ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
Abhinav Kumar, Abhijeet Kumar, Dr. C. Nalini, K.G.S. Venkatesan
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
The number of Wifi capable mobile devices including laptops and handheld devices (e.g., smart phone and tablet PC) has been increasing rapidly. A Mobile Ad hoc Network (MANET) is consisting of a collection of wireless mobile nodes, which form a temporary network without relying on any existing infrastructure or centralized administration. The emergence and the envisioned future of real time and multimedia applications have stimulated the need of high Quality of Service (QoS) support in wireless and mobile networking environments. The QoS support reduces end-to-end transmission delay and enhances throughput to guarantee the seamless communication between mobile devices and wireless infrastructures. we propose a QoS-Oriented Distributed routing protocol (QOD) to enhance the QoS support capability of hybrid networks. Analytical and simulation results based on the random waypoint model and the real human mobility model show that QOD can provide high QoS performance in terms of overhead, transmission delay, mobility-resilience, and scalability.
KEYWORDS |
| Overlay Quality of Service (QoS), Mobile Ad hoc Network (MANET) |
I. INTRODUCTION |
| A mobile ad hoc network is an autonomous collection of mobile devices such as laptops, smart phones, sensors that communicate with each other over wireless links and cooperate in a distributed manner in order to provide the necessary network functionality in the absence of a fixed infrastructure [2]. This type of network, operates as a standalone network or with one or multiple points of attachment to cellular networks or the internet. It paves the way for numerous new and exciting applications. A mobile ad-hoc network (MANET) consists of mobile hosts equipped with wireless communication devices. The transmission of a mobile host is received by all hosts within its transmission range due to the broadcast nature of wireless communication and omni-directional antennae. If two wireless hosts are out of their transmission ranges in the ad hoc networks, other mobile hosts located between them can forward their messages which effectively builds connected networks among the mobile hosts in the deployed area. Due to the mobility of wireless hosts, each host needs to be equipped with the capability of an autonomous system. Ad-Hoc network is a dynamic multihop wireless network that is established by a set of mobile nodes on a shared wireless channel. Each mobile host performs local broadcasts in order to identify its existence to the surrounding hosts [1]. |
| Quality of Service (QOS) refers to a set of service requirements that needs to be met by the network while transporting a packet stream from a source to its destination. Informally, it refers to the probability of a packet passing between two points in the network. The network is expected to guarantee a set of measurable pre-specified service attributes to the users in terms of end-to-end performance, such as end to end delay, throughput, probability of packet loss, delivery ratio [5]. |
 |
II. LITERATURE SURVEY |
| A literature review is a text written by someone to consider the critical points of current knowledge including substantive findings as well as theoretical and methodological contributions to a particular topic. Literature reviews are secondary sources, and as such, do not report any new or original experimental work. Most often associated with academic-oriented literature, such as a thesis, a literature review usually precedes a research proposal and results section. Its main goals are to situate the current study within the body of literature and to provide context for the particular reader [7]. |
| The ability of a Mobile Ad Hoc Network(MANET) to provide adequate quality of service (QOS) is limited by the ability of the underlying routing protocol. Three MANET routing protocols OLSR, DSR and AODV with an emphasis on the effect they have on various QOS metrics [10]. The effects of these differences are quantified in terms of packet delivery ratio, end-to-end hop count, end-to-end latency, and mechanism overhead. We show that the proactive protocol, OLSR, builds paths with consistently lower hop counts than the reactive protocols, AODV and DSR, a fact that leads to a reduction in end-to-end latency [11]. A routing protocol that cannot quickly recover from link breakage caused by mobility renders a QOS model incapable of meeting delivery requirements. Finally, we analyze the effect of mobility on the distribution of end-to-end latencies. Traditionally, reactive protocols are criticized for buffering during the building of routes, buffering phenomenon caused by the proactive mechanisms of OLSR [15]. |
| This paper presents a number of routing protocols for MANET, which are broadly categorized as proactive and reactive. Proactive routing protocols tend to provide lower latency than that of the on-demand protocols, because they try to maintain routes to all the nodes in the network all the time [17]. But the drawback for such protocols is the excessive routing overhead transmitted, which is periodic in nature without much consideration for the network mobility or load. On the other hand, though reactive protocols discover routes only when they are needed, they may still generate a huge amount of traffic when the network changes frequently. Depending on the amount of network traffic and number of flows, the routing protocols could be chosen. When there is congestion in the network due to heavy traffic, in general case, a reactive protocol is preferable. Sometimes the size of the network might be a major considerable point [16]. |
| Multipath routing protocols for mobile ad hoc network addresses the problem of scalability, security, lifetime of networks, instability of wireless transmissions, and their adaptation to applications . The Multipath Dijkstra algorithmis proposed to obtain multiple paths. The algorithm gains great flexibility and extensibility by employing different link metrics and cost functions [19]. In addition ,route recovery and loop detectionare implemented in MP-OLSR in order to improve quality of service regarding OLSR. The backward compatibility with OLSR based on IP source routing is also studied. Simulation based on qualnet simulator is performed in different scenarios. A test bed is also set up to validate the protocol in real world. The results reveal that MP-OLSR is suitable for mobi le, large and dense networks with large traffic and could satisfy critical multimedia applications with high on time constraint [20]. |
| This thesis proposes an on-demand node-disjoint multipath routing protocol with low broadcast redundancy. Multipath routing allows the establishment of multiple paths between a single source and single destination node. It is also beneficial to avoid traffic congestion and frequent link breaks in communication because of the mobility of nodes [18]. The important components of the protocol, such as path accumulation, decreasing routing overhead and selecting nodedisjoint paths, are explained. Because the new protocol significantly reduces the total number of route request packets, this results in an increased delivery ratio, smaller end-to-end delays for data packets, lower control overhead and fewer collisions of packets. Although NDMR provides node-disjoint multipath routing with low route overhead in MANETs, it is only a best-effort routing approach, which is not enough to support QOS [21]. |
| Mobile Ad hoc Networks are highly dynamic networks. Quality of Service (QOS) routing in such networks is usually limited by the network breakage due to either node mobility or energy depletion of the mobile nodes. Also, to fulfill certain quality parameters, presence of multiple node-disjoint paths becomes essential. Such paths aid in the optimal traffic distribution and reliability in case of path breakages. Thus, to cater such problem, we present a node-disjoint multipath protocol. The metric used to select the paths takes into account the stability of the nodes and the corresponding links [24]. |
III. EXISTING SYSTEM |
| There are number of protocols available to improve the QOS parameters in wireless mobile networks by removing the nodes that consume and waste resources. Delivering end-to-end service quality in mobile ad hoc networks is intrinsically linked to the performance of the routing protocol because new routes or alternative routes between sourcedestination pairs need to be periodically computed during ongoing sessions [22]. Most of the approaches address a particular layer in OSI stack. However, there is no detailed research over the effects of packet dropping nodes on the network. |
I V. PROPOSED SYSTEM |
| In the proposed approach, we thoroughly analyses the effects of packet dropping nodes on the network QOS parameters and present our observations. Here we using AODV,DSR,DSDV protocol to identify the optimal measurements [26]. In this project, we are analyzing the following QOS parameters for wireless ad-hoc networks such as end-end delay, throughput, packet delivery ratio and packet drop. The above QOS parameters will be analyzed under two scenarios |
| Scenario 1: The network is in normal condition. That is, there is no presence of packet dropping nodes in the network. The network, in this case, can only be affected by the physical layer problems like link failure, signal drop, interference etc. |
| Scenario 2: The network in this case is in abnormal condition. There is a presence of one adversely [28]. |
| We will analyze these QOS parameters in both the above scenarios and present our observations in this research. |
| • End-end delay : it must be low |
| • Throughput : it must be high |
| • Packet delivery ratio : it must be high |
| • Packet drop : it must be low |
V. MODUELES |
| The following are the modules of the project along with the way they are implemented and that is planned with respect to the proposed system, while overcoming existing system and also providing the support for the future enhancement system. There are totally five modules used in our project which is listed below. Each module has specific usage in the project and is description is given below followed by the list of modules [23]. |
| • Route discovery process |
| A. Route discovery process |
| Route Discovery is used whenever a source node desires a route to a destination node. First, the source node looks up its route cache to determine if it already contains a route to the destination. If the source finds a valid route to the destination, it uses this route to send its data packets. If the node does not have a valid route to the destination, it initiates the route discovery process by broadcasting a route request message. The route request message contains the address of the source and the destination, and a unique identification number [22]. |
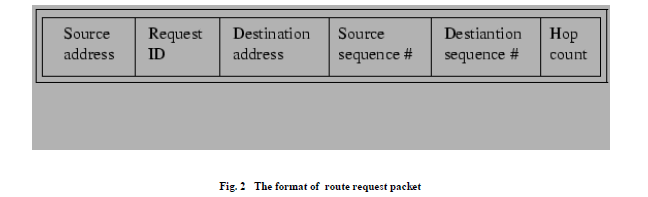 |
| In Fig. 2 an intermediate node that receives a route request message searches its route cache for a route to the destination. If no route is found, it appends its address to the route record of the message and forwards the message to its neighbours. The message propagates through the network until it reaches either the destination or an intermediate node with a route to the destination. Then a route reply message, containing the proper hop sequence for reaching the destination, is generated and unicast back to the source node [25]. |
| B. Route maintenance |
| Route Maintenance is used to handle route breaks. When a node encounters a fatal transmission problem at its data link layer, it removes the route from its route cache and generates a route error message. The route error message is sent to each node that has sent a packet routed over the broken link. When a node receives a route error message, it removes the hop in error from its route cache. Acknowledgment messages are used to verify the correct operation of the route links [26]. |
| C. AODV measurements |
| AODV is a reactive protocol, it establishes a route to a destination only on demand. It does not keep a record of all routes available in a network. The AODV Routing protocol uses an on-demand approach for finding routes, that is, a route is established only when it is required by a source node for transmitting data packets. In AODV [27], the source node and the intermediate nodes store the next-hop information corresponding to each flow for data packet transmission. In an on-demand routing protocol, the source node floods the routerequest packet in the network when a route is not available for the desired destination. It may obtain multiple routes to different destinations from a single route request. A node updates its path information only if the DestseqNum of the current packet received is greater or equal than the last DestseqNum stored at the node with smaller hopcount.A RouteRequest carries the SrcID, DestID, SrcSeqNum,DestSeqNum, BcastID, and the TTLfield. |
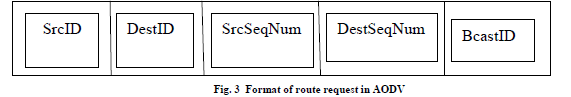 |
| When an intermediate node receives a route request, it either forwards it or prepares a route reply if it has a valid route to the destination. The validity of a route at the intermediate node is determined by comparing the sequence number at the intermediate node with the destination sequence number in the route request packet. If a route request is received multiple times, which is indicated by the BcastID - srcID pair, the duplicate copies are discarded. All intermediate nodes having valid routes to the destination, or the destination node itself, are allowed to send route reply packets to the source. In Figure 3, Every intermediate node, while forwarding a route request, enters the previous node address and itsBcastID. A timer is used to delete this entry in case a route reply is not received before the timer expires [28]. When a node receives a route reply packet, information about the previous node from which the packet was received is also stored in order to forward the data packet to this next node as the next hop toward the destination. After implementing aodv protocol in manet we need to take measurements like |
| • Packet sending |
| • Packet receiving |
| • Delivery ratio |
| • Delay |
| • Throughput |
| In this all we need to take optimal estimations, and generate x-graph for AODV implementation. |
| D. DSDV measurements |
| DSDV is proactive routing protocol. Every node maintains one or more tables represent the entire topology of the networks [25]. It maintains up-to-date routing information. It uses full dump or incremental update to reduce network traffic generated by rout updates. The broadcast of route updates is delayed by settling time. DSDV solve the problem of routing loops and count to infinity . In DSDV, a sequence number is linked to a destination node, and usually is originated by that node (the owner). The only case that a non-owner node updates a sequence number of a route is when it detects a link break on that route. An owner node always uses even-numbers as sequence numbers, and a non-owner node always uses odd-numbers. With the addition of sequence numbers, routes for the same destination are selected based on the following rules: |
| • A route with a newer sequence number is preferred. |
| • In the case that two routes have a same sequence number, the one with a better cost metric is preferred. |
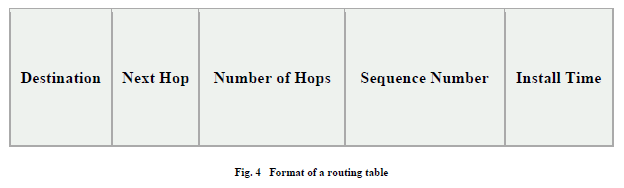
| The routing table contains the following: |
| • All available destinations IP address |
| • Next hop IP address |
| • Number of hops to reach the destination |
| • Sequence number assigned by the destination node |
| • Install time |
 |
| Routing table updates create lots of control traffic. DSDV addresses this problem by using two types of routing update packets. Full Dumps carry all routing table information. It transmitted relatively infrequently. Incremental updates carry only information changed since last full dump. Fits within one network protocol data unit. When updates can no longer fit in one NPDU, send full dump [31]. |
| Routing table consist of destination address, destination sequence number, next hop, hop count. Source node transmit routing table. When neighbor node receive the new routing information, neighbour node update their routing table and continue propagation information. If any link breaks between the nodes [29], |
| • Update the hop count to infinity |
| • Increment the destination sequence number |
| Then node sends update with new route information. After implementing DSDV protocol in MANET we need to take measurement slike, |
| • Packet sending |
| • Packet receiving, |
| • Delivery ratio, |
| • Delay |
| • Throughput. |
| In this all we need to take optimal estimations, and generate x-graph for DSDV implementation. |
| • Route maintenance |
| • AODV measurements |
| • Destination sequence numbers |
| • Next hop information |
| • DSDV measurements |
| • DSR measurements |
| • Performance Analysis |
VI. SYSTEM IMPLEMENTATION |
| Implementation is the most crucial stage in achieving a successful system and giving the user’s confidence that the new system is workable and effective. It may be implementation of a modified application to replace an existing one. This type of conversation is relatively easy to handle, provide there are no major changes in the system [30]. |
| Each program is tested individually at the time of development using the data and has verified that this program linked together in the way specified in the programs specification, the computer system and its environment is tested to the satisfaction of the user. The system that has been developed is accepted and proved to be satisfactory for the user. And so the system is going to be implemented very soon. A simple operating procedure is included so that the user can understand the different functions clearly and quickly [35]. |
| Initially as a first step the executable form of the application is to be created and loaded in the common server machine which is accessible to the entire user and the server is to be connected to a network. The final stage is to document the entire system which provides components and the operating procedures of the system. Implementation is the stage of the project when the theoretical design is turned out into a working system. Thus it can be considered to be the most critical stage in achieving a successful new system and in giving the user, confidence that the new system will work and be effective [39]. |
| The implementation stage involves careful planning, investigation of the existing system and it’s constraints on implementation, designing of methods to achieve changeover and evaluation of changeover methods. Implementation is the process of converting a new system design into operation. It is the phase that focuses on user training, site preparation and file conversion for installing a candidate system. The important factor that should be considered here is that the conversion should not disrupt the functioning of the organization [38]. |
VII. CONCLUSION |
| Thus the three popular ad hoc routing protocols AODV, DSR and DSDV have been compared. The performance of the protocols were measured with respect to metrics like Packet delivery ratio, end – end delay etc. Performance levels of the general DSR decrease when the numbers of malicious node increase. But performance levels of the general AODV increase when the numbers of malicious node decreasing. The results of the simulation indicate that performance of the AODV protocol is better than DSR and DSDV protocols. |
VII. FUTURE ENHANCEMENT |
| MANETs are likely to expand their presence in future communication environments. Support for QOS will thus be an important and desirable component of MANETs. Although difficult, it is quite interesting and challenging to design and develop QOS provisioning techniques for MANETs. This report provides a survey of the state of the art in this area. Several important research issues and open questions need to be addressed to facilitate QOS support in MANETs. Use of location, mobility, power consumption, probability of resource, and route availability are some of the issues currently being examined and needing further |
VII. ACKNOWLEDGEMENT |
| The author would like to thank the Vice Chancellor, Dean-Engineering, Director, Secretary, Correspondent, HOD of Computer Science & Engineering, Dr. K.P. Kaliyamurthie, Bharath University, Chennai for their motivation and constant encouragement. The author would like to specially thank Dr. A. Kumaravel, Dean , School of Computing, for his guidance and for critical review of this manuscript and for his valuable input and fruitful discussions in completing the work and the Faculty Members of Department of Computer Science &Engineering. Also, he takes privilege in extending gratitude to his parents and family members who rendered their support throughout this Research work. |
References |
|