Keywords
|
| Transaction, Technique, Fraud Detection, Verify |
INTRODUCTION
|
| Web mining is the use of data mining techniques to automatically discover and extract information from web documents and services. Web mining is the application of data mining techniques to discover patterns from the Web. Web mining can be divided into three different types, which are Web usage mining, Web content mining and Web structure mining. |
| Fraud is an intentional deception made for personal gain or to damage another user/individual is fraudulent. Legal definition varies by legal jurisdiction for fraud. Fraud is a civil law violation and also a crime. Defrauding people or entities of money is a common purpose of fraud. |
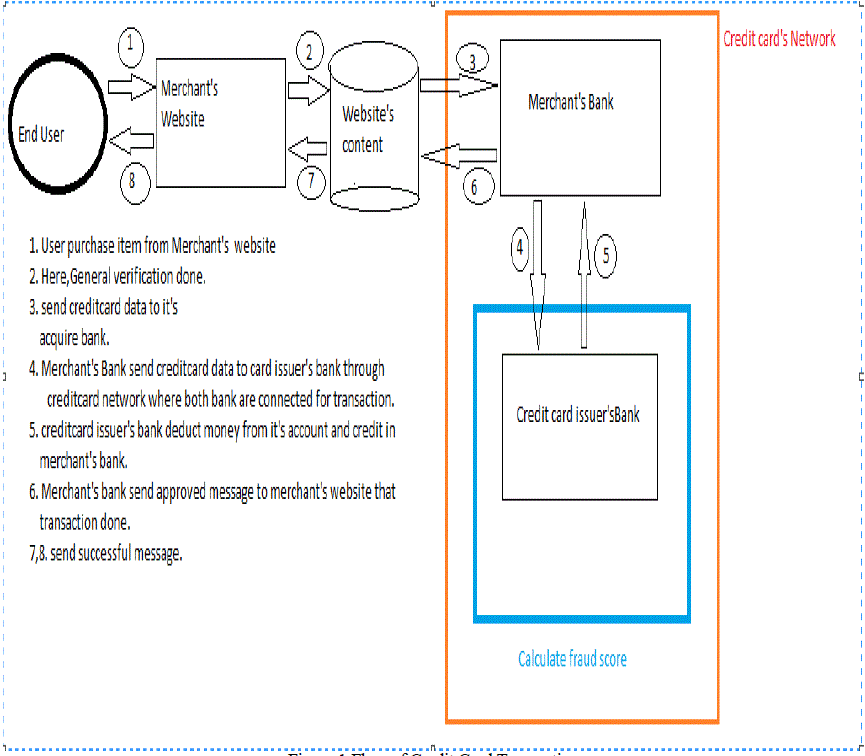
| Credit card is a medium of selling goods or services without having cash in hand. A credit card is a simple way of offering credit to a consumer automatically. Credit card carries an identifying number that helps in shopping transactions rapidity. |
| Credit card is a medium of selling goods or services without having cash in hand. A credit card is a simple way of offering credit to a consumer automatically [2].Credit card carries an identifying number that helps in shopping transactions rapidity. Credit card fraud detection is the process of identifying those transactions that are fraudulent into two classes of legitimate and fraudulent transactions. The credit card fraud detection system developed used four clusters of low, high, risky and high risk. Once the transaction is legitimate, it was processed but if any transaction falls into any of these clusters it was labelled as suspicious/fraudulent. The alert goes off and the reason is given. The fraudulent transaction will not be processed but will be committed to the database. Fraud is an intentional deception made for personal gain or to damage another user/individual is fraudulent. Legal definition varies by legal jurisdiction for fraud [1] [2]. Fraud is a civil law violation and also a crime. Defrauding people or entities of money is a common purpose of fraud. |
II. RELATED WORK
|
| Various techniques like classification, clustering and association of web mining will be integrated to represent the sequence of operations in credit card transaction processing and show how it can be used for the detection of frauds. Initially, web mining techniques trained with the normal behaviour of a cardholder. If an incoming credit card transaction is not accepted by the web mining model with sufficiently high probability, it is considered to be fraudulent. At the same time, the system will try to ensure that genuine transactions will not be rejected. Web mining techniques can be trained on examples of fraud due to lost cards, stolen cards, application fraud, counterfeit fraud, and mail-order fraud [6]. |
| Using data from a credit card issuer, a neural network based fraud detection system was trained on a large sample of labelled credit card account transactions and tested on a holdout data set that consisted of all account activity over a subsequent two-month period of time. The neural network was trained on examples of fraud due to lost cards, stolen cards, application fraud, counterfeit fraud, mail-order fraud and NRI (Non-Received Issue) fraud. The network detected significantly more fraud accounts with significantly fewer false positives over rule-based fraud detection procedures. There are several fraud detection technology exist based on Data mining, Knowledge Discovery and Expert System [6][7]. All these are not capable enough to detect the fraud at the time because there are many fraudulent transactions are in progress due to very less chance of a transaction being fraudulent. |
III. PROPOSED TECHNOLOGY
|
| There are many ways in which fraudsters execute a credit card fraud. As technology changes, so does the technology of fraudsters, and thus the way in which they go about carrying out fraudulent activities. Frauds can be broadly classified into three categories traditional card related frauds, merchant related frauds and Internet frauds. |
| There are many different kinds of neural networks and neural network algorithms. The most popular neural network algorithm is back propagation. In back propagation, Multilayer feed Forward Algorithm used to detect fraud in credit card system. The field of neural networks was originally kindled by psychologists and neurobiologists who sought to develop and test computational analogues of neurons. Back propagation is a common method of training artificial neural networks so as to minimize the objective function. |
IV. IMPLEMENTATION
|
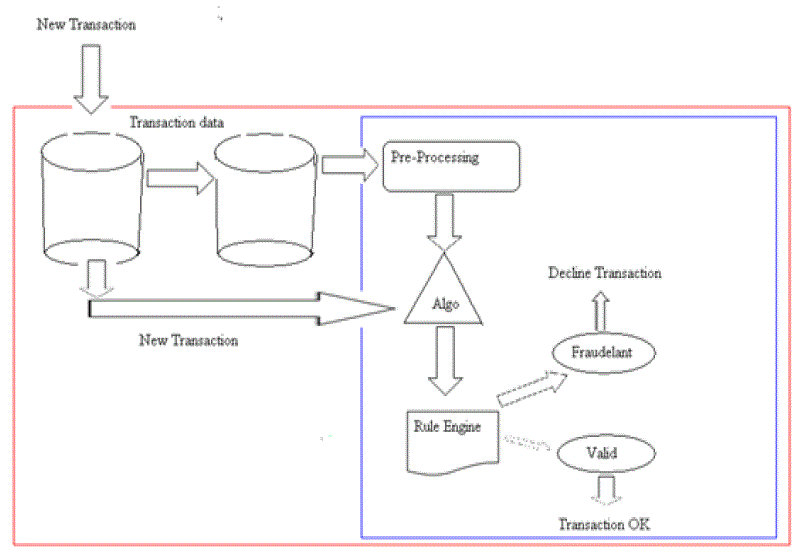
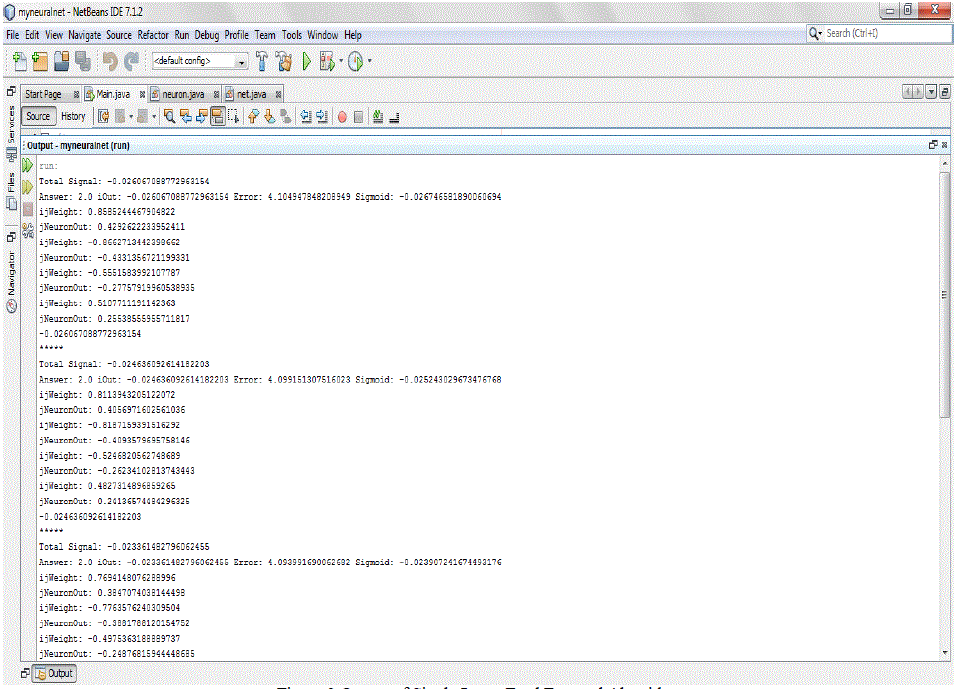
| The proposed work has been implemented in Net beans IDE 7.1.2. Some Patterns is given as the input. Once the errors are found reduction would be done based on Sigmoid. Used single layer feed forward algorithm using random patterns. Here, Inserted Random pattern for train network. For example inserted pattern are given in below table. |
| Our system perform single layer feed forward neural network algorithm and predict the error. Assume & Consider any rth output neuron and for the training example we have calculated the output „O? for which the target output „T? Hence, the error norm in output for the rth output neuron is given by Er 1 = 1/2 er 2 = 1/2 (T-O) 2 The Euclidean norm of error E1 for the first training pattern is given by E1 = 1/2 Σ (Tor – Oor) 2. If we use the same technique for all the training patterns, we get E (V, W) = ΣEj (V, W, I) Where E is the error function depending on the m (1+n) weights of [W] and [V]. |
Effect of Learning Rate ‘η’
|
| Learning rate coefficient determines the size of the weight adjustments made at each iteration and hence influences the rate of convergence. Poor choice of the coefficient can result in a failure in convergence. We should keep the coefficient constant through all the iterations for best results. If the learning rate coefficient is too large, the search path will oscillate and converges more slowly than a direct descent. |
V. CONCLUSION AND FUTURE WORK
|
| The detection of credit card fraud mechanism and examine the result based on the principles of this algorithm. Neural network?s single layer feed forward neural network algorithm that are being used to execute credit card fraud how credit card fraud impact on financial institution as well as merchant and customer, fraud detection. Further work, to study in more detail about the neural network and their role in fraud detection and combine this approach with feature back propagation algorithms to smoothly handle data of different feature types and detect the errors in large amount of transaction of credit card system. If this algorithm is applied into bank credit card fraud detection system, the probability of fraud transactions can be predicted soon after credit card transactions by the banks. The advantages neural networks offer over other techniques is that these models are able to learn from the past and thus, improve results as time passes. They can also extract rules and predict future activity based on the current situation. By employing neural networks effectively, banks can detect fraudulent use of a card, faster and more efficiently. Fraud detected and fraud transactions are generated with the sample data set or patterns. |
ACKNOWLEDGEMENT
|
| Before penning a single word for the Paper, we take this opportunity to thank Mrs. Vaishali Patel bottom of our heart who guided us as much as possible and for giving us valuable information regarding the paper. This was our first professional step toward the high careers in IT field. It was a great experience of exposing as well as learning lot of new things in Information Technology. We are indebted to all those who provided reviews our tasks and we apologize to anyone if we may have failed to mention. |
| |
Tables at a glance
|
|
|
| |
Figures at a glance
|
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
|
| |
References
|
- D.J. Hand, G. Blunt, M.G. Kelly, and N.M. Adams, “Data Mining for Fun and Profit,” Statistical Science, vol. 15, no. 2, pp. 111-131, 2000.
- “Statistics for General and On-Line Card Fraud,” http://www.epaynews.com/statistics/fraud.html, Mar. 2007.
- S. Ghosh and D.L. Reilly, “Credit Card Fraud Detection with a Neural-Network,” Proc. 27th Hawaii Int?l Conf. System Sciences:Information Systems: Decision Support and Knowledge-Based Systems, vol. 3, pp. 621-630, 1994.
- M. Syeda, Y.Q. Zhang, and Y. Pan, “Parallel Granular Networks for Fast Credit Card Fraud Detection,” Proc. IEEE Int?l Conf. FuzzySystems, pp. 572-577, 2002.
- S.J. Stolfo, D.W. Fan, W. Lee, A.L. Prodromidis, and P.K. Chan, “Credit Card Fraud Detection Using Meta-Learning: Issues and InitialResults,” Proc. AAAI Workshop AI Methods in Fraud and Risk Management, pp. 83-90, 1997.
- S.J. Stolfo, D.W. Fan, W. Lee, A. Prodromidis, and P.K. Chan, “Cost-Based Modeling for Fraud and Intrusion Detection: Results fromthe JAM Project,” Proc. DARPA Information Survivability Conf. and Exposition, vol. 2, pp. 130-144, 2000.
- Abdelhalim, A, and I Traore. "Identity Application Fraud Detection using Web”. International Journal of Computer and Network Security1, no. 1 (October 2009): 31-44.
- Aha, David W., Dennis Kibler, and Marc K. Albert. "Instance-based learning algorithms."Machine Learning, 1991: 37-66.
- Aleskerov, Emin, Bernd Freisleben, and Bharat Rao. "Card watch: A neural network based database mining system for credit card frauddetection." Computational Intelligence for Financial Engineering. Piscataway, NJ: IEEE, 1997. 220-226.
- Ali, K., and M. Pazzani. "Error reduction through learning multiple descriptions." Machine Learning 24, no. 3 (1996): 173-202.
- Basel Committee on Banking Supervision. "Basel Accords II." Basel, Switzerland: Bank for International Settlements Press &Communications, June 2006.
- Bolton, R, and D Hand. "Unsupervised Profiling Methods for Fraud Detection." Credit Scoring and Credit Control VII, 2001.
- Brause, R, T Langsdorf, and M Hepp. "Neural Data Mining for Credit Card Fraud Detection." Proceedings of the 11th IEEE InternationalConference on Tools with Artificial Intelligence. Silver Spring: IEEE Computer Society Press, 1999. 103-106.
- Vatsa, S. Sural, and A.K. Majumdar, “A Game-theoretic Approach to Credit Card Fraud Detection,” Proc. First Int?lConf.InformationSystems Security, pp. 263-276, 2005.
- X.D. Hoang, J. Hu, and P. Bertok, “A Multi-Layer Model for Anomaly Intrusion Detection Using Program Sequences of System Calls,” Proc. 11th IEEE Int?l Conf. Networks, pp. 531-536, 2003.
|