ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
Augustus P P1, David Solomon George2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
In this paper, an algorithm for invisible watermarking of digital images has been proposed. This scheme provides self authentication and recovery of watermarked image. The tampered regions in an image, if any, are detected and the recovery of those altered regions are facilitated by the proposed scheme. Image authentication is performed in 4×4 sub-block level. Self recovery is accomplished through descriptors, which enable in reconstructing the altered regions with acceptable quality. The descriptor details corresponding to each region are spatially separated from region of impact. Discrete Wavelet Transform (DWT) and Inverse Discrete Wavelet Transform (IDWT) are employed for the transformations within the image for block based retrieval. The proposed algorithm is experimentally verified and the results are presented.
Keywords |
| Authentication, descriptor, digest, watermarking |
INTRODUCTION |
| Advances in computing hardware, software and networks have created threats to copyright protection and content integrity. Nowadays, softwares are available in market to fruitfully modify the image. With the advent of social networking sites, uploading and sharing of photos became an inevitable need. User community of such sites comprise of people around the globe. However, no measures are currently incorporated in the present day social networking sites to provide reliability of their multimedia content [1]. Therefore, now it is easy to copy, modify and distribute images. Malicious persons can acquire images from the internet and use versatile digital image processing tools to modify them without leaving a trace [2], [3]. The truthfulness of the images shared on the Internet is therefore questionable. These tools are capable of creating ambiguity to pick the original image in midst of spoofed ones. Images, thus uploaded in social networking sites are very much prone to such alterations. The alterations may be casual in some scenario, while harmful in others. Therefore, the need arises to ensure the authentication of digital images. It would be pleasing if the original image details are retrieved from the altered image. Prime concern lies in ensuring the authenticity of target image. Image authentication involves confirmation of the authenticity of image content and the detection of localized alterations, if any. The authentication watermark employed may be visible or invisible. Visibility is formulated based on whether it is perceivable to human eye or not. Many robust, fragile and semi-fragile techniques are available to provide authentication to digital images [4]. Robust watermarks could resist non-malicious distortions [1], [4]. Fragile watermarks are highly sensitive to alterations [1], [4]. They can accurately detect the changes made in the marked image. The underlying idea behind fragile technique is to insert a watermark in such a way that any attempt to alter the content of an image will also alter the watermark itself. Therefore, fragile watermark can be used in all the applications for which no modification on the original content is tolerated. To verify the authenticity of marked image, the watermark is retrieved from the same and is compared with the re-evaluated watermark [1], [5]. |
| Many methods for image authentication have been found in the literature. Image authentication based on set of pseudorandom numbers is proposed in [6]. For the purpose of image recovery, descriptors are needed for the reconstruction of tampered region. A self recovery/embedding block based authentication technique for JPEG image has been described in [5], [7]. Here, an image is divided into non-overlapping blocks. A transformation is applied to every block so as to obtain descriptors which are spatially embedded in distant blocks. Altered blocks are recovered with the help of these block descriptors. A common transformation method employed in the evaluation of descriptor is through the Discrete Cosine Transform (DCT). Performing DCT in an image block, results in a transformed block with one DC coefficient and many AC coefficients. For each block, only a few DCT coefficients have significant amplitude and are embedded in distant blocks, neglecting other coefficients with low amplitude [8]. The image block can be approximately recovered by inverse DCT of embedded coefficients. These coefficients can be used as descriptors. A JPEG compressed version of each block is inserted into the LSBs of a distant block. The distance of this distant block may be approximately chosen as one-third of image size in any chosen direction. |
| Different scheme have been proposed for authentication as well as localization of the tampering of images by dividing image in 8×8 block size [8], [9]. By reducing the block size, better localization with respect to alterations can be provided. Further, it reduces the artefacts incurred during process of reconstruction. In this context, an algorithm which provides detection of tampering and recovery in a 4×4 block size is proposed. Method for reconstruction using descriptors based on quantized DCT coefficients is suggested in [10]. Here, the reconstruction is achieved through descriptors which are evaluated by a combined technique employing DWT and DCT based approaches. These descriptor values are stored at distant locations to ensure that the descriptors are intact. |
PROPOSED SCHEME |
| A watermarked image is formed from the original image through self-embedding process. It concerns with embedding of digest and descriptor in two least significant bits of each pixel in image. The digest is embedded for authentication and the descriptor for purpose of recovery. Digest is evaluated for each 4×4 sub-block by multiplying each pixel in it by one of the 16 pseudorandom numbers generated from a secret key. An overall schematic diagram for the proposed algorithm is shown in Fig. 1. |
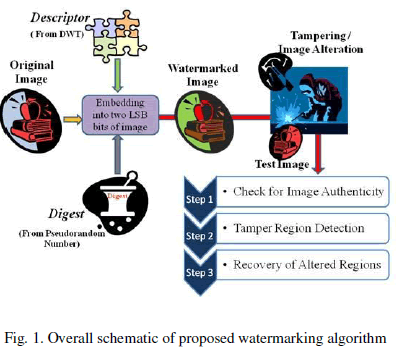 |
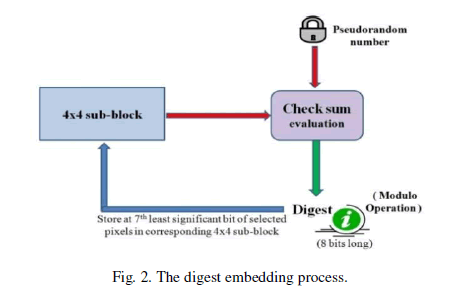
| Simple method for the generation pseudorandom sequence from an integer is hereby discussed. A 16 bit random binary number is chosen. The binary sequence is rotated/ shifted by one place. This shifted sequence is XOR-ed with the previous sequence. Convert this binary sequence to decimal number. Repeat this to form 16 pseudorandom numbers. The check sum is evaluated by the product of pseudorandom numbers with pixel values of 4×4 sub-block. The sum of these products undergo modulo operation to generate the digest. This is shown in Fig. 2. The storage of digest is shown in Fig. 3. The recovered quality of the tampered regions in the image increases as the number of bits allotted for recovery increase. But, as the number of bits for recovery increase, the quality of watermarked image degrades. Therefore, the embedding is confined within two least significant bits. Due to the limitation in the embedding capacity, it is necessary to apply a transformation so as to have a compressed representation that can reconstruct the original image within the storage size constraint. However, during compression of the image content, it has to be ensured that the recovered image is of acceptable quality, considering the embedding capacity of the original image. Descriptor is evaluated through a series of transformation. DWT transformation of entire image is followed by block based DCT transformation of the LL part of the DWT transformed image and its quantization. Fig. 4 describes the descriptor evaluation and embedding process. The watermarked image can undergo tampering/ alteration to form a test image. The obtained test image undergoes check for authenticity. The altered regions in an unauthentic image are detected and further the recovery of those altered regions is done. |
A. Self- Embedding Algorithm for Watermarking |
| The self-embedding process concerns with embedding of digest and descriptor into two least significant bits of the original image. In the proposed algorithm, all pixels in image will undergo this transformation. The self-embedding steps are as follows: |
| 1) Generate 16 pseudorandom sequences using a secret key. |
| 2) Reset the two least significant bits (LSBs) of the original image to zero. |
| 3) Divide the modified image into blocks of size 8×8 and each 8×8 block into four 4×4 sub-blocks. |
| 4) Checksum formation: Based on the 5 most significant bits of each pixel in 4×4 sub-blocks and 16 pseudorandom sequences, evaluate a checksum value corresponding to each sub-block. The block number and image properties, i.e. image dimensions, are also incorporated in evaluation process of checksum. |
| 5) Digest evaluation for image authentication: A modulo operation is done with the obtained checksum, so as to limit the digest to 8 bit value. An integer N is chosen such that the digest is always 8 bit long. Choice of N should be such that it is an odd value less than 255. |
| 6) Storage of digest information: These digest bits are stored in those 4×4 sub-block where the digest was evaluated as their 7th least significant bit of each pixels. The storage is based on selection of 8 pixels from group of 16 pixels in each 4×4 blocks based on relative average luminance. This will help in checking the authentication of each 4×4 sub-block. Embedding o f digest is shown in Fig. 3. |
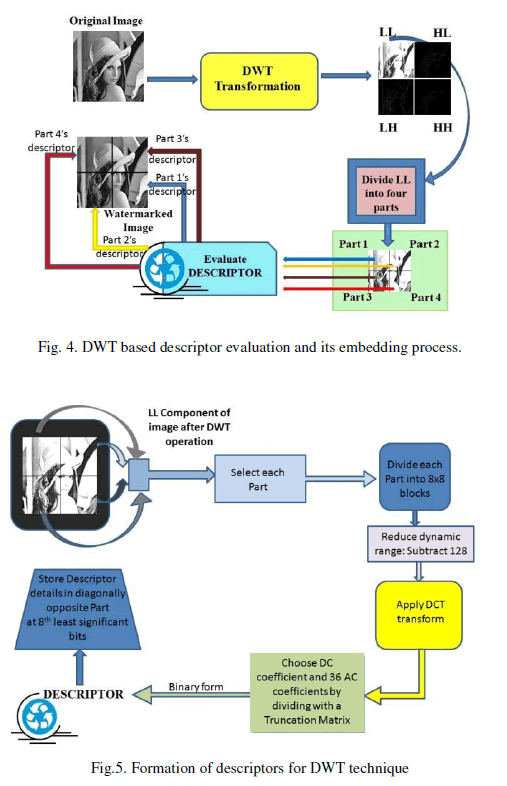
| 7) Descriptor evaluation: Evaluate the first level DWT transformation for the image to obtain LL , LH, HL, HH components. Choose the entire LL matrix and divide it into four non overlapping parts. |
| 8) Each of one of these four parts of LL is further divided into non-overlapping blocks having 8x8 size. |
| 9) Subtract 128 from each element of the matrix to reduce the dynamic range. Apply DCT transformation to each of these 8x8 blocks. |
| 10) Divide each of these transformed matrices with a constant truncation matrix. |
| 11) Quantize the resulting matrix coefficients and store the coefficients in binary form. Also store mean values of HL, LH, HH to forms the descriptor for one LL part of the image. |
| 12) The descriptor details for each part of LL component is stored at 8th least significant bit (LSB) in pixels, but at complement LL component sections, i.e. part one descriptor details is stored at part four of image and part four descriptor being stored at part one of image. |
| 13) Perform this transform operation on remaining three LL components of the image. |
 |
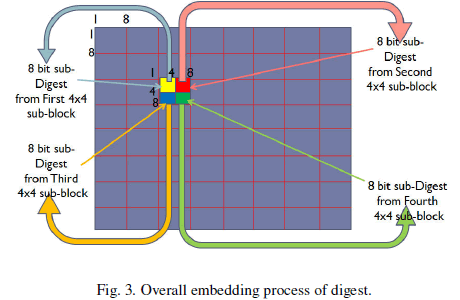 |
| The embedding of descriptors is shown in Fig. 4 and the formation of digest is shown in Fig. 5. |
 |
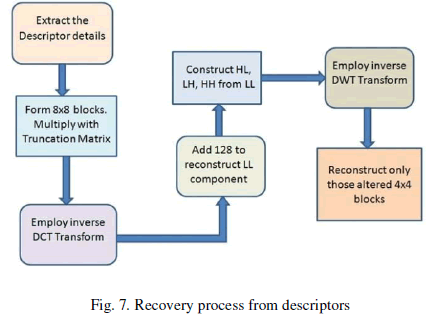
B. Algorithm for Tamper detection and Self-Recovery |
| Watermark extraction is the inverse process of embedding. The crucial part of recovery process is to precisely locate the tampered regions and to extract the embedded watermark from the remaining image to fill tampering regions. An over view of image authentication detection and recovery is shown in Fig. 6. First the obtained watermarked image is checked for authenticity by comparison between extracted digest and calculated digest. After checking for the authenticity, if the image is found unauthentic, then locate the tampered regions. The tampered regions are detected with an accuracy of 4×4 size. Steps for retrieval are further done using inverse discrete wavelet transform. |
| The retrieval steps are listed as follows: |
| 1) Upon receiving a test watermarked image, extract the least significant bit information per sub-block from the watermarked image by embedding rules. |
| 2) Detect the tampered sub-blocks by a comparison between the digest embedded in watermarked image and recalculated digest from the watermarked image. Since the authentication is being done in 4x4 block level, precise localization of tampering is possible. |
| 3) From those descriptor details stored in the least significant bits, reconstruct the DWT coefficient LL by employing the reverse operations used for embedding, i.e. by multiplying with truncation matrix and calculating inverse discrete cosine transform in 8x8 block size. |
| 4) Add 128 from each element of the matrix to obtain the LL component of the image. |
| 5) From the LL component, obtain HL, LH, HH by finding the horizontal, vertical and diagonal edges of LL and weighing each edge accordingly by its mean value. |
| 6) Evaluate the inverse discrete wavelet transform and replace those regions with the reconstructed regions from the descriptor, where the alterations are detected. |
| The recovery of tampered regions from the descriptor is done through the inverse process involved to formulate the descriptors. This is shown in Fig. 7. |
 |
EXPERIMENTAL RESULTS AND VERIFICATION |
| The proposed watermark does not significantly affect the quality of the image. This is visually evident on comparing the original image and the watermarked image which are shown in Fig. 8 (a) and 8 (b) respectively. Since the watermarking is being done in the last two least significant bits, the maximum difference in magnitude of pixel value that occurs between the original and watermarked image is three. |
 |
| For evaluating the quantitative degradation of the image introduced by the proposed algorithm, MSE (mean square error) and PSNR (Peak Signal to Noise Ratio) are calculated. |
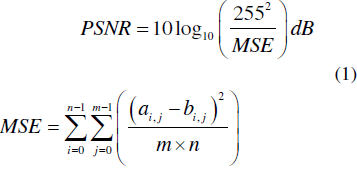 |
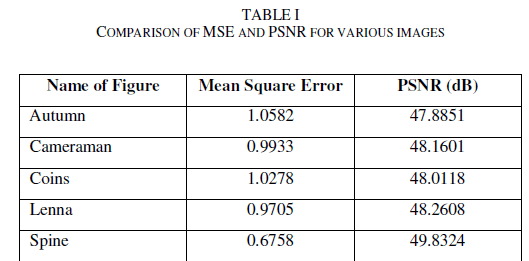
| where, m n is the image size and i , j a and i , j b are the corresponding pixel values of original and watermarked images. The MSE and PSNR of the watermarked Lena image are calculated and obtained as 0.9705 and 48.2608 respectively. These values are quite reasonable. PSNR value above 35dB is appreciable for watermarked images. Table 1. shows a comparison between the MSE and PSNR of various standard images. |
 \ \ |
 |
| Image authentication with a block size of 4×4 is proposed in this paper. Smaller block size results in more localized tamper detection and better reconstruction of the image. Fig. 9 shows comparative results while employing the two different block sizes, 4×4 and 8×8. Watermarked Lena image is shown in Fig. 9 (a). Fig. 9 (b) shows the tampered version of Lena image. Fig. 9 (c) and Fig. 9 (d) show the detection of tampered regions in the image with block size of 4×4 and 8×8 respectively. More accurate detection of tampered region for 4×4 block size is evident by comparing Fig. 9 (c) and 9 (d). Here better localization for tampered regions is obtained in 4x4 based techniques. Better localization helps to reduce the amount of incurred artifacts during reconstruction. |
| Employing descriptors based on DCT and DWT techniques have varying perceptual performances. Fig. 10 shows the recovered output image based DCT and DWT descriptors. |
 |
| The quality of DWT based recovery shows significant improvement over the DCT method. The region near the left eye is poor and blurred in DCT technique, in contrast to DWT technique. DWT method provides better reconstruction quality for high frequency regions. The reconstructed version of the complete image using the descriptors based on DCT and DWT are shown in Fig. 11. This shows significant improvement in visual perception for DWT based descriptor technique. |
 |
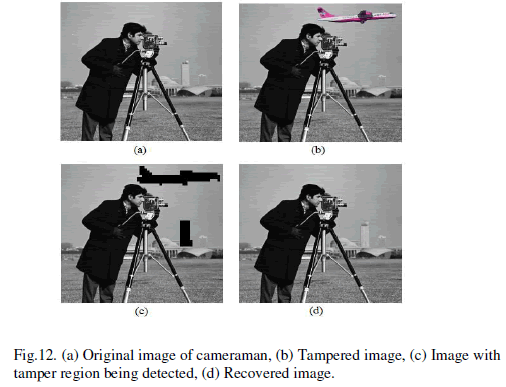
| The effectiveness of the proposed technique is verified in cameraman and Lena images and the results are presented. Fig. 12 (b) shows the tampered version of Fig. 12 (a) in which the structure of a building is erased and an aero plane is added. The proposed technique detects the altered regions by comparing the stored digest and the recalculated digest as discussed in section II. Fig. 12 (c) shows the image with the detection of the altered regions, and Fig. 12 (d) shows the altered regions which are reconstructed from the altered image using the descriptors. |
 |
CONCLUSION |
| A simple but effective algorithm for image tamper detection and self recovery is done. This scheme can detect the alteration/tampering done on the watermarked image with localization in level of 4×4 block size. The advantage of the proposed 4×4 block based algorithm is that, it induces fewer artifacts during the reconstruction than 8×8 block scheme. Utilization of DWT based technique will improve the reconstruction quality in comparison to DCT method. Although the distortion made in large area and tampering done in multiple regions degrade the quality of recovered regions, their detection will never go un-noticed. This algorithm can effectively thwart collage attack. |
References |
|