ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
Gagandeep Kaur1, Poonam Arora2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
Wide range of applications such as disaster management, military and security has drawn attention of researches to this type of networks. There are many issues in wireless sensor networks like battery consumption, scheduling, clustering, packet loss etc. There are many algorithms which are available to reduce these issues. In this paper we introduced new technique which is based upon adaptive technique to prevent packet loss problem. This proposed technique is better than existing technique. In this paper we proposed an Adaptive technique in which we added acknowledgement scheme. By adding acknowledgement concept we reduced the packet collision and increase the network throughput. It implemented using Network Simulator-2.
Keywords |
| WSN, CSMA, Battery Consumption, Packet Loss, Throughput |
INTRODUCTION |
| A wireless sensor network consists of a large number of nodes spread over a specific area where we want to look after at the changes going on there [3]. A sensor node generally consists of sensors, actuators, memory, a processor and they do have communication ability. All the sensor nodes are allowed to communicate through a wireless medium. The wireless medium may either of radio frequencies, infrared or any other medium, of course, having no wired connection. These nodes are deployed in a random fashion and they can communicate among themselves to make an ad-hoc network. If the node is not able to communicate with other through direct link, i.e. they are out of coverage area of each other; the data can be sending to the other node by using the nodes in between them. This property is referred as multi-hoping [4]. All sensor nodes work cooperatively to serve the requests. Generally WSNs are not centralized one as there is peer-to-peer communication between the nodes. So there is no requirement of prior established infrastructure to deploy the network [5]. WSN gives flexibility of adding nodes and removing the nodes as required. But this gives rise to many drastic changes to deal with in the network topology such as updating the path, or the network tree, etc. |
| In a WSN the node that gathers the data information refers to sink. The sink may be connected to the outside world through internet where the information can be utilized within time constraints [6]. The well known problem in using these networks is limited battery life. This is due to fact that the size of a sensor node is expected to be small and this leads to constraints on size of its components i.e. battery size, processors, data storing memory, all are needed to be small. So any optimization in these networks should focus on optimizing energy consumption. In WSN a lot of sensed data and routing information has to be sent which often have some time constraints so that the information can be utilized before any mishap occurs, e.g. industrial monitoring, machinery monitoring, etc. The energy power consumption is much higher in data communication than internal processing. So energy conservation in WSN is needs to be addressed. The remainder of the paper in organized as follows. In section II briefly discusses related work. In section III introduce the CSMA/CA. In section IV explain the proposed modal. The result analyses are packet loss and throughput achieved by using adaptive modulation. |
RELATED WORK |
| Lucas D. P. Mendes et al. [1], they discussed a cross-layer solution is combined to a transmission advertisement scheme to improve a small slotted ALOHA based wireless sensor network throughput and lifetime. To reduced transmission overhead compared to other medium access methods this medium access method scheme has been chosen because it does not add protocol information to be transmitted with data bits. The results shows that, the combination of a cross-layer design and the advertisement scheme has proven to increase the network throughput by more than 10% and to double the network lifetime when compared to a slotted ALOHA wireless sensor network without advertisement. |
| Ossama Younis and Sonia Fahmy [2], proposed a distributed clustering approach for long-lived ad-hoc sensor networks. Proposed approach does not make any assumptions about the presence of infrastructure or about node capabilities, other than the availability of multiple power levels in sensor nodes. They presented a protocol, HEED (Hybrid Energy-Efficient Distributed clustering), that periodically selects cluster heads according to a hybrid of the node residual energy and a secondary parameter, such as node proximity to its neighbours or node degree. HEED terminates in O(1) iterations, incurs low message overhead, and achieves fairly uniform cluster head distribution across the network. |
| Dahlila P. Dahnil, et al. [6], presents a comparative study of clustering techniques and cluster quality of a single criterion cluster heads election and cluster formation in Wireless Sensor Networks. The HEED, LEACH and Energy-based LEACH protocols are simulated and their performance are compared in terms of the number of cluster head generated, cluster size, cluster head distribution, scalability and coverage. The results of these protocols are presented to show how the cluster formation helps to prolong the network lifetime. We investigated scalability aspects in the presence of advanced nodes in the network and its effect on the network lifetime. We proposed to investigate A HEED and AE-LEACH protocols, a new approach for cluster heads election that improved network lifetime in the presence of advanced nodes. The simulation shows that having fraction of advanced nodes in the network gives significant improvement in network lifetime. |
CSMA/CA |
| CSMA/CA (Carrier Sense Multiple Access/Collision Avoidance) is a protocol for carrier transmission in 802.11 networks. Unlike CSMA/CD (Carrier Sense Multiple Access/Collision Detect) which deals with transmissions after a collision has occurred, CSMA/CA acts to prevent collisions before they happen. In CSMA/CA, as soon as a node receives a packet that is to be sent, it checks to be sure the channel is clear (no other node is transmitting at the time). If the channel is clear, then the packet is sent. If the channel is not clear, the node waits for a randomly chosen period of time, and then checks again to see if the channel is clear. This period of time is called the backoff factor, and is counted down by a backoff counter [7]. If the channel is clear when the backoff counter reaches zero, the node transmits the packet. If the channel is not clear when the backoff counter reaches zero, the backoff factor is set again, and the process is repeated. Carrier sense multiple access with collision avoidance (CSMA/CA) in computer networking, is a network multiple access method in which carrier sensing is used, but nodes attempt to avoid collisions by transmitting only when the channel is sensed to be "idle" [8]. The basic idea behind CSMA/CD is that a station needs to be able to receive while transmitting to detect a collision. When there is no collision, the station receives one signal: its own signal. When there is a collision, the station receives two signals: its own signal and the signal transmitted by a second station [9]. To distinguish between these two cases, the received signals in these two cases must be significantly different. In a wired network, the received signal has almost the same energy as the sent signal because either the length of the cable is short or there are repeaters that amplify the energy between the sender and the receiver. This means that in a collision, the detected energy almost doubles. In a wireless network much of the sent energy is lost in transmission. The received signal has very little energy. Therefore, a collision may add only 5 to 10 percent additional energy. This is not useful for effective collision detection. We need to avoid collisions on wireless networks because they cannot be detected. Carrier sense multiple access with collision avoidance (CSMA/CA) was invented for this network. Collisions are avoided through the use of CSMA/CA's three strategies: the inter-frame space, the contention window, and acknowledgments [10]. In controlled access, the stations consult one another to find which station has the right to send. A station cannot send unless it has been authorized by other stations. Three popular controlled-access methods: First reservation method, second Polling method and third one Token passing. CSMA/CA performance is based largely upon the modulation technique used to transmit the data between nodes. Studies show that under ideal propagation conditions (simulations), Direct Sequence Spread Spectrum (DSSS) provides the highest throughput for all nodes on a network when used in conjunction with CSMA/CA and the IEEE 802.11 RTS/CTS exchange under light network load conditions. Frequency Hopping Spread Spectrum (FHSS) follows distantly behind DSSS with regard to throughput with a greater throughput once network load becomes substantially heavy. However, the throughput is generally the same under real world conditions due to radio propagation factors. |
PROPOSED MODAL AND ASSUMPTION |
| The route from the source to destination is established with the Proactive and reactive routing protocols. The Proactive routing protocols are those which store the route matrix and with the use of these matrixes reliable route is established between source and destination. In the MANET, it is very difficult to maintain such matrixes due to its self configuring nature. In such, case another type of routing protocol, .i.e. Reactive routing protocols is used for the route establishment. In reactive routing protocols routes are established between source and destination only when required. AODV and DSR are two most common types of protocols which are used for the route establishment. In AODV routing protocol dijkstra's algorithm is been used, as compared to DSR it is single source algorithm and bellman’s ford algorithm is used for route establishment. Both the protocol, i.e. AODV and DSR use the flooding approach for the route establishment. The route request messages are flooded into the network, and intermediate nodes which are having the path to destination will reply back with the route reply packets. The source selects the best path on the basis of Hop count and sequence number. In the approach of flooding, the network resources like bandwidth, node energy will get wasted. To overcome the problem of flooding approach will be replaced with the multicasting approach. In this work, we mainly focus on to embed the approach of multicasting in AODV protocol for route establishment between source and destination. |
| A WSN composed of 20 sensor nodes. All the nodes in sensor network can be partitioned into small groups is called clusters. In each cluster has a cluster head and rest nodes are member of that cluster. The clustering involves grouping nodes into clusters and electing cluster heads periodically such that members of a cluster can communicate with their cluster heads and these cluster heads send aggregated data received from its members to a base station. There are also four cluster head in each scenario which are communicates with sink. The sink is present at the centre of all the clusters. Adaptive technique is used in it. In adaptive technique as shown in Figure 1 we use adaptive packet request and adaptive packet response for channel access. If any cluster wants channel access than it first send adaptive packet request to the sink. If sink is available, it sends adaptive packet response to cluster head. It also sends response packets to all other cluster head that time sink is busy with this particular cluster head. Now the main problem occurs when there is collision between Adaptive requests of one cluster with Adaptive response of other cluster. At this situation, packets of two clusters collide with each other and packet loss problem begins. That problem solve when cluster head receive response it sends acknowledgment to the sink that it has received response successfully. If acknowledgement is not receives by the sink than it send again response to the cluster head in threshold time. By doing so, packet loss problem is overcome using CSMA/CA solution. |
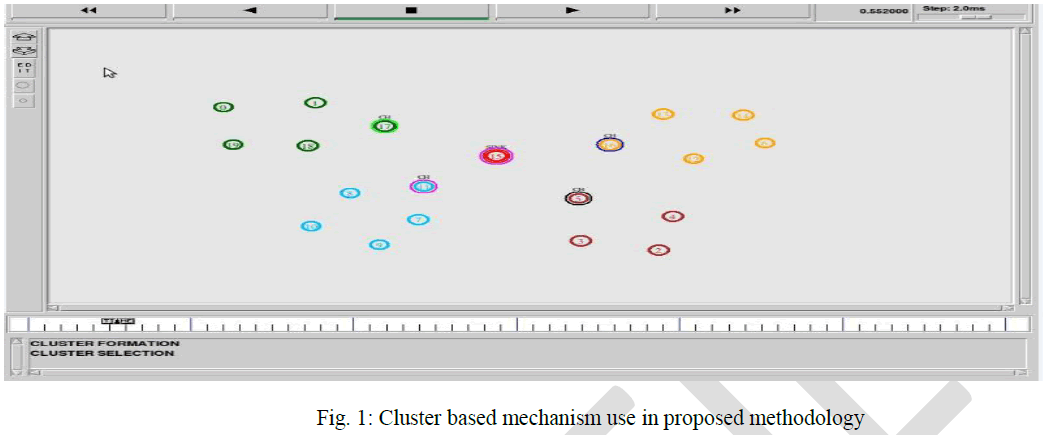 |
RESULT AND DISCUSSION |
| NS2 is used as a simulation platform. NS is a discrete event simulator, where the advance of time depends on the timing of events which are maintained by scheduler. NS simulator is based on two languages: C++, and an OTcl (an object oriented tool command language) interpreter used to execute users command scripts. |
1). Simulation analysis: |
| To analyse and reducing the packet collision and increase the network throughput by using adaptive technique. Sensor node distributed in 800X800 areas. |
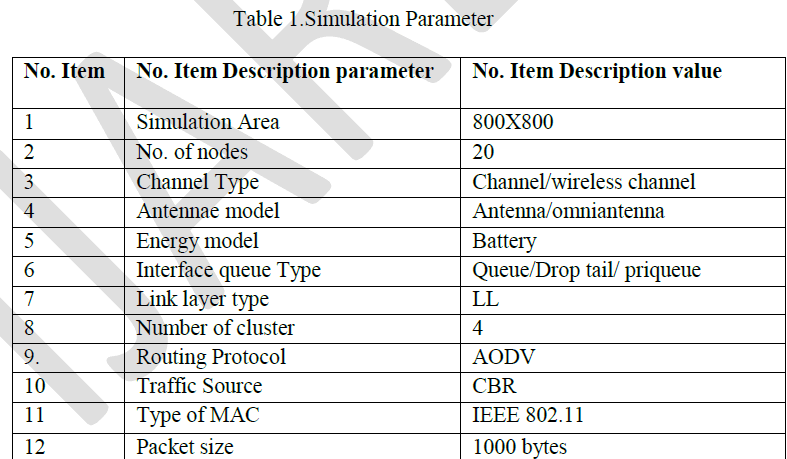 |
2). Simulation Result: |
| The Results of the simulation are shown in the figure 2, figure 3 which shows the packet loss and Throughput in the sensor network |
2.1). Packet Loss: |
| Packet loss is the total number of packets dropped during the simulation. Packet loss is difference between numbers of packet send and numbers of packet receive. Packet loss the network also decreases with new proposed technique. Red line show new packet loss and green line shows old packet loss. |
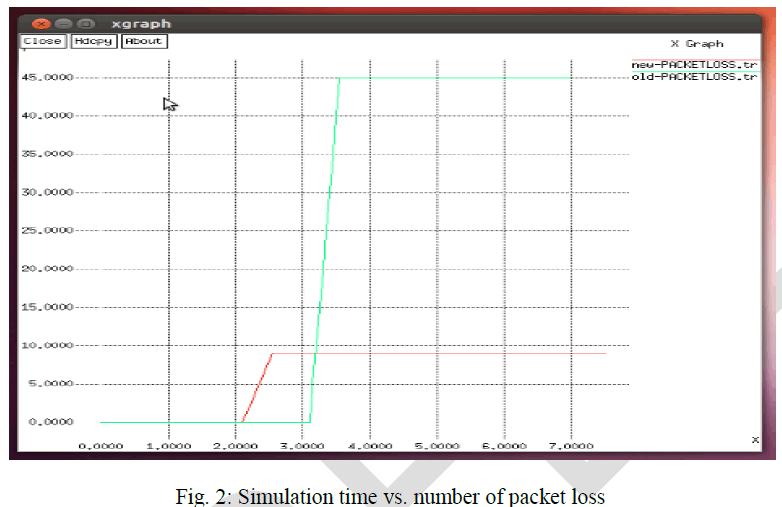 |
2.2). Throughput: |
| Throughput is the average rate of successful message delivery over a communication channel. Figure 3 shows that throughput of network increase with proposed method as compare to existing method. In figure 3 below Red line represent new throughput graph and green line represent old throughput graph. |
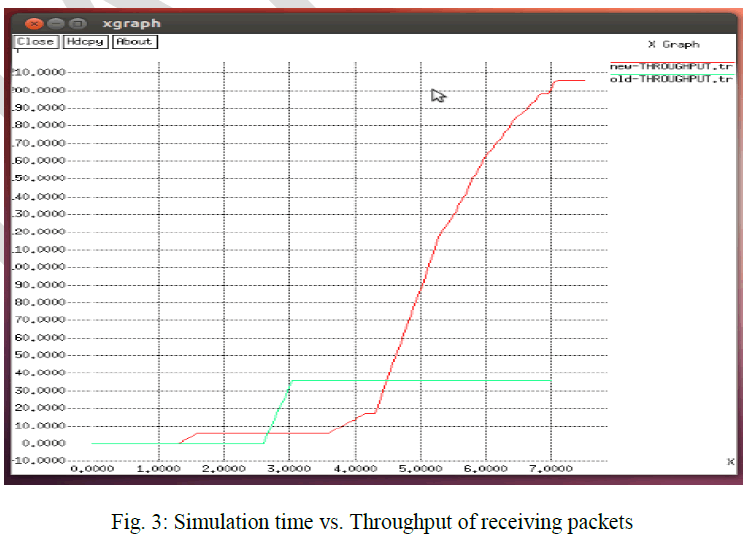 |
CONCLUSION |
| The main objective of this research paper is to discuss various challenges and technique of WSN. We also focused on adaptive technique and its procedure. We believe that proposed algorithms discussed in this paper will give benefit for various research scholars. Its experimental results show that proposed technique gives better result which has better throughput and less packet loss as compare to existing techniques. |
References |
|