ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
D. D. Walanjkar, Prof. Vaishali Nandedkar
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
Textual password is most coomn method use for password authentication. In today’s use of internet is increasing day by day. For security purpose the user selects password, that password are text based passwords or graphical passwords. Most of the user uses text based password because that are easy to remember. But main disadvantage of using text based passwords are many attacks can happen like eavesdropping attack, dictionary attacks, denial of service attacks. To overcome the disadvantages of text based password new graphical passwords are used. Click based graphical password scheme offers a novel approach to address the well known image hotspot problemin popular graphical password systems, such as PassPoints, that often leads to weakpassword choices. So to provide user friendliness and also the protection from various security attacks use of graphical password is important. In this, graphical password scheme, the click event isperformed on various points on same or different images.
Keywords |
| Graphical passwords, password guessing attacks, security primitive, random question generator, CaRP. |
INTRODUCTION |
| The graphical password is new technique which is more secure than text based passwords. In graphical passwords, sequence of clicks is generated to derive the password. The click events are performed on same image or on different image. Or user can also selects sequence of images. Graphical passwords offers protection against the dictionary attacks which is major security threat in online applications. Graphical passwords also provide protection against the relay attacks. |
| The main motivation for graphical passwords is the hypothesis that people are better at remembering images than artificial words. Visual objects seem to offer a much largerset of usable passwords. For example user can recognize the people which he knowsfrom thousands of faces; this fact was used to implement an authentication system. Asanother example, a user could choose a sequence of points in an image as a password;this leads to a vast number of possibilities, if the image is large and complex, and if ithas good resolution. |
| To overcome the shortcomings of textbasedpasswords, graphical passwords have been proposed. Inmost of the schemes, graphical password employs graphicalpresentations such as icons, human faces or custom images tocreate a password. Human brains can process graphical imageseasily. Graphical passwords claim to be superior to the textbased passwords due to this human characteristic. Thesemethods assume if the number of possible pictures issufficiently large, the possible password space of a graphicalpassword scheme may exceed that of text-based password andtherefore it is virtually more resistance to attacks such asdictionary attacks.Many graphical password schemes are already introduced. Graphical password techniques can beclassified into two categories; recognition-based and recallbased.In recognition-based systems, a series of images arepresented to the user and a successful authentication requirescorrect images being clicked in a right order. In recall-basedsystems, the user is asked to reproduce something that he orshe created or selected earlier during the registration. The pastdecade has seen a growing interest in using graphicalpasswords as an alternative to the traditional text-basedpasswords. |
| The paper covers the graphical password used in authentication system; there are chances of attacks on graphical password also so to overcome this new technique introduced random question generation; after user gives right answers to question which are provided to him/her then only user can enter into the system. |
II. LITERETURE SURVEY |
| The need for graphical password is increasing day by day because graphicalpasswords are easy to recall and less likely to being written down also it has greater potential to provide a more symbol space than text based passwords.Many researchers are working on the concept of graphical passwords, some of them also introduced new ideas and some of them are still working to introduce new ideas to provide more secure approach related to graphical passwords. Already, there are many schemes have been proposed in present times. The first idea of graphical password has been given by Blonder in 1996. In Blonder’s scheme, in front of user an image is displayed which is predetermined image on any visual display device which user is using then user has to select one or more positions on image which are already known positions to user in a particular order to access the particular resource[5]. The disadvantage of this method is that users cannot click other positions than known positions so this also works same as text based passwords.A PassPoint[6] method the idea of Blonder’s scheme is used t and further extended to overcome the drawback of Blonder’s method.In PassPoints[6] the predefined boundaries of images are eliminated and arbitrary images are allowed to be used. Because of this when user wants to create password he can click on any place on image without restriction of any boundaries. After the password is created a tolerance around each chosen pixel is calculated, then for authentication of user, the user must click within the tolerance of theirchosen pixels and also in the correct sequence when user wants to access restricted resource or any application which is restricted. |
| In Cued Click Points (CCP), a cued-recallgraphical password technique [7], in this technique, a password is composed of oneclick-point per image for a sequence of 5 images. The nextimage displayed is based on the previous click-point so usersreceive immediate implicit feedback as to whether they are onthe correct path when logging in. A wrong click leads down anincorrect path, with an explicit indication of authenticationfailure only after the final click. The advantage of CCP over PassPoints is the fact that authorized usersget feedback about an error when trying to log in within a second.When users see an incorrect image, they know that the latestclick-point was incorrect and can immediately cancel currentattempt and the process is strated again from beginning. |
| Grid basedschemes are also proposed which uses recall method. A technique called “Draw A Secret” (DAS) [8]where a user draws the password on a 2D grid. Thecoordinates of this drawing on the grid are stored in order.During authentication user must redraw the picture. The useris authenticated if the drawing touches the grid in the sameorder. The major drawback of DAS is that diagonal lines aredifficult to draw and difficulties might arise when the userchooses a drawing that contains strokes that pass too close to agrid-line. Users have to draw their input sufficiently awayfrom the grid lines and intersections in order to enter thepassword correctly. If a user draws a password close to thegrid lines or intersections, the scheme may not distinguishwhich cell the user is choosing. A system where authentication is conducted by having the userdrawing his/her signature using a mouse [9]. The biggestadvantage of this approach is that there is no need tomemorize one’s signature and signatures are hard to fake.However, not everybody is familiar with using mouse as awriting device; the signature can therefore be hard to drawn.A graphical authenticationscheme [10] in which the user selects certain number of imagesfrom a set of random pictures during registration. Later userhas to identify the pre-selected images for authentication. Theusers are presented a set of pictures on the interface, some ofthem taken from their portfolio, and some images selectedrandomly. For successful authentication, users have to select‘their’ pictures amongst the distracters. |
| Passface is a techniquedeveloped by Real User Corporation based on the assumptionthat people can recall human faces easier than other pictures[11]. Here the user is asked to choose four images of human facesfrom a face database as their password.These techniques have the potential to fill the gaps leftbetween traditional authentication techniques, including tradeoffsbetween security levels, expense and error tolerance. Butunfortunately there is a common weakness in the abovegraphical password schemes: They are all vulnerable toshoulder-surfing attacks. To address this issue, a graphical password technique [12]. In theirscheme, the system first displays a number of 3 pass-objects(pre-selected by a user) among many other objects. To beauthenticated, a user needs to recognize pass-objects and clickinside the triangle formed by the 3 pass-objects. |
| A Scalable Shoulder-Surfing ResistantTextual-Graphical Password Authentication Scheme (S3PAS) [13].In this scheme, user is provided with the login-image whichconsists of 93 printable characters. To login, the user mustfind all his/her original pass-characters in that image and thenmake some clicks inside the invisible triangles which arecalled pass-triangles. The pass-triangles are created by 3original pass-characters following a certain click-rule. In thisscheme, user pass-character lies inside the pass-triangle. If theuser password length is k then he has to click k-times insidethe invisible pass-triangles. In S3PAS if the size of every pass trianglearea is too large, attackers are able to click inside theright areas with higher probabilities. A recognition-based graphical password schemeColorLogin[14], it is implemented in an interesting game way toweaken the boring feelings of the graphical authentication.ColorLogin uses background color, a method not previouslyconsidered, to decrease login time greatly. Multiple colors areused to confuse the peepers, while not burdening thelegitimate users. The scheme is resistant to shoulder surfingattack but password space is smaller than text-basedpasswords. Another shoulder-surfingresistant algorithm in which a user selects a number ofpictures as pass-objects[15]. Each pass-object has several variantsand each variant is assigned a unique code. Duringauthentication, the user is challenged with several scenes.Each scene contains several pass-objects and many decoyobjects.The user has to type in a string with the unique codescorresponding to the pass-object. However, these methodsforce the user to memorize too many text strings, and theirshoulder-surfing resistant property is not strong either. In realscenario, these approaches are under-utilized as theauthentications are usually complex and boring for users. |
| One more method based on recognition based scheme is ClickAnimal[1]. This is a captach scheme, in this 3D models of horse and dog are used to generate 2D animals with different colors, textures poses and arranges them on background such as grassland. When the animals are arranged on background, some animals may be overlapped with each other but main parts are not overlapped in order to identify by human. The ClickAnimal has a smaller password space than ClickText[1], in ClickText the alphabets are displayed but alphabets are not overlapped user can easily clicks on them to create or select password. Here when user click on any alphabet then location is tracked to check whether user clicks on correct character. ClickText[1] is also the recognition based scheme to generate graphical passwords |
III. EXISTING SYSTEM |
| In existing system [1], CaRP (Captch as aRaphical Password) is used to authenticate the system. Here, the graphical password is used to authenticate the user instead of text based password. When user enters into the system then user enter the userID after that system generate the image, user then perform click events, if the click events matches with the system database then user authentication is successful otherwise authentication fail. Following figure illustrates the above procedure: |
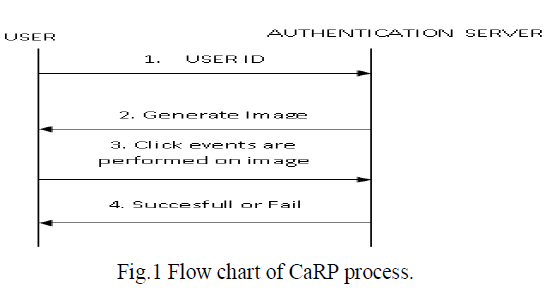 |
| But the problem with this method is that any person can concentrate and get the password when user is clicking on the image. So new method is introduced to multiple existing system problems, that method is discussed in section IV. |
IV. RELATED WORK |
| Dhamija and Perrig[11] proposed a graphical authentication scheme where the user hasto identify the pre-defined images to rove user’s authenticity. In this system, the user selects acertain number of images from a set of random pictures during registration. Later, during loginthe user has to identify the pre-selected images for authentication from a set of images as shownin figure 1. This system is vulnerable to shoulder-surfing. |
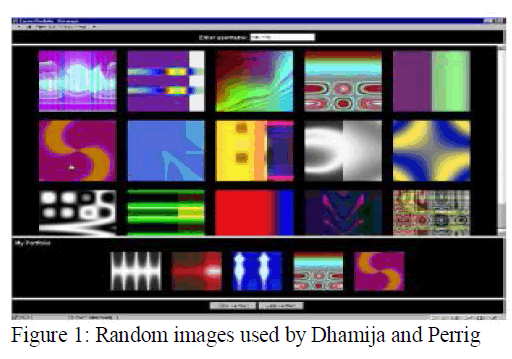 |
| Passface [12] is a technique where the user sees a grid of nine faces and selects one facepreviously chosen by the user as shown in figure 2. Here, the user chooses four images ofhuman faces as their password and the users have to select their pass image from eight otherdecoy images. Since there are four user selected images it is done for four times. |
 |
| Jermyn, et al. [13] proposed a new technique called “Draw- a-Secret” (DAS) as shown in figure 3 where the user is required to re-draw the pre-defined picture on a 2D grid. If the drawing touches the same grids in the same sequence, then the user is authenticated. This authentication scheme is vulnerable to shoulder surfing. |
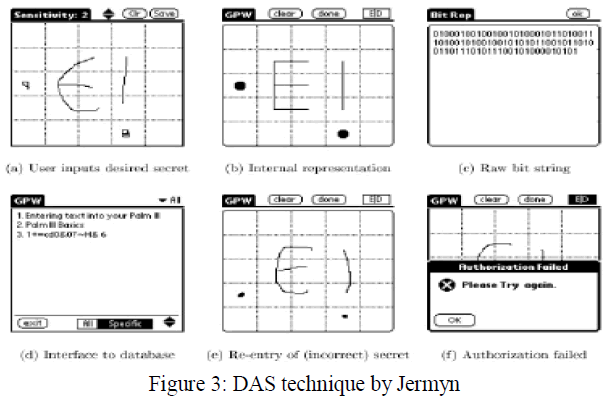 |
| Syukri [14] developed a technique where authentication is done by drawing user signature using a mouse as shown in figure 4. This technique included two stages, registration and verification. At the time of registration stage the user draws his signature with a mouse, after that the system extracts the signature area. In the verification stage it takes the user signature as input and does the normalization and then extracts the parameters of the signature. The disadvantage of this technique is the forgery of signatures. Drawing with mouse is not familiar to many people, it is difficult to draw the signature in the same perimeters at the time of registration. |
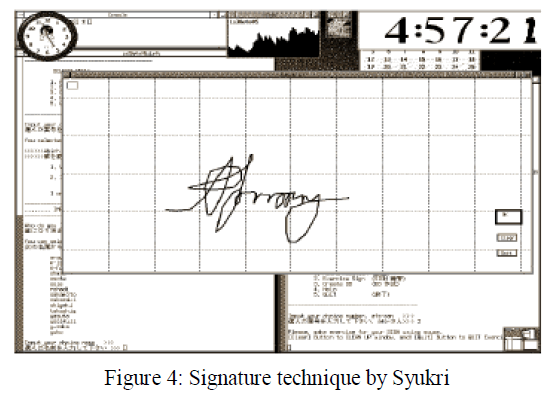 |
| Blonder [15] designed a graphical password scheme where the user must click on the approximate areas of pre-defined locations. Passlogix [16] extended this scheme by allowing the user to click on various items in correct sequence to prove their authenticity. |
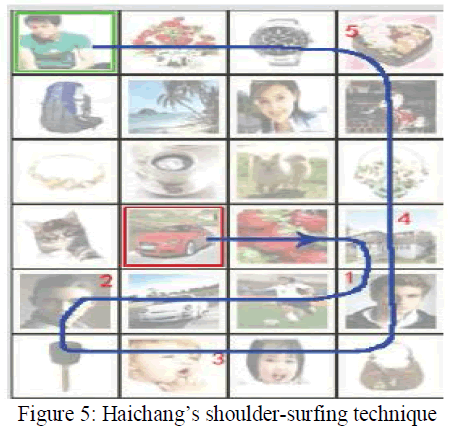
| Haichang et al [17] proposed a new shoulder-surfing resistant scheme as shown in figure 5 where the user is required to draw a curve across their password images orderly rather than clicking on them directly. This graphical scheme combines DAS and Story schemes to provide authenticity to the user. |
 |
V. PROPOSED WORK |
| In this proposed system we use same CaRP scheme toauthenticate the user. But to provide more secure approach mobile interface is introduced. Proposed system includes the following two models: |
A] Random Question Generation: |
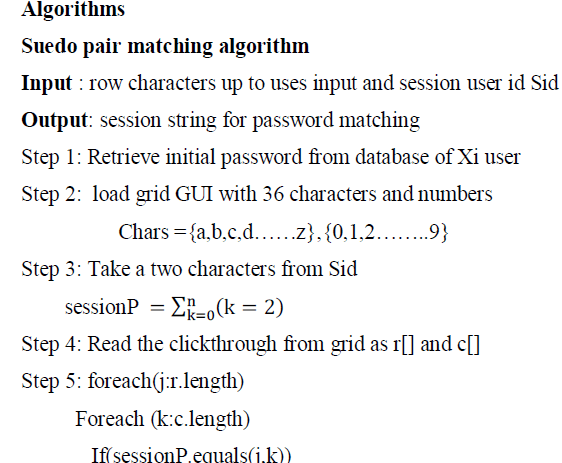
| If any unauthorized/ Untrusted persons know pattern of click based graphical password, then easily enter into the system. To overcome this problem, the proposed method introduces generation of random questions. For this user answers questions (20) asked in registration process. Then save graphical password and question with their respected answers in database. |
B] Mobile Interface for answering generated question: |
| In Login process, after user enter the click based password if it is correct then any two questions from the saved questions during the registration process are send on mobile from registered questions. If user able to correct answer then only login get successful. |
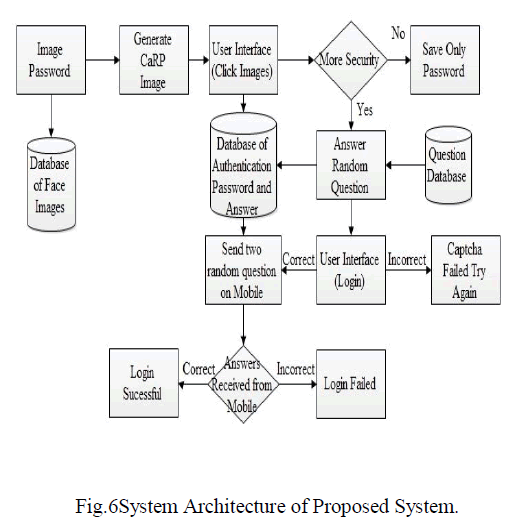
| The system architecture is shown in fig.6; |
 |
 |
 |
VI. CONCLUSION |
| I like to acknowledge my vigorous thanks to Prof. Nandedkar for providing giving suggestions which helped me a lot in my research work and I also want to thanks our friends and classmates for helping me in this research work by giving me there timely suggestions and feedbacks on my research work. |
References |
|