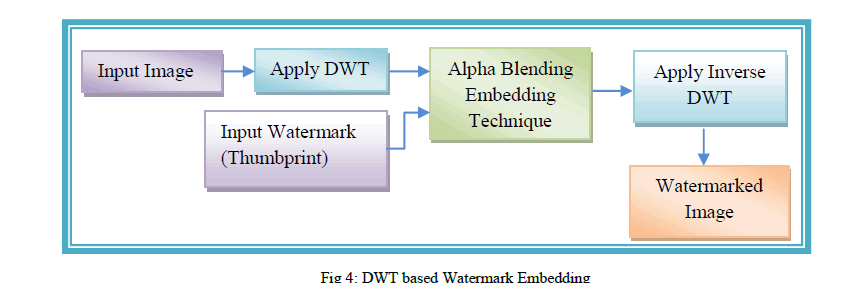
| In this process user has to input original image and thumbprint as a watermark. If input image is color image then convert it into grayscale image. Then apply DWT transform on the input image which decomposes image into four components low frequency approximation, high frequency diagonal, low frequency horizontal, low frequency vertical components. Here we have used “Haar” wavelet. The alpha blending technique is used for inserting the watermark in the cover image. In this technique scaling factor alpha is multiplied with watermark and then added in the decomposed components of the cover image. At last apply inverse DWT for getting watermarked image. In the same manner 2-level and 3-level DWT is also applied to the host image for embedding watermark in cover image. This whole procedure is shown in below figure 4. |
 |
| B. Watermark Embedding Algorithm: |
| Step 1: Read the original image on which watermarking is done. |
| Step 2: Select wavelet filter and apply DWT on input image. |
| Step 3: Input thumbprint as a watermark image. |
| Step 4: Then resize the watermark image. |
| Step 5: Watermark image is alpha blended with original image. |
| Step 6: Alpha Blending Equation is: WI= W * alpha |
| Where WI is new watermarked image, W is thumbprint and alpha is scaling factor |
| Step 7: Using this formula construct the image using inverse of DWT. |
| Step 8: Resultant image is watermarked image. |
| C. Watermark Extraction: |
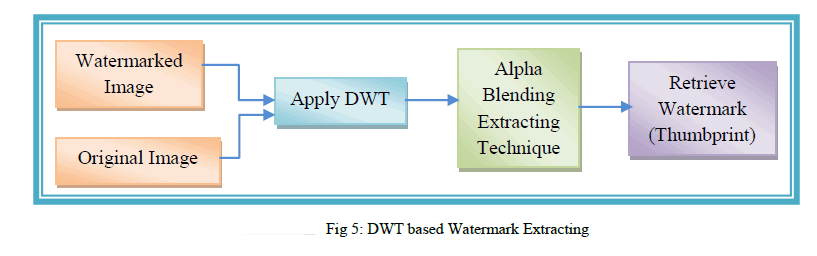
| In this process Watermarked Image and original image both are input. In watermark extracting module DWT is applied to watermarked image and cover image. After that the watermark is recovered from the watermarked image by using alpha blending formula. In this original image is subtracted from watermarked image and then divided by scaling factor alpha. So the resultant image is retrieved watermark. The watermark extraction process is shown in below figure 5. |
 |
| D. Watermark Extracting Algorithm: |
| Step 1: Read Watermarked Image |
| Step 2: Perform DWT on both original and watermark image. |
| Step 3: Recover alpha blending image using following formula |
| W = (Watermarked image – Original image) / alpha |
| Step 3: Convert image to binary image, based on threshold. |
| Step 4: The resulted image is extracted watermark as an original thumbprint. |
VII. SIMULATION RESULTS |
| We have performed this proposed method for two cover images – Leena.bmp and Football.jpg. Here football image is color image. So it is converted into grayscale image. The thumbprint is taken as a watermark. These input data are shown in figure 6 and 7 respectively. |
 |
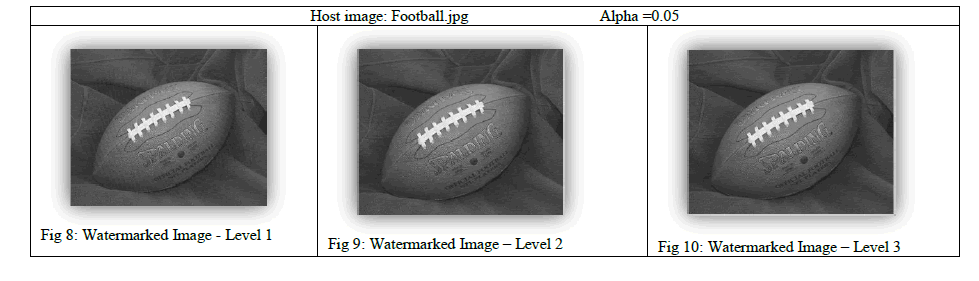
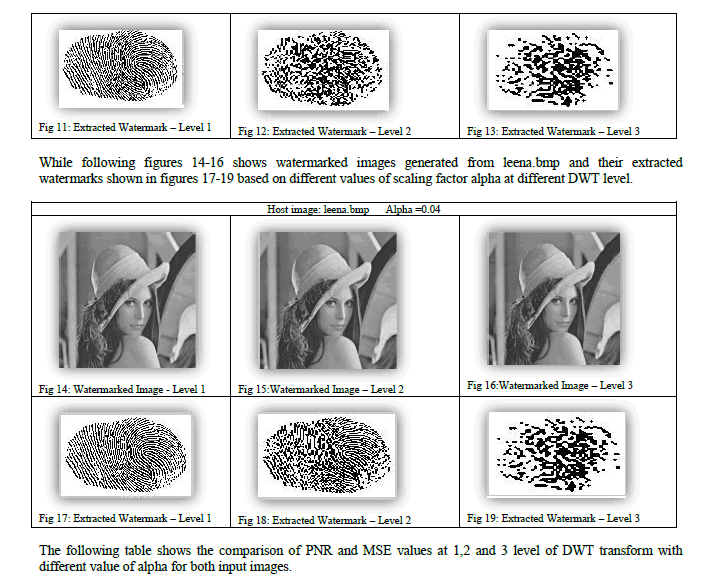
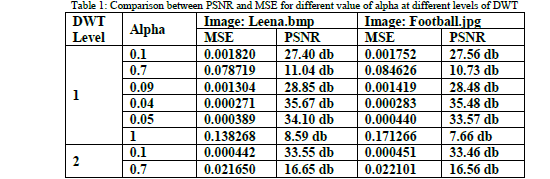
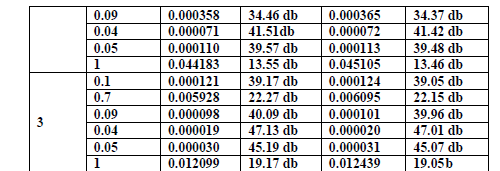
| In this techniques low frequency band of cover image is taken and watermark is added using alpha blending technique. The watermark image is embedded into cover image by varying the different value of alpha at different level of DWT. Alpha gives the best result in between the 0.05 to 0.01. For the value of alpha in between 0.1 to 0.9 the watermark image becomes brighter and completely covers and destroys the cover image. It has been observed that at 2- level DWT watermarked image is robust and retrieved watermark is also of good quality compare to other levels. In level 3 the retrieved watermark becomes darker and improper. The figures 8-10 shows watermarked images generated from football.jpg and their extracted watermarks are shown in figures 11-13 based on different values of scaling factor alpha at different DWT level. |
 |
 |
 |
 |
VIII. CONCLUSION AND FUTURE WORK |
| In this paper thumbprint is used as a watermark for generating secured Image watermark using DWT technique is implemented. Here the watermark insertion and extraction is done using the DWT (Discrete Wavelet Transform) and IDWT (Inverse Discrete Wavelet Transform) respectively. In this method of watermarking we have used alpha blending technique in watermark embedding and extracting process. Here we have used lowest bands (LL) of DWT because the magnitude of DWT coefficients is larger in LL bands compare to other bands. The given results clearly show that the quality of the watermarked image and the recovered watermark is dependent only on the scaling factor alpha. By observing the results it is clear to perform image watermarking at 2-level of DWT having value of alpha is 0.04 or below it. In this level extracted watermark is more robust compare to other levels. Similarly in future another biometric data like iris, face, palm prints are taken as a watermark for video, audio or text watermarking techniques. All the results obtained for the recovered images and the watermark are identical to the original images. |
References |
|