ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
B.Ayisha1, S.Rajeswari2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
A biometric system is a computer system which is used to identify the person on their behavioural and physiological characteristic like fingerprint, face, iris, key-stroke, signature, voice, vein, etc. But now a day’s biometric systems are attacked by using fake biometrics. With the great convenience of computer graphics the image can be easily altered. Many fake images are produced whose content is affected. Thus, the images cannot be judged whether they are real or fake, in this, a fake detection uses singular value decomposition (SVD) as a classifier to make a binary decision on whether an image is fake or real. A typical biometric system consists of detecting, feature extraction, and identical modules. This work is an improvements process to an existence method to detect fake image using SVD. The experimental results prove the effectiveness of this algorithm to detect any small changes in image even with one dot of real image. This introduces three biometric techniques which are Vein recognition, face recognition (Multi Biometric System) and also concentrate on online attendance management.
KEYWORDS |
| Singular value decomposition, multi biometric, online attendance system, vein recognition. |
I. INTRODUCTION |
| The term BIOMETRICS has come to be associated with the automatic identification of a person based on a feature or characteristic. These may be based on either physiological characteristic or behavioural characteristic. Verification mode which authenticates an individual by comparing one specific vein image stored in database. Identification mode compares all the vein image stored in the database. Biometric systems are not perfect. An authorized user may be rejected by the system while an unauthorized user may gain access to it. The False Rejection Rate (FRR) is usually caused by illumination, weather conditions, low quality equipment or inexperience. The False Acceptance rate (FAR) is caused by the security standard being too low. And it is far more serious, as it poses a great risk to have unauthorized people gaining access to the systems. The FARs and FRRs vary between biometric techniques, but vein scanning will be proven to be the only one which is used to eliminate the false acceptation. |
| The reported accuracies of other behavioural methods such as voice, gait and keystroke recognition have been poor. The present strength of the subject, along with certain eco friendly conditions, can significantly degrade the performance of these recognition systems, rendering their use difficult. To overcome the problems of previous biometric systems, new systems using vein patterns from the palms or hands have been introduced and are continuously being researched. In general, vein patterns can be acquired using near-infrared (NIR) light and a camera device. However, the size of the device should be sufficiently large, as palm and hand vein recognition methods require the users to place their hand on the device in order to capture the entire hand region. |
| To overcome the problems of vein recognition systems, finger vein recognition methods have been researched. In the previous research, a local binary pattern (LBP)-based finger vein recognition method was proposed, in which a binary pattern was extracted from a stretched rectangular finger region. Further, a modified Hudson distance (MHD)-based minutiae matching method has been used, in which vein pattern extraction should be performed to extract minutiae points. According to previous finger vein recognition methods, vein pattern or finger-region extraction procedures should be performed for feature extraction or matching. Vein pattern extraction procedures increase the time complexity. Moreover, if a finger image includes noise factors are such as Shadows or fingerprints, a falsely extracted pattern may occur, degrading the recognition accuracy. Even in finger-region extraction methods, stretched quadrangle finger vein images include distortions due to the stretching procedure. |
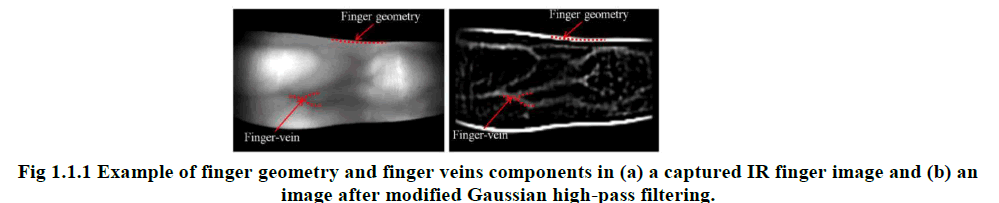 |
II. RELATED WORK |
| The proposed Fingerprint Identification and verification System is biometric identification methodology that uses digital imaging technology to obtain, store and analyse fingerprint data. Here a new method for fingerprint identification technology by minutiae feature extraction using back-propagation algorithm is introduced. For an input image, the local ridge orientation is estimated and the region of interest is located. Then, ridges are extracted from the input image, refined to get rid of the small speckles and holes and thinned to obtain 8connected single pixel wide ridges. Minutiae are extracted from the thinned ridges and refined using some heuristics. |
| A feature extractor finds minutia features such as ridge end, bifurcation, short ridge and spur from the input fingerprint images. For fingerprint recognition, the verification part of the system identifies the fingerprint based training performance of the network. Finally experimental result shows that the number of recognized sample rate of the proposed method is 95% which is much better than the existing fingerprint verification system using artificial neural network (92.5%). Fingerprints have been in use for biometric recognition since long because of their high acceptability, immutability and individuality. Biometrics techniques are divided into two categories i.e. Physiological (fingerprints, face, iris, DNA, retina, voice, hand geometry, palm print, retinal scan etc.) and Behavioural (gait, signature etc.). These physiological or behavioural Characteristics are used for human identification on the basis of their universality, uniqueness, permanence and collectability. |
| Fingerprint is the oldest process to detect human identity. In a recently published World Biometric Market Outlook (2005-2008), analysts predict that the average annual growth rate of the global biometric market is more than 28%, by 2007. The technologies that would be included in this are fingerprint technology by 60%, facial & iris by 13%, keystroke by 0.5% and digital signature scans by 2.5%. So it can be state that automatic fingerprint identification system is an efficient method to recognize human identity.. |
III. PROPOSED ALGORITHM |
| In proposed technique liveness detection techniques which use different physiological properties to differentiate between real and fake image. Attendance Management System provides robust, secure and automatic management using Webcam. Online attendance management system using face recognition. |
| A multi-biometric system is known to follow the universal approach, by offering more than one option to get enrolled with the system. For instance, in case a person is not able to provide his or her finger vein prints as biometric samples, a multi-biometric system can use some other trait for the process of enrollment. Thus, a flexible approach can be followed that remains impossible with Uni-biometric systems. They focused on Quality of an image using IQA Technique for Vein recognition. |
| A. MODULES |
| 1.Pre Processing |
| Preprocessing is nothing but a process in which the input image is converted into problem format which is a bitmap format. There are four main steps in the image preprocessing operation, which are image gray processing, ROI extraction, size normalization and gray normalization. |
| a Image Gray Processing |
| The finger vein image captured by the 24-bit color image with a size of 320 × 240. In order to reduce the computational complexity, the original image is transformed into an 8-bit gray image based on the RGB to Grayscale Equation: Y = R×0.299 + G×0.587 + B×0.114 where R, G and B denote the decimal values of the red, green and blue color components |
| b ROI Extraction |
| As the acquired finger vein image has an unwanted black background which may interfere with the recognition process, this employ an edge detection method to segment the finger vein region, which is defined as the Region of Interest (ROI), from the grayscale image. A Sobel operator with a 3 × 3 mask is used for detecting the edges of a finger. The width of the finger region can be obtained based on the maximum and minimum values of the finger profile and the height of the finger region can be similarly detected. |
| c Size Normalization |
| The size of the ROI is different from image to image due to personal factors such as different finger size and changing location. So it is necessary to normalize the ROI region to the same size before feature extraction. The bilinear interpolation for size normalization used in it and the size of the normalized ROI is set to be 96 × 64. |
| d Gray Normalization |
| In order to extract efficient features, gray normalization is used to obtain a uniform gray distribution. In this, the normalized image is defined as follows: where X (i,j) is the gray value of pixel at position (i,j) of the original image, Xmin denotes the minimum gray value of the original image and Xmax denotes the maximum gray value of the original image. Matchingthe proposed method estimates the similarities between the extracted local directional codes (LDC) and the enrolled codes of a certain individual. |
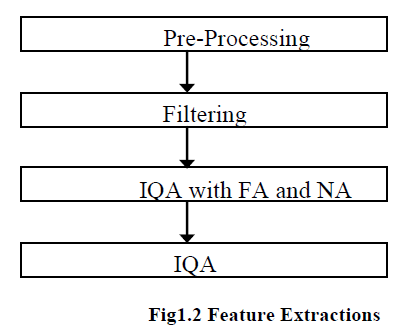
| 2.Feature Extraction |
| In feature extraction the boundaries of the image is extracted using MDF (modified extraction feature) It would be easy for the classifier to identify and verify the signature because in the in the Feature extraction the size of the image is reduced. In this extraction, the two methods are used: |
| • Filtering |
| • IQA |
 |
| a Filtering |
| Noise filters decrease noise by diminishing statistical deviations. Adaptive smoothing filter-Sets pixel intensity to a value somewhere between original value and mean value corrected by degree of noisiness. Good for decreasing statistical, especially single-dependent noise. Median filter-Sets pixel intensity equal to median intensity of pixels in neighborhood. An excellent filter for eliminating intensity spikes. Sigma filter-Sets pixel intensity equal to mean of intensities in neighborhood within two of the mean. Good filter for signal-independent noise. |
| 3..Classification |
| Once the enhanced histograms are computed, A nonlinear SVD classifier with radial basis function kernel used for determining whether the input image corresponds to a live face or not. The SVD classifier is first trained using a set of positive (real) and negative (fake) samples. Based on the measures final result are verified using the SVD classifier. |
| 4.Matching |
| The comparison stage has been made by basically comparing test and original feature sets with the Hudson distance method. Both distance relative to edge minutiae point sets and cross minutiae point sets were calculated separately and the global distance was obtained by weighting the 2 results. |
| 5.Attendance Management |
| An attendance management system is an automated Window application using Webcam. It is used to perform all the actions which are needed to record the attendance in an educational institution. This application deals with all the issues that may arise in an efficient management of attendance. This type of applications might be helpful to reduce the down time and human strain. This system avoids long queue in the office of an educational institution. It’s been a huge task for many colleges and other educational Institution to keep track of an efficient attendance management system. |
IV.IMPLEMENTATION AND RESULT |
A. Algorithms Used |
| a Region of Interest (ROI) |
| ROI is an edge detection method from gray scale image. There are three fundamentally different means of encoding a ROI: |
| 1. As an integral part of the sample data set, with a unique or masking value that may or may not be outside the normal range of normally occurring values and which tags individual data cells. |
| 2. As separate, purely graphic information, such as with vector or bitmap drawing elements, perhaps with some accompanying plain text in the format of the data itself. |
| 3. A separate structured semantic information (such as coded value types) with a set of temporal coordinates. |
| b Local directional codes (LDC) |
| It measures the similarity between two images by ROI extracted image. |
| c Hudson distance method |
| It is used for compare two finger vein image based on minutiae distance measure value. |
| d Biometric Liveness Detection using IQA Techniques |
| Liveness detection in a biometric system means the capability for the system to detect, during enrollment and identification/verification, whether or not the biometric sample presented is alive or not. If the system is designed to protect against attacks with artificial Biometrics (Fingerprint, Face, Iris, Signature), it must also check that the presented biometric sample belongs to the live human being who was originally enrolled in the system and not just any live human being. Biometrics (Fingerprint, Face, Iris and Signature) scanners can be spoofed by artificial fingers using moldable plastic, clay, gelatin, silicone rubber materials, etc. Liveness detection is an anti-spoofing method which can detect physiological signs of life from fingerprints to ensure only live fingers can be captured for enrollment or authentication. |
| e Singular Value Decomposition (SVD) |
| Singular value decomposition takes a rectangular matrix of gene expression data (defined as A, where A is an n x p matrix) in which the n rows represents the genes and the p columns represents the experimental conditions. The SVD theorem states: |
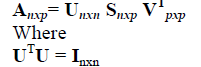 |
| VTV = Ipxp |
| (i.e. U and V are orthogonal) |
IV. SIMULATION RESULTS |
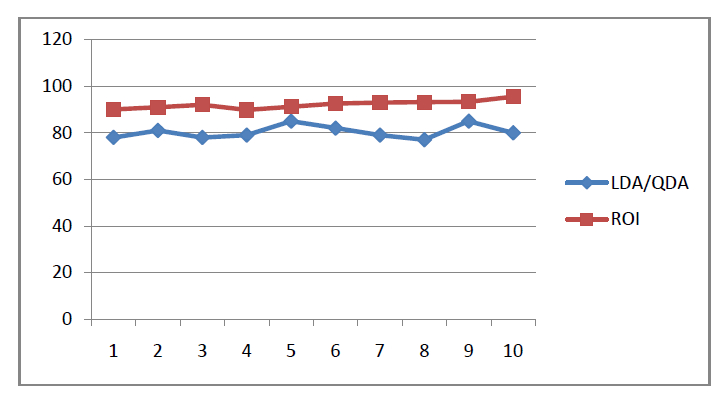 |
V. CONCLUSION AND FUTURE WORK |
| Image quality assessment for liveness detection technique is used to detect the fake biometrics. Due to Image quality measurements it is easy to find out real and fake users because fake identities always have some different features than original. it always contain different color and luminance levels, general artifacts, quantity of information and quantity of sharpness, found in both type of images, structural distortions or natural appearance. This workstudied about Online attendance management system using face recognition and the Quality of an image using image Quality Assessment for Vein recognition has been proposed in this work. |
| In future for making this system more secures adding the one more biometric system into this system and trying to improve the system. |
| • Use of video quality measures for video attacks (e.g., illegal access attempts considered in the replay-attack db.). |
| • Analysis of the features individual relevance. |
References |
|