ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
T.Keerthikala1 , L.Hemalatha2 , B.Sundarraj3
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
The data transfer rate in maximum level of network. It is used to observe how much amount of data can send through connection. Most of the networks are fail to guess the bandwidth availability accurately in the wireless setting. So that advance bandwidth reservation can become a critical task to improve the network resources utilization. This type of system will provide increased inconsistency of wireless channel conditions difficult for bandwidth calculation. To overcome these problems we are introducing a scheme as “Bandwidth Recycling”, (i.e.) to recycle the unused bandwidth without changing the existing bandwidth reservation. We are calculating the each node in the networks bandwidth calculation considering through the queries for long time periods. For small scale networks we are using optimal algorithm with exponential time complexity, for large scale networks we are developing the heuristics with polynomial time complexity and we are using token bucket algorithm to avoid packet loss while it travelling in the network. By using this bandwidth calculation we can achieve both good accuracy and accurate levels in the networks for each node.
KEYWORDS |
| Bandwidth calculation, Bandwidth recycling, probe packets, Qos. |
I. INTRODUCTION |
| Bandwidth can be used in E-business, file transfer and network connections. While sending the files or any document in the network out of the bandwidth the data will be loss. To overcome this problem we are introducing bandwidth recycling concept [6]. |
| The objective of available bandwidth calculation is to assume the service offered by a network path from traffic measurements [3] taken by end system only. In bandwidth calculation [3,4] methods, end systems exchange time stamped probe packets [4] and study the distribution of these packets after they have traversed a network of nodes. Many most of the popular methods for available bandwidth estimation [4] are based on congestion including packet trains, a sequence of probe packets are available in the probe trains. By sending packet trains at the rate exceeding the available bandwidth, the networks becomes congested, there by imprinting information on the network state on the distribution of probe packets. We distribute with the modeling assumption of a work conserving queuing system [9] and taking advantage of concepts from the uncertain network calculus replace it with that of a general stationary system. |
| To improve the information measure utilization whereas maintaining constant QoS [1] secured services, our analysis objective is twofold: 1) the present information measure reservation is not modified to keep up constant QoS secured services. 2) Our analysis work focuses on increasing the information measure utilization by utilizing the unused information measure[5]. we tend to propose a theme, named Bandwidth Recycling[6], that recycles the unused information measure whereas keeping constant QoS secured services while not introducing further delay. the overall idea behind our theme is to permit different SSS to utilize the unused information measure left by the present sending SS. Since the unused information measure is not presupposed to occur often, our theme permits SSS with non-real time applications, that have a lot of flexibility of delay necessities, to recycle the unused information measure. Consequently, the unused information measure within the current frame will be used. Its completely different from the information measure adjustment during which the adjusted information measure is enforced as early as within the next coming back frame[10]. Moreover, the unused information measure[10] is probably going to be discharged briefly (i.e., solely within the current frame) and therefore the existing information measure reservation does not modification. Therefore, our theme improves the general output whereas providing constant QoS secured services. There are two varieties of BRs outlined within the IEEE 802.16 [6] standard: progressive and combination BRs. the previous enable the SS to point the additional information measure needed for a affiliation. Thus, the number of reserved information measure will be solely accrued via progressive BRs. On the opposite hand, the SS specifies the present state of queue for the actual affiliation via a combination request. The baccalaureate resets its perception of that service’s wants upon receiving the request. Consequently, the reserved information measure could also be small through this we are able to achieve Qos and good accuracy for giant scale networks and for tiny scale networks. |
II. EXISTING SYSTEM DRAWBACK |
| In existing system calculate the bandwidth efficiency of each node to be distributed as a constant rate of fixed efficiency. We have buffer space for storing purpose. Each node access the bandwidth as depending upon the data, system and accessibility of that node. We use the bandwidth o each node as content rate depending on the data packets at the bandwidth. The excess bandwidth is not used of each node. In some conditions some nodes have a least bandwidth based on the content rate. |
III. ALGORITHM |
| A. Polynomial time complexity |
| Time complexity of an algorithm is measures how much amount of time taken by an algorithm to run as a function. It is commonly calculate by counting the number of elementary operations perform an algorithm. |
| Polynomial time complexity is used to measure the time taken for to perform an operation. Polynomial time is basically performs the mathematical operations. |
| In this paper heuristic with polynomial time complexity used to measure time taken for each packet sending from source system to destination system in network and it is also used to measure the time taken for all packets sending from source system to destination system in the network. It is used only in large scale networks. The results of this algorithm will give the approximate results. |
| B. Optimal algorithm |
| Optimal algorithm is used to assume knowing the future. It is not used for longest period of time [10]. |
| In this paper optimal algorithm is used to know the upcoming packets (i.e)its already allocated in the queue. It is used in small scale networks. |
| C. Exponential time complexity |
| In this paper exponential time complexity algorithm is used to measure time taken for each packet sending from source to destination system. It is used in small scale networks. |
| D. Core stateless fair queuing algorithm |
| It is used to reduce the implementation complexity yet still packets achieves destination. It send packets in FIFO method. |
| E. Token bucket algorithm |
| It can be used to check that data transmissions, in the form of packets. In our paper if the bucket fill with the packets, the packets send in the network in the sequence order by using the core stateless fair queuing algorithm [1]. |
IV. WIRELESS NETWORKS |
| The devices are connected without wires are called wireless. By using wireless networks we can share and access information directly in the same location and same time in the easier manner. It is easy process compare with the wired network. Wireless network[1,3] is convenience to access information and share information. It can access anywhere and it provides robust security protection. |
V. RELATED WORKS |
| 1) Ravindra R Patil,” Token Based Fair Queuing Algorithms for Wireless Networks”, IJSEAT, Vol 2, Issue 4, April,2014. |
| The paper develops single carrier Time Division Multiple Access (TDMA) systems, to suit WINNER Orthogonal Frequency Division Multiple Access (OFDMA) air-interface. This algorithm mainly concentrated in Qos. In this paper token based scheduler is used. In this we can predict the user terminal from higher interference by using Token based fair queuing. |
| 2) Umme Gousia, Dr.Mohd.Abdul.Waheed, Syed Shah Md Saifullah Hussaini,” A Dynamic Performance- Based Flow Control Method for High-Speed Data Transfer”, IJCSN, Vol.2, Issue 4, August 2013. |
| The paper develops a protocol, performance, adaptive UDP (hence PA-UDP),which dynamically and autonomously systems. Based on models, it has been implemented under Linux and the experimental results demonstrate that PA-UDP out performs other existing high-speed protocols in terms of packet loss, throughput and CPU utilization. PA-UDP is efficient for reliable high-performance bulk data transfer over dedicated local area networks using rate control algorithm |
| 3) Ajeet Kumar Singh, Jatindra Kr Deka, ”A Study of Bandwidth Measurement Technique in Wireless Mesh Networks”, IJASUC, Vol.2, No.3, September 2011. |
| In this paper introducing a new technique to estimate bandwidth for wireless mesh networks and multi-hop wireless network. Here we are using the statistical measurement technique to avoid delay and effect of random errors in wireless channels. Estimation based on the dispersion principle that uses probe packet trains. |
| 4) Vishnu Kumar Sharma, Dr. Sarita Singh Bhadauria,” Agent based Bandwidth Reservation Routing Technique in Mobile Ad Hoc Networks”, IJACSA,Vol. 2, No. 12, 2011. |
| This paper proposed an agent based bandwidth reservation technique for MANETs. The mobile agent from which source starts forwarding the data packets trough the path which has minimum cost, congestion, and bandwidth. In this resource allocation technique reduces the losses and improves the network performance. |
| 5) Er.S.Sharma, Er.A. Singhal,” A PDF Based Dynamic Bandwidth Allocation Algorithm Using Last Recent Polling Table”, IJAIEM, Vol. 2, Issue 7, July 2013 |
| By using EPONs we presented a PDF-polling bandwidth allocation algorithm. It improves the network performance in the terms of queue length, packet delay and bandwidth utilization as a well known efficient DBA algorithm proposed. This algorithm will improve the Qos and support the different type traffic loads. |
VI. LITERATURE SURVEY |
Paper 1:A Dynamic Performance-Based Flow Control Method for High-Speed Data Transfer |
| This paper builds up a convention, Performance Adaptive UDP (consequently PA-UDP),which intends to progressively and self-sufficiently expand execution under diverse frameworks. A scientific model and related calculations are proposed to portray the hypothetical premise behind powerful cushion and CPU administration. A novel postponement based rate throttling model is likewise exhibited to be exceptionally exact under various framework latencies. Taking into account these models, we executed model under Linux, and the test results show that PA-UDP out performs other existing high velocity conventions on thing equipment regarding throughput, bundle misfortune, and CPU use. Dad UDP is productive for fast research systems, as well as for solid elite mass information exchange over devoted neighborhood where clogging and decency are normally not a worry. Here we are utilizing rate control calculation. |
Paper 2: Scheduling and Transport for File Transfers on High-Speed Optical Circuits |
| Arranging resources on Grids is a remarkable issue. The extension of Grids to Lambda Grids obliges the booking of lambdas, i.e., end-to-end fast circuits. In this paper, we propose a booking heuristic for such lambdas in maneuvering of generous scale legitimate applications that oblige high-throughput trades of tremendous files.We imply this heuristic as 'Changing Bandwidth List Scheduling' (VBLS) because the scheduler gives back a Time- Range-Capacity (TRC) distribution vector with varying information transmission levels consigned for various time goes inside the compass of a trade. The purpose of enthusiasm of VBLS more than a changed information exchange limit segment arrangement is that it allows the scheduler to trim any openings left in resource assignments. Enabling VBLS obliges end host applications to show the record measure in their trade requests. To depict VBLS, we ran reenactment investigates that exhibit that VBLS execution methodologies pack trading execution. This result suggests that record trades can take advantage ofbandwidth that becomes acquainted with open resulting to the start of trades, a present and segregating inconvenience of basic settled information transmission task plots in circuittraded frameworks. Next, we recognize the key highlights needed in a vehicle tradition that works in conjunction with VBLS and add to the 'Changing Bandwidth Transport Protocol'(VBTP). VBTP is a rate based stream control scheme that is coupled with Selective-ARQ based goof control. Finally, the paper closes with a dialog on the impact of transport issues on VBLS booking. Here we are using File-trade arranging counts and Lambda-Scheduling Algorithm |
Paper 3: Lambda scheduling algorithm for file transfers on high-speed optical circuits |
| Planning assets on Grids is a remarkable issue. The expansion of Grids to Lambda Grids obliges booking of lambdas, i.e., end-to-end fast circuits. In this paper, we propose a heuristic for the planning of lambdas particularly for document exchanges, given that numerous e-Science applications oblige high-throughput exchanges of extensive records. We call this heuristic Varying-Bandwidth List Scheduling (VBLS) on the grounds that the scheduler gives back a period range-limit (TRC) allotment vector with changing transfer speed levels doled out for diverse time extends inside the term of an exchange. The point of interest of VBLS more than a settled data transfer capacity allotment plan is that it permits the scheduler to inlay any openings left in asset allotments. Such a plan is empowered by end host applications indicating the record estimate in their exchange demands. To portray VBLS, we utilized explanatory models and ran recreations. Our outcomes demonstrate that VBLS execution is near to bundle exchanging execution, which implies that record exchanges can exploit data transmission that gets to be accessible consequent to the begin of exchanges, a basic disadvantage of common altered transfer speed designation plots in circuit-exchanged systems. Here we are utilizing File-exchange booking calculations and Lambda- Scheduling Algorithm |
Paper 4: Networks With Advance Reservations: The Routing Perspective |
| This paper gives a starting take a gander at how bolster for development reservations influences the many-sided quality of the way choice process in systems. Advance reservations are liable to end up progressively imperative as systems and dispersed applications get to be practically wealthier, and there have been various past works and examinations that investigated different related viewpoints. Be that as it may, the effect of development reservations on way determination is a point that has been left generally untouched. This paper researches a few administration models for development reservations, which extend from the conventional fundamental model of saving a given measure of data transmission for quite a while later on, to more complex models went for expanding the adaptability of administrations accessible through development reservations. The emphasis is basically on the issue of computational multifaceted nature when supporting development reservations, and in that connection, we determine various calculations and/or obstinacy results for the different models we consider. Here we are utilizing Path determination and Routing calculations. |
Paper 5: Packet Fair Queuing Algorithms for Wireless Networks with Location-Dependent Errors |
| While Packet Fair Queuing (PFQ) calculations give both limited postpone and reasonableness in wired systems, they can't be connected straightforwardly to remote systems. The key trouble is that in remote systems sessions can encounter area ward channel blunders. This may prompt circumstances in which a session gets fundamentally less administration than it should, while an alternate gets more. This outcomes in vast disparities between the sessions' virtual times, making it hard to give both postponement ensures and decency at the same time. |
VII. PROPOSED SYSTEM |
| Excess bandwidth allocation can be designed in shared access networks and propose ISP traffic control schemes based on core-stateless fair queuing (CSFQ) and token bucket algorithm. If the reserved bandwidth more than the demand, we can use that balance bandwidth for another user. That can be adjusting via buffers. The unused reserved bandwidth can be applied as early as to the next coming frame and there is no way to utilize in current frame. By using token bucket algorithm[1] we can avoid the traffic issues and compromise Qos. |
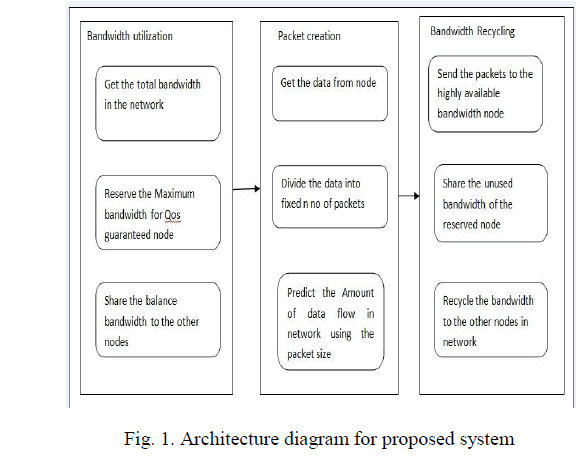 |
| The main idea of this project is to reduce the bandwidth constraints while transferring the packets from node to node. For that the first thing here is bandwidth utilization[5] in this it will get the total bandwidth in the network and it will reserve the maximum bandwidth for QOS guaranteed node. It is different from the bandwidth adjustment in which the adjusted bandwidth is enforced as early as in the next coming frame. The unused bandwidth is likely to be released temporarily (i.e., only in the current frame) and the existing bandwidth reservation does not change. So that it improves throughput while providing the same QoS guaranteed services. Next it will share the remaining or balance bandwidth the other nodes. The second step is Packet creation in this it will get the data from the node and it will divide the data into fixed n number of packets. Using packet size it will predict the amount of dataflow in the network. After predicting it will go for bandwidth recycling [6,10], it will send the packet to the highly available bandwidth[2,7,8] node and it will share the unused bandwidth of the reserved node, it will recycle the bandwidth to the other nodes in the network through this we are getting the information without loss, Qos and bandwidth can be utilized fully. |
VIII. SIMULATION RESULTS |
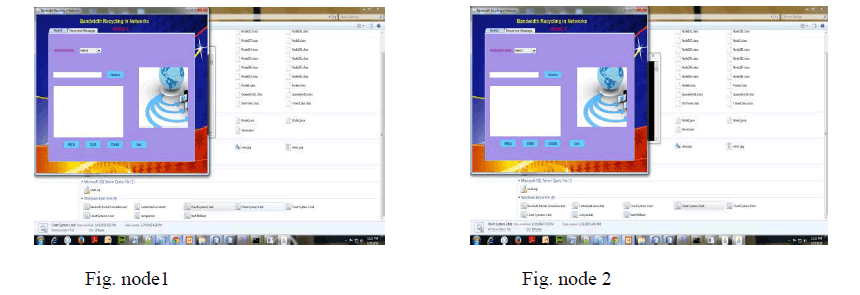 |
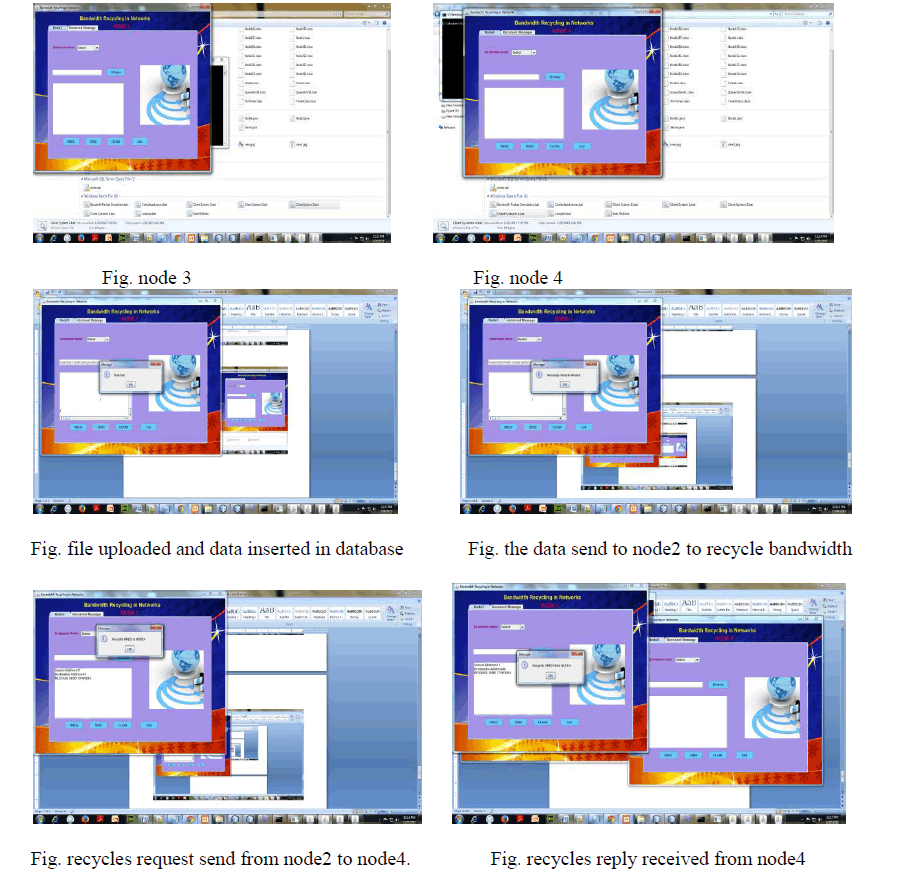 |
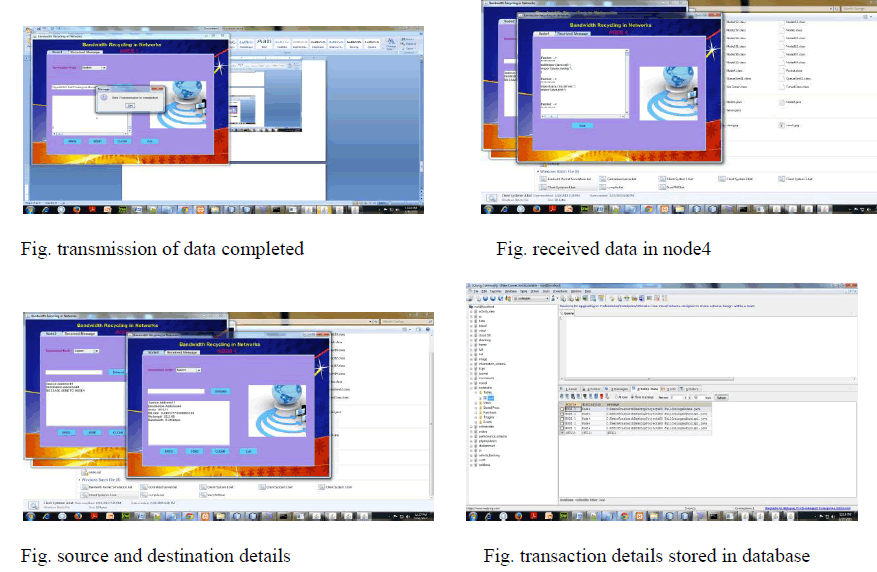 |
IX. CONCLUSION |
| Our proposed system will not change the present bandwidth that recycles the unused bandwidth that occurs once. This will provide the base station to allocate a complementary station for every transmission station. The entire CL transmission interval will monitor the every complementary station and to recycle the unused bandwidth [6,10]. The algorithms used in proposed work are Token bucket algorithm, Core stateless fair queuing [9] algorithm, Exponential time complexity, Polynomial time complexity. At last our work shows that it not only improve the through put and also reduces the delay along with satisfy the Qos requirement. |
References |
|